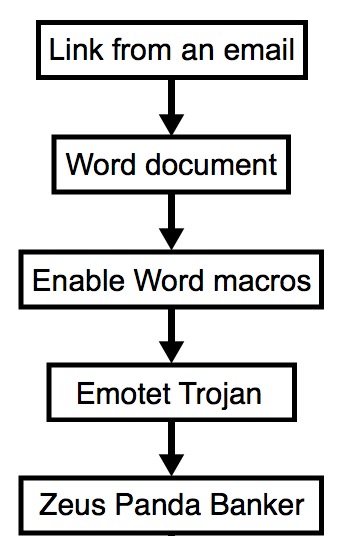
2018-01-09 - EMOTET INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-09-Emotet-infection-with-Zeus-Panda-Banker.pcap.zip 2.7 MB (2,682,442 bytes)
- 2018-01-09-Emotet-infection-with-Zeus-Panda-Banker.pcap (3,183,730 bytes)
- 2018-01-09-malware-from-Emotet-infection.zip 284.6 kB (284,603 bytes)
- 2018-01-08-Zeus-Panda-Banker-store.json.exe (172,032 bytes)
- 2018-01-09-Emotet-maldoc-sample-INCORRECT_INVOICE.doc (143,872 bytes)
- 2018-01-09-Emotet-sample-shedulecart.exe (151,552 bytes)
NOTES:
- I don't have an associated email today. In tweets tagged with#Emotet on Twitter, I found someone's Pastebin post and got a URL to kick off this infection chain.
- I haven't been recording the infection traffic long enough, because I should see Zeus Panda Banker after Emotet infections, as @iCyberFighter recently pointed out.
Shown above: Flowchart for today's Emotet infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domain:
- hxxp[:]//blog.flexsuplementos[.]com[.]br/erros/Outstanding-Invoices/
- hxxp[:]//www.brscan[.]com[.]br/informativo/vMh3t/
- hxxp[:]//www.evisu[.]co/C2Wg6s/
- hxxp[:]//www.ovk-grupp[.]ru/BoPc6/
- hxxp[:]//www.katinka[.]org/v8io1/
- rendomunza[.]gdn
- namingotslon[.]gdn
TRAFFIC
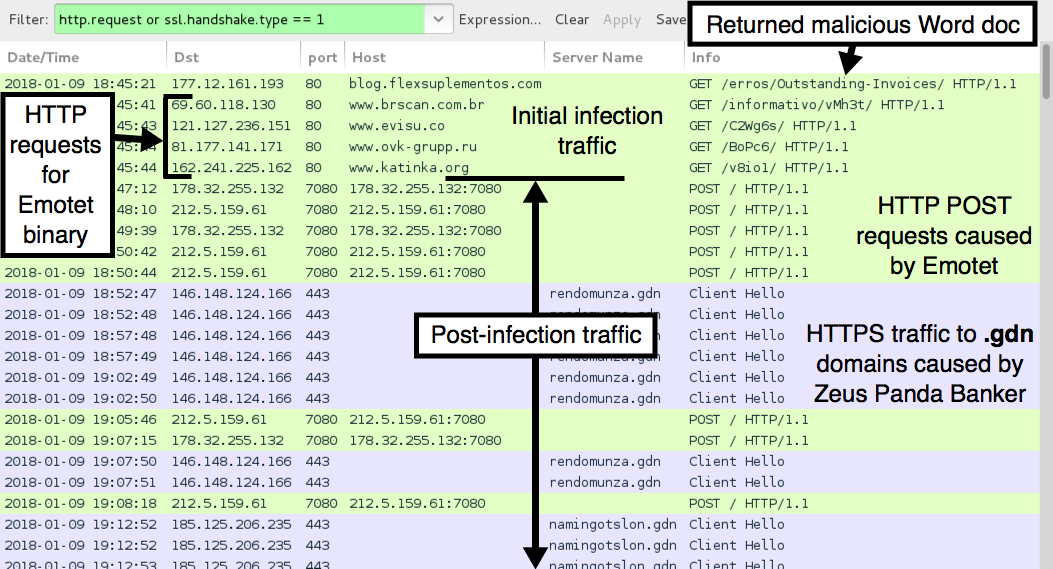
Shown above: Infection traffic filtered in Wireshark.
POST-INFECTION TRAFFIC:
- 177.12.161[.]193 port 80 - blog.flexsuplementos[.]com[.]br - GET /erros/Outstanding-Invoices/
- 69.60.118[.]130 port 80 - www.brscan[.]com[.]br - GET /informativo/vMh3t/
- 121.127.236[.]151 port 80 - www.evisu[.]co - GET /C2Wg6s/
- 81.177.141[.]171 port 80 - www.ovk-grupp[.]ru - GET /BoPc6/
- 162.241.225[.]162 port 80 - www.katinka[.]org - GET /v8io1/
- 69.16.193[.]12 port 4143 - Attempted TCP connections, no response from the server
- 178.32.255[.]132 port 7080 - 178.32.255[.]132:7080 - POST /
- 212.5.159[.]61 port 7080 - 212.5.159[.]61:7080 - POST /
- 146.148.124[.]166 port 443 - rendomunza[.]gdn - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- 185.125.206[.]235 port 443 - namingotslon[.]gdn - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- www.google.com - Connectivity check caused by Zeus Panda Banker
MALWARE
DOWNLOADED WORD DOC:
- SHA256 hash: 6e4a276dd2d745f57faa6e18ba90e255836ef4976c65cdfd831412b8ae4ab91c
File size: 143,872 bytes
File name: INCORRECT INVOICE.doc
EMOTET BINARY RETRIEVED BY THE WORD MACRO:
- SHA256 hash: 20061d675c927c3c43aa22d2589d7d2429de94b45d6fd4d25ea7f3d54be83cad
File size: 151,552 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\shedulecart.exe
ZEUS PANDA BANKER (KINS) RETRIEVED BY EMOTET:
- SHA256 hash: d68b860629e1ac2b3e0befe71957d3b23cc4229e07ecd1d33594c54d0df3b3ae
File size: 172,032 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
Click here to return to the main page.