2017-11-12 - "MERCURY TEXT" POPUP ON CHROME & FIREFOX PUSHES MONERO CRYPTOCURRENCY MINER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-11-12-Mercury-Text-popup-sends-Monero-coinminer.pcap.zip 2.6 MB (2,610,565 bytes)
- 2017-11-12-Mercury-Text-popup-sends-Monero-coinminer.pcap (2,835,555 bytes)
- 2017-11-12-Monero-Coinminer-malware.zip 2.4 MB (2,431,814 bytes)
- ttf.js (11,150 bytes)
- winhost.exe (2,586,112 bytes)
NOTES:
- Special thanks to @killamjr for notifying me about this.
IMAGES
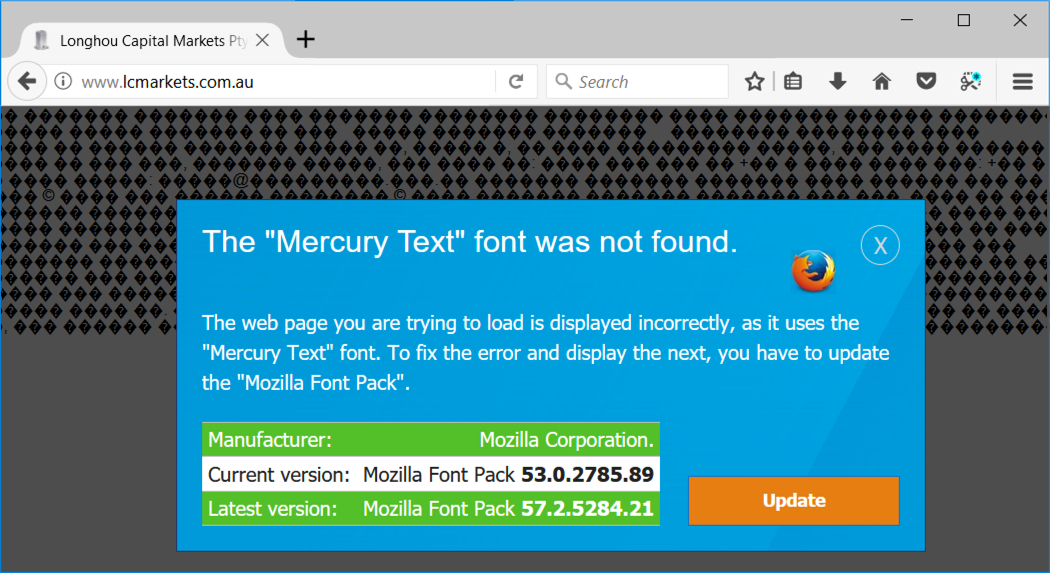
Shown above: Mercury Text popup on page from compromised site when using FireFox.
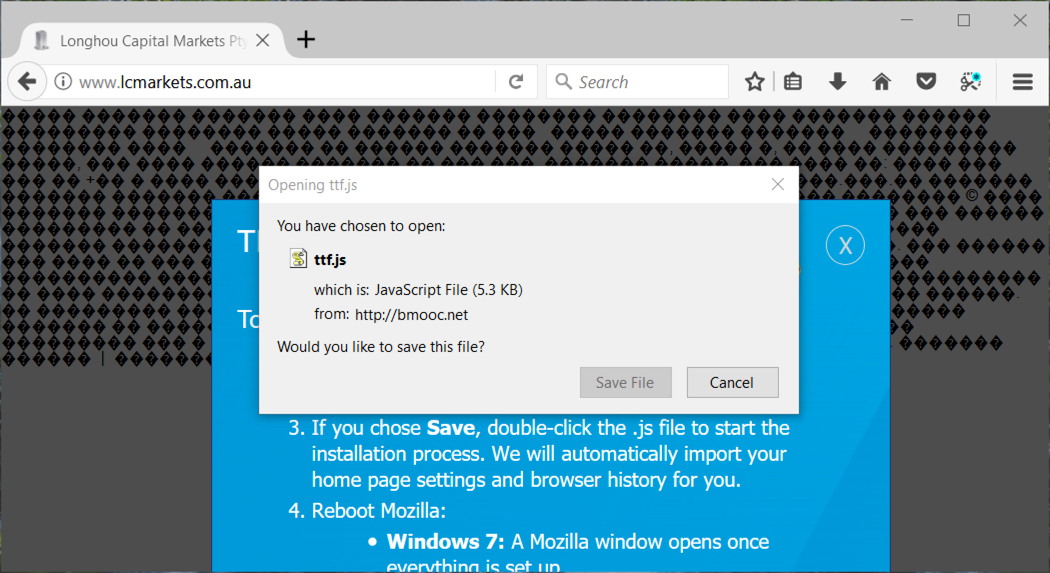
Shown above: When using FireFox, this popup sends the JavaScript (.js) file directly.
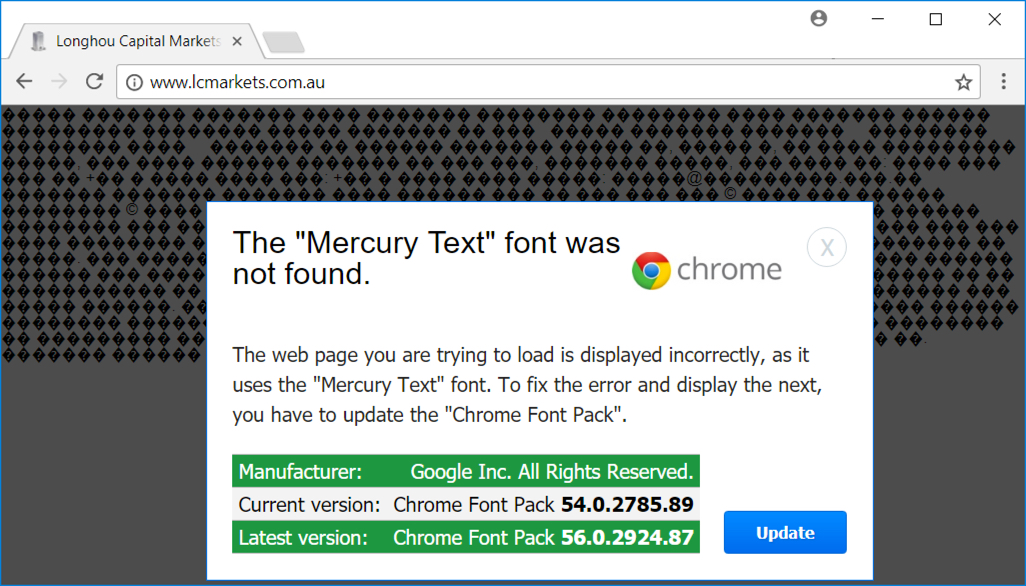
Shown above: Mercury Text popup on page from compromised site when using Chrome.
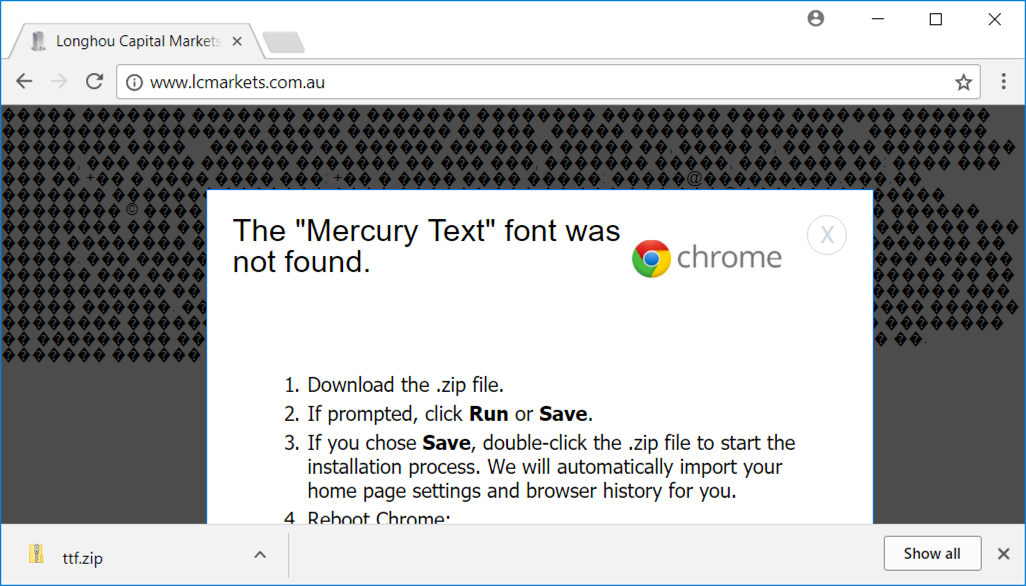
Shown above: When using Chrome, this popup sends the JavaScript (.js) in a zip archive.
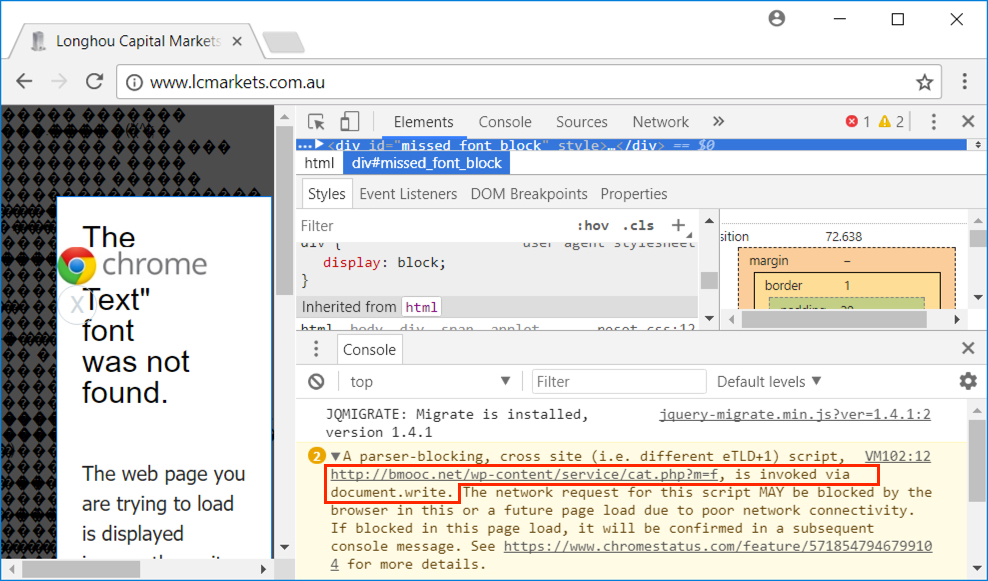
Shown above: Script displaying the Mercury Text popup isn't native to the site, but called from bmooc[.]net.
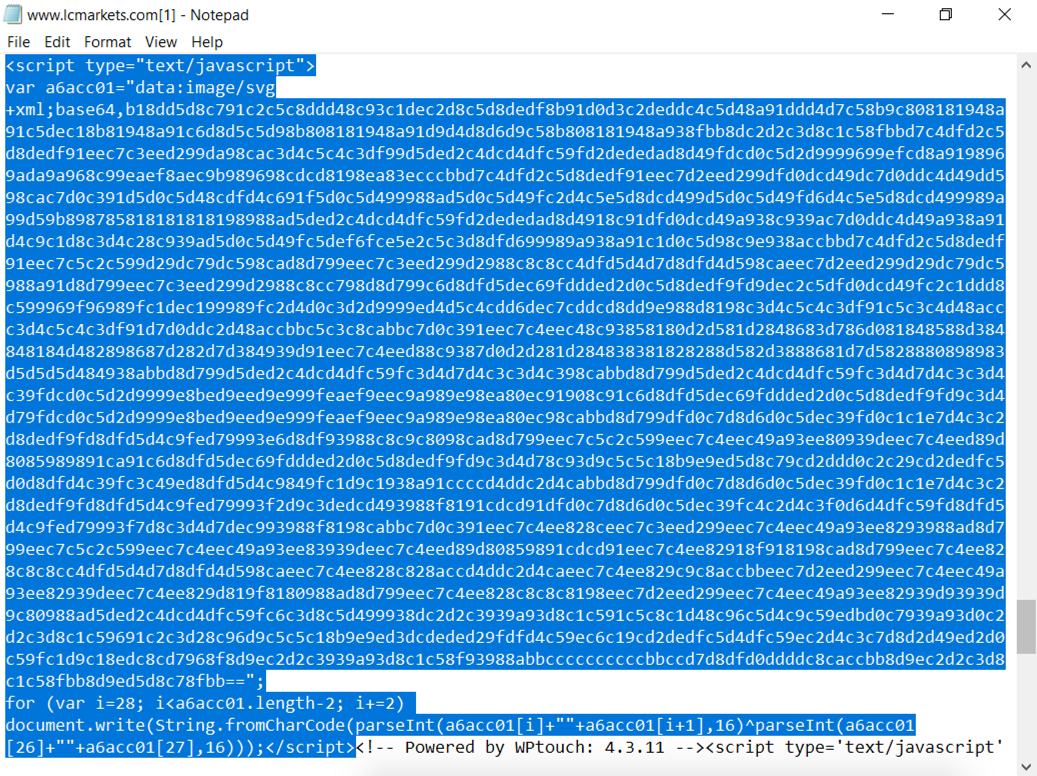
Shown above: The bmooc[.]net URL was generated through a document.write, and this is the only JavaScript I found with a document.write.
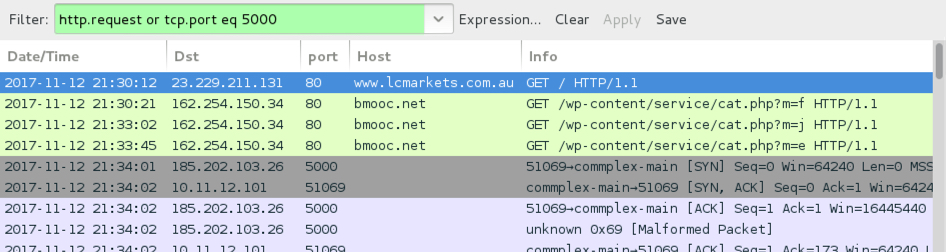
Shown above: Traffic from an infection filtered in Wireshark.

Shown above: Post-infection traffic indicates this malware is the Monero (XMR) CPU miner.
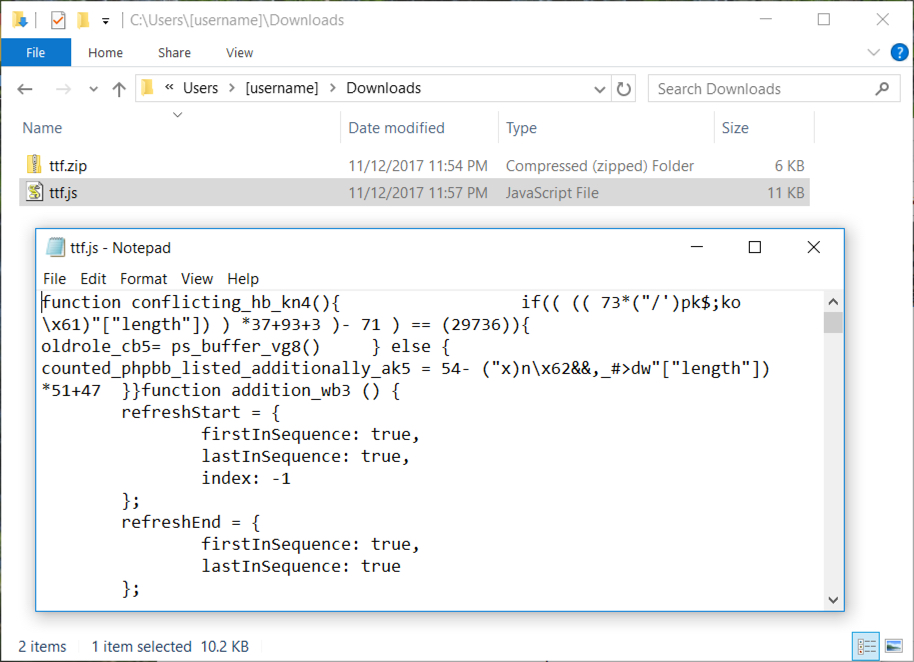
Shown above: What ttf.js looks like when extracted from the zip archive.
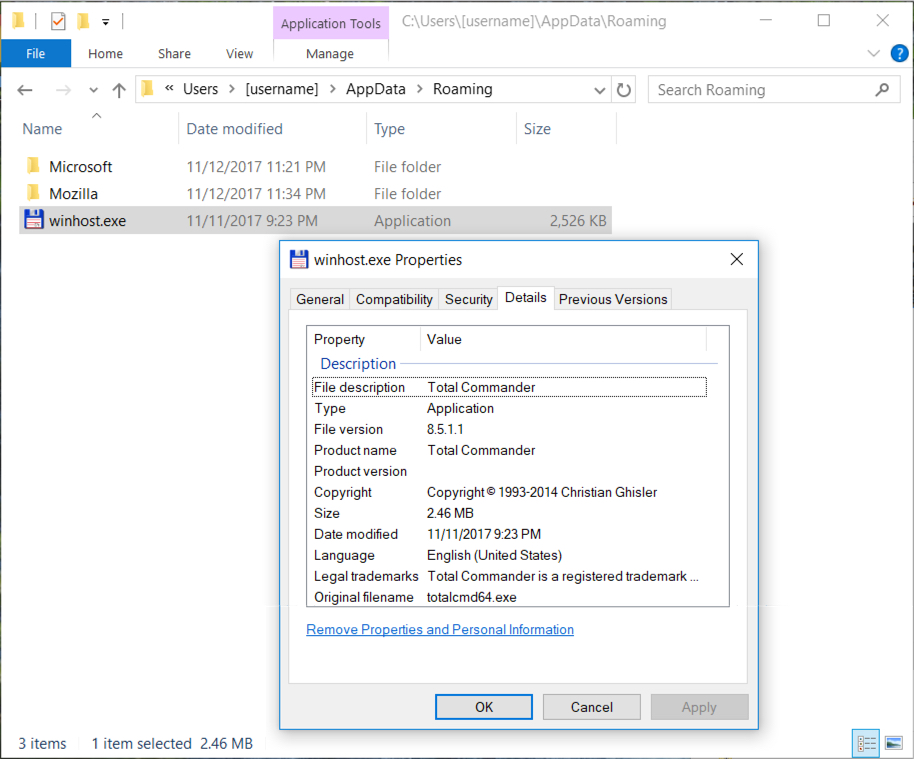
Shown above: Monero coin miner downloaded and run by the extracted .js file.
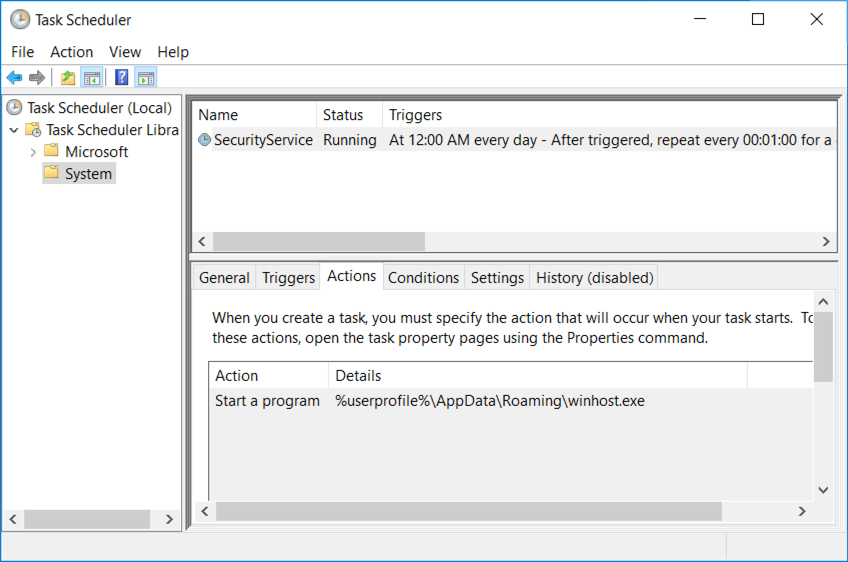
Shown above: Scheduled task making the Monero coin miner persistent on the infected host.
TRAFFIC
ASSOCIATED DOMAINS:
- www.lcmarkets[.]com[.]au - GET / [compromised site]
- 162.254.150[.]34 port 80 bmooc[.]net - GET /wp-content/service/cat.php?m=f [returned Javascript for Mercury Text popup]
- 162.254.150[.]34 port 80 bmooc[.]net - GET /wp-content/service/cat.php?m=j [returned ttf.js]
- 162.254.150[.]34 port 80 bmooc[.]net - GET /wp-content/service/cat.php?m=e [returned Monero CPU miner malware]
- 185.202.103[.]26 port 5000 - post-infection TCP traffic for Monero coin miner
MALWARE
DOWNLOADED .JS FILE (USING FIREFOX BROWSER):
- SHA256 hash: 33fced63e4209e813861c5abd18236bec68a864362bb3433791bcb38238c3bfc
File size: 11,150 bytes
File name ttf.js
MONERO (XMR) COIN MINER:
- SHA256 hash: a49ab3e7aa54532a2086ad35a08b253fc330a38803698c33c48912f7438c49a5
File size: 2,586,112
File location C:\Users\[username]\AppData\Roaming\winhost.exe
Click here to return to the main page.
