2017-11-22 - NETFLIX-THEMED PHISHING
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-11-22-Netflix-phishing-traffic.saz.zip 300.2 kB (300,218 bytes)
- 2017-11-22-Netflix-phishing-traffic.saz (307,529 bytes)
- 2017-11-22-Netflix-phishing-traffic.pcap.zip 765.8 kB (765,810 bytes)
- 2017-11-22-Netflix-phishing-traffic.pcap (848,321 bytes)
- 2017-11-22-Netflix-phishing-emails.zip 22.4 kB (22,430 bytes)
- 2017-11-22-Netflix-phishing-email-1635-UTC.txt (6,463 bytes)
- 2017-11-22-Netflix-phishing-email-1636-UTC.txt (6,461 bytes)
- 2017-11-22-Netflix-phishing-email-1654-UTC.txt (6,439 bytes)
- 2017-11-22-Netflix-phishing-email-1659-UTC.txt (6,440 bytes)
- 2017-11-22-Netflix-phishing-email-1707-UTC.txt (6,439 bytes)
- 2017-11-22-Netflix-phishing-email-1715-UTC.txt (6,440 bytes)
- 2017-11-22-Netflix-phishing-email-1728-UTC.txt (6,446 bytes)
- 2017-11-22-Netflix-phishing-email-1729-UTC.txt (6,445 bytes)
- 2017-11-22-Netflix-phishing-email-1745-UTC.txt (6,445 bytes)
- 2017-11-22-Netflix-phishing-email-1802-UTC.txt (6,440 bytes)
- 2017-11-22-Netflix-phishing-email-tracker.csv (1,951 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains:
- Anything with authorize-eu[.]com as the domain suffix. For example:
- webcmd.netflixsupport.billingupdate.authlogin.authorize-eu[.]com
EMAILS
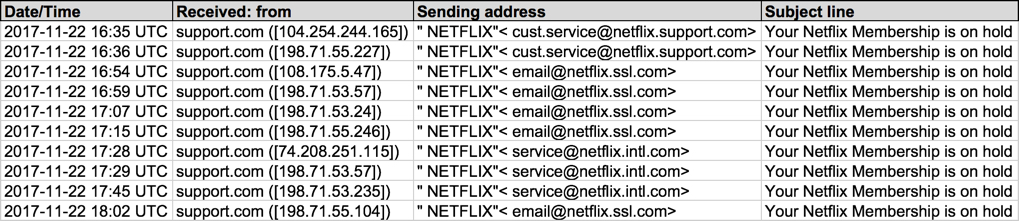
Shown above: Screenshot from the spreadsheet tracker.
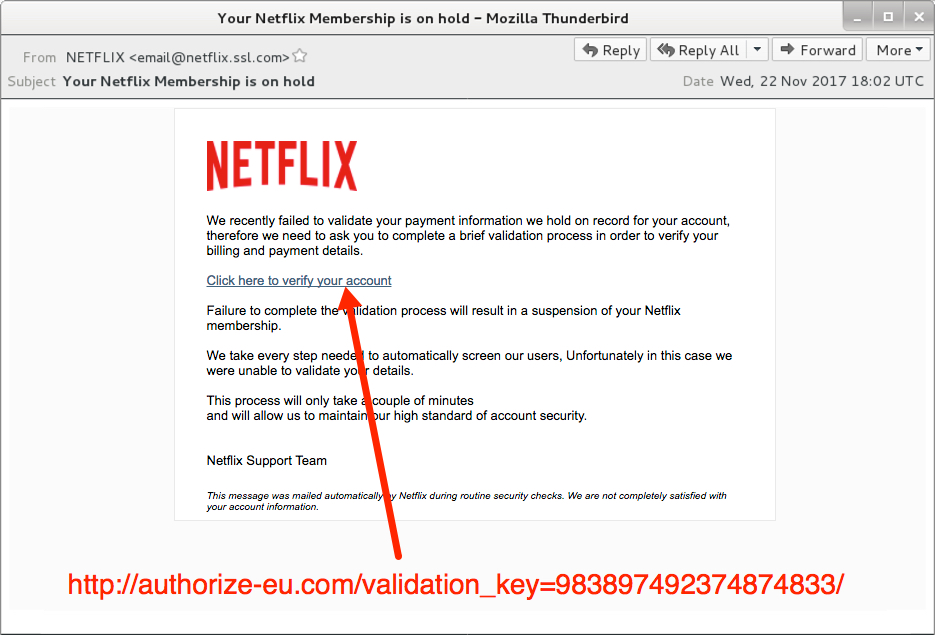
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2017-11-22 as early as 16:35 UTC through at least 18:02 UTC
- Subject: Your Netflix Membership is on hold
- From: " NETFLIX"< cust.service@netflix.support[.]com>
- From: " NETFLIX"< email@netflix.ssl[.]com>
- From: " NETFLIX"< service@netflix.intl[.]com>
TRAFFIC
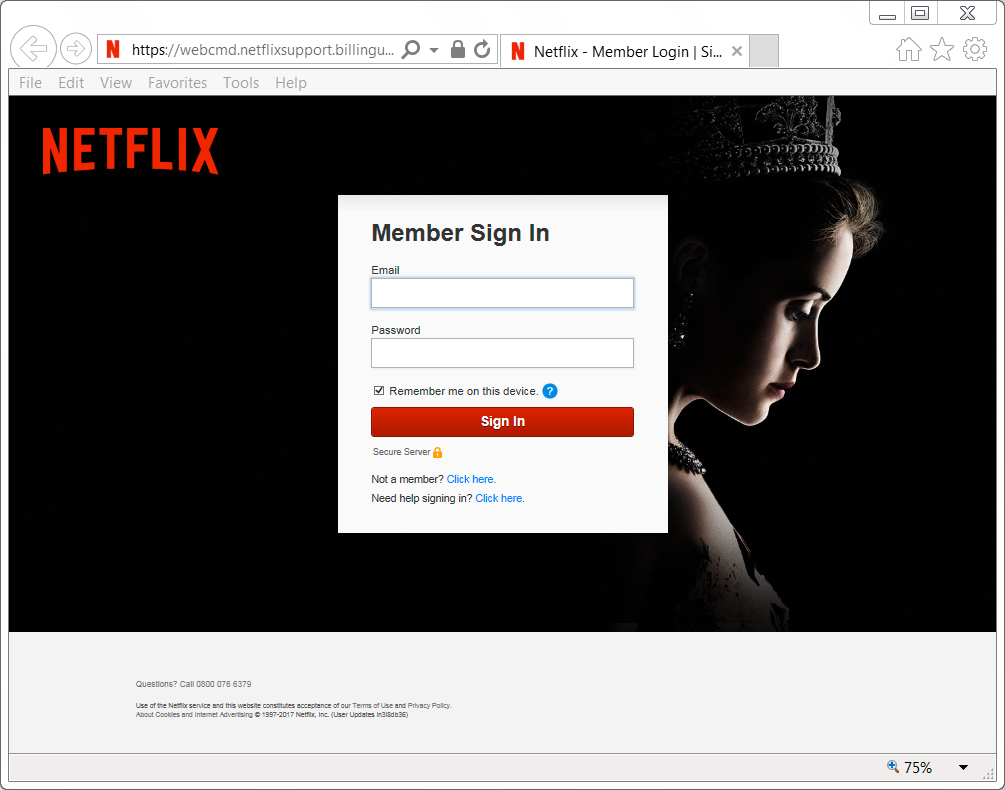
Shown above: Fake Netflix login page.
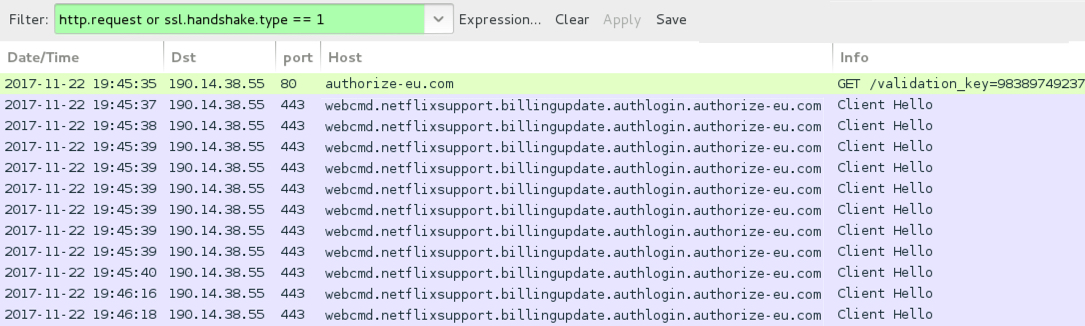
Shown above: Traffic from the infection filtered in Wireshark.
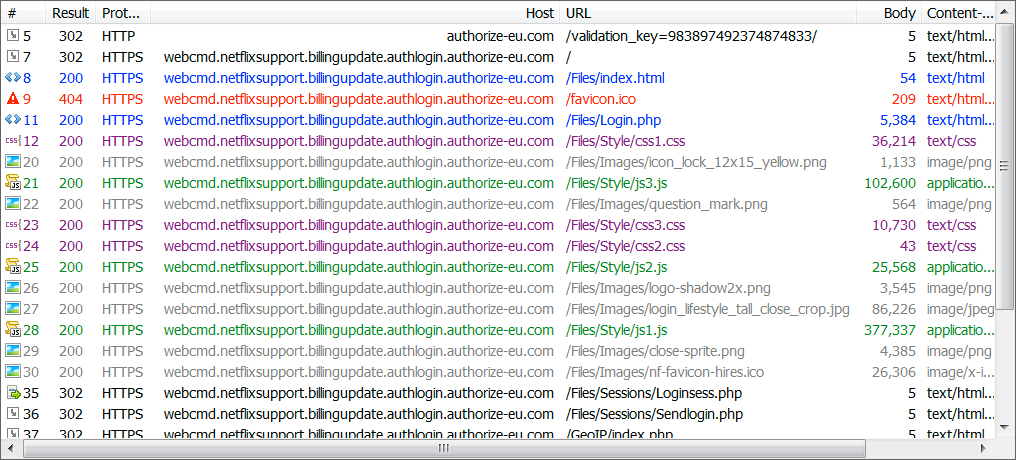
Shown above: Traffic from the infection as recorded in Fiddler.
NETWORK TRAFFIC FROM MY LAB HOST:
- 190.14.38[.]55 port 80 - authorize-eu[.]com - GET /validation_key=983897492374874833/
- 190.14.38[.]55 port 443 (HTTPS) - webcmd.netflixsupport.billingupdate.authlogin.authorize-eu[.]com - fake Netflix login site
Click here to return to the main page.
