2018-01-09 - SEAMLESS CAMPAIGN RIG EK SENDS RAMNIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-09-Seamless-campaign-Rig-EK-sends-Ramnit.pcap.zip 1.9 MB (1,850,410 bytes)
- 2018-01-09-Seamless-campaign-Rig-EK-sends-Ramnit.pcap (2,783,529 bytes)
- 2018-01-09-Seamless-campaign-Rig-EK-artifacts-and-malware.zip 167.5 kB (167,471 bytes)
- 2018-01-09-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2018-01-09-Rig-EK-flash-exploit.swf (13,895 bytes)
- 2018-01-09-Rig-EK-landing-page.txt (97,319 bytes)
- 2018-01-09-Seamless-campaign-Rig-EK-payload-Ramnit.exe (167,424 bytes)
NOTES:
- Thanks to @jeromesegura for reminding me that Seamless is using punycode for the URLs before Rig EK.
- Also thanks to @nao_sec. @DynamicAnalysis, @BroadAnalysis, and @Zerophage1337, who have posted pcaps of Rig EK traffic on their respective blogs.
- Finally, thanks to others like @anyrun_app, @cyber_attacks, @VK_Intel, and @thlnk3r who have tweeted or published information about Rig EK in recent months.
DOCUMENTATION ON THE SEAMLESS CAMPAIGN:
- 2017-03-29 - Cisco Umbrella Blog - 'Seamless' campaign delivers Ramnit via Rig EK
- 2017-05-11 - ISC Diary - Seamless Campaign using Rig Exploit Kit to send Ramnit Trojan
- 2017-05-17 through 2017-11-12 - Malware Breakdown - various blog posts on the Seamless campaign
- 2017-06-02 - Malware-Traffic-Analysis.net - Seamless campaign continues using Rig EK to send Ramnit
- 2017-08-25 - Malware-Traffic-Analysis.net - Seamless campaign Rig EK sends Ramnit
- 2017-09-07 through 2017-11-10 - Broadanalysis.com - various blog posts titled: Rig Exploit Kit via Seamless malvertising delivers Ramnit banking malware
- 2017-12-04 - MalwareBytes blog - Seamless campaign serves RIG EK via Punycode
- 2017-12-25 - traffic.moe - Seamless->RigEK->Ramnit
- 2018-01-09 - app.any.run - Analysis of Rig Exploit Kit.html
- 2018-01-09 - traffic.moe - Seamless->RigEK->Ramnit
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domain:
- xn--b1aanbboc3ad8jee4bff[.]xn--p1ai
- ccookd72yyeuj6y[.]com
TRAFFIC
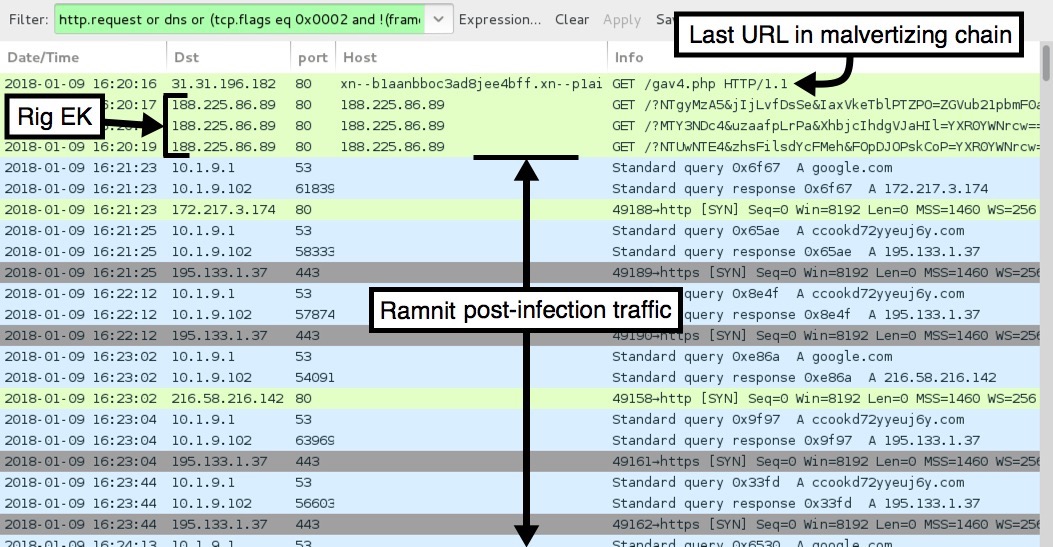
Shown above: Infection traffic in Wireshark.
INFECTION TRAFFIC:
- 31.31.196[.]182 port 80 - xn--b1aanbboc3ad8jee4bff[.]xn--p1ai - GET /gav4.php
- 188.225.86[.]89 port 80 - 188.225.86[.]89 - Rig EK
- Attempted connections to google[.]com caused by Ramnit
- 195.133.1[.]37 port 443 - ccookd72yyeuj6y[.]com - encoded traffic caused by Ramnit (not HTTPS/SSL/TLS)
- 207.244.112[.]70 port 4000 - encoded traffic (not HTTPS/SSL/TLS)
- 207.244.112[.]70 port 4001 - encoded traffic (not HTTPS/SSL/TLS)
MALWARE
RIG EK FLASH EXPLOIT:
- SHA256 hash: b8408fbe0c46d124ccd7ef96a9084663a43d630fdfb9e987657f7447ca27b13a
File size: 13,895 bytes
RIG EK PAYLOAD - RAMNIT:
- SHA256 hash: 4ecba920d0da06a821be364998083d4d2b1ea5014243a81e46c6c036d0e03662
File size: 167,424 bytes
File location: C:\Users\[username]\AppData\Local\Temp\bilo458.exe
File location: C:\Users\[username]\AppData\Local\Temp\ktfpuxkb.exe
File location: C:\Users\[username]\AppData\Local\Temp\ramissyv.exe
File location: C:\Users\[username]\AppData\Local\Temp\vvxpiiaa.exe
File location: C:\Users\[username]\AppData\Local\wdxyjubt\bxnknleu.exe
IMAGES
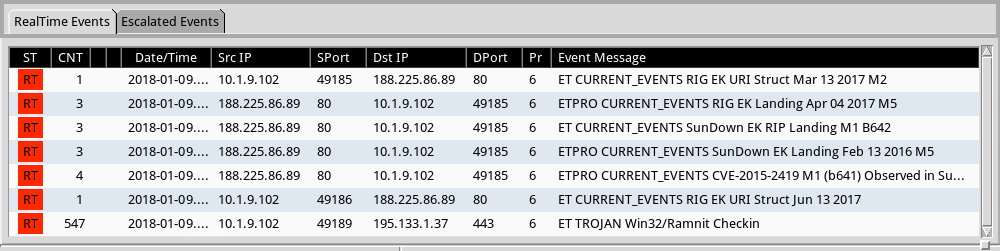
Shown above: Some alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
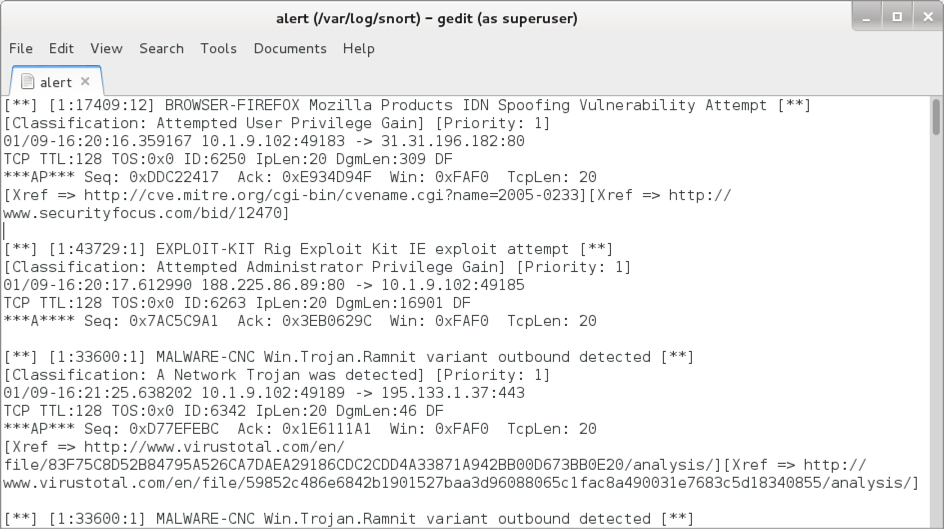
Shown above: Some alerts on the infection traffic from the Snort subscriber ruleset when reading the pcap with Snort 2.9.11.
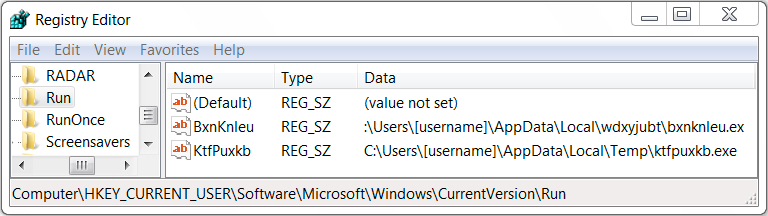
Shown above: Registry key on the infected Windows host updated for malware persistence.
Shown above: There's also a link in the Startup folder from the Start Menu
to keep the malware persistent.
Click here to return to the main page.
