2018-01-12 - NANOCORE RAT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2018-01-12-NanoCore-RAT-infection-traffic.pcap.zip 379.0 kB (379,003 bytes)
- 2018-01-12-NanoCore-RAT-infection-traffic.pcap (415,958 bytes)
- Zip archive of the email and malware: 2018-01-12-NanoCore-RAT-email-and-malware.zip 2.0 MB (1,956,920 bytes)
- 2018-01-11-NanoCore-RAT-malspam-0034-UTC.eml (635,772 bytes)
- TNT SHIPMENT INFORMATION.exe (1,968,344 bytes)
- TNT SHIPMENT INFORMATION.r14 (466,579 bytes)
- filename.exe (1,968,344 bytes)
- filename.vbs (1,016 bytes)
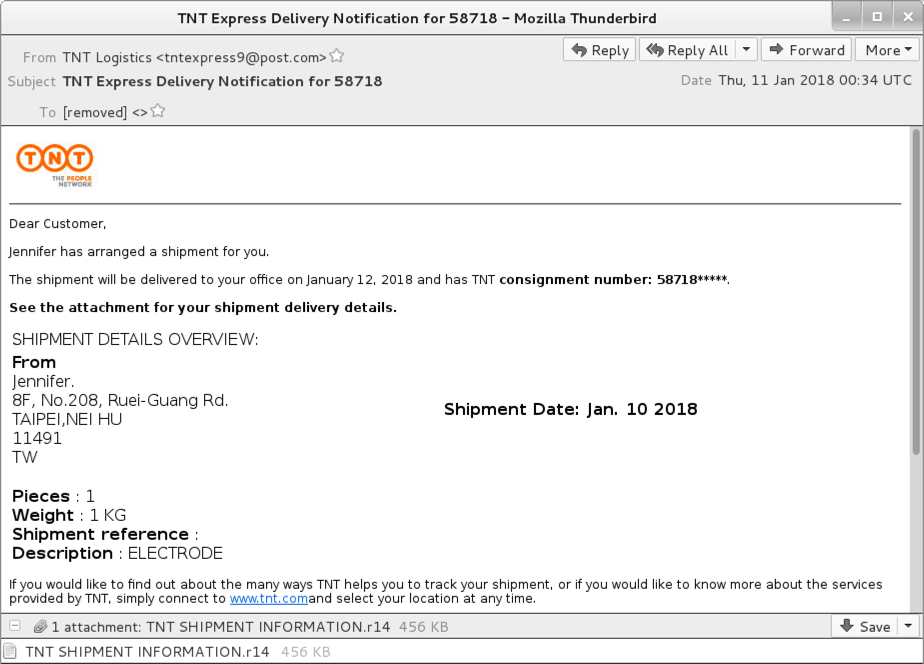
Shown above: Screenshot of the email.
EMAIL INFORMATION:
- Date: Thursday, 2018-01-10 at 00:34 UTC
- Subject: TNT Express Delivery Notification for 58718
- From: "TNT Logistics" <tntexpress9@post[.]com>
- Message-ID: <trinity-26dc5425-03cf-4e37-af49-ca5a58ee7118-1515630841229@3c-app-mailcom-lxa11>
- Attachment name: TNT SHIPMENT INFORMATION.r14
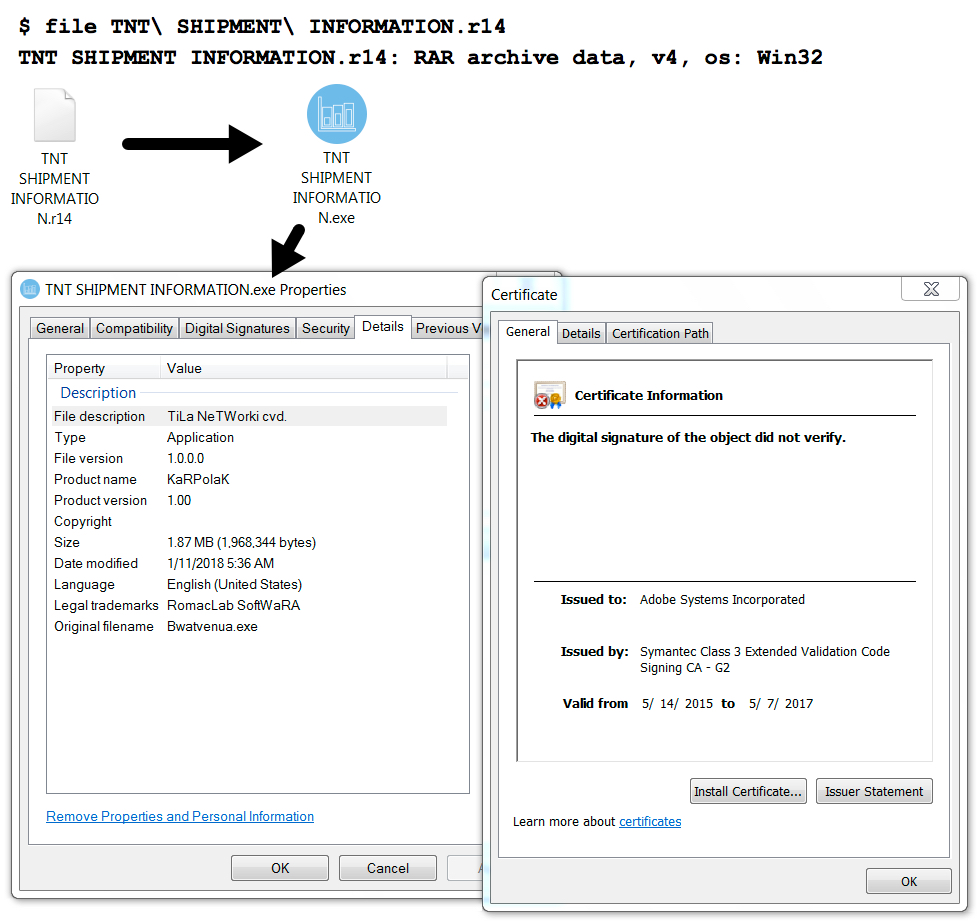
Shown above: Extracting the malware from the attached RAR archive.
TRAFFIC
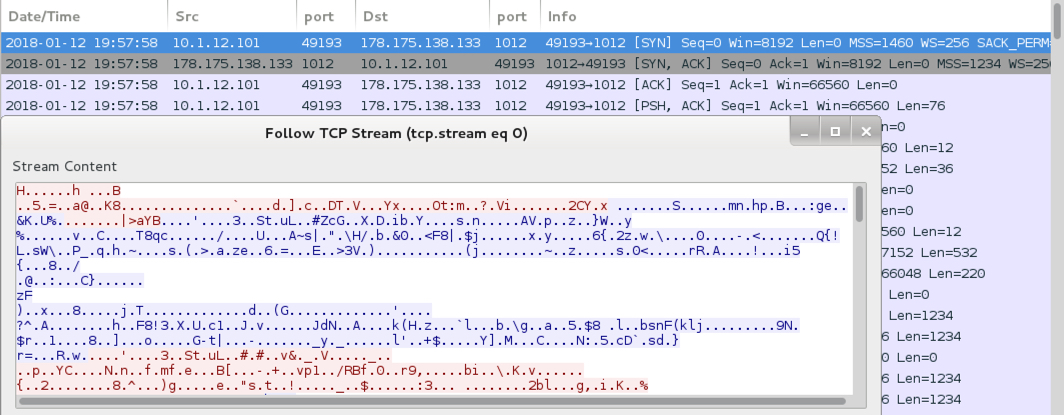
Shown above: Infection traffic filtered in Wireshark.
INFECTION TRAFFIC:
- 178.175.138[.]133 port 1012 - encoded or encrypted TCP traffic caused by NanoCore RAT
MALWARE
RAR ARCHIVE FROM LINK IN THE EMAIL:
- SHA256 hash: 6d9a8f316d3888ce833c47bd80fca2533a2a6997b76d89f3ab9d661bd5803ad5
File size: 466,579 bytes
File name: TNT SHIPMENT INFORMATION.r14
EXE FILE (NANOCORE RAT) EXTRACTED FROM THE RAR ARCHIVE:
- SHA256 hash: 95975fb33ea3a2488e9621baeba7468cfc5421562c0c5518cfe2d5d029e92fac
File size: 1,968,344 bytes
File name: TNT SHIPMENT INFORMATION.exe
NANOCORE RAT ARTIFACTS FROM THE INFECTED WINDOWS HOST:
- SHA256 hash: df0a89272b7d3879219cb69496c1c38e9827b679f7f4b881587665fd2e847c0e
File size: 1,968,344 bytes
File location: C:\Users\[username]\AppData\Local\Temp\subfolder\filename.exe
- SHA256 hash: [various hashes, depending on victim's Windows account name]
File size: approximately 1 kB
- File location: C:\Users\[username]\AppData\Local\Temp\subfolder\filename.vbs
WINDOWS REGISTRY ENTRY FOR PERSISTENCE:
- Registry Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Value name: Registry Key Name
- Value Type: REG_SZ
- Value Data: C:\Users\[username]\Local\Temp\subfolder\filename.vbs
IMAGES
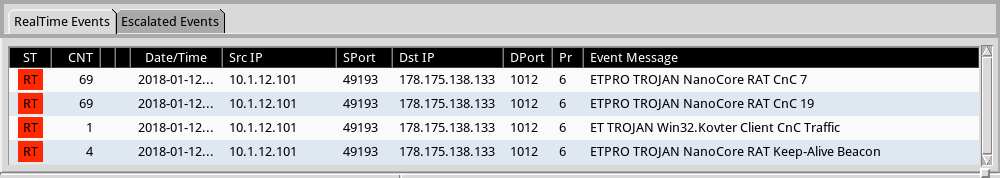
Shown above: Alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
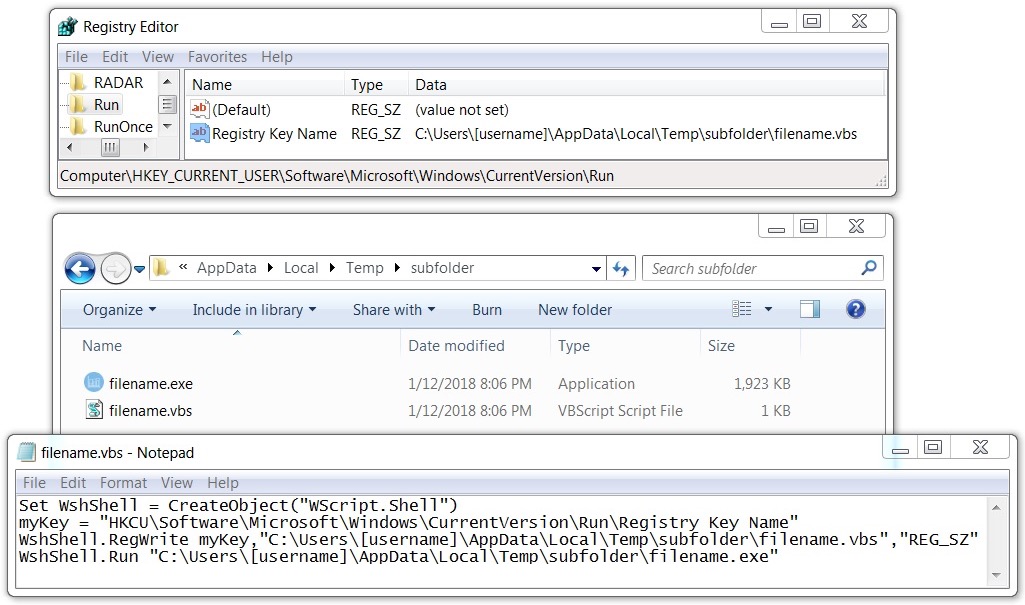
Shown above: Registry key and associated files on the infected Windows host.
Click here to return to the main page.
