2018-01-04 - FORMBOOK INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-04-Formbook-infection-traffic.pcap.zip 1.3 MB (1,251,503 bytes)
- 2018-01-04-Formbook-infection-traffic.pcap (1,831,112 bytes)
- 2018-01-04-Formbook-email-and-malware.zip 676.3 kB (676,254 bytes)
- 2018-01-04-Formbook-malware-sample.exe (425,984 bytes)
- 2018-01-04-malspam-attachment-Proforma-INV-44748.rar (214,334 bytes)
- 2018-01-04-malspam-pushing-Formbook-1419-UTC.eml (317,143 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following partial URLs:
- hxxp[:]//www.alizayuh[.]com/iz/
- hxxp[:]//www.privewin14[.]com/iz/
- hxxp[:]//www.thestokelife[.]com/iz/
- hxxp[:]//www.wshzkq[.]com/iz/
- hxxp[:]//www.enwei999[.]com/iz/
- hxxp[:]//www.armdmbw6-liquidwebsites[.]com/iz/
- hxxp[:]//www.austinhedna[.]com/iz/
- hxxp[:]//www.captfresh[.]com/iz/
- hxxp[:]//www.consejeriahumanitaria[.]com/iz/
- hxxp[:]//www.jordigarreta[.]com/iz/
- hxxp[:]//www.mrpirateproxy[.]com/iz/
- hxxp[:]//www.supermarioruncoins[.]today/iz/
- hxxp[:]//www.amercon[.]info/iz/
- hxxp[:]//www.mavericktrailblazing[.]com/iz/
- hxxp[:]//www.turboexercise[.]com/iz/
- hxxp[:]//www.930pe[.]com/iz/
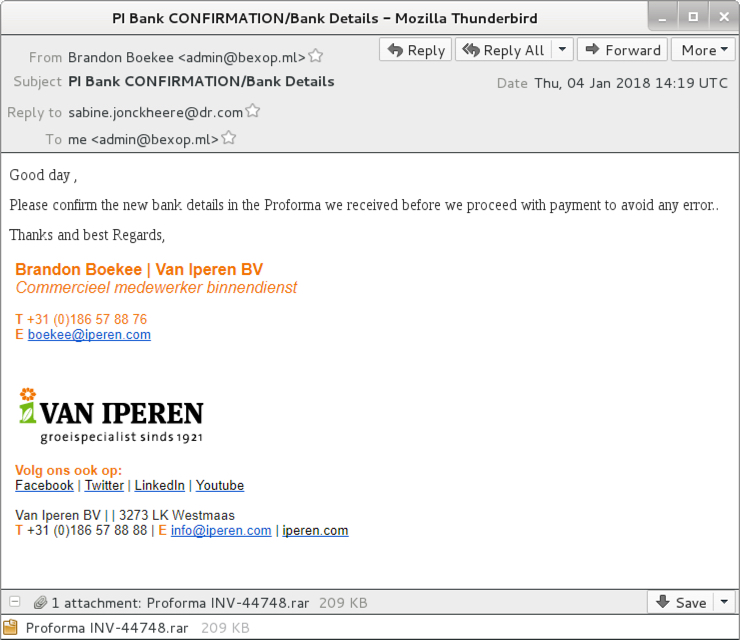
Shown above: Screenshot of the email.
EMAIL INFORMATION:
- Date: Thursday, 2018-01-04 at 14:19 UTC
- Subject: PI Bank CONFIRMATION/Bank Details
- From: "Brandon Boekee"<admin@bexop.ml>
- Message-Id: <201801050003.m0503jvBM790659500@mail-kairos-rmail7.pg1.krane.9rum.cc>
- Attachment name: Proforma INV-44748.rar

Shown above: Attached RAR file is actually an ACE archive.
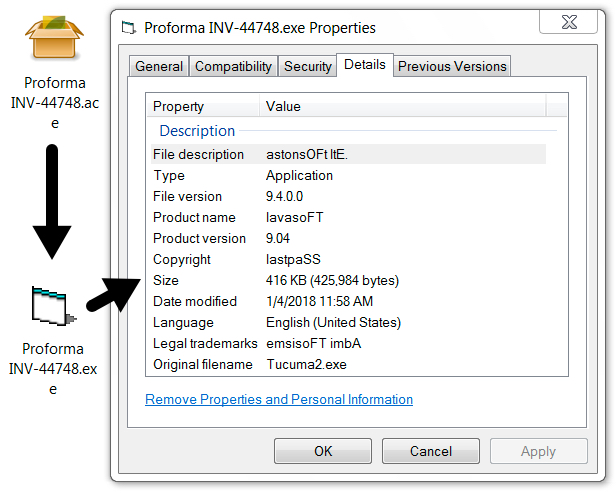
Shown above: Malware extracted from the ACE archive.
TRAFFIC
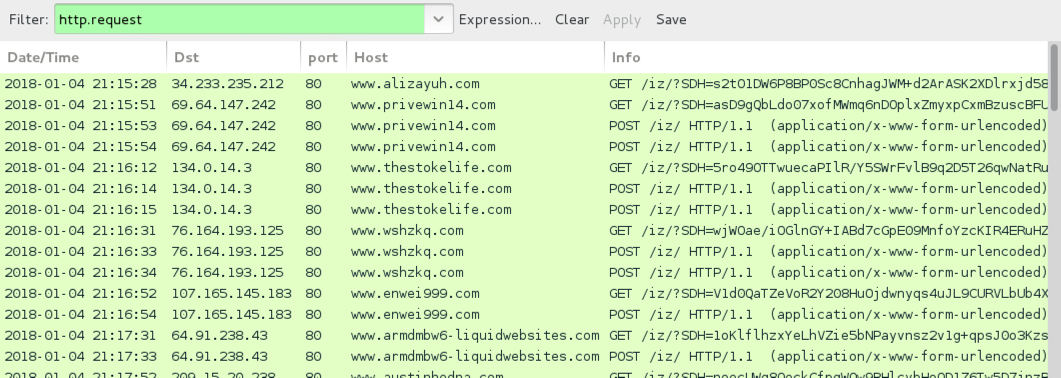
Shown above: Infection traffic filtered in Wireshark.
ASSOCIATED TRAFFIC:
- 34.233.235[.]212 port 80 - www.alizayuh[.]com - GET /iz/?SDH=[long string of characters]
- 69.64.147[.]242 port 80 - www.privewin14[.]com - GET /iz/?SDH=[long string of characters]
- 69.64.147[.]242 port 80 - www.privewin14[.]com - POST /iz/
- 134.0.14[.]3 port 80 - www.thestokelife[.]com - GET /iz/?SDH=[long string of characters]
- 134.0.14[.]3 port 80 - www.thestokelife[.]com - POST /iz/
- 76.164.193[.]125 port 80 - www.wshzkq[.]com - GET /iz/?SDH=[long string of characters]
- 76.164.193[.]125 port 80 - www.wshzkq[.]com - POST /iz/
- 107.165.145[.]183 port 80 - www.enwei999[.]com - GET /iz/?SDH=[long string of characters]
- 107.165.145[.]183 port 80 - www.enwei999[.]com - POST /iz/
- 64.91.238[.]43 port 80 - www.armdmbw6-liquidwebsites[.]com - GET /iz/?SDH=[long string of characters]
- 64.91.238[.]43 port 80 - www.armdmbw6-liquidwebsites[.]com - POST /iz/
- 209.15.20[.]238 port 80 - www.austinhedna[.]com - GET /iz/?SDH=[long string of characters]
- 209.15.20[.]238 port 80 - www.austinhedna[.]com - POST /iz/
- 198.105.244[.]228 port 80 - www.captfresh[.]com - GET /iz/?SDH=[long string of characters]
- 198.105.244[.]228 port 80 - www.captfresh[.]com - POST /iz/
- 74.208.236[.]98 port 80 - www.consejeriahumanitaria[.]com - GET /iz/?SDH=[long string of characters]
- 74.208.236[.]98 port 80 - www.consejeriahumanitaria[.]com - POST /iz/
- 181.224.129[.]125 port 80 - www.jordigarreta[.]com - GET /iz/?SDH=[long string of characters]
- 181.224.129[.]125 port 80 - www.jordigarreta[.]com - POST /iz/
- 103.224.182[.]243 port 80 - www.mrpirateproxy[.]com - GET /iz/?SDH=[long string of characters]
- 103.224.182[.]243 port 80 - www.mrpirateproxy[.]com - POST /iz/
- 68.65.122[.]92 port 80 - www.supermarioruncoins[.]today - GET /iz/?SDH=[long string of characters]
- 68.65.122[.]92 port 80 - www.supermarioruncoins[.]today - POST /iz/
- 198.54.121[.]12 port 80 - www.amercon[.]info - GET /iz/?SDH=[long string of characters]
- 198.54.121[.]12 port 80 - www.amercon[.]info - POST /iz/
- 34.232.43[.]118 port 80 - www.mavericktrailblazing[.]com - GET /iz/?SDH=[long string of characters]
- 34.232.43[.]118 port 80 - www.mavericktrailblazing[.]com - POST /iz/
- DNS queries for www.turboexercise[.]com - Standard query response: Server failure
- DNS queries for www.930pe[.]com - Standard query response: A www.930pe.com SOA ns1.dns[.]com
MALWARE
ACE ARCHIVE FROM THE MALSPAM:
- SHA256 hash: 83b8926914fa55f05b58e2e5d6664ae4d3878e42f2698a2461a402141eb7c7e8
File size: 214,334 bytes
File name: Proforma INV-44748.rar
NOTE: This is an ACE archive, not a RAR file.
FORMBOOK MALWARE EXTRACTED FROM THE ACE ARCHIVE:
- SHA256 hash: 745de339d343a9249bf999bb38a0869bc54230c288dc1b9a302952ef8473eb78
File size: 425,984 bytes
File name: Proforma INV-44748.exe
File location: C:\Program Files (x86)\Nljod5zx\7nj88vzv14x.exe
WINDOWS REGISTRY ENTRY FOR PERSISTENCE:
- Registry Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Value name: 2D9L_RFPQRU
- Value Type: REG_SZ
- Value Data: C:\Program Files (x86)\Nljod5zx\7nj88vzv14x.exe
IMAGES
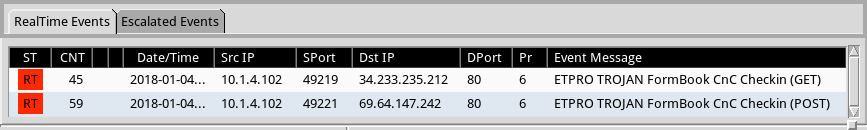
Shown above: Alerts from Sguil on the infection traffic in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
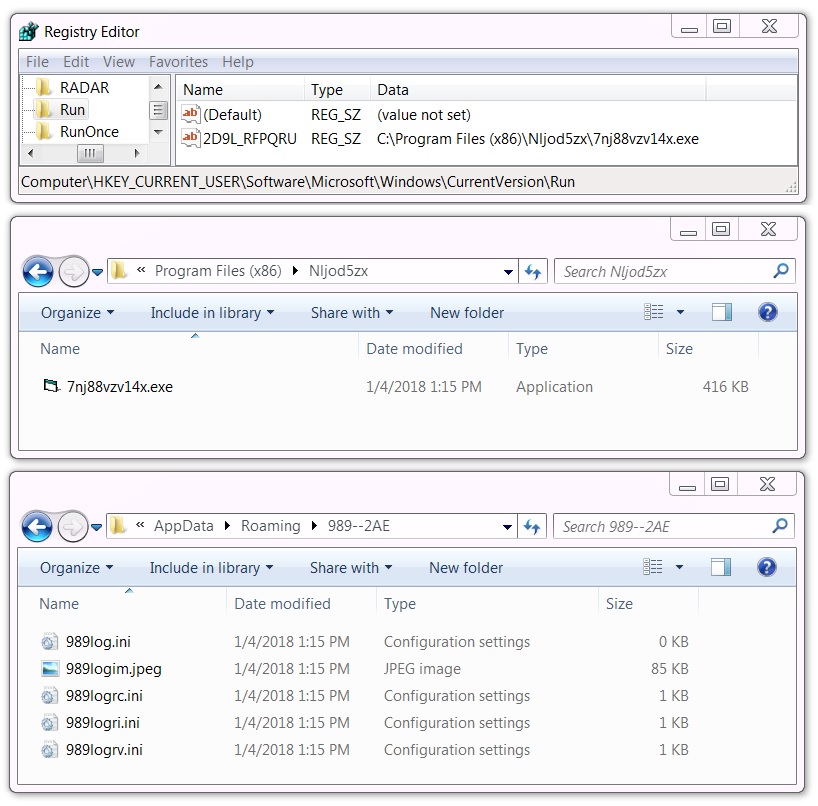
Shown above: Registry key and associated files on the infected Windows host
Click here to return to the main page.
