2018-01-24 - QUICK POST: HANCITOR INFECTION WITH ZEUS PANDA BANKER AND SEND SAFE ENTERPRISE (SSE) SPAMBOT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-01-24-Hancitor-infection-with-Zeus-Panda-Banker-and-SSE-spambot.pcap.zip 4.6 MB (4,554,149 bytes)
- 2018-01-24-Hancitor-infection-with-Zeus-Panda-Banker-and-SSE-spambot.pcap (9,461,350 bytes)
- Zip archive of the emails: 2018-01-24-Hancitor-malspam-12-examples.txt.zip 2.2 kB (2,168 bytes)
- 2018-01-24-Hancitor-malspam-12-examples.txt (25,671 bytes)
- Zip archive of the malware: 2018-01-24-malware-from-Hancitor-infection.zip 1.9 MB (1,858,264 bytes)
- 2018-01-24-Hancitor-RTF-sample-invoice_254455.doc (156,854 bytes)
- 2018-01-24-Hancitor-decoded-from-base64-string-in-RTF-file.exe (41,472 bytes)
- 2018-01-24-Zeus-Panda-Banker-sample.exe (204,800 bytes)
- 2018-01-24-follow-up-malware-SSE-installer.exe (2,040,320 bytes)
NOTES:
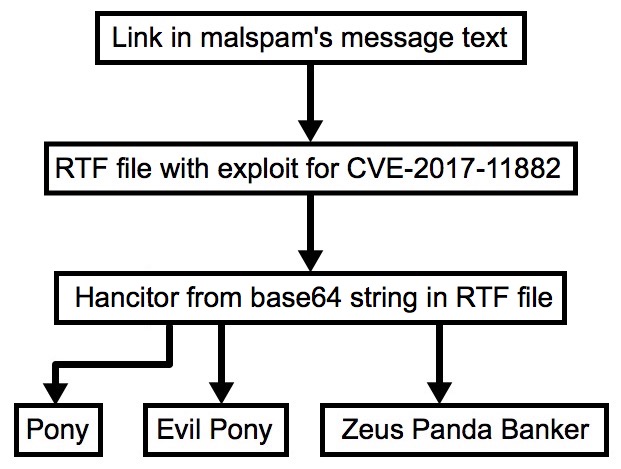
- I wrote an ISC diary covering yesterday's Hancitor: RTF files for Hancitor utilize exploit for CVE-2017-11882
- Read that diary for a better understanding of today's traffic.
- There are two differences in Today's Hancitor compared to yesterday:
1) Script with the base64 string for the Hancitor binary was embedded in the RTF file instead of being retrieved from a server.
2) My infected lab host spewed a great deal of additional Hancitor malspam in the post-infection SMTP traffic.
- Zip files are password-protected. If you don't know the password, look at the "about" page of this website.
INDICATORS:
EMAIL INFO: - Subject: Shipment status changed for parcel #1234! - From: usps@ncasef[.]com BLOCK LIST FROM INDICATORS IN THE PCAP: - 777rent[.]com - boxerproperty[.]info - boxerworkstyle[.]net - buildmyofficespace[.]com - buildyourofficespace[.]com - cheap-office-space[.]net - denver-office-space[.]net - el-paso-office-space[.]com - houston-executive-suites[.]net - jbaportfolio[.]com - naveundpa[.]com - suptalefthed[.]ru - hxxp[:]//www.dressedfortime[.]com/wp-content/plugins/title-and-nofollow-for-links/inc/1 - hxxp[:]//www.dressedfortime[.]com/wp-content/plugins/title-and-nofollow-for-links/inc/2 - hxxp[:]//www.dressedfortime[.]com/wp-content/plugins/title-and-nofollow-for-links/inc/3 - hxxp[:]//store.firmbarbershop[.]com/wp-content/plugins/custom-firmshop/62b.exe MALWARE: - SHA256 hash: b489ca02dcea8dc7d5420908ad5d58f99a6fef160721dcecfd512095f2163f7a - Description: 2018-01-24 Hancitor RTF sample: invoice_254455.doc - SHA256 hash: e205b987b1faa34dc3457c76299779f5b1fe604a276cf578fc5642e708be5f12 - Description: 2018-01-24 Hancitor binary decoded from base64 string in RTF file - SHA256 hash: 92c07ff5e7e08360ed324a574d6b3db9a2d6934bff6eb4cd1deee80e72f7ed33 - Description: 2018-01-24 Zeus Panda Banker - SHA256 hash: 998184a140b0998732144be054f4c8f5c1609d997155830c52feee05160db3b8 - Description: 2018-01-24 follow-up malware: Send Safe Enterprise (SSE) spambot installer
IMAGES:
Shown above: Flow chart for this Hancitor infection.
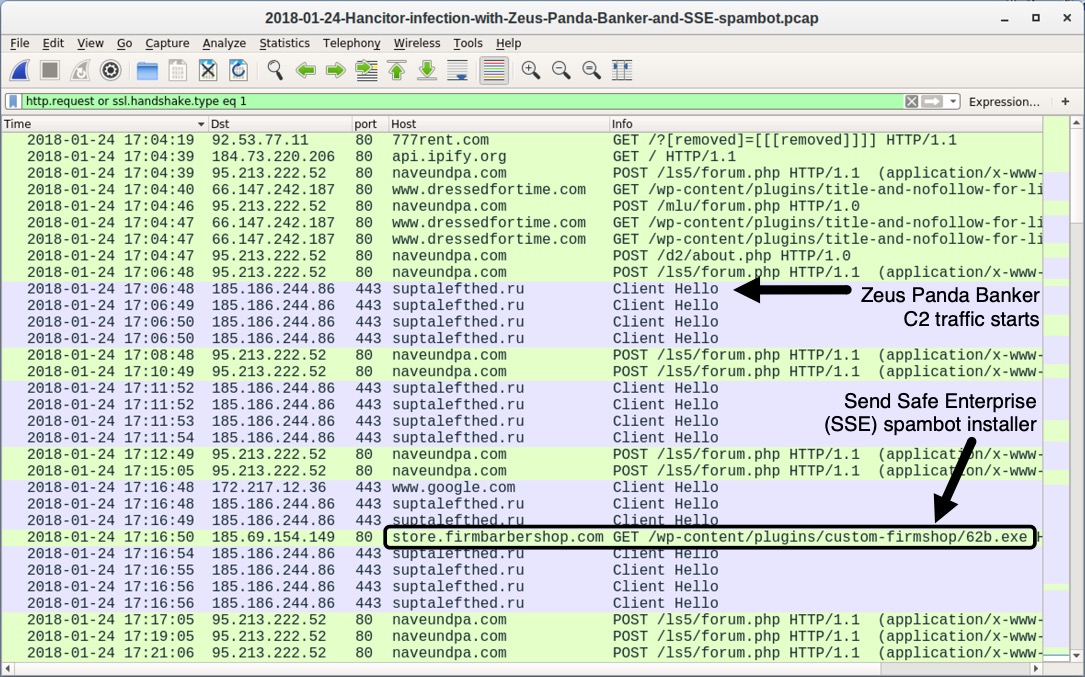
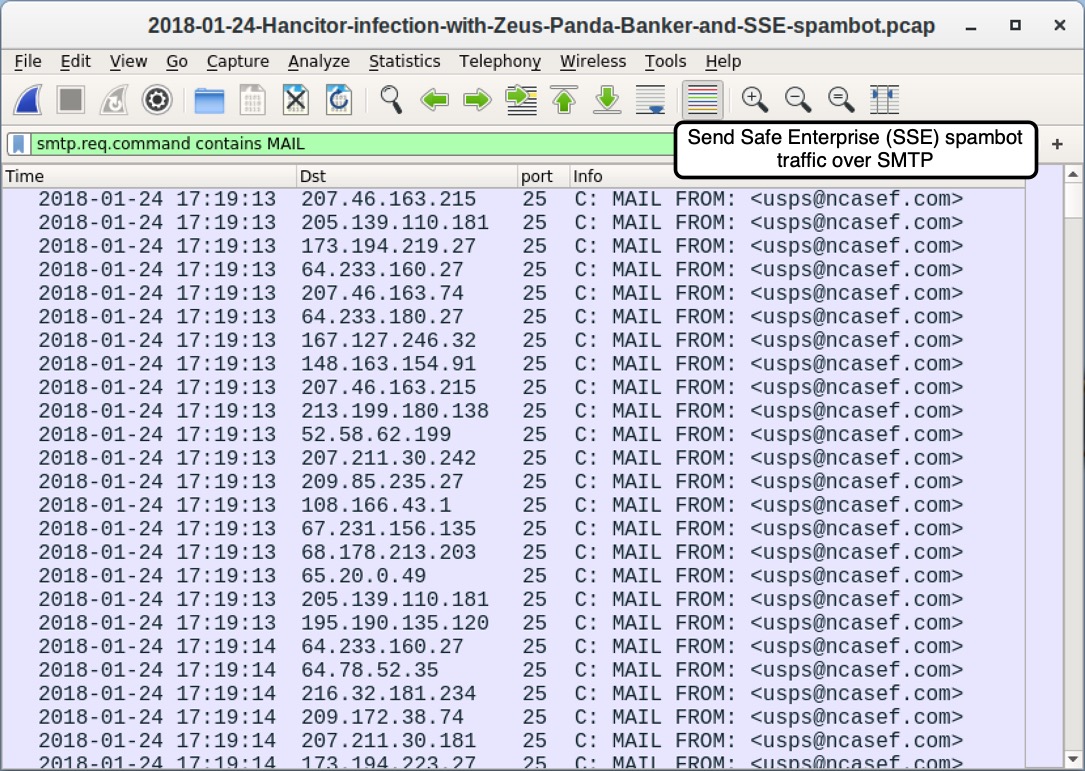
Shown above: Traffic from an infection filtered in Wireshark, highlighting Send Safe Enterprise (SSE) spambot installer.
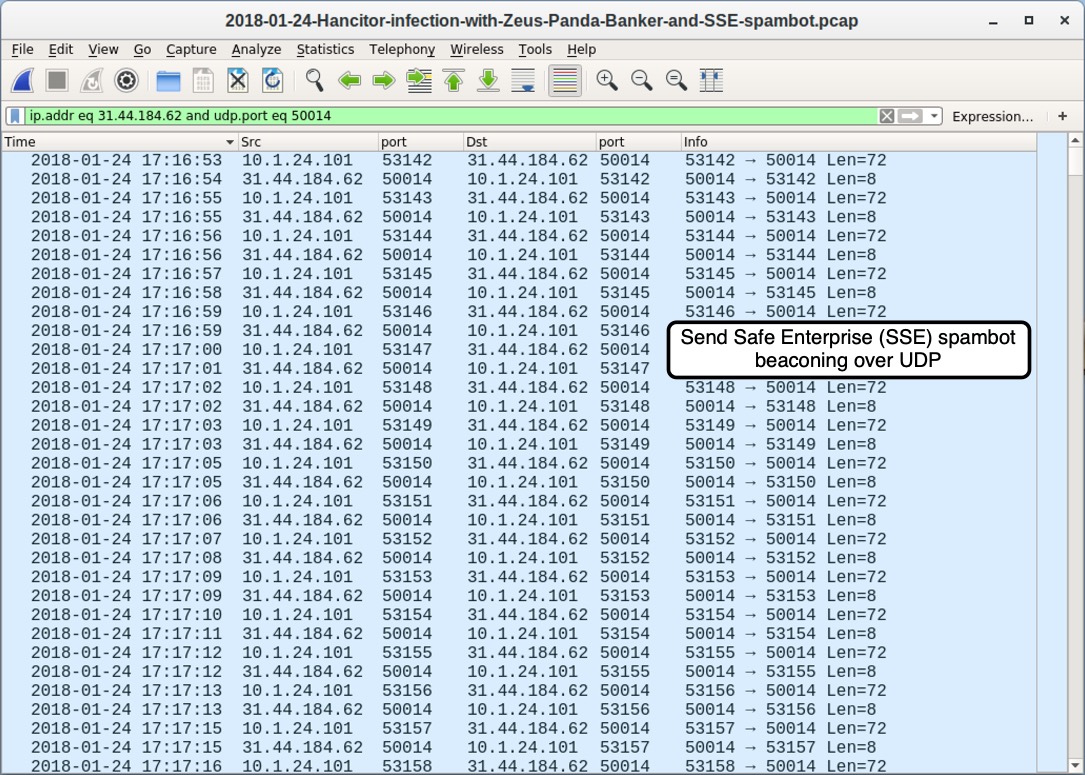
Shown above: SSE spambot-infected host beaconing to 31.44.184[.]62 over UDP port 50014.
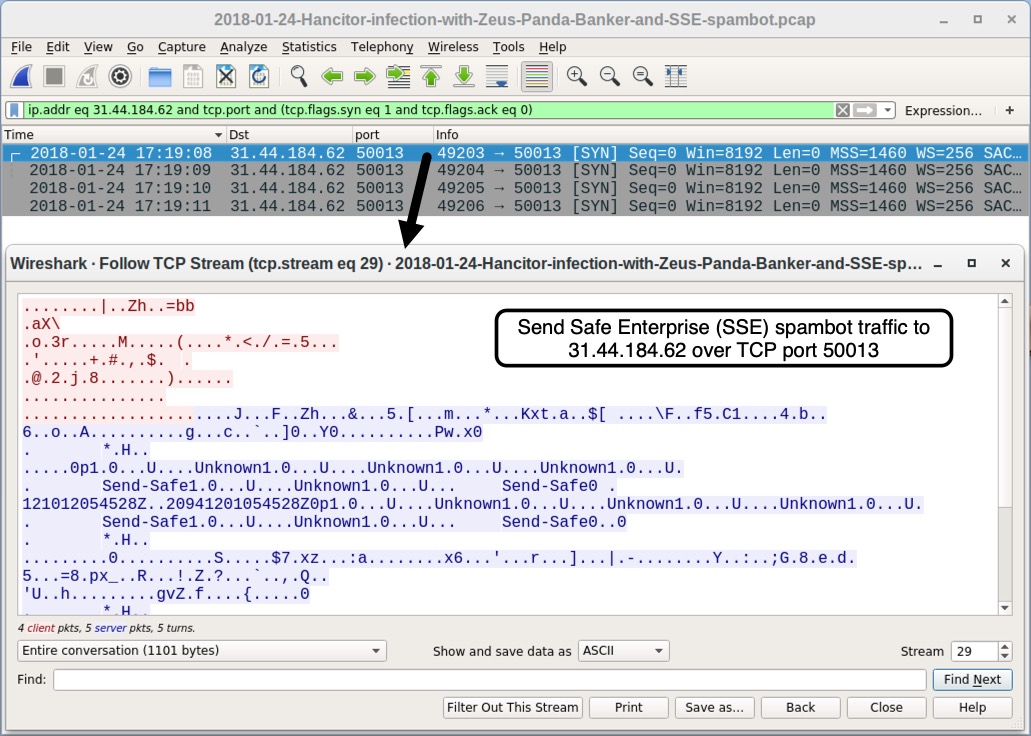
Shown above: SSE spambot-infected host TLS traffic to 31.44.184[.]62 over TCP port 50013.
Shown above: SMTP traffic showing spambot activity from my Hancitor-infected Windows host.
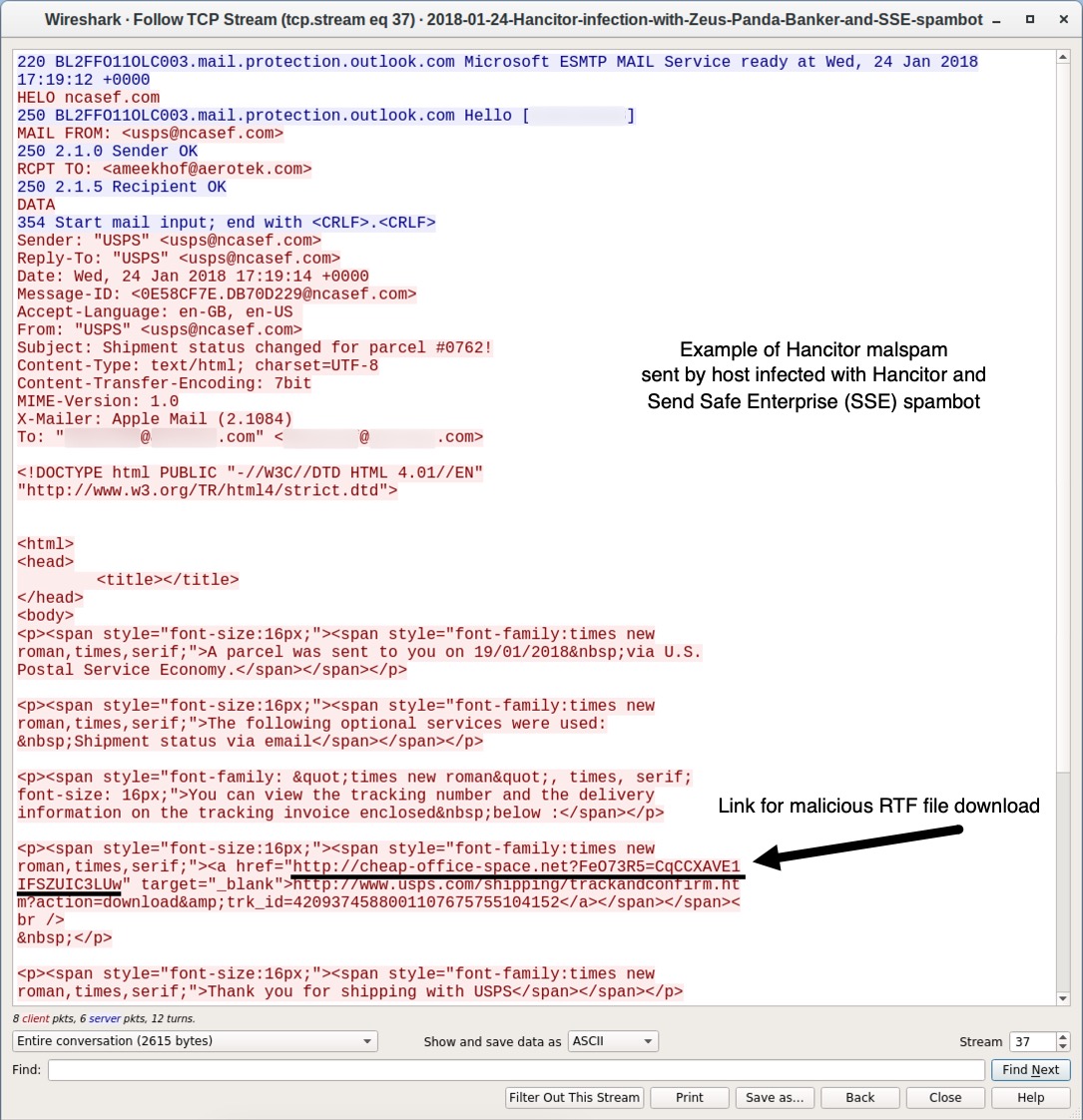
Shown above: Example of the Hancitor malspam sent from my Hancitor-infected Windows host.
Click here to return to the main page.