2017-12-21 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of 33 emails: 2017-12-21-Hancitor-malspam-33-examples.zip 33.6 kB (33,611 bytes)
- Zip archive of the pcap: 2017-12-21-Hancitor-infection-wth-Zeus-Panda-Banker.pcap.zip 490.8 kB (490,802 bytes)
- Zip archive of the malware: 2017-12-21-malware-from-Hancitor-infection-with-Zeus-Panda-Banker.zip 223.7 kB (223,739 bytes)
NOTES:
- Today, post-infection malware from Hancitor malspam includes the Zeus Panda banking Trojan.
- Of course, there's still Pony and Evil Pony (both fileless) also downloaded by Hancitor from the Word document macro.
- As always, thanks to people like @fletchsec, @James_inthe_box, @Simpo13, and others who contributed to the Twitter discussion today.
- @James_inthe_box published additional indicators (link) that I've included in this report.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- coffeedoesgood[.]com
- coffeeforles[.]us
- eciggystore[.]com
- ecigsforless[.]com
- eleanorlarsonart[.]com
- hybriscoach[.]com
- planetfriendlycoffee[.]com
- planetfriendlywater[.]com
- quickkups[.]com
- royalconnection[.]org
- royalconnectioncoffee[.]com
- tikihut[.]coffee
- tikihutcafe[.]com
- tikihutcoffee[.]biz
- tikihutcoffee[.]us
- utahrates[.]com
- andrejoter[.]com
- dokemyhed[.]ru
- vehopehers[.]ru
- hxxp[:]//boobsandbabes[.]com/1
- hxxp[:]//boobsandbabes[.]com/2
- hxxp[:]//boobsandbabes[.]com/3
- hxxp[:]//rutstudio[.]pl/1
- hxxp[:]//rutstudio[.]pl/2
- hxxp[:]//rutstudio[.]pl/3
- hxxp[:]//wingchun-giessen[.]de/wp-content/uploads/2014/06/1
- hxxp[:]//wingchun-giessen[.]de/wp-content/uploads/2014/06/2
- hxxp[:]//wingchun-giessen[.]de/wp-content/uploads/2014/06/3
- hxxp[:]//www.americanfreethought[.]com/wordpress/1
- hxxp[:]//www.americanfreethought[.]com/wordpress/2
- hxxp[:]//www.americanfreethought[.]com/wordpress/3
- hxxp[:]//www.emilianobursese.com[.]ar/wp-content/plugins/bulletproof-security/1
- hxxp[:]//www.emilianobursese.com[.]ar/wp-content/plugins/bulletproof-security/2
- hxxp[:]//www.emilianobursese.com[.]ar/wp-content/plugins/bulletproof-security/3
- kedfortmoleft.ru
EMAILS
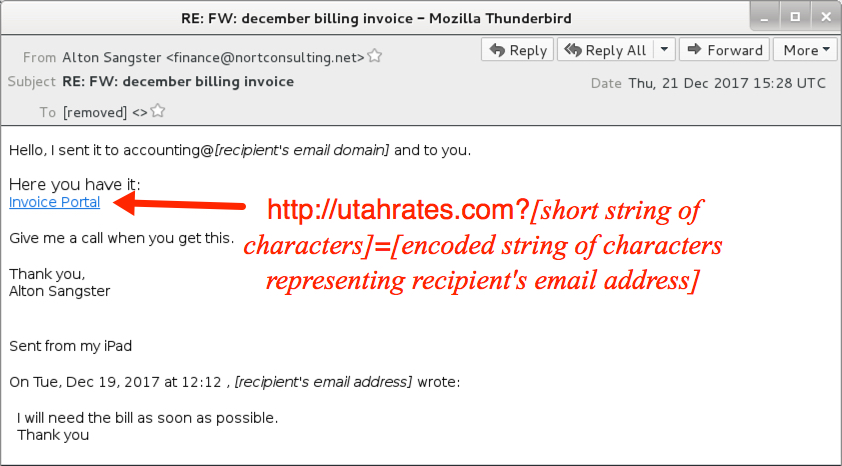
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Thursday 2017-12-21 as early as 15:28 through at least 20:07 UTC
- Subject: RE: FW: december billing invoice
- Received: from nortconsulting[.]net ([12.186.237[.]244])
- Received: from nortconsulting[.]net ([24.43.195[.]254])
- Received: from nortconsulting[.]net ([24.119.166[.]10])
- Received: from nortconsulting[.]net ([24.159.72[.]85])
- Received: from nortconsulting[.]net ([24.183.26[.]75])
- Received: from nortconsulting[.]net ([24.222.94[.]46])
- Received: from nortconsulting[.]net ([50.249.244[.]57])
- Received: from nortconsulting[.]net ([50.79.52[.]5])
- Received: from nortconsulting[.]net ([64.60.13[.]226])
- Received: from nortconsulting[.]net ([67.52.227[.]178])
- Received: from nortconsulting[.]net ([67.77.243[.]36])
- Received: from nortconsulting[.]net ([68.236.205[.]98])
- Received: from nortconsulting[.]net ([69.15.124[.]81])
- Received: from nortconsulting[.]net ([69.161.91[.]237])
- Received: from nortconsulting[.]net ([70.88.231[.]82])
- Received: from nortconsulting[.]net ([71.12.100[.]6])
- Received: from nortconsulting[.]net ([71.191.193[.]11])
- Received: from nortconsulting[.]net ([72.4.5[.]34])
- Received: from nortconsulting[.]net ([72.87.93[.]93])
- Received: from nortconsulting[.]net ([73.233.73[.]224])
- Received: from nortconsulting[.]net ([86.151.153[.]185])
- Received: from nortconsulting[.]net ([90.63.216[.]156])
- Received: from nortconsulting[.]net ([97.90.104[.]14])
- Received: from nortconsulting[.]net ([98.103.65[.]114])
- Received: from nortconsulting[.]net ([185.16.210[.]16])
- Received: from nortconsulting[.]net ([190.4.186[.]152])
- Received: from nortconsulting[.]net ([192.154.121[.]214])
- Received: from nortconsulting[.]net ([201.229.68[.]245])
- Received: from nortconsulting[.]net ([213.120.121[.]78])
- Received: from nortconsulting[.]net ([216.26.206[.]112])
- Received: from nortconsulting[.]net ([216.37.70[.]43])
- Received: from nortconsulting[.]net ([216.174.116[.]246])
- From (spoofed): "Alayna Croxton" <finance@nortconsulting[.]net>
- From (spoofed): "Alton Sangster" <finance@nortconsulting[.]net>
- From (spoofed): "Amos Coonrod" <finance@nortconsulting[.]net>
- From (spoofed): "Annalisa Benedict" <finance@nortconsulting[.]net>
- From (spoofed): "Antoinette Valentine" <finance@nortconsulting[.]net>
- From (spoofed): "Bernadine Daub" <finance@nortconsulting[.]net>
- From (spoofed): "Bronwyn Rambo" <finance@nortconsulting[.]net>
- From (spoofed): "Christiane Littles" <finance@nortconsulting[.]net>
- From (spoofed): "Clarinda Johnston" <finance@nortconsulting[.]net>
- From (spoofed): "Cornell Lowy" <finance@nortconsulting[.]net>
- From (spoofed): "Danilo Decaro" <finance@nortconsulting[.]net>
- From (spoofed): "Darryl Ryberg" <finance@nortconsulting[.]net>
- From (spoofed): "Gennie Haggard" <finance@nortconsulting[.]net>
- From (spoofed): "Heath Burroughs" <finance@nortconsulting[.]net>
- From (spoofed): "Junita Garcia" <finance@nortconsulting[.]net>
- From (spoofed): "Kirstie Mertz" <finance@nortconsulting[.]net>
- From (spoofed): "Kisha Escovedo" <finance@nortconsulting[.]net>
- From (spoofed): "Lesha Northington" <finance@nortconsulting[.]net>
- From (spoofed): "Letitia Foronda" <finance@nortconsulting[.]net>
- From (spoofed): "Margurite Schnee" <finance@nortconsulting[.]net>
- From (spoofed): "Monika Punch" <finance@nortconsulting[.]net>
- From (spoofed): "Soila Etienne" <finance@nortconsulting[.]net>
- From (spoofed): "Yahaira Hummer" <finance@nortconsulting[.]net>
- From (spoofed): "Yvette Mcclane" <finance@nortconsulting[.]net>
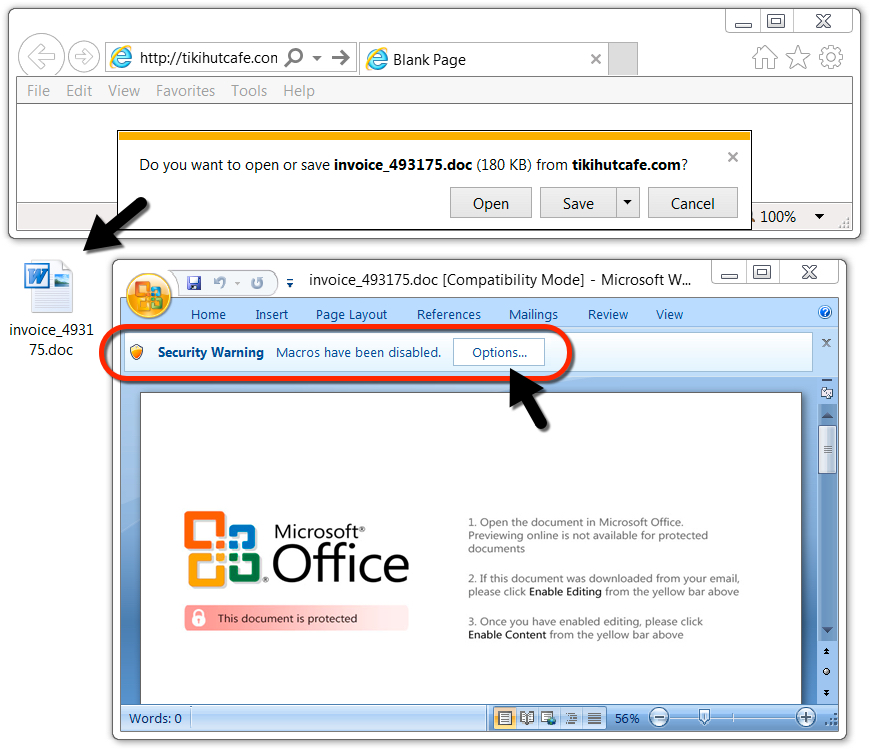
Shown above: Malicious Word document from link in the malspam.
TRAFFIC
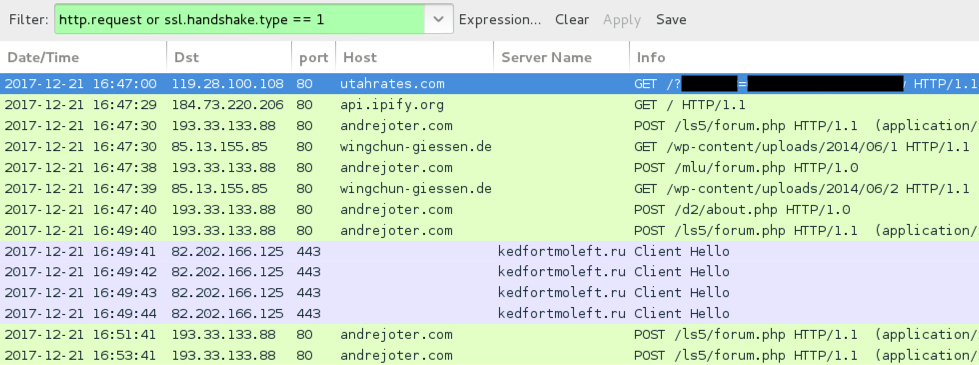
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- hxxp[:]//coffeeforles[.]us?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//eciggystore[.]com?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//ecigsforless[.]com?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//eleanorlarsonart[.]com?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//hybriscoach[.]com?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//planetfriendlycoffee[.]com?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//planetfriendlywater[.]com?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//quickkups[.]com?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//royalconnection[.]org?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//royalconnectioncoffee[.]com?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//tikihut[.]coffee?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//tikihutcafe[.]com?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//tikihutcoffee[.]biz?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//tikihutcoffee[.]us?[encoded string]=[encoded string representing recipient's email address]
- hxxp[:]//utahrates[.]com?[encoded string]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM MY INFECTED LAB HOST:
- 119.28.100[.]108 port 80 - utahrates[.]com - GET /?[string of characters]=[encoded string representing recipient's email address]
- api.ipify[.]org - GET /
- 193.33.133[.]88 port 80 - andrejoter[.]com - POST /ls5/forum.php
- 193.33.133[.]88 port 80 - andrejoter[.]com - POST /mlu/forum.php
- 193.33.133[.]88 port 80 - andrejoter[.]com - POST /d2/about.php
- 85.13.155[.]85 port 80 - wingchun-giessen[.]de - GET /wp-content/uploads/2014/06/1
- 85.13.155[.]85 port 80 - wingchun-giessen[.]de - GET /wp-content/uploads/2014/06/2
- 82.202.166[.]125 port 443 - kedfortmoleft[.]ru - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- www.google[.]com - HTTPS traffic, probably a connectivity check by infected Windows host
FILE HASHES
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 9906d7cbd7675f3334ef91e3a63792180e149b07a5899b1e2f9be5dcc6e8a086
File size: 184,320 bytes
File name: invoice_[6 random digits].doc
File description: Word document with macro for Hancitor
- SHA256 hash: 103176ef8223aa3f3cbf0bce91019a1688258eeea257d9aa617b31676e373c86
File size: 174,592 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
IMAGES
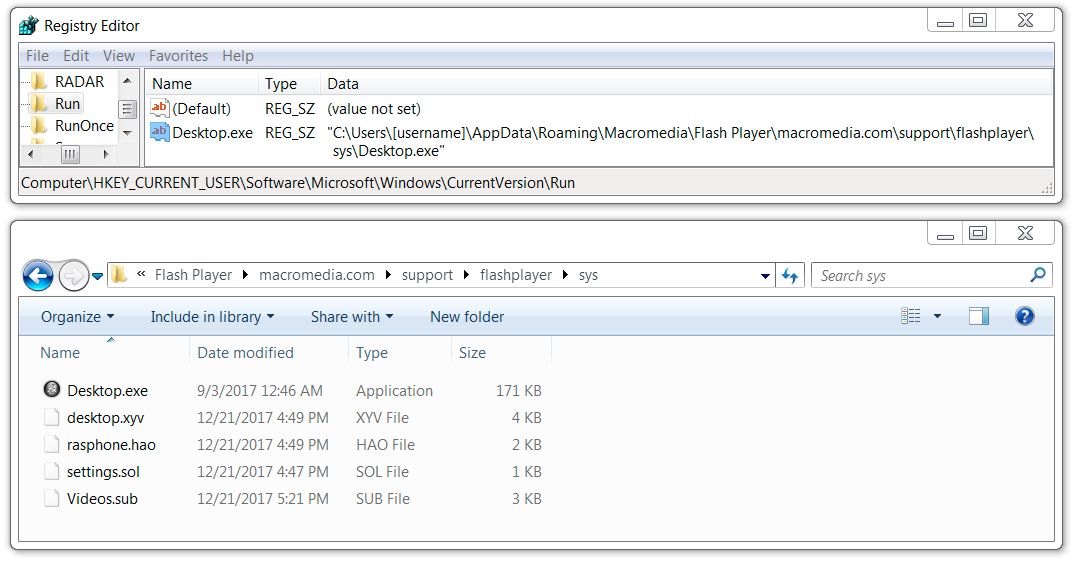
Shown above: Zeus Panda Banker persistent on the infected Windows host.
Click here to return to the main page.
