2017-12-11 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-11-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 1.8 MB (1,801,555 bytes)
- 2017-12-11-Hancitor-infection-with-Zeus-Panda-Banker.pcap (2,364,151 bytes)
- 2017-12-11-Hancitor-malspam-1654-UTC.eml.zip 1.1 kB (1,077 bytes)
- 2017-12-11-Hancitor-malspam-1654-UTC.eml (2,767 bytes)
- 2017-12-11-malware-from-Hancitor-infection.zip 215.3 kB (215,280 bytes)
- 2017-12-11-Hancitor-maldoc-eFax_729569.doc (40,128 bytes)
- 2017-12-11-Zeus-Panda-Banker-sample.exe (152,064 bytes)
NOTES:
- Today, post-infection malware from Hancitor malspam includes Zeus Panda Banker.
- It's been switching between Zeus Panda Banker and IcedID during the past two weeks or so.
- Of course, there's still Pony and Evil Pony (both fileless) also downloaded by Hancitor from the Word document macro.
- Thanks to @James_inthe_box, who published additional indicators (link) that I've included in this report.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- agelessbuy[.]com
- agelessshow[.]com
- beautyandthearts[.]org
- buyoesh[.]com
- iaaaward[.]com
- iaapublishing[.]com
- iaasavesthearts[.]com
- oesh[.]org
- oeshshoes[.]com
- oeshshoes[.]net
- wearoesh[.]com
- hxxp[:]//aboutthebike[.]co[.]uk/wp-content/plugins/all-in-one-seo-pack/1
- hxxp[:]//aboutthebike[.]co[.]uk/wp-content/plugins/all-in-one-seo-pack/2
- hxxp[:]//aboutthebike[.]co[.]uk/wp-content/plugins/all-in-one-seo-pack/3
- hxxp[:]//beyondthebag.feedprojects[.]com/wp-content/plugins/featured-image-widget/1
- hxxp[:]//beyondthebag.feedprojects[.]com/wp-content/plugins/featured-image-widget/2
- hxxp[:]//beyondthebag.feedprojects[.]com/wp-content/plugins/featured-image-widget/3
- hxxp[:]//modelhover[.]org/1
- hxxp[:]//modelhover[.]org/2
- hxxp[:]//modelhover[.]org/3
- hxxp[:]//sterrenburgvanduijn[.]nl/wp-content/plugins/gallery-bank/1
- hxxp[:]//sterrenburgvanduijn[.]nl/wp-content/plugins/gallery-bank/2
- hxxp[:]//sterrenburgvanduijn[.]nl/wp-content/plugins/gallery-bank/3
- hxxp[:]//www.nationejobs[.]com/campaign/1
- hxxp[:]//www.nationejobs[.]com/campaign/2
- hxxp[:]//www.nationejobs[.]com/campaign/3
- butenrestold[.]com
- hadrecrolof[.]ru
- goonronto[.]ru
- aningtorsfave[.]com
EMAILS
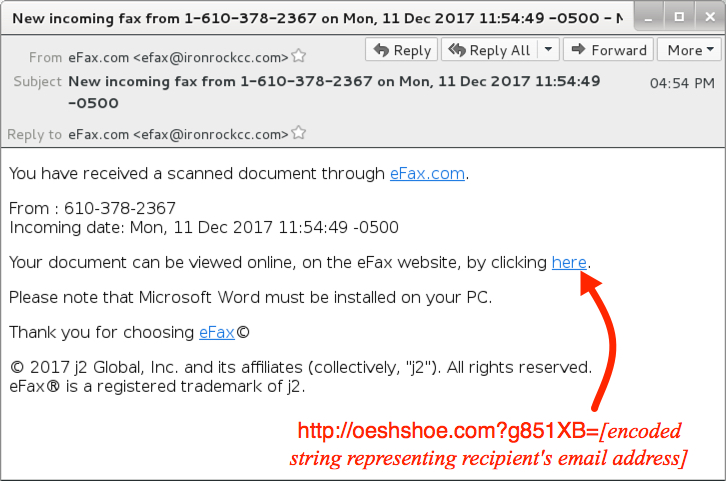
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Received: from ironrockcc[.]com ([168.111.104.[153]
- Date/Time: Monday 2017-12-11 at 16:54 UTC
- Subject: New incoming fax from 1-610-378-2367 on Mon, 11 Dec 2017 11:54:49 -0500
- From (spoofed): "eFax.com" <efax@ironrockcc[.]com>
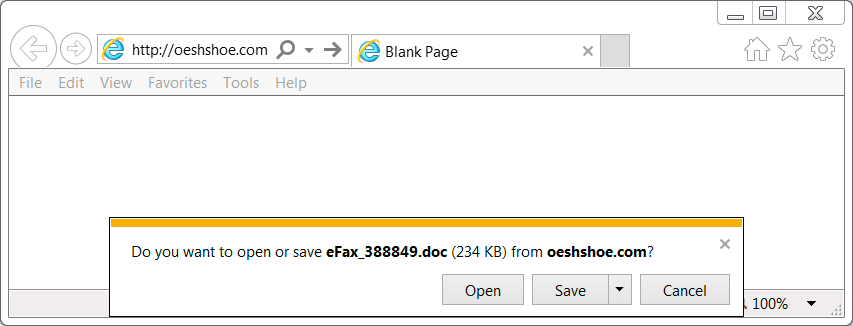
Shown above: Clicking on link from the email.
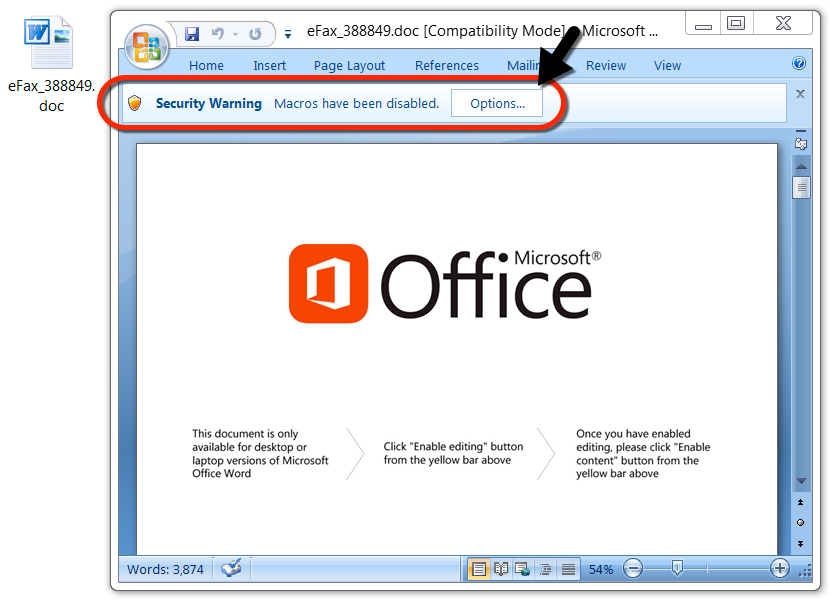
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
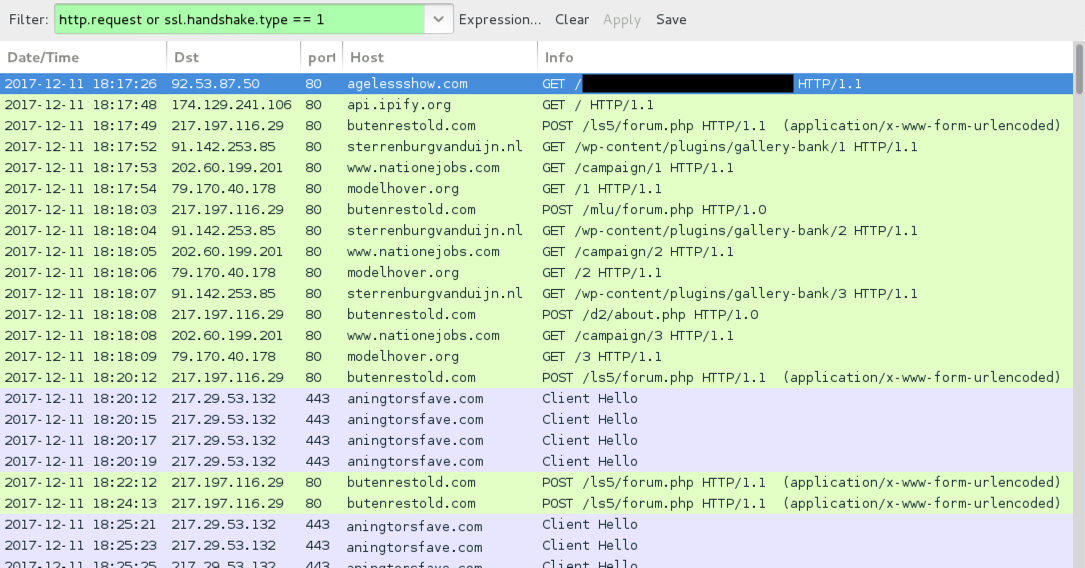
Shown above: Traffic from an infection filtered in Wireshark.
DOMAINS FROM LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- hxxp[:]//agelessbuy[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//agelessshow[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//beautyandthearts[.]org/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//buyoesh[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//iaaaward[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//iaapublishing[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//iaasavesthearts[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//oesh[.]org/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//oeshshoes[.]com/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//oeshshoes[.]net/?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//wearoesh[.]com/?[encoded string]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM MY INFECTED LAB HOST:
- 92.53.87[.]50 port 80 - agelessshow[.]com - GET /?[encoded string]=[encoded string representing recipient's email address]
- api.ipify[.]org - GET / [IP address check by the infected Windows host]
- 217.197.116[.]29 port 80 - butenrestold[.]com - POST /ls5/forum.php
- 217.197.116[.]29 port 80 - butenrestold[.]com - POST /mlu/forum.php
- 217.197.116[.]29 port 80 - butenrestold[.]com - POST /d2/about.php
- 91.142.253[.]85 port 80 - sterrenburgvanduijn[.]nl - GET /wp-content/plugins/gallery-bank/1
- 91.142.253[.]85 port 80 - sterrenburgvanduijn[.]nl - GET /wp-content/plugins/gallery-bank/2
- 91.142.253[.]85 port 80 - sterrenburgvanduijn[.]nl - GET /wp-content/plugins/gallery-bank/3
- 202.60.199[.]201 port 80 - www.nationejobs[.]com - GET /campaign/1
- 202.60.199[.]201 port 80 - www.nationejobs[.]com - GET /campaign/2
- 202.60.199[.]201 port 80 - www.nationejobs[.]com - GET /campaign/3
- 79.170.40[.]178 port 80 - modelhover[.]org - GET /1
- 79.170.40[.]178 port 80 - modelhover[.]org - GET /2
- 79.170.40[.]178 port 80 - modelhover[.]org - GET /3
- 217.29.53[.]132 port 443 - aningtorsfave[.]com - HTTPS/SSL/TLS traffic associated with Zeus Panda Banker
FILE HASHES
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 4bef47068c1d5f8bbea0662a31df9a1a7ecfef2448f0b2eb9acdb502be210c3d
File size: 240,128 bytes
File name: eFax_[6 random digits].doc
File description: Word document with macro for Hancitor
- SHA256 hash: 05e7b5f18cf8ca0d672121b879d5b7ad2e854f8b6052f9e5b8f60ad4a3daa808
File size: 152,064 bytes
File location: C:\Users\[username]\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\Internet Explorer.exe
File description: Zeus Panda Banker
IMAGES
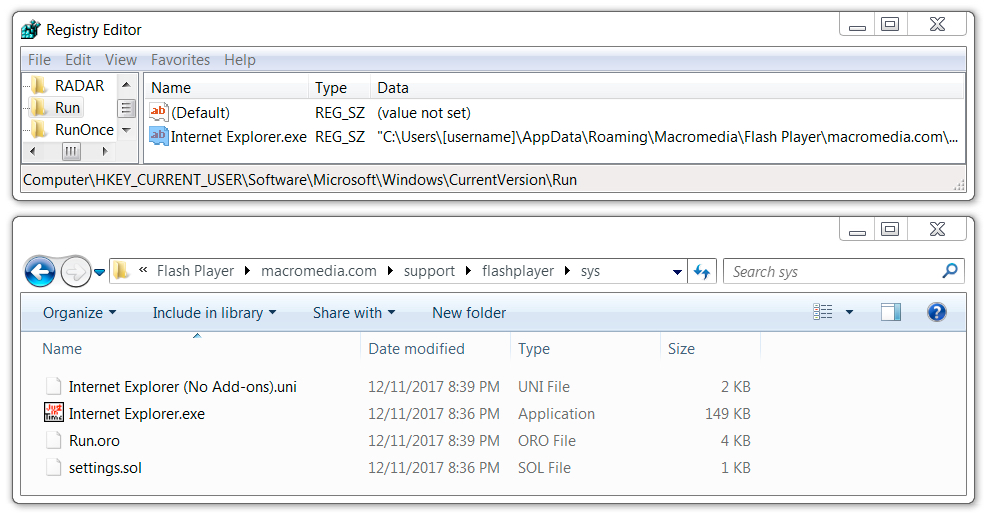
Shown above: Zeus Panda Banker persistent on the infected Windows host.
Click here to return to the main page.
