2017-12-01 - PHISHING EMAILS FOR SHOPPING JOB AT TARGET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-01-phishing-web-page-spoofing-Target.pcap.zip 4.5 kB (4,521 bytes)
- 2017-12-01-phishing-web-page-spoofing-Target.pcap (848,321 bytes)
- 2017-12-01-phishing-emails-spoofing-Target-12-examples.zip 6.1 kB (6,081 bytes)
- 2017-12-01-header-lines-from-12-phishing-emails-spoofing-Target.txt (9,800 bytes)
- 2017-12-01-phishing-email-spoofing-Target-full-example.eml (18,706 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- hxxp[:]//www.tomtomsports[.]tech/wp-content/plugins/signup.html
- hxxp[:]//www.tomtomsports[.]tech/wp-content/plugins/variable1.php
EMAILS

Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Friday 2017-12-01 as early as 15:45 UTC through at least 17:01 UTC
- From: "Target[.]com" <career@target[.]com>
- From: "Target[.]com" <careers@target[.]com>
- From: "Target[.]com" <jobs@target[.]co>
- Subject: Job Offer
- Received: from royaweb[.]com ([88.99.109[.]55])
- Received: from mail.site2site[.]com ([52.26.213[.]196])
- Received: from toppenskrivare[.]nu ([37.233.77[.]120])
- Received: from mail.oreinlighting[.]com ([34.226.91[.]30])
- Received: from mail.blf-eps[.]de ([88.198.40[.]200])
- Received: from email01.riveroaksdental[.]local ([96.81.184[.]238])
- Received: from mail.hongyusky[.]cn ([122.96.149[.]116])
- Received: from plasse.hanyang[.]ac[.]kr ([166.104.245[.]157])
- Received: from mail.showmeinsurance[.]net ([12.196.106[.]194])
- Received: from mm.ubs.com[.]tw ([61.31.89[.]53])
- Received: from zeus.ee.kogakuin.ac[.]jp ([133.80.183[.]43])
- Received: from haywardcollision.officecentral[.]biz ([69.198.129[.]70])
TRAFFIC
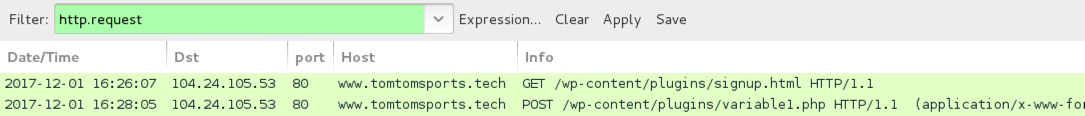
Shown above: Network traffic filtered in Wireshark.
NETWORK TRAFFIC FROM MY LAB HOST:
- 104.24.105[.]53 port 80 - www.tomtomsports[.]tech - GET /wp-content/plugins/signup.html
- 104.24.105[.]53 port 80 - www.tomtomsports[.]tech - POST /wp-content/plugins/variable1.php
IMAGES
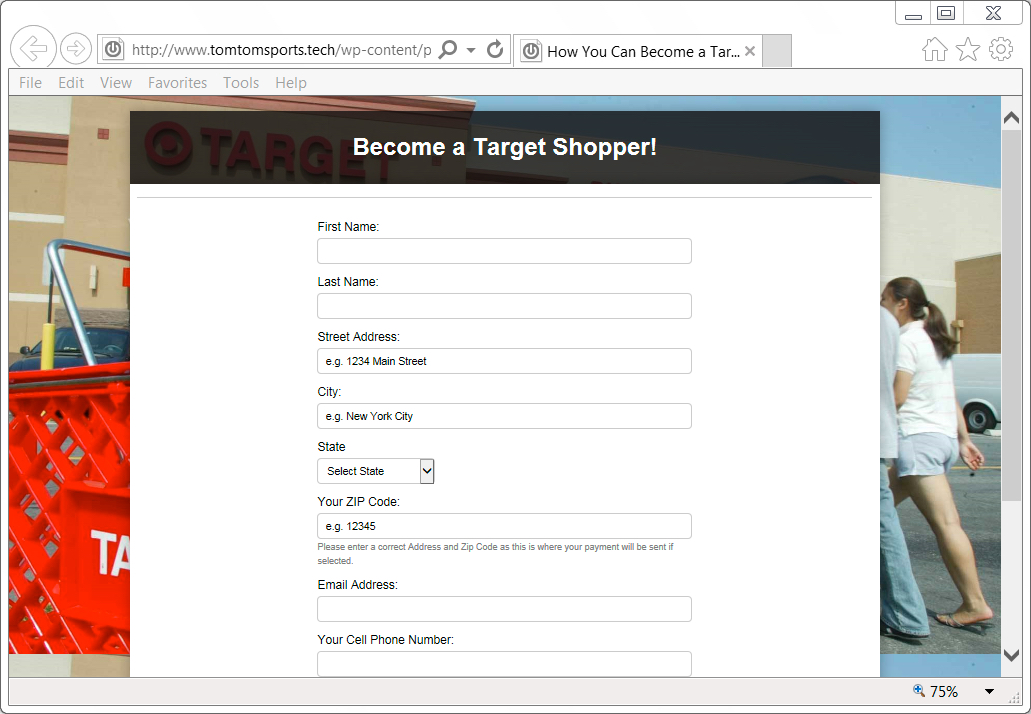
Shown above: Fake login page for Target job advertisement.
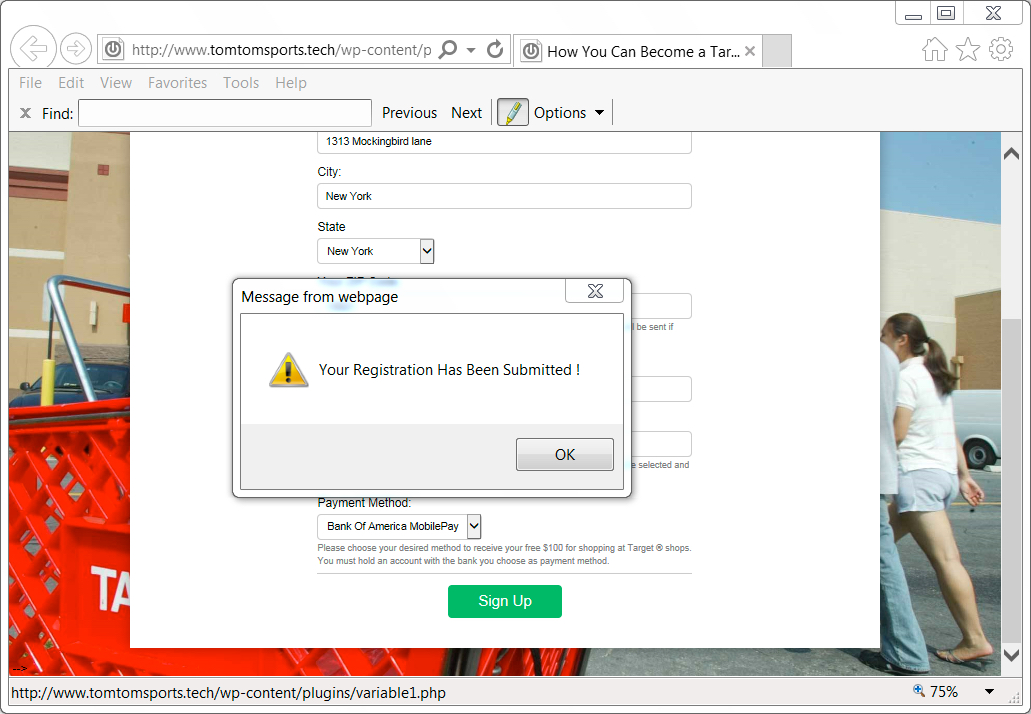
Shown above: After submitting information to the fake login page for Target job advertisement.
Click here to return to the main page.
