2018-01-02 - FAKE FLASH UPDATER IS ACTUALLY A CRYPTOCURRENCY MINER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-02-fake-Flash-player-installs-coinminer.pcap.zip 659.0 kB (658,966 bytes)
- 2018-01-02-fake-Flash-player-installs-coinminer.pcap (713,781 bytes)
- 2018-01-02-fake-Flash-update-page-and-coinminer.zip 273.3 kB (273,258 bytes)
- 2018-01-02-fake-flash-update-page.txt (9,542 bytes)
- 2018-01-02-fake-flashupdate.exe (558,080 bytes)
- 2018-01-02-scheduled-task-for-persistence.txt (3,720 bytes)
NOTES:
- This was a case of malvertising during casual web browsing.
- I'm able to share two URLs in the chain of events before it reached the fake Flash update page.
Shown above: The fake Flash updater page presenting its malware for download.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains:
- zad33a[.]ru
- 4chrup56[.]ru
- adobeflashplayer.kilahb[.]xyz
- 1sjs21891[.]ru
- pronetads[.]com
TRAFFIC
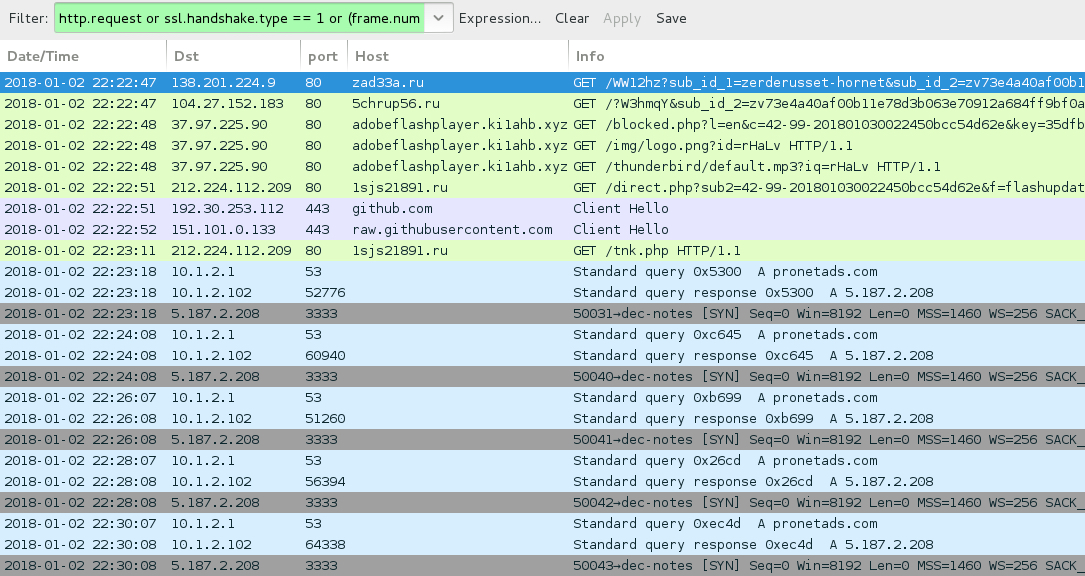
Shown above: Traffic from the infection filtered in Wireshark.
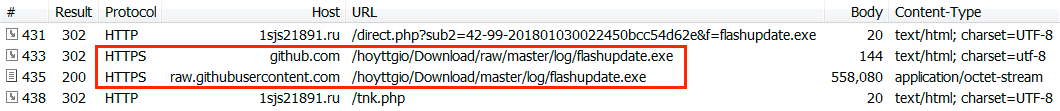
Shown above: HTTPS URLs from the traffic shown in Fiddler web debugger.

Shown above: Post-infection coinminer traffic.
ASSOCIATED DOMAINS:
- 138.201.224[.]98 port 80 - zad33a[.]ru - GET /WW12hz?[string of paramters]
- 104.27.152.183 port 80 - 5chrup56[.]ru - GET /?W3hmqY&[string of paramters]
- 37.97.225.90 port 80 - adobeflashplayer.ki1ahb[.]xyz - GET /blocked.php?[string of paramters]
- 37.97.225.90 port 80 - adobeflashplayer.ki1ahb[.]xyz - GET /img/logo.png?id=rHaLv
- 37.97.225.90 port 80 - adobeflashplayer.ki1ahb[.]xyz - GET /thunderbird/default.mp3?iq=rHaLv
- 212.224.112.209 port 80 - 1sjs21891[.]ru - GET /direct.php?sub2=42-99-201801030022450bcc54d62e&f=flashupdate.exe
- port 443 (HTTPS) - github[.]com - GET /hoyttgio/Download/raw/master/log/flashupdate.exe
- port 443 (HTTPS) - raw.githubusercontent[.]com - GET /hoyttgio/Download/master/log/flashupdate.exe
- 212.224.112[.]209 port 80 - 1sjs21891[.]ru - GET /tnk.php
- 5.187.2[.]208 port 3333 - pronetads[.]com - Coinmining post-infection traffic
MALWARE
COINMINER DOWNLOADED FROM FAKE FLASH UPDATE PAGE:
- SHA256 hash: 09678e49d00b5d0d0b130e9f264d078f7981dace298d2f38bb45ec9fe8567a52
File size: 558,080 bytes
File name: flashupdate.exe
File location after infection: C:\ProgramData\vshub.exe
Shown above: Fake metadata for the coinminer malware.
IMAGES
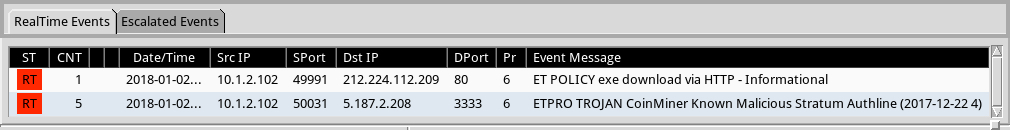
Shown above: Alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
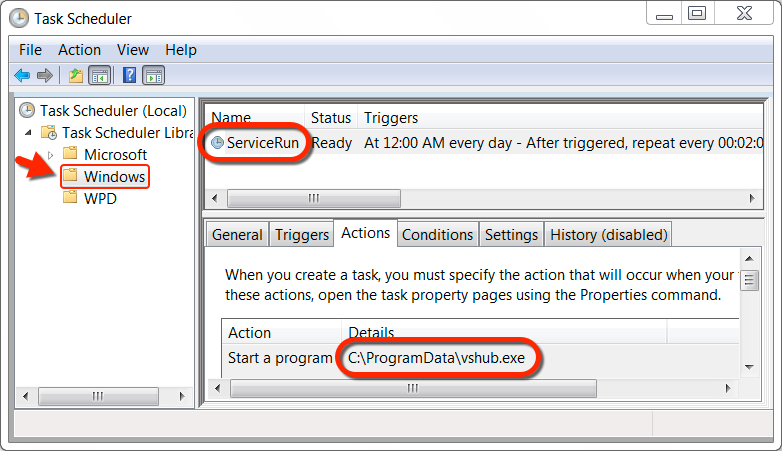
Shown above: Scheduled task to keep the coinminer persitent after a reboot.
Shown above: Coinminer malware copied itself to the C:\ProgramData folder.
Click here to return to the main page.


