2018-01-09 - JAVA-BASED RAT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-09-Java-based-RAT-infection-traffic.pcap.zip 489.6 kB (489,644 bytes)
- 2018-01-09-Java-based-RAT-infection-traffic.pcap (534,031 bytes)
- 2018-01-09-Java-based-RAT-email-and-malware.zip 1.6 MB (1,634,153 bytes)
- 2018-01-08-Java-based-RAT-malspam-UTC.txt (7,736 bytes)
- ImportantSign_PDF.jar (712,446 bytes)
- ImportantSign_PDF.zip (696,956 bytes)
- _0.247387460198232888134367552441532945.class (247,088 bytes)
NOTES:
- This often gets tagged as "Adwind", but it's gone through a few name changes, and it might be called jRAT now.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domain:
- prodocusign[.]com
- vvrhhhnaijyj6s2m[.]onion[.]top
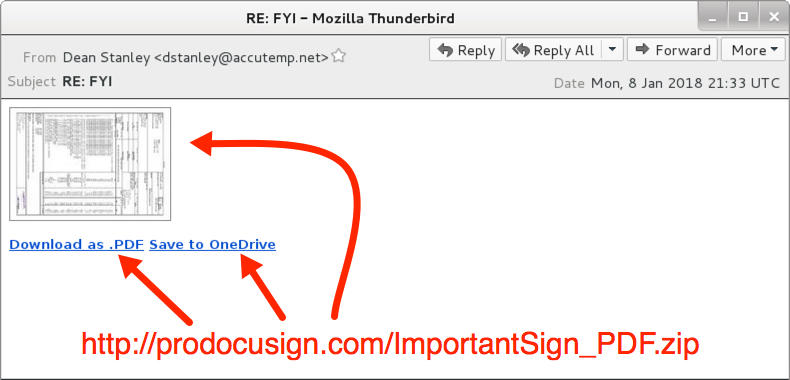
Shown above: Screenshot of the email.
EMAIL INFORMATION:
- Date: Monday, 2018-01-08 at 21:33 UTC
- Subject: RE: FYI
- From: Dean Stanley <dstanley@accutemp[.]net>
- Message-ID: <F8CCF827-C349-46FC-9F0B-C67C290307C5@accutemp[.]net>
- Received: from NAM02-BL2-obe.outbound.protection.outlook[.]com ([104.47.38.236])
- Link in the email: hxxp[:]//producsign[.]com/ImportantSign_PDF.zip
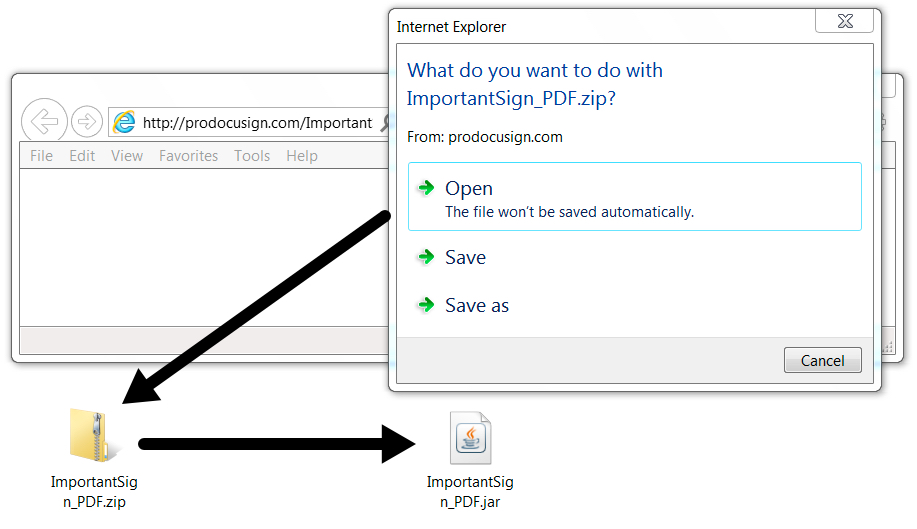
Shown above: Downloading the malicious zip archive and extracting its contents.
TRAFFIC
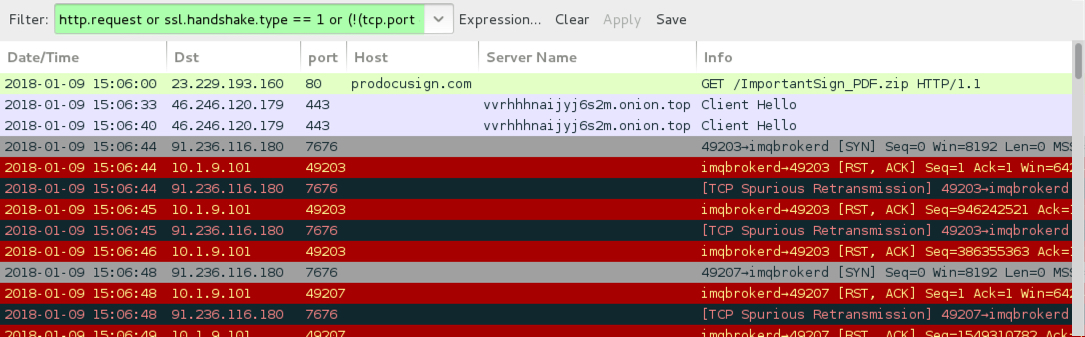
Shown above: Infection traffic filtered in Wireshark.
INFECTION TRAFFIC:
- 23.229.193[.]160 port 80 - prodocusign[.]com - GET /ImportantSign_PDF.zip
- 46.246.120[.]179 port 443 - vvrhhhnaijyj6s2m[.]onion[.]top - HTTPS traffic
- 91.236.116[.]180 port 7676 - Attempted TCP connections (SYN packets sent, but RST from server)
MALWARE
ZIP ARCHIVE FROM LINK IN THE EMAIL:
- SHA256 hash: 726d745b31a66b17db70353e3f5ae58ca020401ef29401364165bc0aa23a2f0d
File size: 712,446 bytes
File name: ImportantSign_PDF.zip
JAVA ARCHIVE (.JAR) FILE EXTRACTED FROM THE ZIP ARCHIVE:
- SHA256 hash: ffcbbe10a4e0ececf0b13e3b06c329ebc11d4f394daa8ad3dc8adc3d6949aa6f
File size: 712,446 bytes
File name: ImportantSign_PDF.jar
File location: C:\Users\[username]\AppData\WCUkrffrYPW\WUrfrLvepB.JStdFrfrc
ARTIFACT FROM THE INFECTED WINDOWS HOST:
- SHA256 hash: 97d585b6aff62fb4e43e7e6a5f816dcd7a14be11a88b109a9ba9e8cd4c456eb9
File size: 247,088 bytes
File name: ImportantSign_PDF.jar
File location: C:\Users\[username]\AppData\Local\Temp\_0.247387460198232888134367552441532945.class
File location: C:\Users\[username]\AppData\Local\Temp\_0.3243062791444255803638734785218251.class
File location: C:\Users\[username]\AppData\Local\Temp\_0.79817373850884391680127356134437643.class
File location: C:\Users\[username]\AppData\Local\Temp\_0.97236765186552721410066307447487038.class
WINDOWS REGISTRY ENTRY FOR PERSISTENCE:
- Registry Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Value name: raFnSZOca
- Value Type: REG_EXPAND_SZ
- Value Data: "C:\Users\[username]\AppData\Roaming\Oracle\bin\javaw.exe" -jar "C:\Users\[username]\AppData\WCUkrffrYPW\WUrfrLvepB.JStdFrfrc"
IMAGES
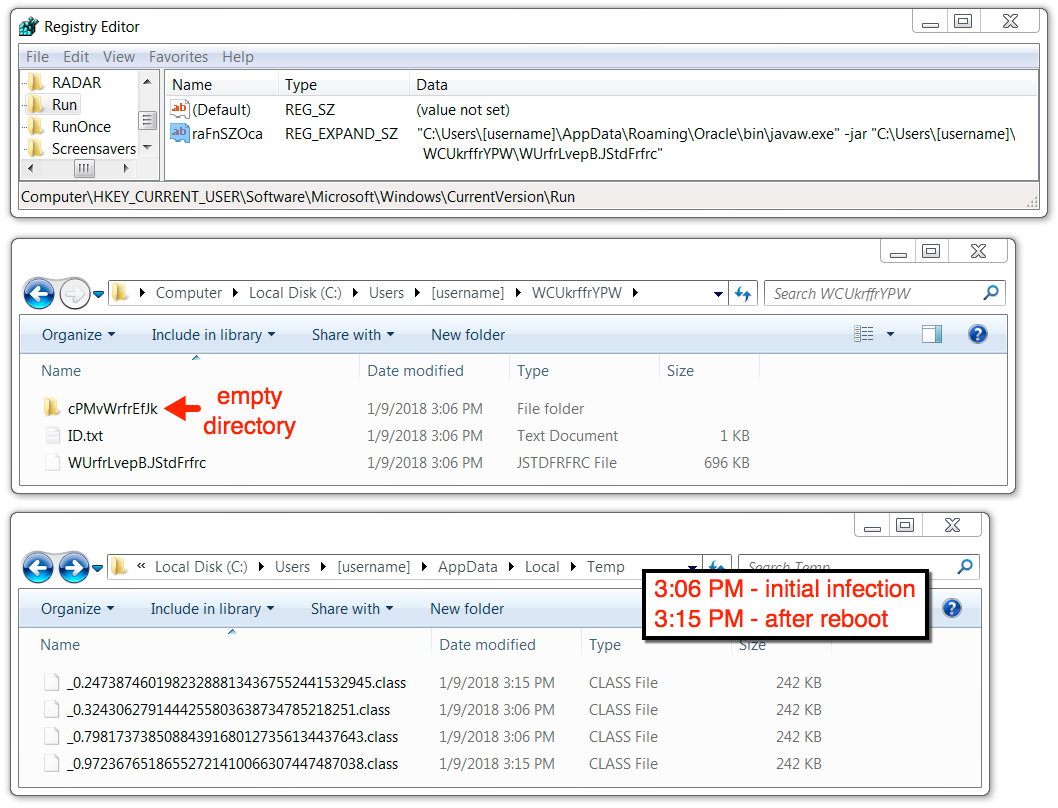
Shown above: Registry key and associated files on the infected Windows host.
Click here to return to the main page.
