2018-01-19 - THREE RECENT EXAMPLES OF NGAY CAMPAIGN RIG EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-19-three-pcaps-from-Ngay-campaign-Rig-EK.zip 4.0 MB (4,046,115 bytes)
- 2018-01-12-Rig-EK-sends-SmokeLoader-sends-Monero-coinminer.pcap (3,183,941 bytes)
- 2018-01-14-Rig-EK-sends-Monero-coinminer.pcap (974,045 bytes)
- 2018-01-19-Rig-EK-sends-Remcos-RAT.pcap (341,560 bytes)
- 2018-01-19-malware-and-artifacts-from-Ngay-campaign-Rig-EK.zip 3.6 MB (3,591,125 bytes)
- 2018-01-12-Monero-post-infection-artifact-RotlLipoma.cab (754,387 bytes)
- 2018-01-12-Monero-post-infection-artifact-garibaldis.dll (65,536 bytes)
- 2018-01-12-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2018-01-12-Rig-EK-flash-exploit.swf (13,806 bytes)
- 2018-01-12-Rig-EK-landing-page.txt (96,839 bytes)
- 2018-01-12-Rig-EK-payload-SmokeLoader.exe (129,080 bytes)
- 2018-01-12-follow-up-malware-Monero-coinminer.exe (849,985 bytes)
- 2018-01-14-Monero-post-infection-artifact-Biogen.cab (754,105 bytes)
- 2018-01-14-Monero-post-infection-artifact-Romaic.dll (86,016 bytes)
- 2018-01-14-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2018-01-14-Rig-EK-flash-exploit.swf (13,796 bytes)
- 2018-01-14-Rig-EK-landing-page.txt (96,787 bytes)
- 2018-01-14-Rig-EK-payload-Monero-coinminer.exe (855,963 bytes)
- 2018-01-19-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2018-01-19-Rig-EK-flash-exploit.swf (13,836 bytes)
- 2018-01-19-Rig-EK-landing-page.txt (96,812 bytes)
- 2018-01-19-Rig-EK-payload-Remcos-RAT.exe (171,520 bytes)
NOTES:
- This is likely the "Ngay" campaign first documented by @nao_sec on 2017-12-11 at http://www.nao-sec.org/2017/12/survey-of-ngay-campaign.html
- My previous most-recently document example of this campaign was on Thursday 2018-01-11. See that write-up for more details.
- Different domains on 88.99.48[.]65 are fake porn domains used by this campaign as a gate to Rig EK.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains:
- saumottam[.]ru
- hxxp[:]//104.236.16[.]69/mnnst.exe
- proqnoz[.]ga
- top.geezy1[.]xyz
TRAFFIC
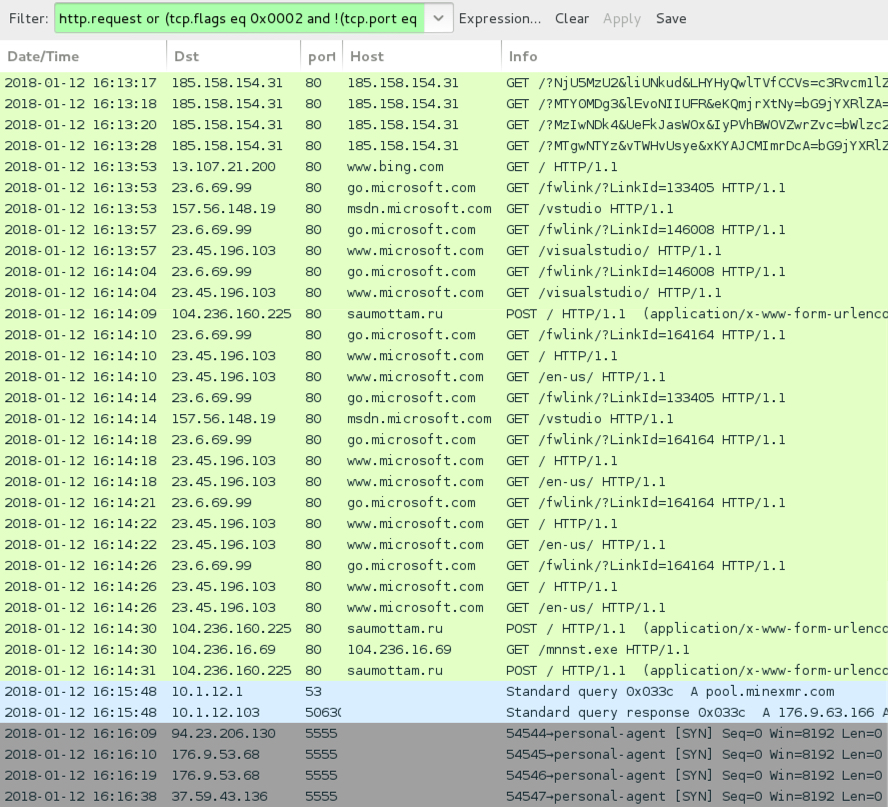
Shown above: Ngay campaign Rig EK from Friday 2018-01-12.
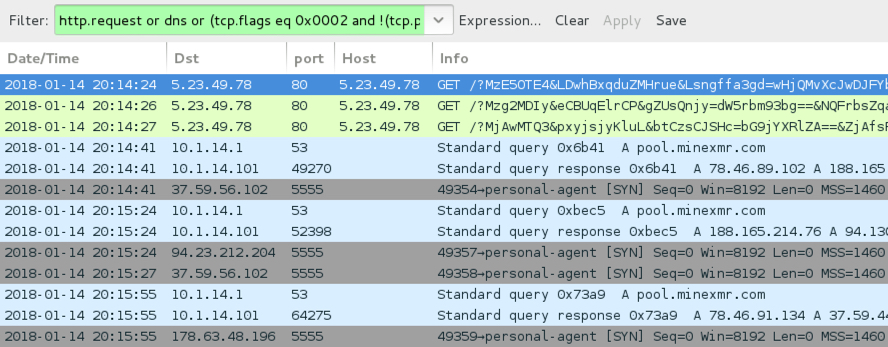
Shown above: Ngay campaign Rig EK from Monday 2018-01-14.
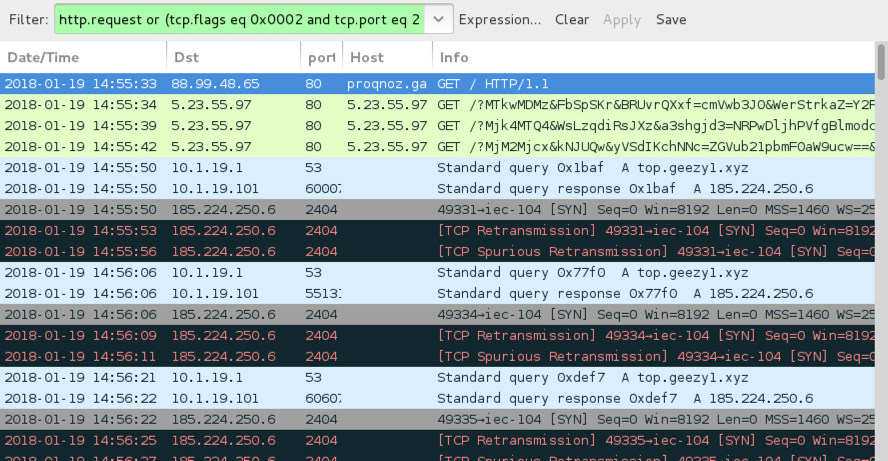
Shown above: Ngay campaign Rig EK from Friday 2018-01-19.
FRIDAY 2018-01-12:
- 185.158.154[.]31 port 80 - 185.158.154[.]31 - Rig EK
- www.bing[.]com - GET / (caused by SmokeLoader but not malicious)
- go.microsoft[.]com - GET /fwlink/?LinkId=133405 (caused by SmokeLoader but not malicious)
- go.microsoft[.]com - GET /fwlink/?LinkId=146008 (caused by SmokeLoader but not malicious)
- go.microsoft[.]com - GET /fwlink/?LinkId=164164 (caused by SmokeLoader but not malicious)
- msdn.microsoft[.]com - GET /vstudio (caused by SmokeLoader but not malicious)
- www.microsoft[.]com - GET /visualstudio/ (caused by SmokeLoader but not malicious)
- www.microsoft[.]com - GET / (caused by SmokeLoader but not malicious)
- www.microsoft[.]com - GET /en-us/ (caused by SmokeLoader but not malicious)
- 104.236.160[.]225 port 80 - saumottam[.]ru - POST / (SmokeLoader check-in)
- 104.236.16[.]69 port 80 - 104.236.16[.]69 - GET /mnnst.exe
- 37.59.43[.]136 port 5555 - pool.minexmr[.]com - Monero coin miner traffic
- 94.23.206[.]130 port 5555 - pool.minexmr[.]com - Monero coin miner traffic
- 176.9.53[.]68 port 5555 - pool.minexmr[.]com - Monero coin miner traffic
MONDAY 2018-01-14:
- 5.23.49[.]78 port 80 - 5.23.49[.]78 - Rig EK
- 37.59.56[.]102 port 5555 - pool.minexmr[.]com - Monero coin miner traffic
- 94.23.212[.]204 port 5555 - pool.minexmr[.]com - Monero coin miner traffic
- 178.63.48[.]196 port 5555 - pool.minexmr[.]com - Monero coin miner traffic
FRIDAY 2018-01-19:
- 88.99.48[.]65 port 80 - proqnoz[.]ga - GET / (fake porn domain used as gate by Ngay campaign)
- 5.23.55[.]97 port 80 - 5.23.55[.]97 - Rig EK
- 185.224.250[.]6 port 2404 - top.geezy1[.]xyz - RemcosRAT callback traffic
FILE HASHES
RIG EK FLASH EXPLOITS:
- SHA256 hash: 38d12d6c41bcb02535951706bfdadcf271839b9a964c1840c8f612bef1c90158 - 2018-01-12 Rig EK Flash exploit
- SHA256 hash: 2e995e8636d8a334913d5ea2061c6a7dee1924cb0febe75e8c435cbe77fbb248 - 2018-01-14 Rig EK Flash exploit
- SHA256 hash: f98de469c0e70bec1a58a47b1cc9ed73cf3791e14f3b7a7b25075781efa9c366 - 2018-01-19 Rig EK Flash exploit
RIG EK PAYLOADS OR FOLLOW-UP MALWARE:
- SHA256 hash: 9566f2a94e92acda0a895fde2363fd3da8e46c146bae389b680f52ef68f3cfe3 - 2018-01-12 Rig EK payload: SmokeLoader
- SHA256 hash: 68ba050bc8dba981d55c1b543d999239b0fdf552b180042accd6fa30624c97d8 - 2018-01-12 follow-up malware: Monero coin miner
- SHA256 hash: 3516aaab0bf1d26c8b2a2d64a782ac0d96e38ebe615d6f5e48063589c8272226 - 2018-01-14 Rig EK payload: Monero coin miner
- SHA256 hash: ff92829dfb4bba5730f8cdf860db9a64751a3d7c318b6adc0fa8b26a3a06086f - 2018-01-19 Rig EK payload: Remcos RAT
Click here to return to the main page.
