2017-12-01 - FAKE ANTI-VIRUS PAGE FROM EITEST CAMPAIGN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-01-EITest-campaign-fake-av-page-traffic.pcap.zip 273.8 kB (273,756 bytes)
- 2017-12-01-EITest-campaign-fake-av-page-traffic.pcap (316,234 bytes)
- 2017-12-01-EITest-campaign-fake-av-artifacts.zip 198.8 kB (198,769 bytes)
- 2017-12-01-EITest-campaign-fake-av-page-audio.mp3 (262,144 bytes)
- 2017-12-01-EITest-campaign-fake-av-page-html.txt (9,746 bytes)
- 2017-12-01-page-from-accutech_net-with-injected-EITest-campaign-script.txt (17,843 bytes)
BACKGROUND:
- "EITest" is a long-running campaign that formerly used exploit kits to distribute malware.
- EITest is current pushing different things like fake anti-virus pages for tech support scams as shown in this blog post.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains:
- 0our0support32911[.]bid
- callinghere6301123[.]tk
TRAFFIC

Shown above: Injected script in page from compromised site.

Shown above: Network traffic filtered in Wireshark.
NETWORK TRAFFIC FROM MY LAB HOST:
- www.accutech[.]net - Legitimate, but compromised, website
- 162.244.35[.]33 port 80 - 0our0support32911[.]bid - GET /index/?MCPKV8
- 162.244.35[.]36 port 80 - callinghere6301123[.]tk - GET /?number=800-552-8162
- 162.244.35[.]36 port 80 - callinghere6301123[.]tk - GET /landinf/defender.png
- 162.244.35[.]36 port 80 - callinghere6301123[.]tk - GET /landinf/err.mp3
IMAGES
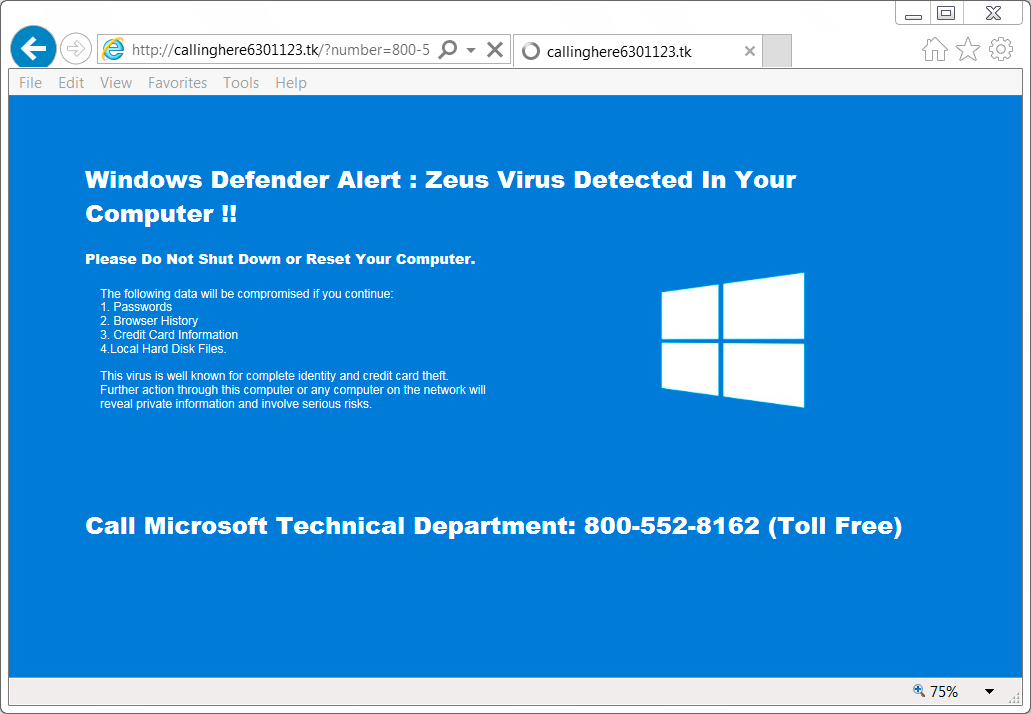
Shown above: Fake anti-virus page.

Shown above: Pop-up from fake anti-virus page.
Click here to return to the main page.
