2017-11-01 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-11-01-Hancitor-malspam-24-examples.txt.zip 2.7 kB (2,738 bytes)
- 2017-11-01-Hancitor-malspam-24-examples.txt (32,613 bytes)
- 2017-11-01-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 333.7 kB (333,693 bytes)
- 2017-11-01-Hancitor-infection-with-Zeus-Panda-Banker.pcap (444,600 bytes)
- 2017-11-01-malware-from-Hancitor-infection.zip 234.4 kB (234,394 bytes)
- 2017-11-01-Hancitor-maldoc-fax_953654.doc (219,648 bytes)
- 2017-11-01-Zeus-Panda-Banker.exe (186,368 bytes)
INFORMATION COVERING THE 2017-11-01 WAVE OF HANCITOR
- @James_inthe_box: Incoming #hancitor run: "New incoming Fax from <digits>" pastebin.com/RTVN0SjK updates as I get them. (link to tweet)
NOTES:
- Looks like Hancitor has settled on Zeus Panda Banker and given up on DELoader/ZLoader (or whatever you call it).
Shown above: My tribute to the fallen.
EMAILS
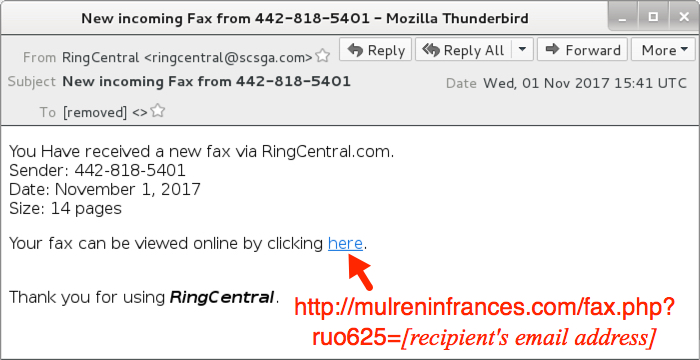
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2017-11-01 as early as 15:41 UTC through at least 18:51 UTC
- From: "RingCentral" <ringcentral@scsga[.]com>
- Received: from scsga[.]com ([5.40.45[.]99])
- Received: from scsga[.]com ([12.235.201[.]58])
- Received: from scsga[.]com ([24.121.0[.]239])
- Received: from scsga[.]com ([24.198.72[.]63])
- Received: from scsga[.]com ([66.214.96[.]122])
- Received: from scsga[.]com ([66.251.57[.]58])
- Received: from scsga[.]com ([67.78.226[.]170])
- Received: from scsga[.]com ([69.4.50[.]182])
- Received: from scsga[.]com ([69.160.204[.]254])
- Received: from scsga[.]com ([70.184.164[.]23])
- Received: from scsga[.]com ([71.0.220[.]4])
- Received: from scsga[.]com ([71.9.45[.]154])
- Received: from scsga[.]com ([71.12.100[.]6])
- Received: from scsga[.]com ([72.164.13[.]170])
- Received: from scsga[.]com ([74.93.19[.]115])
- Received: from scsga[.]com ([74.93.101[.]9])
- Received: from scsga[.]com ([74.116.202[.]94])
- Received: from scsga[.]com ([107.2.249[.]5])
- Received: from scsga[.]com ([173.25.235[.]195])
- Received: from scsga[.]com ([173.219.159[.]242])
- Received: from scsga[.]com ([174.141.60[.]58])
- Received: from scsga[.]com ([206.174.36[.]58])
- Received: from scsga[.]com ([209.151.132[.]206])
- Received: from scsga[.]com ([216.201.251[.]238])
- Subject: New incoming Fax from 407-046-4410
- Subject: New incoming Fax from 417-250-5487
- Subject: New incoming Fax from 421-580-6121
- Subject: New incoming Fax from 422-015-6021
- Subject: New incoming Fax from 422-187-1865
- Subject: New incoming Fax from 425-680-2708
- Subject: New incoming Fax from 426-552-1233
- Subject: New incoming Fax from 430-263-7400
- Subject: New incoming Fax from 431-231-0514
- Subject: New incoming Fax from 435-351-6605
- Subject: New incoming Fax from 442-818-5401
- Subject: New incoming Fax from 454-083-6353
- Subject: New incoming Fax from 454-166-6806
- Subject: New incoming Fax from 454-441-7340
- Subject: New incoming Fax from 456-287-1607
- Subject: New incoming Fax from 456-718-8837
- Subject: New incoming Fax from 458-613-2213
- Subject: New incoming Fax from 468-412-5488
- Subject: New incoming Fax from 475-502-0142
- Subject: New incoming Fax from 475-540-2766
- Subject: New incoming Fax from 477-862-8313
- Subject: New incoming Fax from 481-178-7060
- Subject: New incoming Fax from 483-773-1434
- Subject: New incoming Fax from 488-745-5318
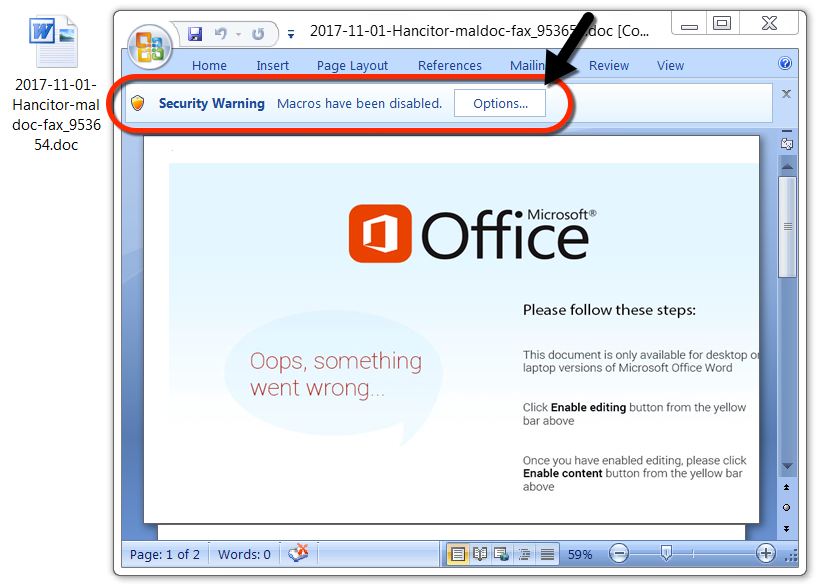
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
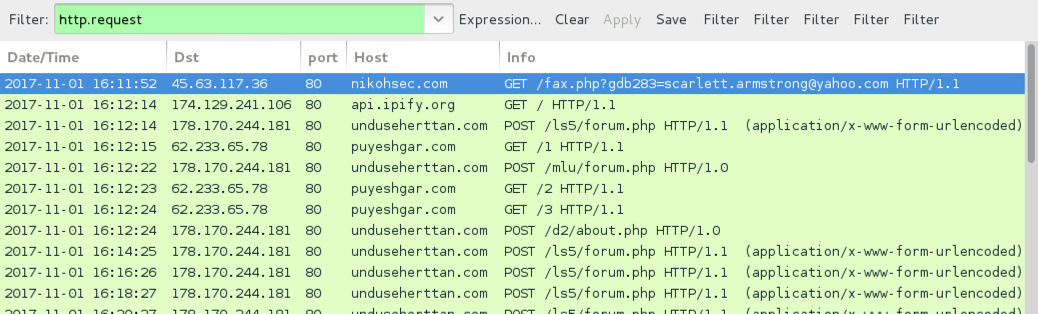
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- acehh[.]com - GET /fax.php?jue353=[recipient's email address]
- acehh[.]com - GET /fax.php?lad607=[recipient's email address]
- annapeds[.]com - GET /fax.php?iag336=[recipient's email address]
- annapeds[.]com - GET /fax.php?qdt367=[recipient's email address]
- annapeds[.]com - GET /fax.php?rny447=[recipient's email address]
- instanttaxsolutions[.]biz - GET /fax.php?srw411=[recipient's email address]
- instanttaxsolutions[.]biz - GET /fax.php?ssu260=[recipient's email address]
- instanttaxsolutions[.]biz - GET /fax.php?tre248=[recipient's email address]
- mulreninfrances[.]com - GET /fax.php?etc018=[recipient's email address]
- mulreninfrances[.]com - GET /fax.php?ruo625=[recipient's email address]
- nikohsec[.]com - GET /fax.php?ctp325=[recipient's email address]
- nikohsec[.]com - GET /fax.php?gbd283=[recipient's email address]
- nikohsec[.]com - GET /fax.php?jkb582=[recipient's email address]
- nikohsec[.]com - GET /fax.php?mhi707=[recipient's email address]
- summerill[.]biz - GET /fax.php?fgq222=[recipient's email address]
- summerill[.]biz - GET /fax.php?jnc305=[recipient's email address]
- summerill[.]biz - GET /fax.php?tif185=[recipient's email address]
- summerill[.]org - GET /fax.php?jks360=[recipient's email address]
- summerill[.]org - GET /fax.php?pga184=[recipient's email address]
- summerill[.]org - GET /fax.php?tvf326=[recipient's email address]
- summerill[.]org - GET /fax.php?uih258=[recipient's email address]
- summerill[.]org - GET /fax.php?xxf418=[recipient's email address]
- w10836dom[.]com - GET /fax.php?ujp575=[recipient's email address]
- wildwoodreunion[.]com - GET /fax.php?erg057=[recipient's email address]
NAME FOR THE MALICIOUS WORD DOCUMENT:
- fax_[six random digits].doc
POST-INFECTION TRAFFIC FROM MY INFECTED HOST:
- 45.63.117[.]36 port 80 - nikohsec[.]com - GET /fax.php?gdb283=[victim's email address]
- 178.170.244[.]181 port 80 - unduseherttan[.]com - POST /ls5/forum.php
- 178.170.244[.]181 port 80 - unduseherttan[.]com - POST /mlu/forum.php
- 178.170.244[.]181 port 80 - unduseherttan[.]com - POST /d2/about.php
- 62.233.65[.]78 port 80 - puyeshgar[.]com - GET /1
- 62.233.65[.]78 port 80 - puyeshgar[.]com - GET /2
- 62.233.65[.]78 port 80 - puyeshgar[.]com - GET /3
- 78.46.236[.]26 port 443 - tontrumuchtors[.]com - attempted TCP connections (RST from the server) caused by Zeus Panda Banker
- api.ipify[.]org - GET /
FILE HASHES
WORD DOCUMENT FROM LINK IN THE EMAIL:
- SHA256 hash: 667752cadad91de5900ec1da18b81a4ba623468d33ce7847330fbd99dba2a263
File name: fax_953654.doc
File size: 219,648 bytes
File description: Hancitor maldoc
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: daa74336508773712e6d40216490ff5a8d912950535ef9950f34318823142a35
File location: C:\Users\[username]\AppData\Roaming\[random existing path]\[random name].exe
File size: 186,368 bytes
File description: Zeus Panda Banker
Click here to return to the main page.

