2018-01-22 - SMOKELOADER INFECTION WITH OTHER MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-22-SmokeLoader-infection-with-other-malware.pcap.zip 4.1 MB (4,067,755 bytes)
- 2018-01-22-SmokeLoader-infection-with-other-malware.pcap (6,040,488 bytes)
- 2018-01-22-SmokeLoader-and-other-malware-from-the-infection.zip 1.9 MB (1,875,758 bytes)
- 2018-01-22-GlobeImposter-READ__ME.html (2,808 bytes)
- 2018-01-22-GlobeImposter-artifact-tmp3AFC.tmp.bat.txt (448 bytes)
- 2018-01-22-GlobeImposter-decryptor-style.css (1,930 bytes)
- 2018-01-22-GlobeImposter-decryptor.html (9,180 bytes)
- 2018-01-22-GlobeIposter-ransomware-sample.exe (286,720 bytes)
- 2018-01-22-Smoke-Loader-sample.exe (286,720 bytes)
- 2018-01-22-Zeus-Panda-Banker-sample.exe (1,104,896 bytes)
- 2018-01-22-another-executable-retrieved-from-the-pcap.exe (568,832 bytes)
NOTES:
- The source is malspam with a Word document attachment containing a malicious macro that requires PowerShell 3.0 to run properly.
- This was a real messy infection, and I wasn't able to isolate the coin miner malware and replicate that specific traffic.
RECENT DOCUMENTATION:
- 2017-11-19 - Internet Storm Center (ISC) - Resume-themed malspam pushing Smoke Loader
- 2017-12-20 - My Online Security - More Resume malspam with password protected word doc attachments continue to deliver a variety of different malware
- 2018-01-22 - My Online Security - Website Job Application resume malspam continues to deliver Smoke / Sharik trojan
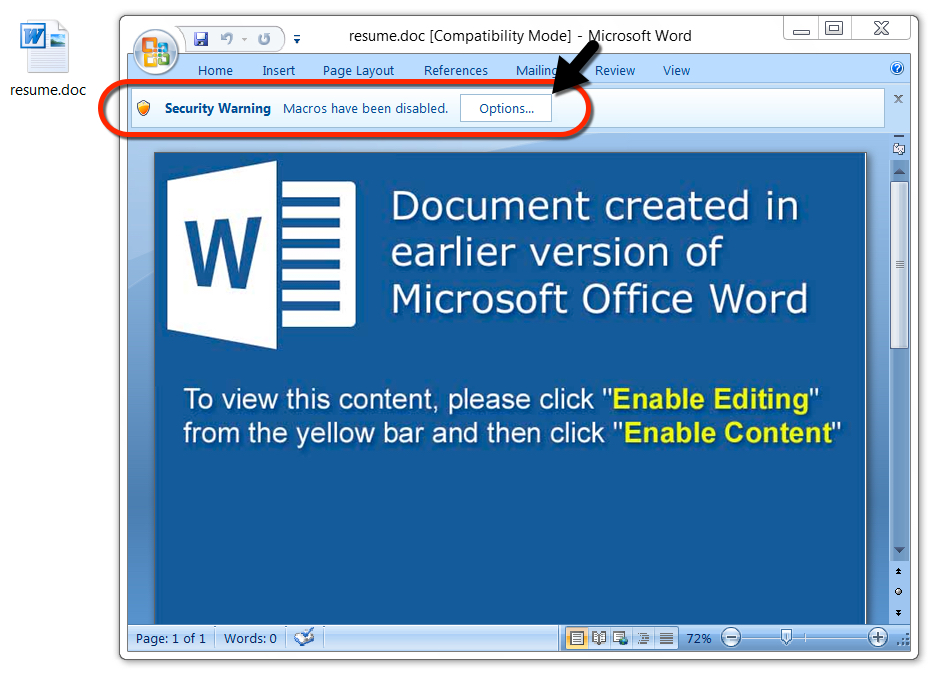
Shown above: The malicious Word document.
Shown above: The messiness of an infected Windows host from that Word document.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URL and domains:
- hxxp[:]//80.82.67[.]217/poop.jpg
- microsoftoutlook[.]bit
- dorraldps[.]top
- bcwfga5ssxh3jrlp[.]onion
TRAFFIC

Shown above: Traffic caused by macro from the Word document.
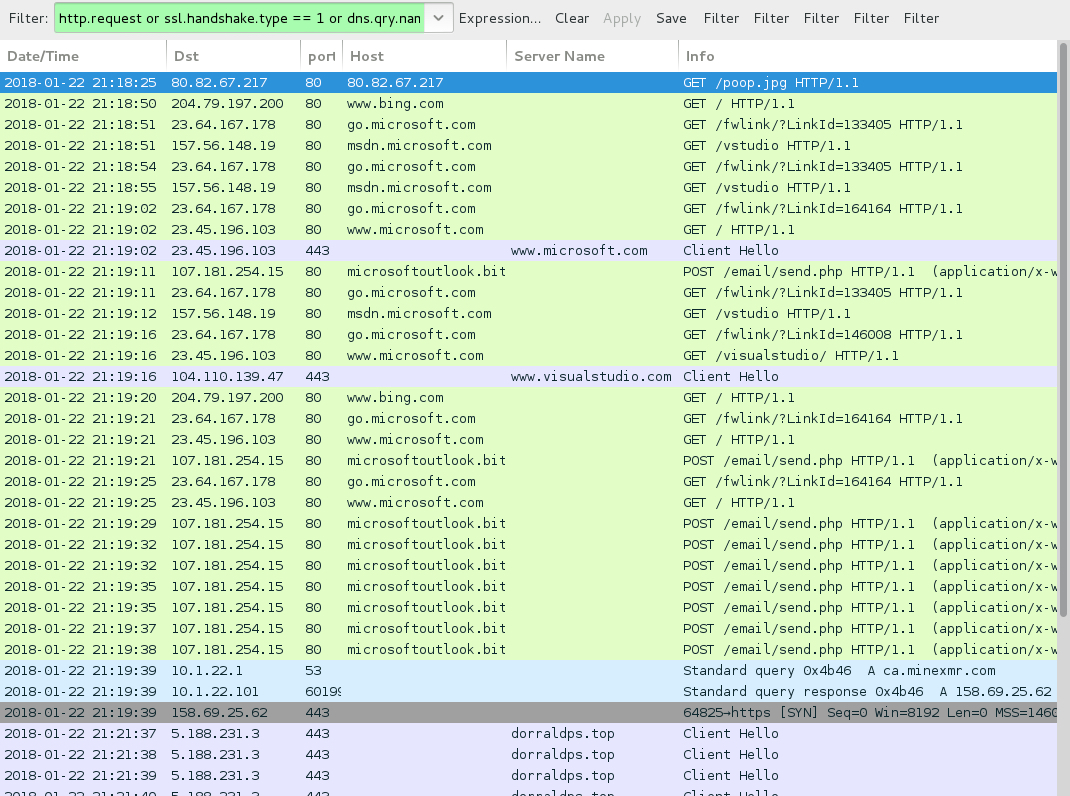
Shown above: Traffic from an infected Windows host filtered in Wireshark.
MALICIOUS TRAFFIC:
- 80.82.67[.]217 port 80 - 80.82.67[.]217 - GET /poop.jpg
- 107.181.254[.]15 port 80 - microsoftoutlook[.]bit - POST /email/send.php - Smoke Loader/Sharik traffic
- 158.69.25[.]62 port 443 - ca.minexmr[.]com - Coinminer traffic (proabably for Monero)
- 5.188.231[.]3 port 443 - dorraldps[.]top - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- bcwfga5ssxh3jrlp[.]onion - GET /shfgealjh.php (GlobeImposter devs forgot to put .link after .onion in the URL)
FILE HASHES
ORIGINAL DOCUMENT:
- SHA256 hash: 3f64519c0d543c39a62ac71893bb7e028b5eb96cfa3b261efb29a880cc8c7a21
File size: 100,864 bytes
File name: resume.doc
File description: Word document with malicious macros to download/install Smoke Loader (Sharik)
FOLLOW-UP MALWARE:
- SHA256 hash: c795650baf72f201a871feffa65760aee2a75e3ce75d3b5871199b8aaef1b870
File size: 286,720 bytes
File location: hxxp[:]//80.82.67[.]217/poop.jpg
File description: 2018-01-22 Smoke Loader (Sharik) sample
- SHA256 hash: 3e14353ab3b35d228db287d2a3cac79bc5a7264c57f634c023946db2b9096602
File size: 286,720 bytes
File description: 2018-01-22 GlobeIposter ransomware sample
- SHA256 hash: b22b86daccd03921c5ec3c88ed636be0389611a5aaf81b4a995cf2ba9fc09356
File size: 286,720 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File description: 2018-01-22 Zeus Panda Banker (KINS) sample
- SHA256 hash: 2b83c69cf32c5f8f43ec2895ec9ac730bf73e1b2f37e44a3cf8ce814fb51f120
File location: C:\Users\[username]\AppData\Local\Temp\[3 or 4 random hex digits].tmp\wuauclt.exe
File size: 568,832 bytes
File description: A legitimate system file, a Windows update tool, returned from microsoftoutlook.bit during HTTP POST traffic
- SHA256 hash: 2105f0ec180e17a93e93981d1041835588ee23c80328e05818815f2fc7dbacda
File size: 1,066,496 bytes
File location: C:\Users\[username]\AppData\Local\Temp\68FF.tmp.exe
File description: Unknown. I can't make it do anything useful in a dynamic environment on its own.
IMAGES
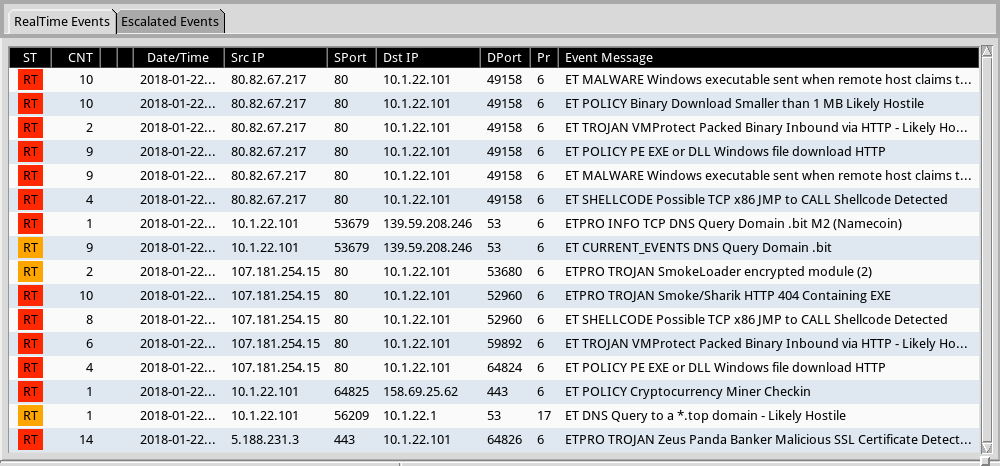
Shown above: Alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
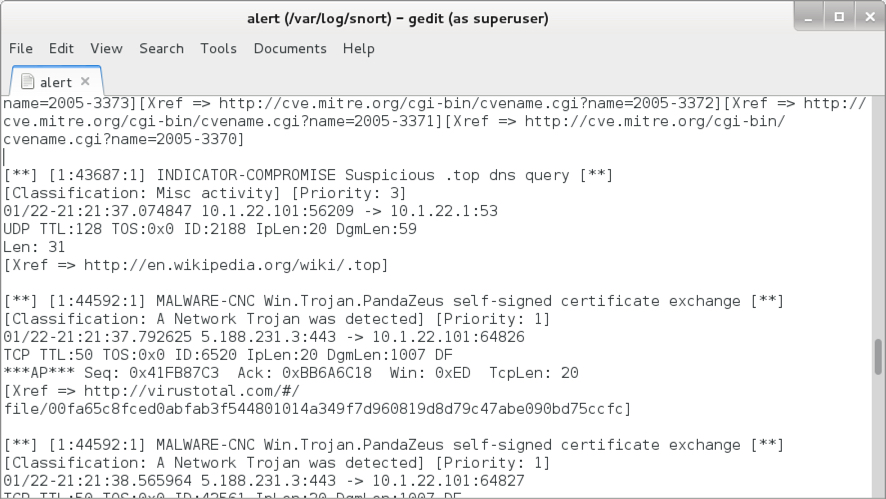
Shown above: Some alerts on the infection traffic from the Snort subscriber ruleset when reading the pcap with Snort 2.9.11.1
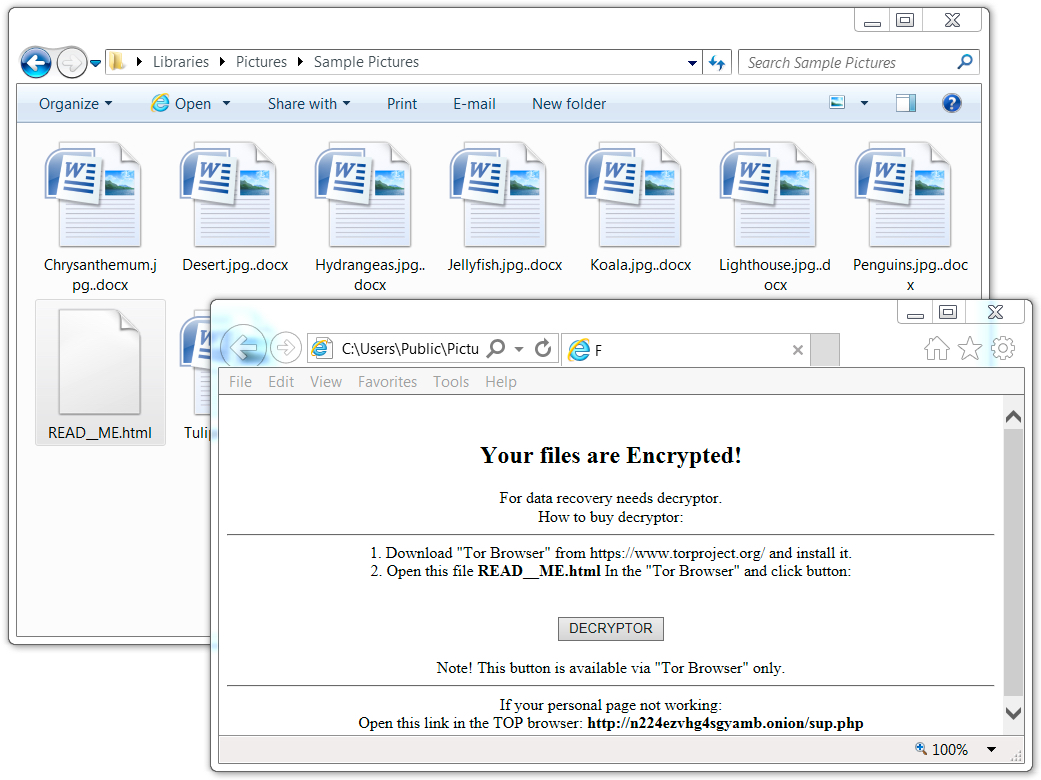
Shown above: GlobeImposter ransomware now more VM aware, and it uses a ..docx file extension for encrypted files.
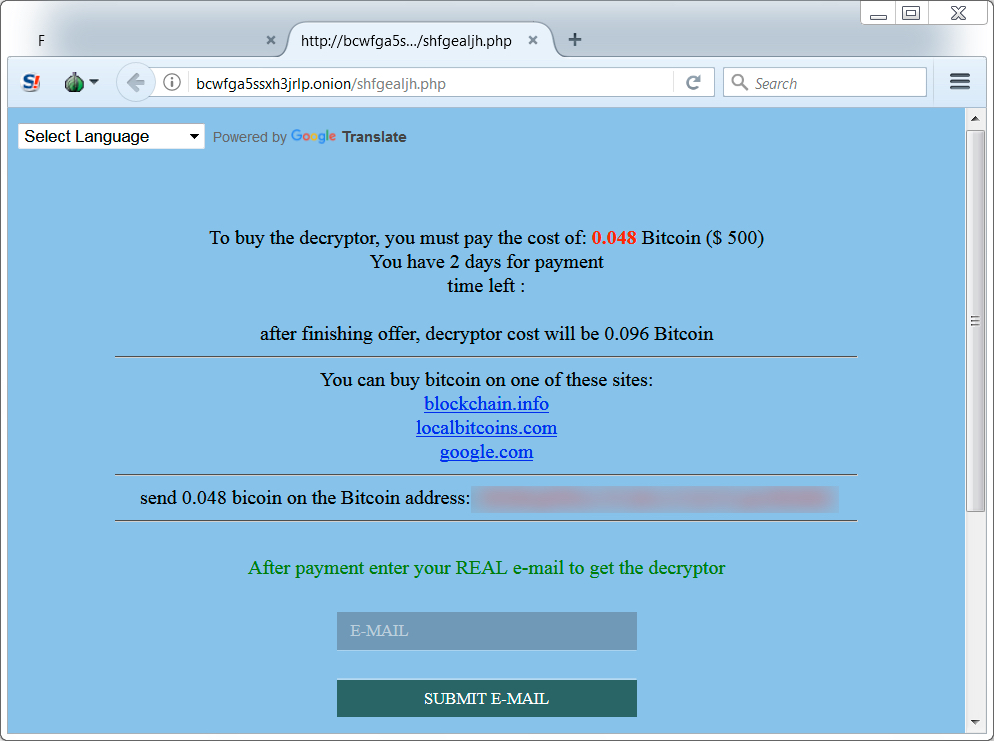
Shown above: Had to open the decryption instructions in a Tor browser to get to the follow-up decryptor page.
Click here to return to the main page.