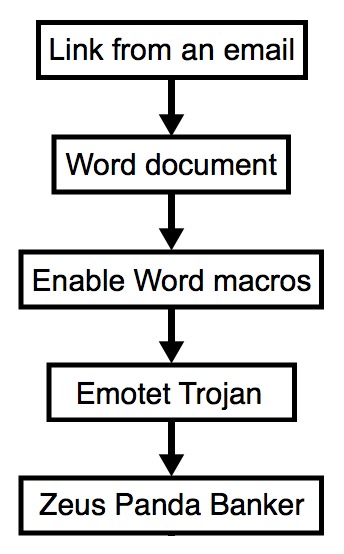
2017-12-27 - EMOTET INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-27-Emotet-infection-with-Zeus-Panda-Banker.pcap.zip 2.2 MB (2,206,403 bytes)
- 2017-12-27-Emotet-infection-with-Zeus-Panda-Banker.pcap (2,505,252 bytes)
- 2017-12-27-Emotet-malspam-1156-UTC.eml.zip 1.2 kB (1,212 bytes)
- 2017-12-27-Emotet-malspam-1156-UTC.eml (1,787 bytes)
- 2017-12-27-malware-from-Emotet-infection.zip 379 kB (379,179 bytes)
- 09:49 2017-12-27-Emotet-shedulecart.exe (200,704 bytes)
- 2017-12-27-Zeus-Panda-Banker-818200132aebmoouht.exe (266,240 bytes)
- Your Holidays Card.doc (196,096 bytes)
NOTES:
- See the comments section in this VirusTotal entry for more indicators/URLs to block.
- Additional indicators from analysis of a similar malspam message are listed in this tweet by @pollo290987.
Shown above: Flowchart for today's traffic.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//entplus[.]se/Your-Christmas-Gift-Card/
- hxxp[:]//bigeggdrop[.]com/WpDpV1/
- rendomunza[.]gdn
- namingotslon[.]gdn
HEADER INFORMATION:
- Date: Wednesday, 2017-12-27 at 11:56 UTC
- Recieved: from fed1rmfepo202.cox[.]net ([68.230.241[.]147])
- Message-ID: <767422129277.20171227115611@[recipient's email domain]>
- From: Lockett, Paula <kevin.metzger@cox[.]net>
- Subject: Merry Christmas!
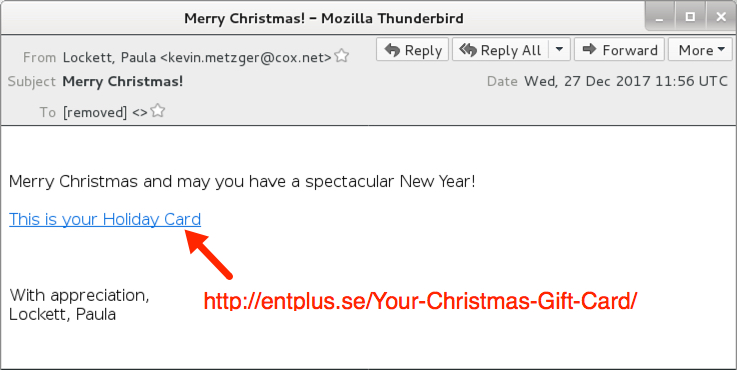
Shown above: Screenshot of the email.
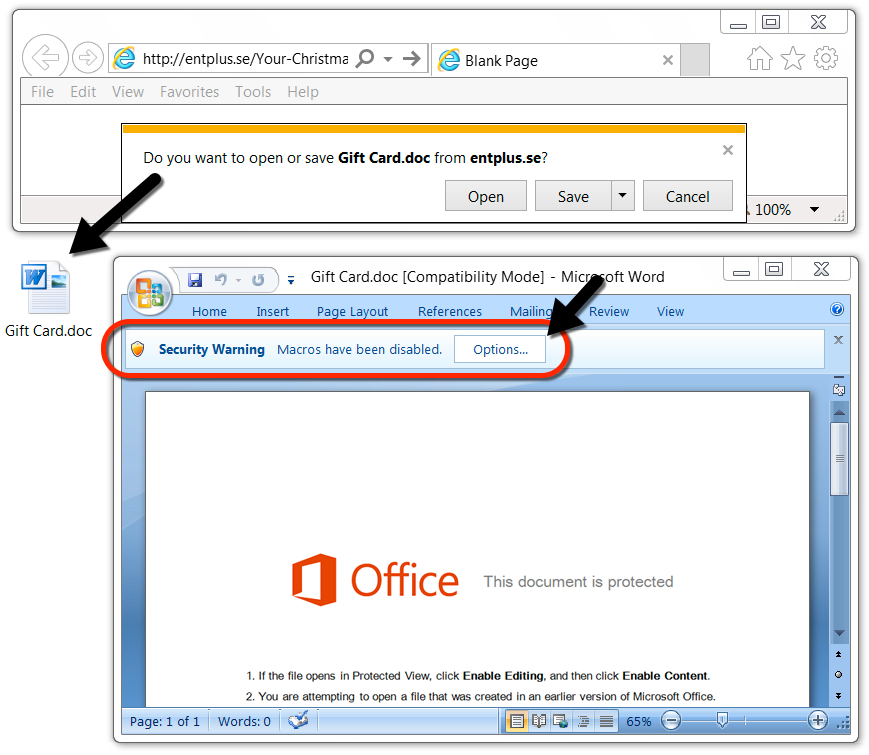
Shown above: Downloading a malicious Word document from link in the email.
TRAFFIC

Shown above: Traffic from an infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 46.30.213[.]154 port 80 - entplus[.]se - GET /Your-Christmas-Gift-Card/ (Word document download)
- 208.97.176[.]19 port 80 - bigeggdrop[.]com - GET /WpDpV1/ (Emotet binary download)
- 87.106.247[.]42 port 8080 - 87.106.247[.]42:8080 - POST / (Emotet post-infection traffic)
- 85.214.219[.]12 port 443 - 85.214.219[.]12:443 - POST / (Emotet post-infection traffic, encoded content but not HTTPS, also grabs Zeus Panda Banker)
- 146.148.124[.]166 port 443 - rendomunza[.]gdn - Zeus Panda Banker HTTPS traffic
- 185.117.72[.]70 port 443 - namingotslon[.]gdn - Zeus Panda Banker HTTPS traffic
- port 443 www.google[.]com - Connectivity check by Zeus Panda Banker
MALWARE
EMAIL ATTACHMENT (WORD DOCUMENT):
- SHA256 hash: a73924f6b3bc139c6f2365bc45eb1fa7727d6bfcea45ed3f9b21f97995d3daae
File size: 196,096 bytes
File name example: Your Holidays Card.doc
EMOTET BINARY:
- SHA256 hash: dfb6a732af0b962771f5a84cd14eb0057fa7c63e9622ec08433db3abaada09ff
File size: 200,704 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\shedulecart.exe
ZEUS PANDA BANKER:
- SHA256 hash: b7ad996132de4f379dc58267b91b6c075a625ab3b7c29099fb79ce289abd5121
File size: 266,240 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File location example: C:\Users\[username]\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\818200132aebmoouht.exe
IMAGES
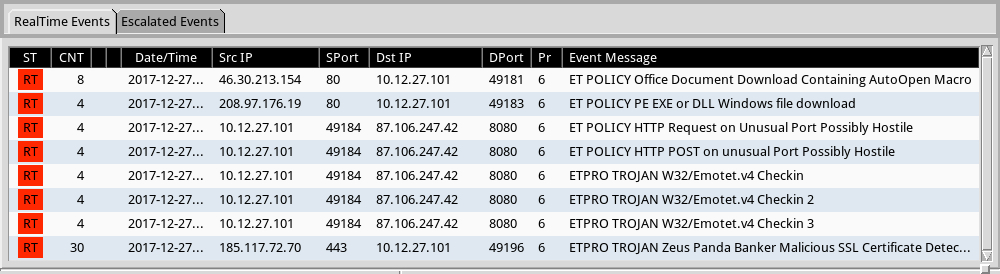
Shown above: Some alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
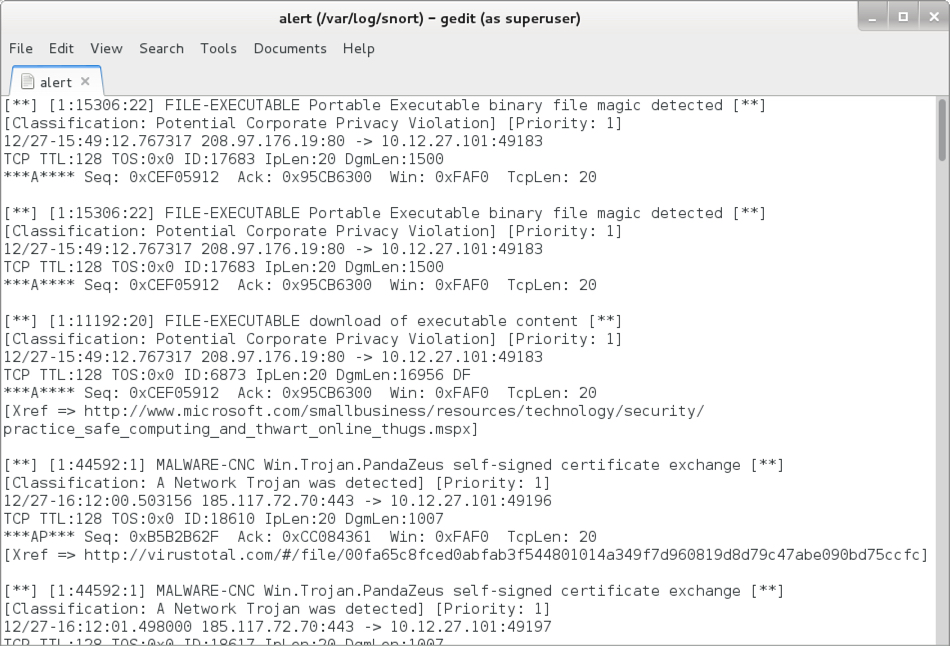
Shown above: Some alerts on the infection traffic from the Snort subscriber ruleset when reading the pcap with Snort 2.9.11.
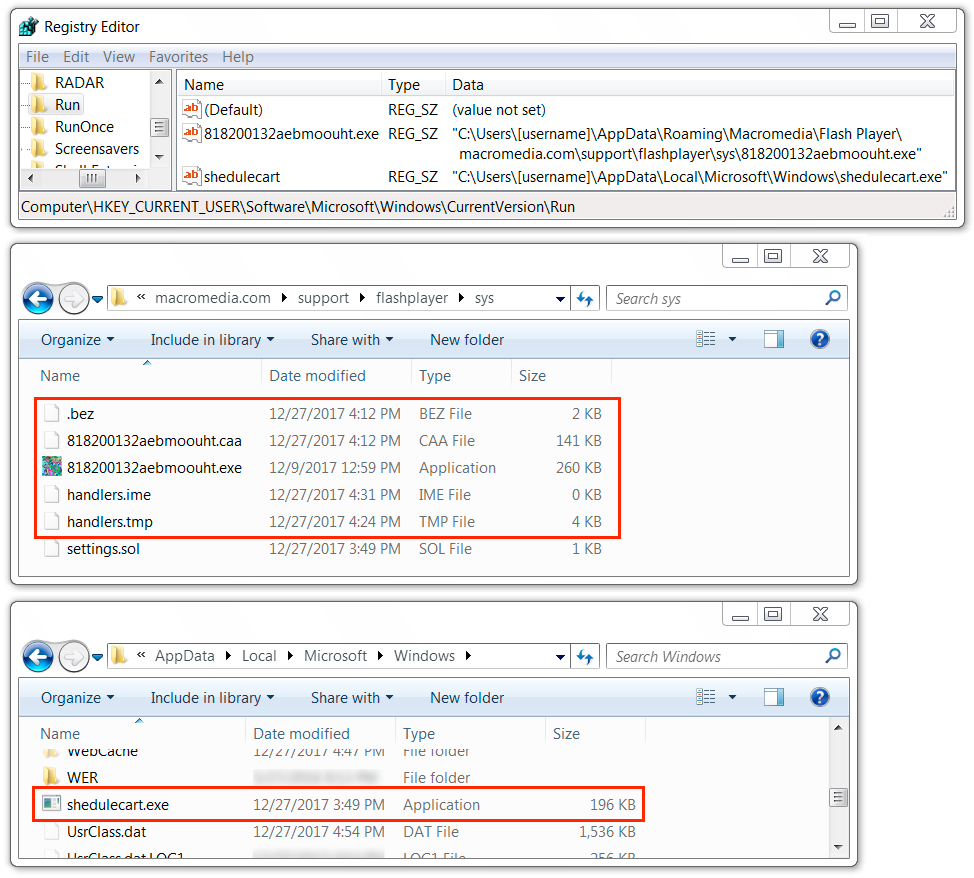
Shown above: Malware persistent on the infected Windows host.
Click here to return to the main page.