2018-01-15 - FORMBOOK FROM CVE-2017-11882 RTF DOCUMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-15-Formbook-infection-traffic.pcap.zip 485.8 kB (485,763 bytes)
- 2018-01-15-Formbook-infection-traffic.pcap (791,092 bytes)
- 2018-01-15-malware-from-Formbook-infection.zip 221.0 kB (220,962 bytes)
- 2018-01-14-email-attachment-CVE-2017-11882-RTF-document.bin (50,274 bytes)
- 2018-01-14-Formbook-malspam-2137-UTC.eml (70,951 bytes)
- 2018-01-15-Formbook-executable.exe (292,792 bytes)
- 2018-01-15-all-malware-from-SMB-server.zip 2.8 MB (2,820,682 bytes)
- ad1.src (284,600 bytes)
- ad2.src (309,176 bytes)
- ap1.src (306,280 bytes)
- ap2.src (289,896 bytes)
- bnk.src (231,664 bytes)
- emm.src (239,856 bytes)
- frn.src (248,048 bytes)
- joe.src (292,792 bytes)
- kin.src (288,696 bytes)
- kri.src (292,792 bytes)
- min.src (314,472 bytes)
- pri.src (314,472 bytes)
- thg.src (302,184 bytes)
- tim.src (314,472 bytes)
- xpl.src (306,280 bytes)
NOTES:
- Today's malspam attachment is an RTF file disguised as a Microsoft Word document that uses an exploit for CVE-2017-11882.
- The exploit only requires that you open the RTF file using an out-of-date version of Microsoft Word on a vulnerable Windows host.
- The follow-up malware (Formbook) was retrieved using SMB (TCP port 445) from a shared drive at \\185.198.59[.]121\s.
- I previously documented another case of CVE-2017-11882 last year on 2017-12-13 (it was pushing Lokibot that time).
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and partial URLs:
- hxxp[:]//www.yg082[.]com/ch19/?id=
- hxxp[:]//www.www477234[.]com/ch19/?id=
- hxxp[:]//www.pmeglobal[.]com/ch19/?id=
- hxxp[:]//www.julianshots[.]com/ch19/?id=
- hxxp[:]//www.egiztechnologyx[.]com/ch19/?id=
- hxxp[:]//www.769hqi[.]info/ch19/?id=
- hxxp[:]//www.choruscallasia[.]tech/ch19/?id=
- hxxp[:]//www.lifullness[.]com/ch19/?id=
- hxxp[:]//www.goldenmindbody[.]com/ch19/?id=
- hxxp[:]//www.bjxitianyun[.]com/ch19/?id=
- hxxp[:]//www.tqceyp[.]info/ch19/?id=
- www.spinepoint[.]biz
- www.0t5fivethan[.]men
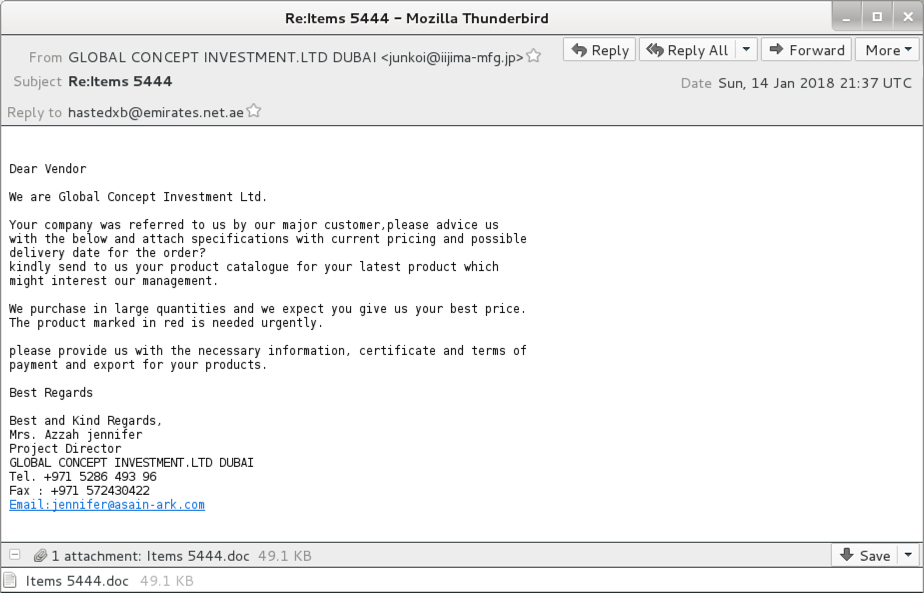
Shown above: Screenshot of the email.
EMAIL INFORMATION:
- Date: Sunday, 2018-01-14 at 21:37 UTC
- Subject: Re:Items 5444
- From: "GLOBAL CONCEPT INVESTMENT.LTD DUBAI" <junkoi@iijima-mfg[.]jp>
- Received: from v133-130-68-111.myvps.jp (v133-130-68-111.myvps[.]jp [133.130.68[.]111])
- Message-ID: <5aae29598e665cb24fb47681e4d09003.squirrel@webmail.iijima-mfg[.]jp>
- Reply-To: hastedxb@emirates[.]net[.]ae
- Attachment name: Items 5444.doc
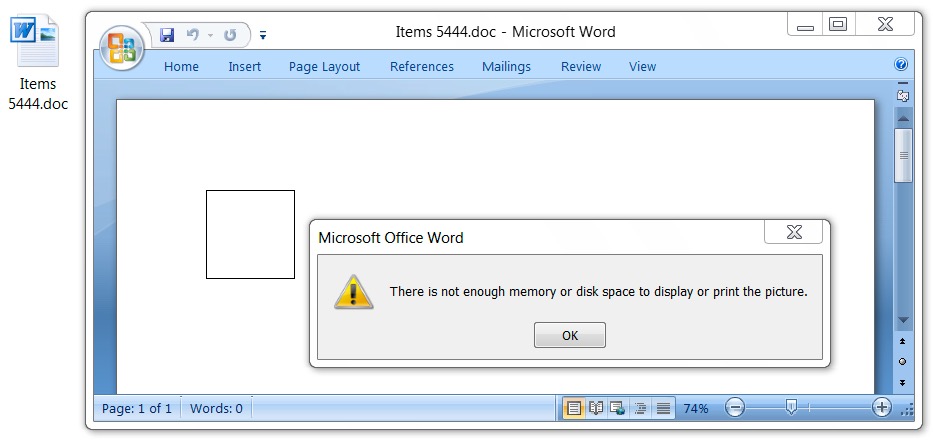
Shown above: Opening the RTF file in Microsoft Word gives you a fake popup notification to distract you from the infection that's happening.
TRAFFIC
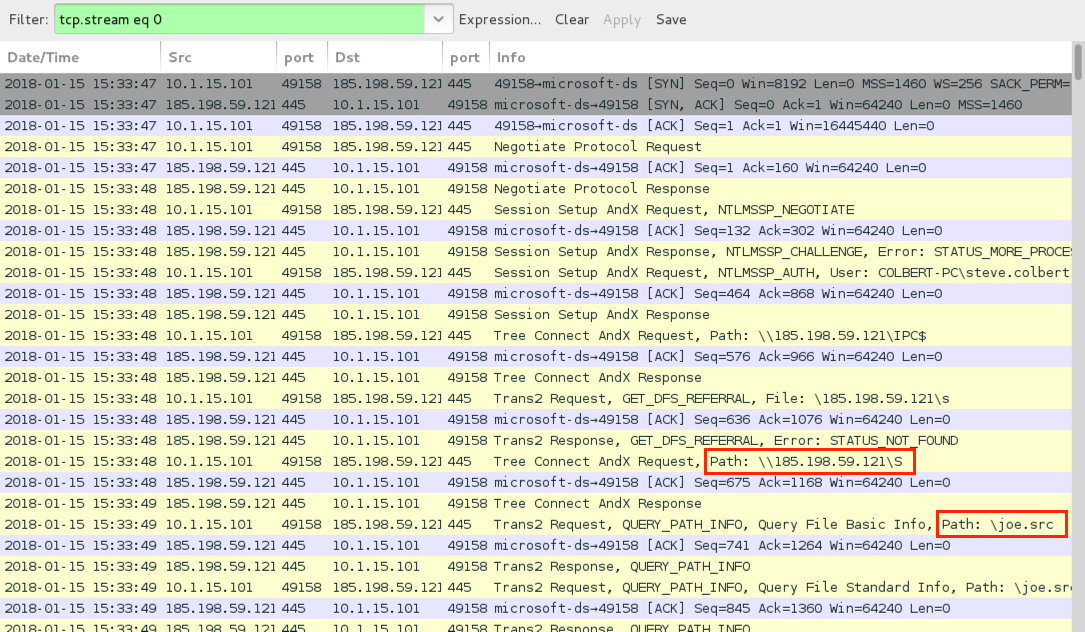
Shown above: SMB traffic to retreive the follow-up malware as seen in Wireshark.
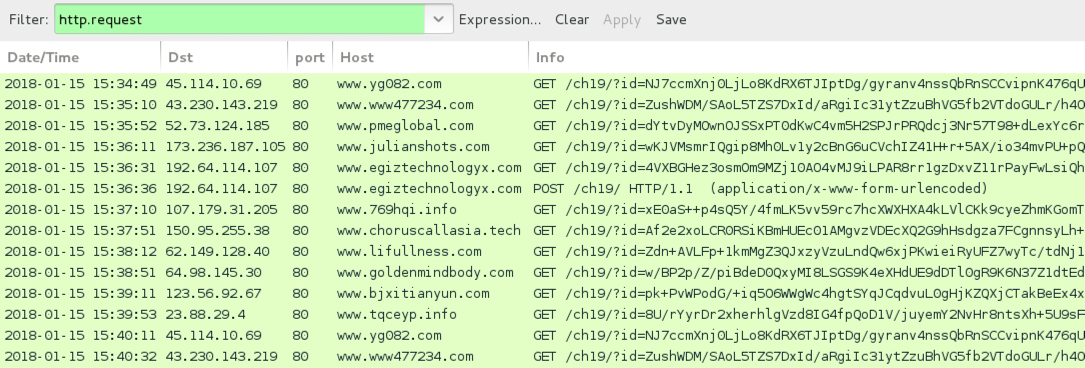
Shown above: HTTP traffic caused by the Formbook info stealer.
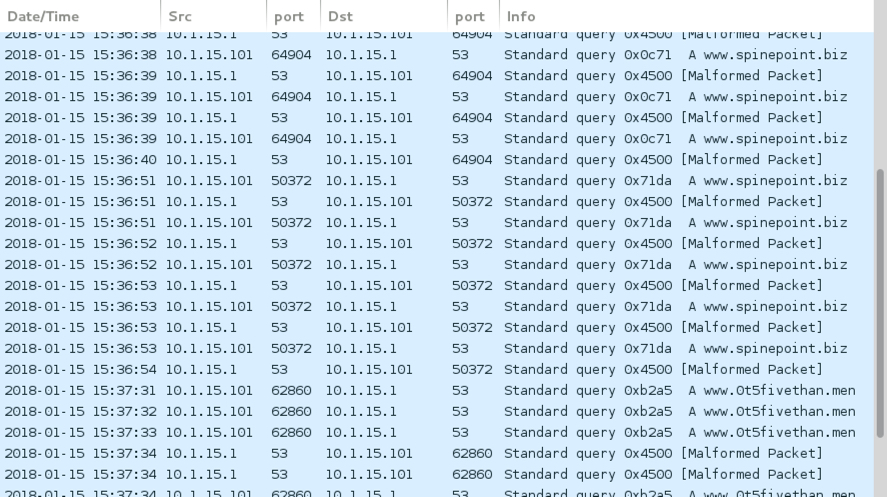
Shown above: DNS responses for two domains were malformed.
INFECTION TRAFFIC:
- 185.198.59[.]121 port 445 - SMB traffic generated by CVE-2017-11882 Word doc to retrieved follow-up malware
- 45.114.10[.]69 port 80 - www.yg082[.]com - GET /ch19/?id=[long string]==&sLNh=zPQlgBOhWfKdzF
- 43.230.143[.]219 port 80 - www.www477234[.]com - GET /ch19/?id=[long string]==&sLNh=zPQlgBOhWfKdzF&sql=1
- 52.73.124[.]185 port 80 - www.pmeglobal[.]com - GET /ch19/?id=[long string]==&sLNh=zPQlgBOhWfKdzF
- 173.236.187[.]105 port 80 - www.julianshots[.]com - GET /ch19/?id=[long string]==&sLNh=zPQlgBOhWfKdzF
- 192.64.114[.]107 port 80 - www.egiztechnologyx[.]com - GET /ch19/?id=[long string]==&sLNh=zPQlgBOhWfKdzF
- 192.64.114[.]107 port 80 - www.egiztechnologyx[.]com - POST /ch19/
- 107.179.31[.]205 port 80 - www.769hqi[.]info - GET /ch19/?id=[long string]==&sLNh=zPQlgBOhWfKdzF
- 150.95.255[.]38 port 80 - www.choruscallasia[.]tech - GET /ch19/?id=[long string]==&sLNh=zPQlgBOhWfKdzF
- 62.149.128[.]40 port 80 - www.lifullness[.]com - GET /ch19/?id=[long string]==&sLNh=zPQlgBOhWfKdzF
- 64.98.145[.]30 port 80 - www.goldenmindbody[.]com - GET /ch19/?id[long string]==&sLNh=zPQlgBOhWfKdzF
- 123.56.92[.]67 port 80 - www.bjxitianyun[.]com - GET /ch19/?id=[long string]==&sLNh=zPQlgBOhWfKdzF
- 23.88.29[.]4 port 80 - www.tqceyp[.]info - GET /ch19/?id=[long string]==&sLNh=zPQlgBOhWfKdzF
- DNS queries for www.spinepoint[.]biz that returned malformed response
- DNS queries for www.0t5fivethan[.]men that returned malformed response
MALWARE
EMAIL ATTACHMENT - RTF USING EXPLOIT FOR CVE-2017-11882:
- SHA256 hash: 5b307600b1ceb84f29315c95e5b21776eb6154b79214528629e4fc2310cd50e3
File size: 50,274 bytes
File name: Items 5444.doc
FORMBOOK MALWARE RETRIEVED FROM 185.198.59[.]121 OVER SMB:
- SHA256 hash: 3f83a4ff3803dffbed605a82e30f79e39620ded61bd4a09b8e1abd08ec4c2ecb
File size: 292,792 bytes
File location: \\185.198.59[.]121\s\joe.src
File location: C:\Program Files\V7n7l_rn0\mrxhxjot.exe
OTHER MALWARE FROM \\185.198.59[.]121\S:
- SHA256 hash: 3a55297697608f546edb2bc6cd45d8bfbda6080c68824976fb983c4448272705 - ad1.src
- SHA256 hash: 7eab92ce6b13221cb8f280da249df28503beb141197e5c0534dd76457f42a915 - ad2.src
- SHA256 hash: d917fc781c4a69b5c77c63afce20f3055c7f21d5e48d3aa033851e2d5167e87c - ap1.src
- SHA256 hash: 79044d29c331fa75a08f55a92ba18b48dd96ccc3814ab2586ff6d4448e859aee - ap2.src
- SHA256 hash: 2d3294ea7046f87e8675d6632edc643645862b5bd8c581b1d4811ea7c3394fab - bnk.src
- SHA256 hash: dcd346ca948ab0cbd1e3acb3107caee62e53e9e5805722c1555d0d277a1cb001 - emm.src
- SHA256 hash: 7be2ef0b3c88e508404b408b437ef1537c4cd9bcd11ca097e089b7211a110f5c - frn.src
- SHA256 hash: bf9b9c3cd391104a1398d685a7e08412b7cfdda6c44d5c874ff117947467f97d - kin.src
- SHA256 hash: 635e5d23fe5caa9ccd951391f5a927a883f0a4500b4a9b880d2bf2190aa9c932 - kri.src
- SHA256 hash: 32d481d669217370b0090f9c7efe1b8f911d198f6b6c77521cef660b5e411ec0 - min.src
- SHA256 hash: e4185b89d3b55f32677841c0b4e3d14c7e608e39c8b9e0349547cfcc54c9e8c9 - pri.src
- SHA256 hash: ee9daf2cd61ef475fe4adc9856d6202ff9921e346af0ad74304ce987f80cc314 - thg.src
- SHA256 hash: a00127d8b50411deaad498541496de2ad7e74cfd0f7241d887de37b71badb0fd - tim.src
- SHA256 hash: 3ea6830d62856acba5023f049bef88bedfe30539635ed7098ff120a0f55ed634 - xpl.src
IMAGES
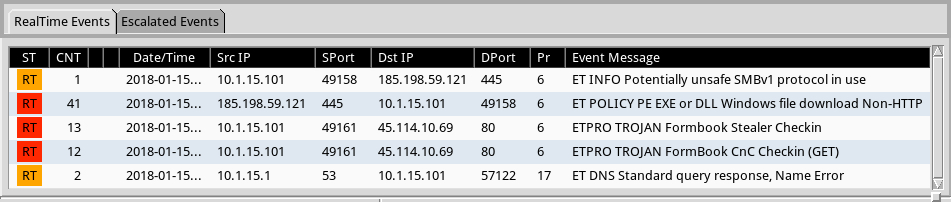
Shown above: Alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
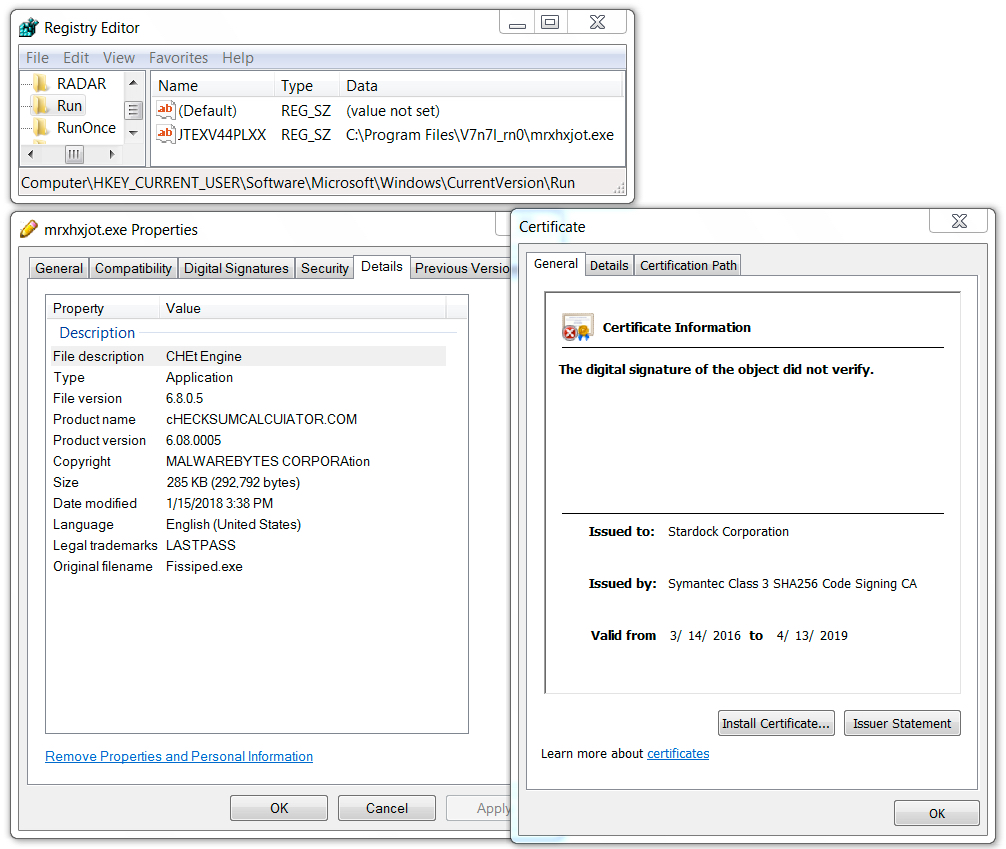
Shown above: Registry key and associated Formbook malware on the infected Windows host.
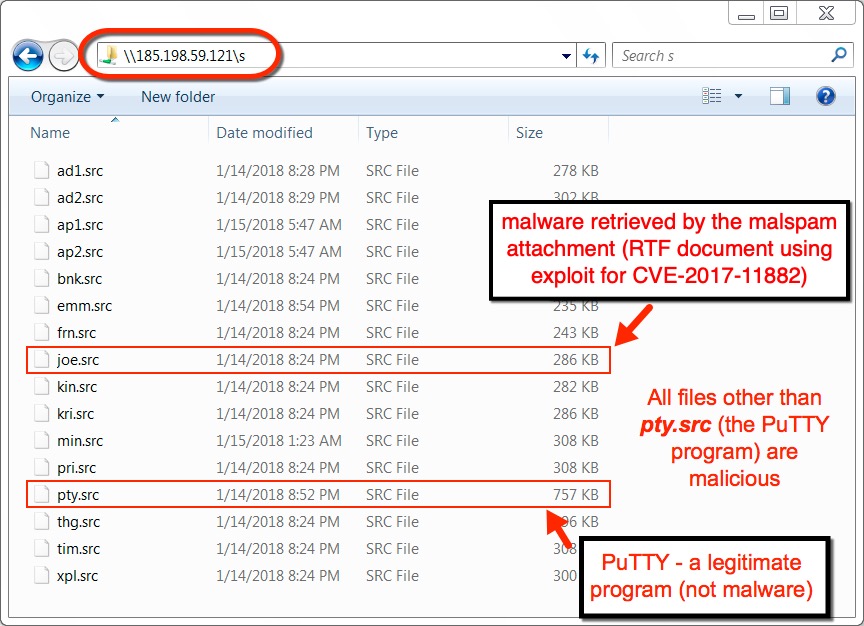
Shown above: You can easily connect to the shared drive on 185.198.59[.]121 and see more malware.
Shown above: Although the file extensions are all .src, they are all Windows executable files.
Click here to return to the main page.
