2017-12-06 - HANCITOR INFECTION WITH ICEDID
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-06-Hancitor-infection-with-IcedID.pcap.zip 1.0 MB (1,032,107 bytes)
- 2017-12-06-Hancitor-infection-with-IcedID.pcap (1,934,709 bytes)
- 2017-12-06-Hancitor-malspam-30-examples.txt.zip 3.7 kB (3,671 bytes)
- 2017-12-06-Hancitor-malspam-30-examples.txt (34,526 bytes)
- 2017-12-06-malware-from-Hancitor-infection.zip 695.0 kB (694,985 bytes)
- 2017-12-06-Hancitor-maldoc-invoice_491457.doc (214,528 bytes)
- 2017-12-06-IcedID-theatctaa.exe (903,168 bytes)
- 2017-12-06-binary-from-nobleduty_com.exe (825,856 bytes)
NOTES:
- Yesterday, post-infection malware from Hancitor malspam included Zeus Panda Banker. Today, it included IcedID.
- Of course, there's still Pony and Evil Pony (both fileless) being downloaded by Hancitor from the Word document macro.
- I previously documented IcedID from Hancitor malspam on 2017-11-21.
- There's another file similar to IcedID involved (same file icon), but I don't think it's a downloader this time.
- Not sure what the encoding is for the string that represents the recipient's email address in links from the malspam. It's not a Base64 string like we've seen before.
- Thanks to @James_inthe_box and @Techhelplistcom who published additional indicators that I've included in this report.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- artsforglobalpeaceandhealing[.]com
- artsforglobalpeaceandhealing[.]org
- ecocoutoure[.]com
- hrhprincessleith[.]com
- iaanetwork[.]tv
- iaanetworknews[.]com
- iaasearch[.]com
- princessleith[.]com
- princessleitheatonde-grimaldi[.]com
- princessleithofmonaco[.]com
- theartspost[.]com
- theartssearch[.]com
- theartsuniversity[.]com
- athedtburen[.]ru
- ronhingotlo[.]ru
- torsharucal[.]com
- hxxp[:]//halletts[.]com/wp-content/plugins/wp-db-backup-made/1
- hxxp[:]//halletts[.]com/wp-content/plugins/wp-db-backup-made/2
- hxxp[:]//halletts[.]com/wp-content/plugins/wp-db-backup-made/3
- hxxp[:]//mebelucci[.]com[.]ua/wp-content/plugins/bwp-google-xml-sitemaps/1
- hxxp[:]//mebelucci[.]com[.]ua/wp-content/plugins/bwp-google-xml-sitemaps/2
- hxxp[:]//mebelucci[.]com[.]ua/wp-content/plugins/bwp-google-xml-sitemaps/3
- hxxp[:]//mutznutzpetcare[.]com/wp-content/plugins/category-posts/1
- hxxp[:]//mutznutzpetcare[.]com/wp-content/plugins/category-posts/2
- hxxp[:]//mutznutzpetcare[.]com/wp-content/plugins/category-posts/3
- hxxp[:]//sgs36[.]ru/wp-content/plugins/lightbox-plus/1
- hxxp[:]//sgs36[.]ru/wp-content/plugins/lightbox-plus/2
- hxxp[:]//sgs36[.]ru/wp-content/plugins/lightbox-plus/3
- hxxp[:]//utilitia[.]com/wp-content/plugins/custom-post-type-ui/1
- hxxp[:]//utilitia[.]com/wp-content/plugins/custom-post-type-ui/2
- hxxp[:]//utilitia[.]com/wp-content/plugins/custom-post-type-ui/3
- camorata[.]com
- excelano[.]net
- dorothyle[.]net
- nobleduty[.]com
EMAILS
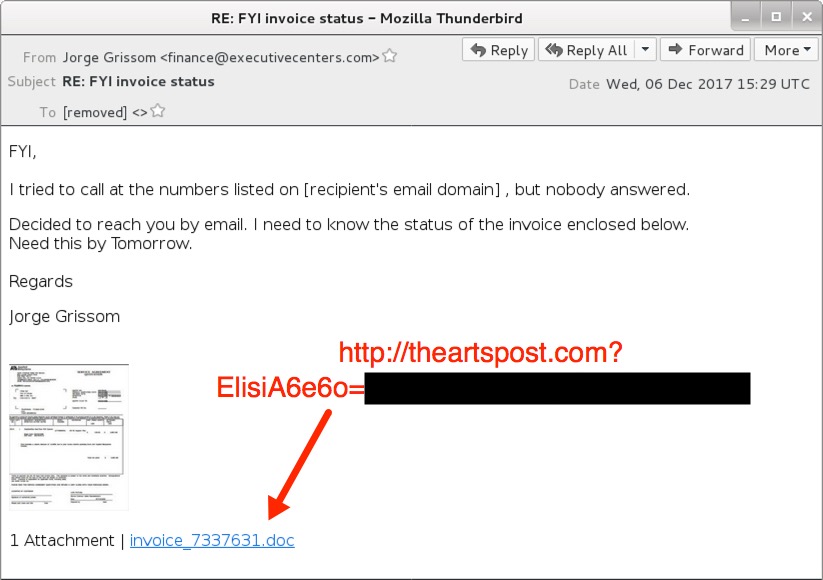
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2017-12-06 as early as 15:29 UTC through at least 19:48 UTC
- Subject: RE: FYI invoice status
- From: "[random first and last names]" <finance@executivecenters[.]com>
- Received: from executivecenters[.]com ([12.154.171[.]180])
- Received: from executivecenters[.]com ([23.31.1[.]70])
- Received: from executivecenters[.]com ([24.18.144[.]193])
- Received: from executivecenters[.]com ([24.153.220[.]106])
- Received: from executivecenters[.]com ([24.172.35[.]186])
- Received: from executivecenters[.]com ([64.60.9[.]115])
- Received: from executivecenters[.]com ([64.61.172[.]230])
- Received: from executivecenters[.]com ([68.188.200[.]115])
- Received: from executivecenters[.]com ([69.68.213[.]2])
- Received: from executivecenters[.]com ([71.9.102[.]11])
- Received: from executivecenters[.]com ([71.12.100[.]6])
- Received: from executivecenters[.]com ([74.93.156[.]78])
- Received: from executivecenters[.]com ([76.237.148[.]143])
- Received: from executivecenters[.]com ([96.40.51[.]123])
- Received: from executivecenters[.]com ([96.82.114[.]57])
- Received: from executivecenters[.]com ([96.83.60[.]30])
- Received: from executivecenters[.]com ([104.136.18[.]139])
- Received: from executivecenters[.]com ([107.11.97[.]242])
- Received: from executivecenters[.]com ([142.176.85[.]144])
- Received: from executivecenters[.]com ([162.222.234[.]]111])
- Received: from executivecenters[.]com ([173.8.67[.]169])
- Received: from executivecenters[.]com ([173.14.210[.]225])
- Received: from executivecenters[.]com ([184.169.59[.]9])
- Received: from executivecenters[.]com ([190.25.45[.]116])
- Received: from executivecenters[.]com ([201.229.68[.]245])
- Received: from executivecenters[.]com ([208.245.21[.]68])
- Received: from executivecenters[.]com ([216.164.4[.]50])
- Received: from executivecenters[.]com ([216.174.138[.]18])
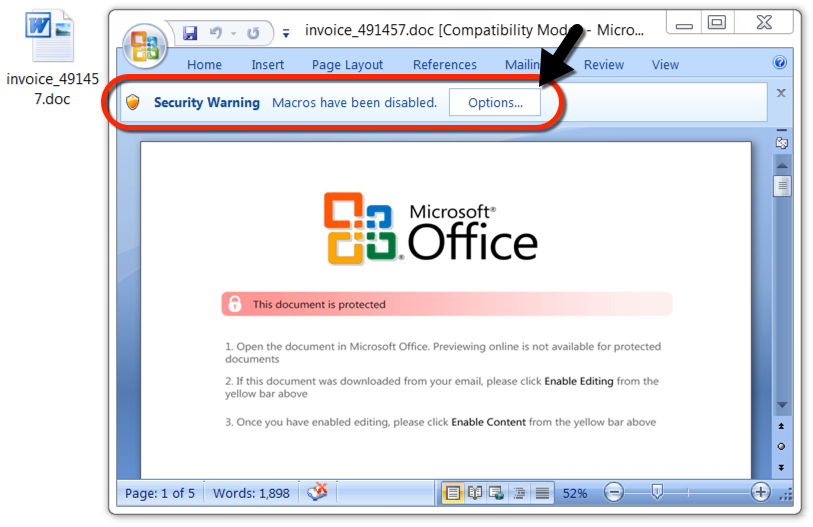
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
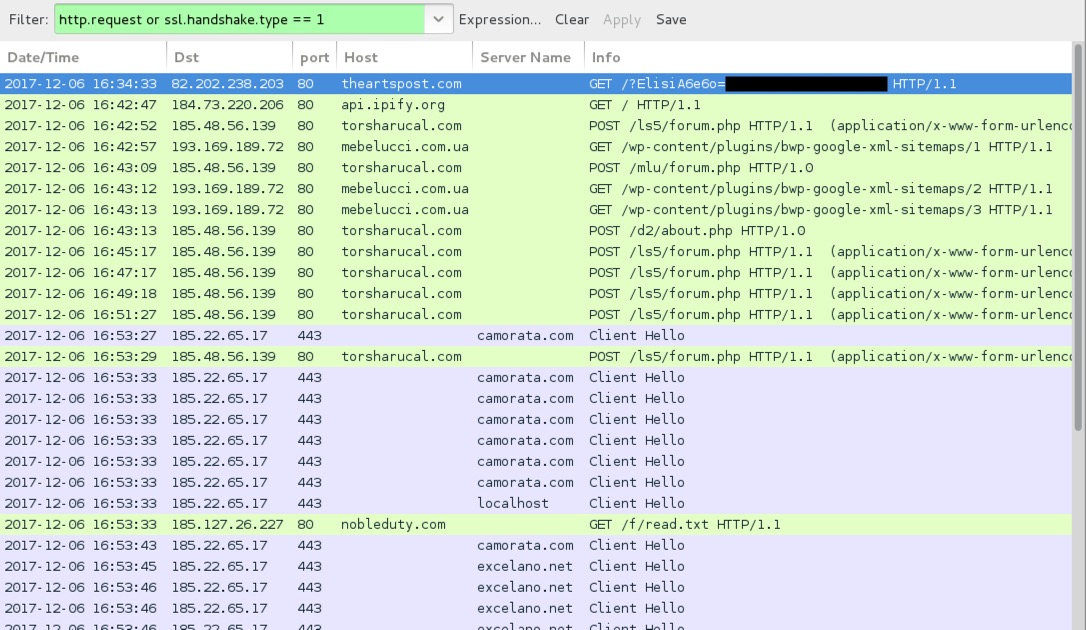
Shown above: Traffic from the infection filtered in Wireshark.

Shown above: Some alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro ruleset.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- hxxp[:]//artsforglobalpeaceandhealing[.]com?NAb47u34E7XuyXe68v=[encoded string representing recipient's email address]
- hxxp[:]//artsforglobalpeaceandhealing[.]com?oQImm5wem6ox2=[encoded string representing recipient's email address]
- hxxp[:]//artsforglobalpeaceandhealing[.]org?4ukqo3E5Ork0nas=[encoded string representing recipient's email address]
- hxxp[:]//artsforglobalpeaceandhealing[.]org?cvt4Q66EXmNu26JUb=[encoded string representing recipient's email address]
- hxxp[:]//ecocoutoure[.]com?xR7AJ43vObbAEQEzu=[encoded string representing recipient's email address]
- hxxp[:]//hrhprincessleith[.]com?2r1n0I2277=[encoded string representing recipient's email address]
- hxxp[:]//hrhprincessleith[.]com?Gd45D0EG=[encoded string representing recipient's email address]
- hxxp[:]//hrhprincessleith[.]com?i008MIfOIL=[encoded string representing recipient's email address]
- hxxp[:]//hrhprincessleith[.]com?w0Y64121C5uVY=[encoded string representing recipient's email address]
- hxxp[:]//hrhprincessleith[.]com?WQ24=[encoded string representing recipient's email address]
- hxxp[:]//iaanetwork[.]tv?E3clUSC8o6AfA42=[encoded string representing recipient's email address]
- hxxp[:]//iaanetwork[.]tv?T8mFyUD6Qn70yZUO=[encoded string representing recipient's email address]
- hxxp[:]//iaanetworknews[.]com?PkynM35oxA=[encoded string representing recipient's email address]
- hxxp[:]//iaasearch[.]com?4UuiH3040oQJ0=[encoded string representing recipient's email address]
- hxxp[:]//iaasearch[.]com?cYu3s8S8pUpu014=[encoded string representing recipient's email address]
- hxxp[:]//iaasearch[.]com?dHYHiy1a61UU0=[encoded string representing recipient's email address]
- hxxp[:]//iaasearch[.]com?ILmOP2=[encoded string representing recipient's email address]
- hxxp[:]//iaasearch[.]com?oIu=[encoded string representing recipient's email address]
- hxxp[:]//princessleith[.]com?82ae0F4bEU43T5=[encoded string representing recipient's email address]
- hxxp[:]//princessleith[.]com?FPl62ideBmy6azE6oe=[encoded string representing recipient's email address]
- hxxp[:]//princessleith[.]com?M723p=[encoded string representing recipient's email address]
- hxxp[:]//princessleitheatonde-grimaldi[.]com?JA2cO3Ey6=[encoded string representing recipient's email address]
- hxxp[:]//princessleithofmonaco[.]com?8JINjpco2hJN=[encoded string representing recipient's email address]
- hxxp[:]//princessleithofmonaco[.]com?ZL1O7d23Lq=[encoded string representing recipient's email address]
- hxxp[:]//theartspost[.]com?06e0A5PoP2Ith8t=[encoded string representing recipient's email address]
- hxxp[:]//theartspost[.]com?7EL7OXDb6lmy8=[encoded string representing recipient's email address]
- hxxp[:]//theartspost[.]com?ElisiA6e6o=[encoded string representing recipient's email address]
- hxxp[:]//theartssearch[.]com?iri0uI2gUces=[encoded string representing recipient's email address]
- hxxp[:]//theartssearch[.]com?M00=[encoded string representing recipient's email address]
- hxxp[:]//theartsuniversity[.]com?OgWYIRY54H7UK71=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM MY INFECTED LAB HOST:
- 82.202.238[.]203 port 80 - theartspost[.]com - GET /?ElisiA6e6o=[encoded string representing recipient's email address]
- api.ipify[.]org - GET / [IP address check by the infected Windows host]
- 185.48.56[.]139 port 80 - torsharucal[.]com - POST /ls5/forum.php
- 185.48.56[.]139 port 80 - torsharucal[.]com - POST /mlu/forum.php
- 185.48.56[.]139 port 80 - torsharucal[.]com - POST /d2/about.php
- 193.169.189[.]72 port 80 - mebelucci[.]com[.]ua - GET /wp-content/plugins/bwp-google-xml-sitemaps/1
- 193.169.189[.]72 port 80 - mebelucci[.]com[.]ua - GET /wp-content/plugins/bwp-google-xml-sitemaps/2
- 193.169.189[.]72 port 80 - mebelucci[.]com[.]ua - GET /wp-content/plugins/bwp-google-xml-sitemaps/3
- 185.22.65[.]17 port 443 - camorata[.]com - HTTPS/SSL/TLS traffic associated with IcedID
- 185.22.65[.]17 port 443 - localhost - HTTPS/SSL/TLS traffic associated with IcedID
- 185.127.26.]227 port 80 - nobleduty[.]com - GET /f/read.txt [returned Windows exectuable]
- 185.22.65[.]17 port 443 - excelano[.]net - HTTPS/SSL/TLS traffic associated with IcedID
FILE HASHES
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 39e5933d46bcdc90baeee09b4ea2419f872cfce5ff7b64f0dbabd13372d4067c
File size: 214,528 bytes
File name: invoice_[6 random digits].doc
File description: Word document with macro for Hancitor
- SHA256 hash: 0817708eea27bc52e6fc60dc61730c47554d759a917485eefecded8db76746d4
File size: 903,168 bytes
File location: C:\Users\[username]\AppData\Local\Temp\BN87E4.tmp
File location: C:\Users\[username]\AppData\Local\hemansgol\theatctaa.exe
File description: Wubdiws EXE for IcedID
- SHA256 hash: 2e743c85b9cb9c28be19d7d5a945fafa9f4663c2e7615bef7378136dcbf2f6eb
File size: 825,856 bytes
File location: hxxp[:]//nobleduty[.]com/f/read.txt
File description: Windows EXE, possibly related to the IcedID infection
IMAGES
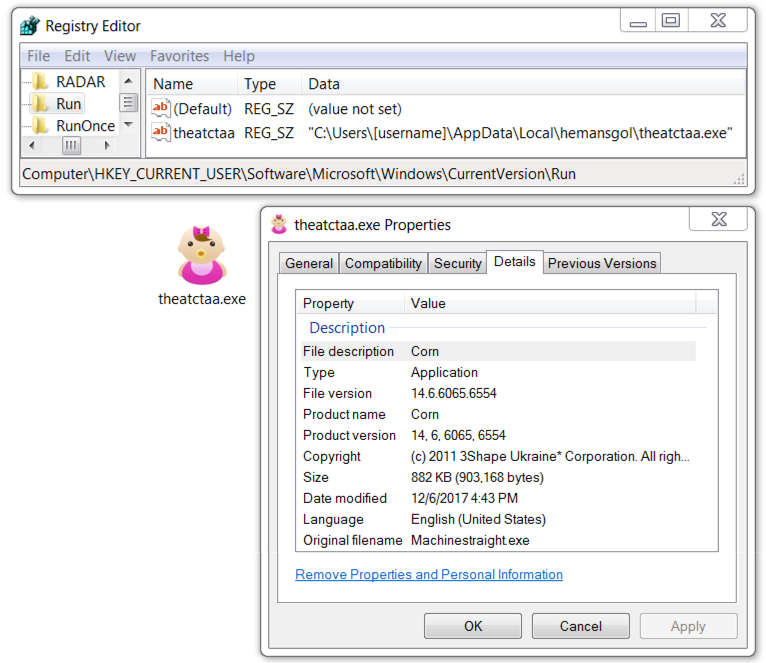
Shown above: IceID persistent on the infected Windows host.
Click here to return to the main page.
