2017-11-30 - NECURS BOTNET MALSPAM PUSHES GLOBEIMPOSTER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-11-30-Necurs-Botnet-malspam-tracker.csv.zip 1.8 kB (1,801 bytes)
- 2017-11-30-GlobeImposter-infection-traffic-2-pcaps.zip 300.6 kB (300,648 bytes)
- 2017-11-30-Necurs-Botnet-malspam-and-GlobeImposter-malware-and-artifacts.zip 1.3 MB (1,307,481 bytes)
NOTES:
- Malspam from the Necurs Botnet stopped after a brief wave on Thursday 2017-11-23.
- Necurs Botnet malspam reappeared today on Thursday 2017-11-30.
- Emails from today's wave of malspam had 7-zip attachments containing VBS files.
- These VBS files are designed to infect Windows computers with GlobeImposter ransomware.
- Saw 2 waves so far today.
- Sites hosting the GlobeImposter ransomware binaries appear to be legitimate domains that have been compromised.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//accessyouraudience[.]com/JHGcd476334?
- hxxp[:]//alucmuhendislik[.]com/JHGcd476334?
- hxxp[:]//awholeblueworld[.]com/JHGcd476334?
- hxxp[:]//bit-chasers[.]com/JHGcd476334?
- hxxp[:]//datenhaus[.]info/JHGcd476334?
- hxxp[:]//hexacam[.]com/JHGcd476334?
- hxxp[:]//mh-service[.]ru/JHGcd476334?
- hxxp[:]//yamanashi-jyujin[.]jp/JHGcd476334?
- summi[.]space
- n224ezvhg4sgyamb[.]onion[.]rip
IMAGES
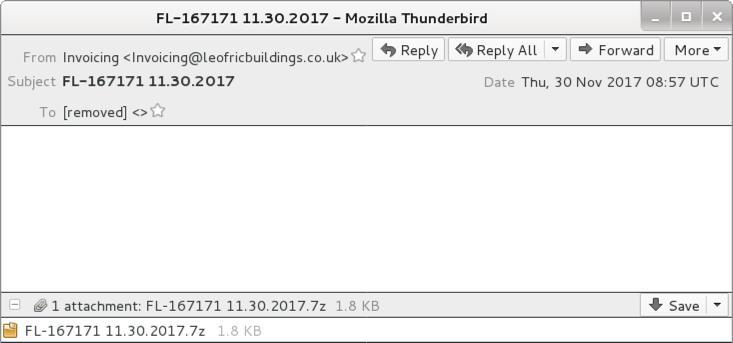
Shown above: Example of an email from the 1st wave of malspam.
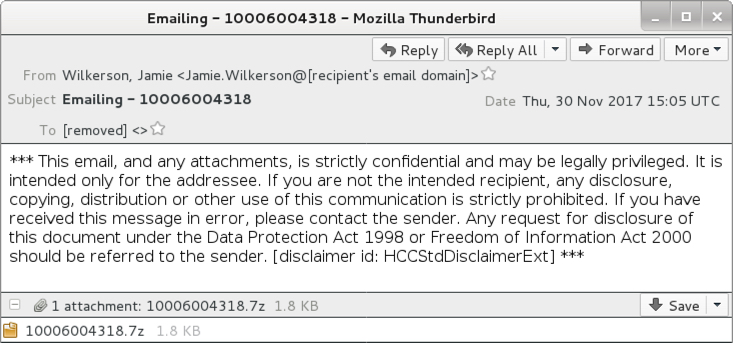
Shown above: Example of an email from the 2nd wave of malspam.
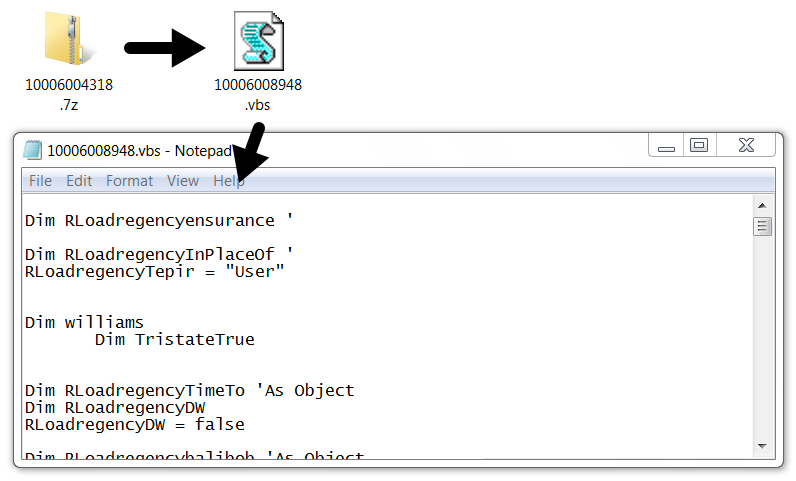
Shown above: One of the attached 7-zip archives and extracted VBS file.
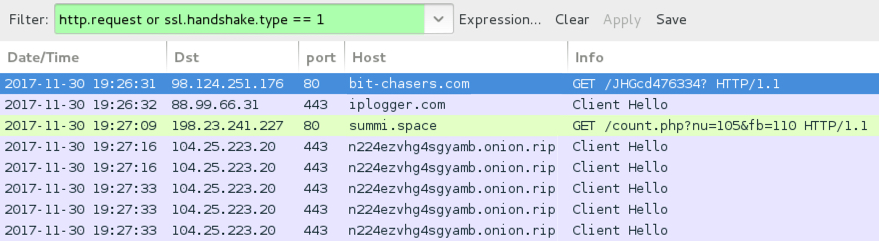
Shown above: Traffic from an infection filtered in Wireshark.
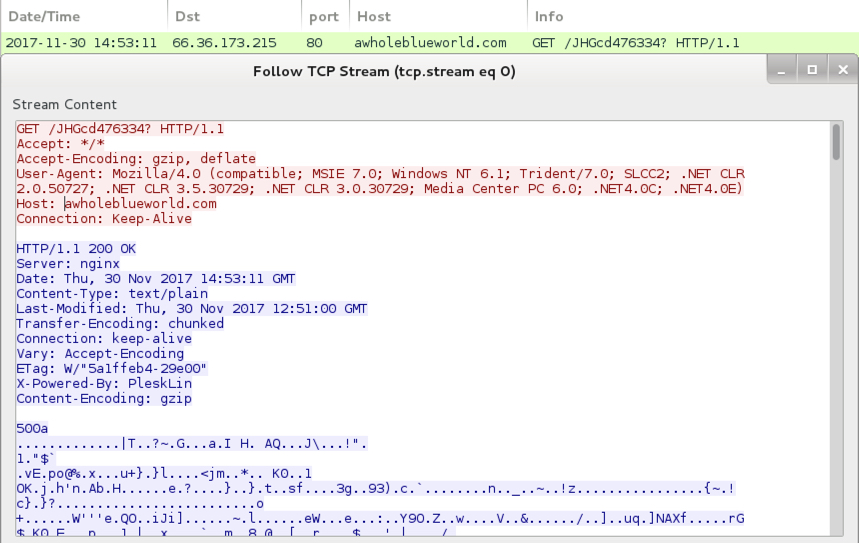
Shown above: Example of the HTTP GET request for the GlobeImposter ranosmware binary.
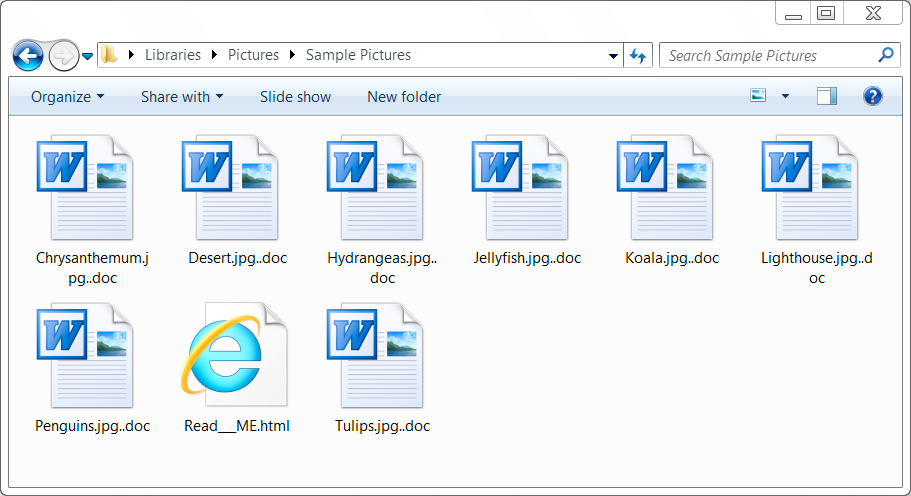
Shown above: Examples of encrypted files on an infected Windows host.
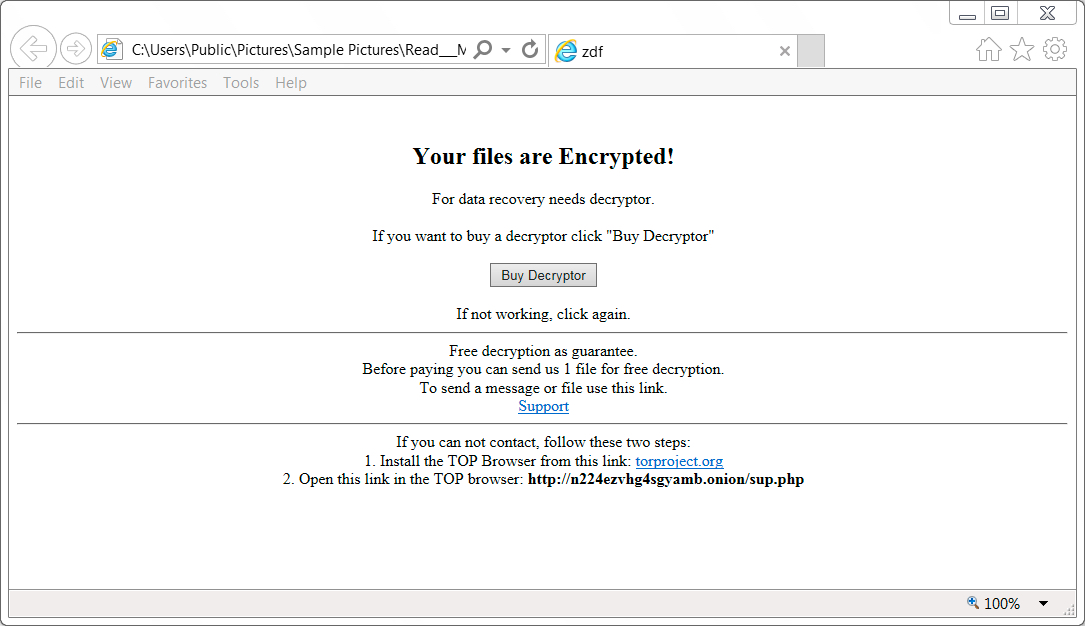
Shown above: Decryption instructions from the HTML file dropped on the infected Windows host.
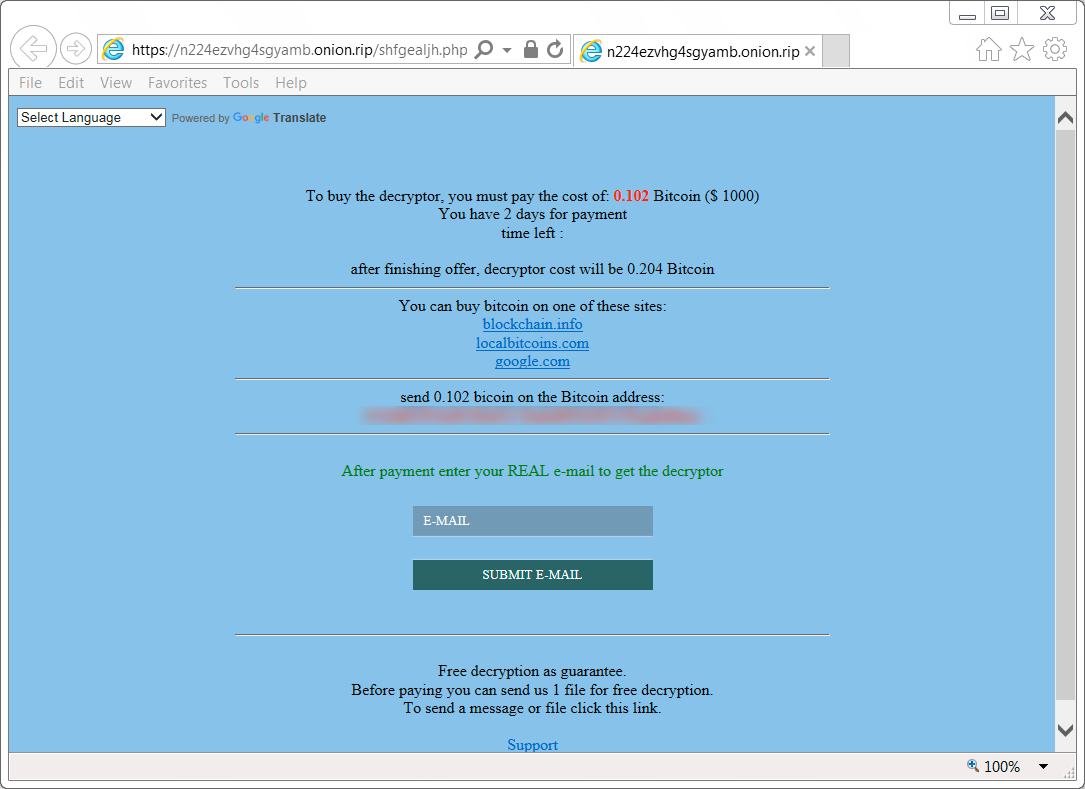
Shown above: GlobeImposter decryptor shows ransom payment as 0.102 Bitcoin ($1,000).
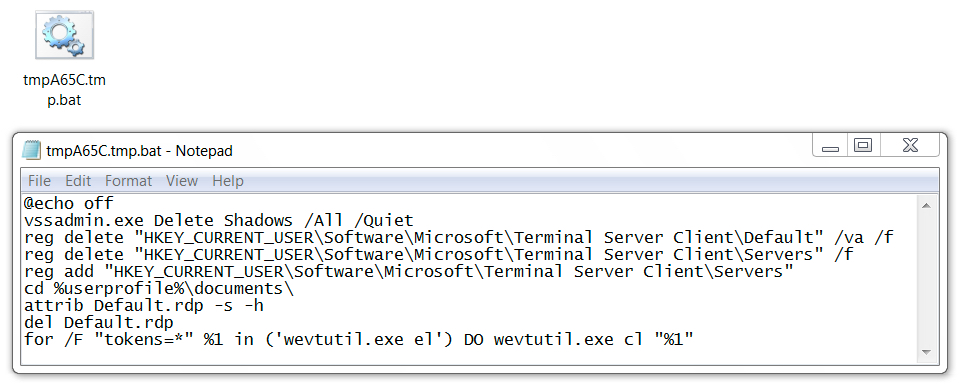
Shown above: Artifact found in the user's AppData\Local\Temp directory.
INDICATORS
EMAIL DATA:
- Date/Time: Thursday 2017-11-30 as early as 08:57 UTC through at least 20:33 UTC
- Received: from [46.217.87[.]159] ([46.217.87[.]159])
- Received: from [113.23.17[.]88] ([113.23.17[.]88])
- Received: from 77-62-238-49.southernonline[.]net ([49.238.62[.]77])
- Received: from 85.99.104[.]15.dynamic.ttnet[.]com[.]tr ([85.99.104[.]15])
- Received: from 119-40-95-122.bdcom[.]com ([119.40.95.122])
- Received: from 189-211-190-52.static.axtel[.]net ([189.211.190[.]52])
- Received: from 197-248-160-198.safaricombusiness[.]co[.]ke ([197.248.160[.]198])
- Received: from abts-north-dynamic-161.57.69[.]182.airtelbroadband[.]in ([182.69.57[.]161])
- Received: from abts-tn-dynamic-201.34.178[.]122.airtelbroadband[.]in ([122.178.34[.]201])
- Received: from bzq-79-180-175-197.red.bezeqint[.]net ([79.180.175[.]197])
- Received: from customer-ZRA-153-254.megared[.]net[.]mx ([200.92.153[.]254])
- Received: from dsl-tn-dynamic-219.246.164[.]122.airtelbroadband[.]in ([122.164.246[.]219])
- Received: from f95.zicom[.]pl ([217.70.52[.]95])
- Received: from host-197-220-22-250.iconnect[.]zm ([197.220.22[.]250])
- Received: from pppoe-46-239-40-202.teol[.]net ([46.239.41[.]218])
- Received: from smtp.ttml[.]co[.]in ([202.189.253[.]213])
- Received: from static.vnpt[.]vn ([14.236.2[.]68])
- Received: from static.vnpt[.]vn ([113.172.17[.]170])
- Received: from static.vnpt[.]vn ([113.172.167[.]15])
- Received: from static.vnpt[.]vn ([113.181.217[.]111])
- From: Invoicing <Invoicing@ambiflex[.]com>
- From: Invoicing <Invoicing@b-carpentry[.]com>
- From: Invoicing <Invoicing@bournemedia[.]co[.]uk>
- From: Invoicing <Invoicing@bruceandleslie[.]com>
- From: Invoicing <Invoicing@dorukcar[.]com>
- From: Invoicing <Invoicing@jolijtransport[.]nl>
- From: Invoicing <Invoicing@leofricbuildings[.]co[.]uk>
- From: Invoicing <Invoicing@mpatransportes[.]com[.]br>
- From: Invoicing <Invoicing@pinnacleminds[.]com[.]sg>
- From: Invoicing <Invoicing@tarragona.tinet[.]org>
- From: "Balfour, James" <James.Balfour@[recipient's email domain]>
- From: "Carew, Jana" <Jana.Carew@[recipient's email domain]>
- From: "Gillespie, Eve" <Eve.Gillespie@[recipient's email domain]>
- From: "Heigie, Gabriela" <Gabriela.Heigie@[recipient's email domain]>
- From: "Mousley, Lenore" <Lenore.Mousley@[recipient's email domain]>
- From: "Rodgers, Laurel" <Laurel.Rodgers@[recipient's email domain]>
- From: "Sire, Erin" <Erin.Sire@[recipient's email domain]>
- From: "Southward, Tabitha" <Tabitha.Southward@[recipient's email domain]>
- From: "Wilkerson, Jamie" <Jamie.Wilkerson@[recipient's email domain]>
- From: "Wooley, Shari" <Shari.Wooley@[recipient's email domain]>
- Subject: FL-063344 11.30.2017
- Subject: FL-089780 11.30.2017
- Subject: FL-167171 11.30.2017
- Subject: FL-297800 11.30.2017
- Subject: FL-374278 11.30.2017
- Subject: FL-482657 11.30.2017
- Subject: FL-614773 11.30.2017
- Subject: FL-722801 11.30.2017
- Subject: FL-881504 11.30.2017
- Subject: FL-995965 11.29.2017
- Subject: Emailing - 10006000321
- Subject: Emailing - 10006000563
- Subject: Emailing - 10006001623
- Subject: Emailing - 10006002669
- Subject: Emailing - 10006002824
- Subject: Emailing - 10006003224
- Subject: Emailing - 10006004318
- Subject: Emailing - 10006006238
- Subject: Emailing - 10006007520
- Subject: Emailing - 10006008098
SHA256 HASHES FOR THE ATTACHMENTS
- 79dfffd25ff73882f4ce6edb79867edb98a1da3b0861ae25c4d71be301d7be7b - FL-063344 11.30.2017.7z
- 33f9b1d681aaa415de76b5e2afd4b7b0c6bb8d88ea589d9c28c4aa38d3fdf2b3 - FL-089780 11.30.2017.7z
- b46cfd6d78faa01b46b038d96c0cf1ea01b285ab393f1ac24fe374687e7b294a - FL-167171 11.30.2017.7z
- 2faeb526071487c4546162bbfa818196a0aa2c1690fb88f098554f0aed82707f - FL-297800 11.30.2017.7z
- 41b03c20b4dd5f5d78482c8648e90935e202945a1248fe9d379c3fa593d2c59f - FL-374278 11.30.2017.7z
- d23c75ae4b7feaf7e5468d31e5202c690c9a57bbafc625a8fd9e54c189c0a345 - FL-482657 11.30.2017.7z
- 303ab9956ba320392fd7c6db638c11b8c3c1cd390f7a7d746edba35042b70a5d - FL-614773 11.30.2017.7z
- 47dbff4e543f925288c051ced4d4cb8e46df958f2d0b7f0e24ec84c69e9c7f36 - FL-722801 11.30.2017.7z
- 3d810fbd0c061439cbc39f0a6721d109276f40d45384473e0a6887a1d07bbee9 - FL-881504 11.30.2017.7z
- d239969c2e3c1e50d39143aedf0191c9624a61730416d8699d62f3524cfea6f3 - FL-995965 11.29.2017.7z
- 56b3e9ee6963d8c165667438705fa649714dcc7da35f73b0c857c20ce2746285 - 10006000321.7z
- 9629c342777187adc31c340bd39362c3d64f3d77438b759eebfe8385bb133f20 - 10006000563.7z
- f5c68949bee86f70a64a13369ddcb94742ad7ff950d77f9a575eee2fd195d6b0 - 10006001623.7z
- b2a608b95a390e2f15138ced6a9d8780a76efb8ca9f8ccd3c5b07c4fbf13eb81 - 10006002669.7z
- ed1409968ec53354db8b875f9ee09eaf3987a255a17fcf716edf45be3526d01b - 10006002824.7z
- ce6ce999df89a96a1da6f1cead0a1464849ae551a926a3155e64e0361c412ba5 - 10006003224.7z
- 2cac2de9a183ba2674a312fa02d233b3b72db974d487b9d9dbd3fdb90751d2db - 10006004318.7z
- f0933a393e9e15ff1698b5e0b1d921f1ab124078e96179900431d52938ba0a9c - 10006006238.7z
- b1d30537703c8222398218716eac30951931057ddd8334642a07be66da1c159a - 10006007520.7z
- 4924ee41a2e8690c462b8b672fa1de1e9dd66c718b91e707a99f1e93a46bbea2 - 10006008098.7z
SHA256 HASHES FOR THE EXTRACTED VBS FILES:
- e6ad045ab1805a6033e7ea10e3516161074a098921dcb14738d339d9786a82bd - FL-136846.vbs
- bfd840a1fdbd346bdd57be0830bdd4b8aa334e7215ba925852c08b051daddaf8 - FL-215108.vbs
- 6e93b2e18630c7fb52f84f913e8bb00ae76a9d3704985c786232bc41abdb03a5 - FL-216077.vbs
- a215021f3d80f187c31115e76b4836d86c818b02c74641e5c1c8bd3e4d9d70b4 - FL-271931.vbs
- f9be695298b75d95f9e63231062bc12e7f5e081f000d764b4fc35b5f66890765 - FL-376730.vbs
- fcd153d60aea7174bea36f29508101fde516be0f011435b0937db822c09d61f1 - FL-439831.vbs
- e123be77e7e76b07b5421b00a178d8779ebb9cfdef74ab6fed4cec4cf68a8ee6 - FL-452798.vbs
- e23c78045e816b79c4d4566c5d4af793a5c6b744bd66a80e89aa037dd4d2e284 - FL-48031.vbs
- b4c4ff6b5dffdb7865e491b74d7e9e6c857ce0592528578076303fc09081843a - FL-840996.vbs
- 52e7f4f3a0490fc14e0e0bb9f11580a6c0b1bd229d19f24566a0ebe27cf2bb95 - FL-940726.vbs
- b6f5b6cc5285f9e20fd334244dc23bdf3fcd0427ca055f20f28ffef5d8fac1b2 - 10006001670.vbs
- c896e5bfa6056ba6d0123c6173aa3041088c53531d9ce9570cbbdeea20a96f0c - 10006001835.vbs
- 5d41434105f180e9db0f6c741f70d063669941dc3b6bc44f8df94c7fed22cb61 - 10006001954.vbs
- 6556e44efebf0c7aea01913e39568b9bffdc07daf3e8f77ece23d997528d3252 - 10006002090.vbs
- 0c67cf6d78964a4340ef442d6a5e61cb1a04900466607705e2982375194c4a30 - 10006002100.vbs
- 6a7d231231f9fa867cd60099ca30af48f3bb49017eb9f16bcec33781da652037 - 10006004526.vbs
- b4e84efdd79bbbd668f02b453b474135a21797ebc75c330fb7a40a98a1b085cc - 10006005005.vbs
- 0510d80370b06c3a990f1df653772ae929e929b25766c78908cd030f060a5b00 - 10006006195.vbs
- c9ea677dea851b73a75af6b39686ab12b13c2c0fb319e8bcee7afcd4a771d8bf - 10006008030.vbs
- a1c6dcaeb3cb516122bafb10ad281694dfd1e5fe1ca4db44306decda92397058 - 10006008948.vbs
URLS FROM THE VBS FILES TO RETRIEVE GLOBEIMPOSTER RANSOMWARE:
- accessyouraudience[.]com - GET /JHGcd476334?
- alucmuhendislik[.]com - GET /JHGcd476334?
- awholeblueworld[.]com - GET /JHGcd476334?
- bit-chasers[.]com - GET /JHGcd476334?
- datenhaus[.]info - GET /JHGcd476334?
- hexacam[.]com - GET /JHGcd476334?
- mh-service[.]ru - GET /JHGcd476334?
- yamanashi-jyujin[.]jp - GET /JHGcd476334?
POST-INFECTION TRAFFIC AFTER RUNNING A VBS FILE/CHECKING DECRYPTION INSTRUCTIONS:
- port 443 (HTTPS) - iplogger[.]com - GET /ZqHJ7
- 198.23.251[.]227 port 80 - summi[.]space - GET /count.php?nu=105&fb=110
- 104.24.223[.]20 port 443 (HTTPS) - n224ezvhg4sgyamb[.]onion[.]rip - GET /shfgealjh.php
GLOBEIMPOSTER RANSOMWARE EXECUTABLES:
- SHA256 hash: a0e749b9d7015d13733a3b79904d0a80d645d07fe6b896efb8d2ed4420aacca2
- File size: 148,012 bytes
- SHA256 hash: 13e164380585fe44ac56ed10bd1ed5e42873a85040aee8c40d7596fc05f28920
- File size: 171520 bytes
OTHER INFORMATION:
- Extensions for all encrypted files: ..doc
- Ransom payment cost: 0.102 Bitcoin ($1,000 US)
Click here to return to the main page.
