2017-12-12 - NGAY CAMPAIGN RIG EK PUSHES QUANT LOADER & MONERO COIN MINER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-12-Ngay-campaign-Rig-2-EK-pcaps.zip 1.1 MB (1,139,059 bytes)
- 2017-12-12-Ngay-campaign-Rig-EK-and-Quant-Loader-and-Monero-coin-miner-malware-and-artifacts.zip 1.8 MB (1,794,779 bytes)
NOTES:
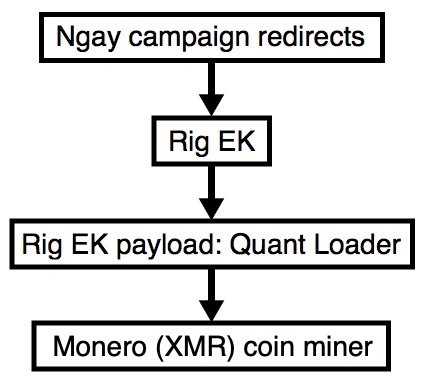
- This is Rig EK used by the Ngay campaign, first documented by @nao_sec at: http://www.nao-sec.org/2017/12/survey-of-ngay-campaign.html
- Today's Rig EK payload was Quant Loader which then grabbed Monero coin miner.
Shown above: Flow chart for today's infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- colennao[.]ml
- colennao[.]tk
- hxxp[:]//159.203.186[.]255/mprocess.exe
- ngay16[.]ru
- ngay1617[.]ru
TRAFFIC
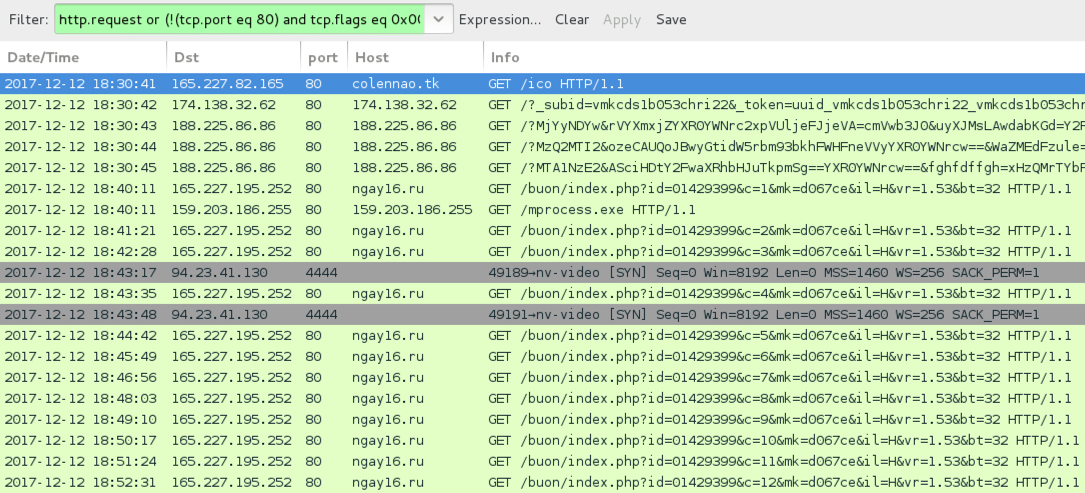
Shown above: Traffic from an infection filtered in Wireshark.
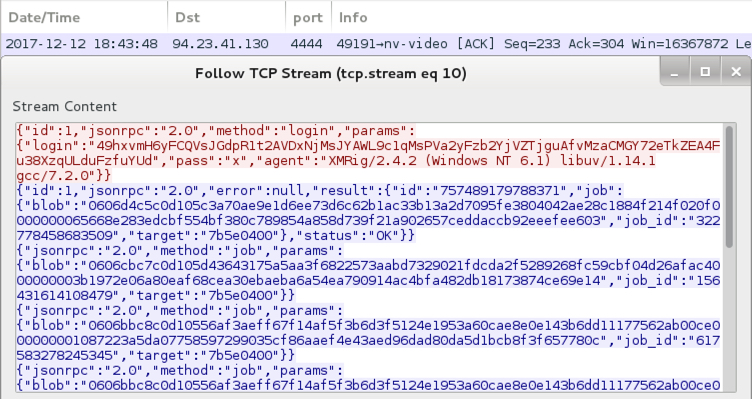
Shown above: Traffic caused by the Monero (XMR) coin miner.
FIRST RUN (NO POST-INFECTION TRAFFIC):
- 165.227.82[.]165 port 80 - colennao[.]ml - GET /ico
- 174.138.32[.]62 port 80 - 174.138.32[.]62 - GET /?_subid=[long string of chracters]
- 188.225.86[.]86 port 80 - 88.225.86[.]86 - Rig EK
SECOND RUN:
- 165.227.82[.]165 port 80 - colennao[.]tk - GET /ico
- 174.138.32[.]62 port 80 - 174.138.32[.]62 - GET /?_subid=[long string of chracters]
- 188.225.86[.]86 port 80 - 188.225.86[.]86 - Rig EK
- 165.227.195[.]252 port 80 - ngay16[.]ru - GET /buon/index.php?id=[long string of characters]
- 159.203.186[.]255 port 80 - 159.203.186[.]255 - GET /mprocess.exe
- DNS query for ngay1617[.]ru - response: No such name
- 94.23.41[.]130 port 4444 - pool.minexmr[.]com - TCP traffic associated with Monero coin miner
MALWARE AND ARTIFACTS FROM AN INFECTED WINDOWS HOST
- SHA256 hash: e04c3fe5a8afefba3ef810781ad9cc2cc0e066d3d67fcec7d8b3375f1b3fd7a8
- File size: 14,198 bytes
- File description: Rig EK flash exploit seen on 2017-12-12
- SHA256 hash: 527a757c937ad6a7a8b3f2f4fec261db3af4c10657414450085079bdd2a69715
- File size: 121,775 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\bilo263.exe
- File location: C:\Users\[username]\AppData\Roaming\01429399\csrss.exe
- File description: Quant Loader
- SHA256 hash: 7f55ffb0790a62ae0eb993bd241dd5234f67d1da0f5cf4c591f719b0f299631e
- File size: 809,445 bytes
- File location: hxxp://159.203.186.255/mprocess.exe
- File location: C:\Users\[username]\AppData\Local\Temp\184011.exe
- File location: C:\Users\[username]\AppData\Roaming\xerography.exe
- File description: Monero (XMR) coin miner
- SHA256 hash: ca9ee4c87496f976ac80c4582b7f24dc50866acbb6320f6eba8a085fe7675f72
- File size: 12,800 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\Musca.dll
- SHA256 hash: 63a3ffde6bac00d9793163011921448e91a4c3962829e86763343853ab30af09
- File size: 49,130 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\Zircalloy.dat
- File description: data file, might be used by Musca.dll
- SHA256 hash: 70fa3d4ef792fb3f9a950f518f3e6ad38a86ff6fe48813f3be8652876b2b78b6
- File size: 12,800 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\amuser.dll
- SHA256 hash: 44e7a2b2e2d129592e0b606a45946eaeb154ced1e0584c3800fb8f332e580ce3
- File size: 753,169 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\Assagai.cab
- File description: data file, might be used by amuser.dll
IMAGES
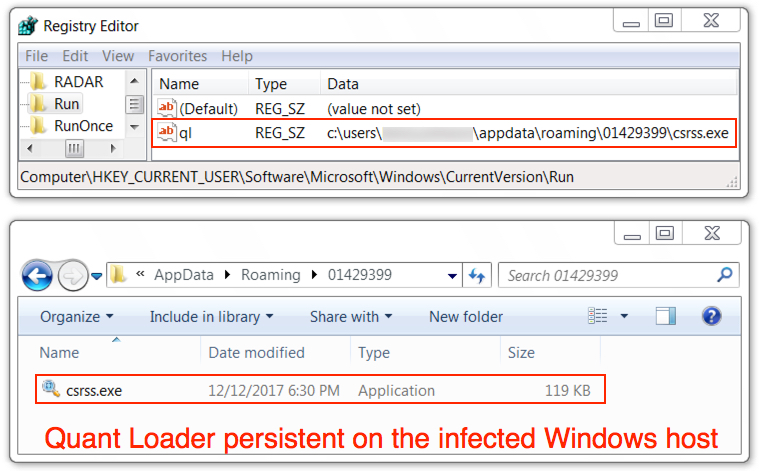
Shown above: Quant Loader persistent on the infected Windows host.
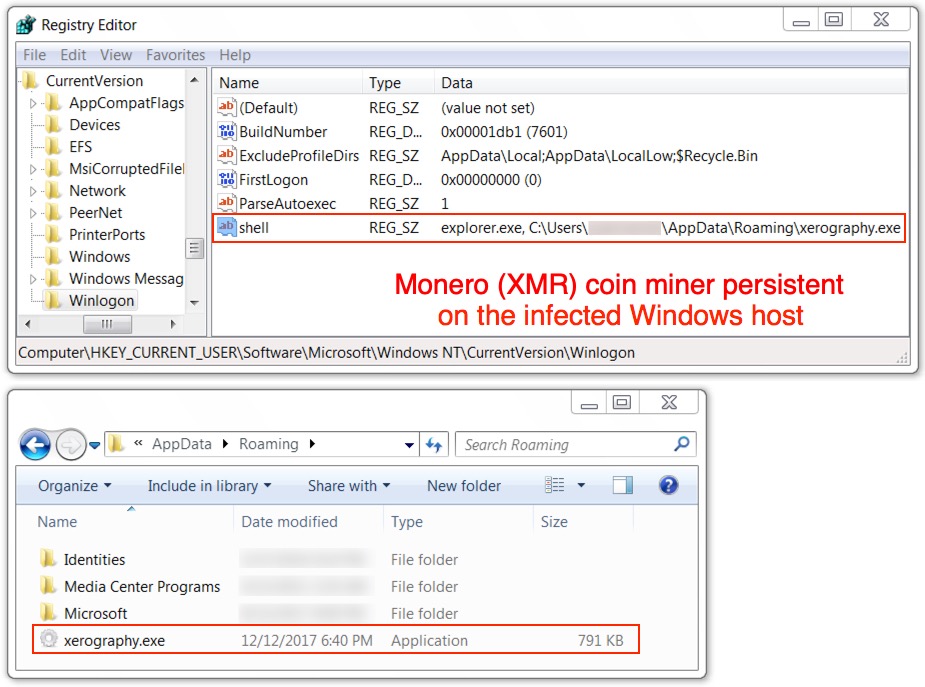
Shown above: Monero (XMR) coin miner persistent on the infected Windows host.
Click here to return to the main page.