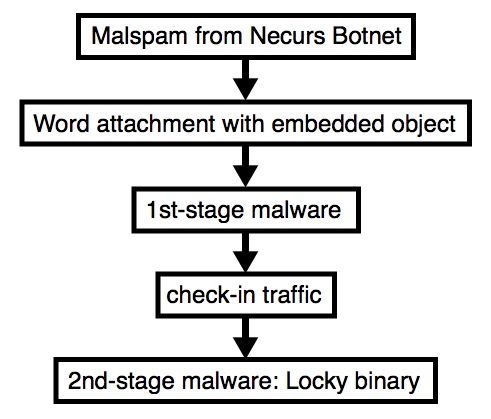
2017-11-01 - NECURS BOTNET MALSPAM CONTINUES PUSHING LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-11-01-Necurs-botnet-malspam-pushes-Locky-ransomware.pcap.zip 582.2 kB (582,220 bytes)
- 2017-11-01-Necurs-Botnet-malspam-tracker.csv.zip 0.9 kB (923 bytes)
- 2017-11-01-Necurs-Botnet-malspam-and-Locky-ransomware-samples.zip 2.0 MB (1,977,048 bytes)
SOME PRIOR DOCUMENTATION:
- 2017-10-19 - SANS Internet Storm Center (ISC) - Necurs Botnet malspam pushes Locky ransomware using DDE attack
- 2017-10-24 - My Online Security - Locky ransomware delivered via DDE exploit Scan Data malspam no-reply@victim domain
- 2017-10-24 - malware-traffic-analysis.net - Necurs Botnet malspam uses DDE attack to push Locky ransomware
- 2017-10-30 - malware-traffic-analysis.net - Necurs Botnet malspam uses DDE attack to push Locky ransomware
- 2017-10-31 - My Online Security - blank emails with fake invoice attachments deliver Locky ransomware via word docs with embedded OLE objects
- 2017-10-31 - malware-traffic-analysis.net - Necurs Botnet malspam stops using DDE, still uses Word docs to push Locky ransomware
NOTES:
- Necurs Botnet malspam is using Word docs with embedded objects (not DDE attack) for the 2nd day in a row.
- Like yesterday, the Word documents have embedded objects that call PowerShell to retrieve the first-stage malware.
Shown above: Current chain of events (no DDE, but embedded objects).
EMAILS
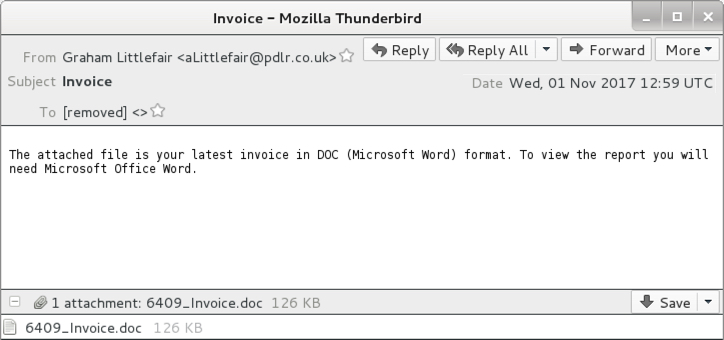
Shown above: Example of an email from this wave of malspam.
EMAIL HEADERS:
- Date: Wednesday 2017-11-01 as early as 10:29 UTC through at least 12:59 UTC
- Subject: Invoice
- Attachment names: [random digits]_Invoice.doc
EXAMPLES OF SENDING ADDRESSES (ALL SPOOFED):
- From: Brittney Bee <aBee@brownmail.worldonline[.]co[.]uk>
- From: Graham Littlefair <aLittlefair@pdlr[.]co[.]uk>
- From: Lester Makins <aMakins@dothat[.]uk>
- From: Misty Bates <aBates@hartleyromaniuk[.]co[.]uk>
- From: Pearlie Bossence <aBossence@acornresearch[.]co[.]uk>
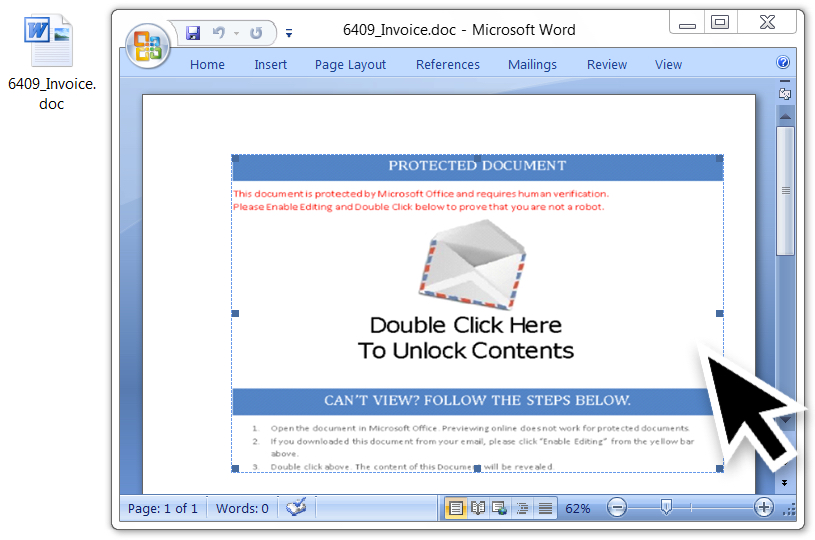
Shown above: Word document from one of the emails with malicious embedded object).
TRAFFIC
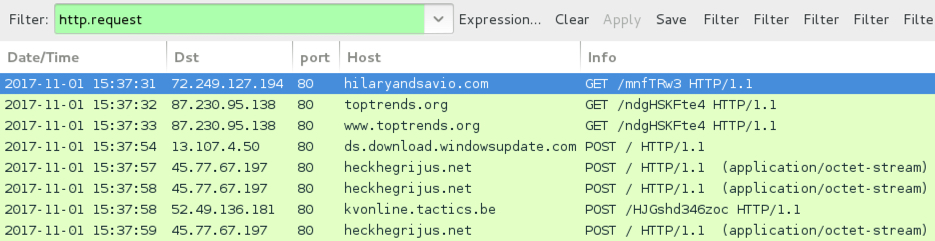
Shown above: Traffic from the infection filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 72.249.127[.]194 port 80 - hilaryandsavio[.]com - GET /mnfTRw3
- 87.230.95[.]138 port 80 - toptrends[.]org - GET /ndgHSKFte4
- 87.230.95[.]138 port 80 - www.toptrends[.]org - GET /ndgHSKFte4
- ds.download.windowsupdate[.]com - POST /
- 45.77.67[.]197 port 80 - heckhegrijus[.]net - POST /
- 52.49.136[.]181 port 80 - kvonline.tactics[.]be - POST /HJGshd346zoc
OTHER HTTP REQUESTS GENERATED BY THE MALICIOUS WORD DOCUMENTS:
- cirad[.]or[.]id - GET /mnfTRw3
- givagarden[.]com - GET /mnfTRw3
- heart-sp[.]com - GET /mnfTRw3
- internet-webshops[.]de - GET /mnfTRw3
OTHER HTTP REQUESTS FOR THE 1ST-STAGE MALWARE:
- urea-art[.]ru - GET /ndgHSKFte4
- celebrityonline[.]cz - GET /ndgHSKFte4
- claridge-holdings[.]com - GET /ndgHSKFte4
- dotecnia[.]cl - GET /ndgHSKFte4
- transmercasa[.]com - GET /ndgHSKFte4
- envi-herzog[.]de - GET /ndgHSKFte4
TOR DOMAIN FOR LOCKY DECRYPTION:
- g46mbrrzpfszonuk[.]onion
FILE HASHES
WORD DOCUMENTS WITH EMBEDDED OBJECT:
- SHA256 hash: 03db0e3eb42ffca3d32778f38a881872190dc5686b3699b2893fbf06f8120d34 - 222849_Invoice.doc
- SHA256 hash: ca6152dfcb2c2a2aec09322ca19ac8e883792a75dec95f588883cc6e181b4f5e - 328731_Invoice.doc
- SHA256 hash: 9cf8e4808b26e996a6531c01a30ebd5bf7b32247393c19e952d60888d04ba0cd - 49545_Invoice.doc
- SHA256 hash: 899e5742602d14bf59be0ccabc94b6f51254964b64001d77540774486797def7 - 57588_Invoice.doc
- SHA256 hash: 016dbaece7e91bd36a439c279815bdc095e7a3a8df5eb83fdaf8d4bcdc93a9fb - 6409_Invoice.doc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 8930bd4ab06a60d8b079d37fe029ff6039786988efd4cb0b4c5197d0b39d2a12
File size: 232,128 bytes
File location: C:\Users\[username]\AppData\Local\Temp\gnu64.exe
File location: C:\Users\[username]\AppData\Local\Temp\{3efee3d4-bc4f-ab17-4f3e-b1d4a9a108df}\w16E8508.exe
File description: Initial malware (generates callback traffic & downloads Locky)
Registry update: KHCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- SHA256 hash: 1b087b85b0f1c2b14dfa1b9c82004de598903a89a76af49ee4c4eed03bfefe24
File size: 585,728 bytes
File location: C:\Users\[username]\AppData\Local\Temp\E7SRXkYl.exe
File description: Locky ransomware (.asasin variant)
IMAGES
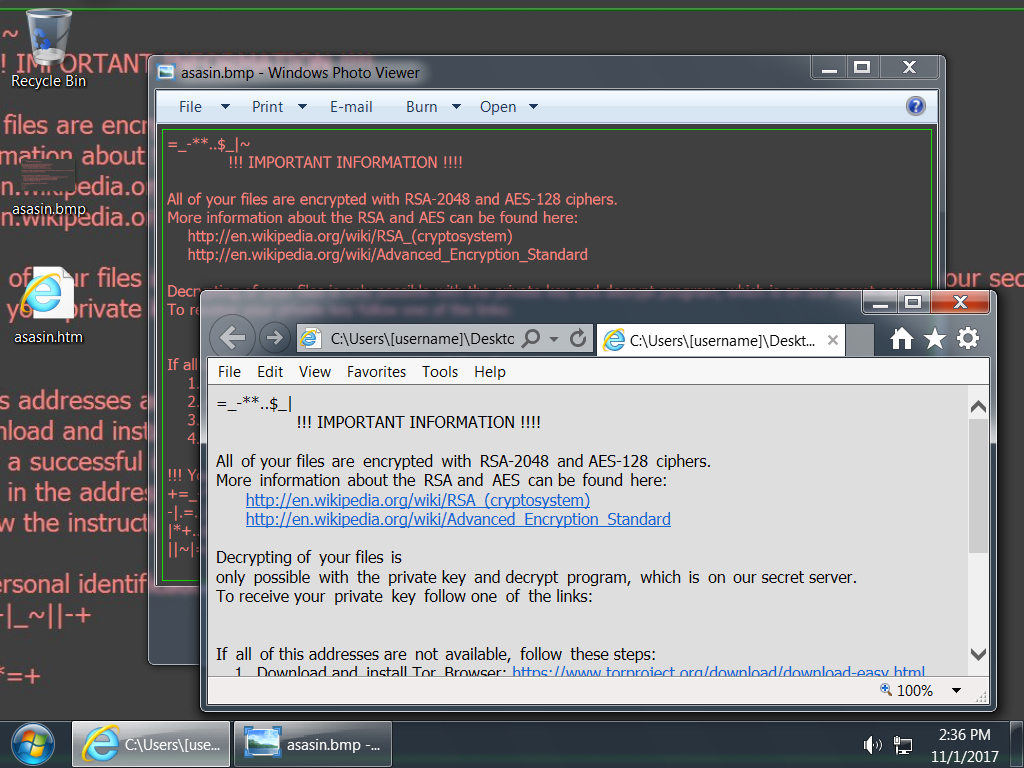
Shown above: Desktop from an infected Windows host.
Click here to return to the main page.