2018-01-29 - THREE DAYS OF SEAMLESS CAMPAIGN RIG EK PUSHING GANDCRAB RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcaps: 2018-01-29-three-pcaps-from-Seamless-Rig-EK-sending-GandCrab-ransomware.zip 851.6 kB (851,601 bytes)
- 2018-01-27-Seamless-Rig-EK-sends-GandCrab-ransomware.pcap (339,191 bytes)
- 2018-01-28-Seamless-Rig-EK-sends-GandCrab-ransomware.pcap (267,865 bytes)
- 2018-01-29-Seamless-Rig-EK-sends-GandCrab-ransomware.pcap (317,434 bytes)
- Zip archive of the malware: 2018-01-29-Seamless-campaign-Rig-EK-malware-and-artifacts.zip 508.2 kB (508,201 bytes)
- 2018-01-27-GDCB-DECRYPT.txt (2,774 bytes)
- 2018-01-27-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2018-01-27-Rig-EK-flash-exploit.swf (11,917 bytes)
- 2018-01-27-Rig-EK-landing-page.txt (97,376 bytes)
- 2018-01-27-Seamless-campaign-Rig-EK-payload-GandCrab-ransomware.exe (221,184 bytes)
- 2018-01-28-GDCB-DECRYPT.txt (2,774 bytes)
- 2018-01-28-Rig-EK-artifact-u32.tmp.txt (1,141 bytes)
- 2018-01-28-Rig-EK-flash-exploit.swf (11,909 bytes)
- 2018-01-28-Rig-EK-landing-page.txt (95,204 bytes)
- 2018-01-28-Seamless-campaign-Rig-EK-payload-GandCrab-ransomware.exe (148,992 bytes)
- 2018-01-29-Rig-EK-artifact-u32.tmp.txt (1,141 bytes)
- 2018-01-29-Rig-EK-flash-exploit.swf (11,909 bytes)
- 2018-01-29-Rig-EK-landing-page.txt (95,583 bytes)
- 2018-01-29-Seamless-campaign-Rig-EK-payload-GandCrab-ransomware.exe (235,520 bytes)
NOTES:
- Gandcrab is a ransomware that first appeared from Rig exploit kit (EK) on Friday, 2018-01-26.
- This was Rig EK used by the Seamless campaign, which has been pushing Ramnit for several months until this activity.
- 2018-01-26 - Twitter thread.
- 2018-01-27 - Unpacking GandCrab Ransomware.
WEB TRAFFIC BLOCK LIST
The following block list is based on URLs and domains from the infection traffic. See the traffic images for more details.
- hxxp[:]//xn--80abmi5aecft[.]xn--p1acf/gav4.php
- hxxp[:]//92.53.66[.]11/curl.php?token=1019
- hxxp[:]//78.155.206[.]6/curl.php?token=1019
- gdcbghvjyqy7jclk[.]onion[.]top
- gdcbghvjyqy7jclk[.]onion[.]casa
- gdcbghvjyqy7jclk[.]onion[.]guide
- gdcbghvjyqy7jclk[.]onion[.]rip
- gdcbghvjyqy7jclk[.]onion[.]plus
- gandcrab[.]bit
- nomoreransom[.]bit
TRAFFIC
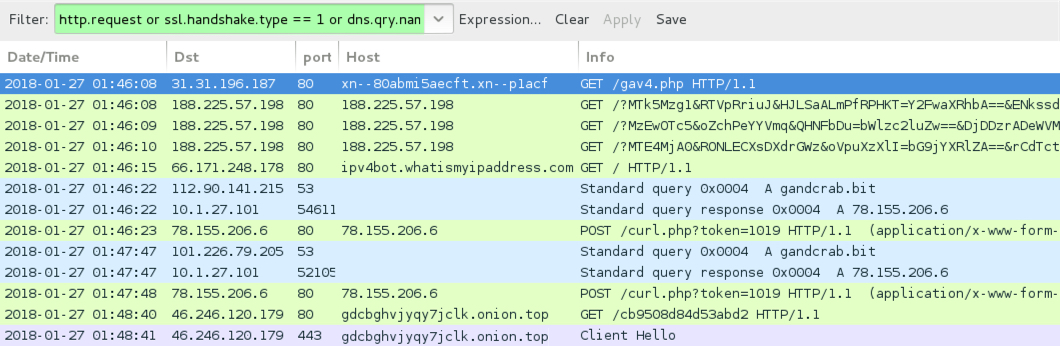
Shown above: Seamless campaign Rig EK from 2018-01-27.
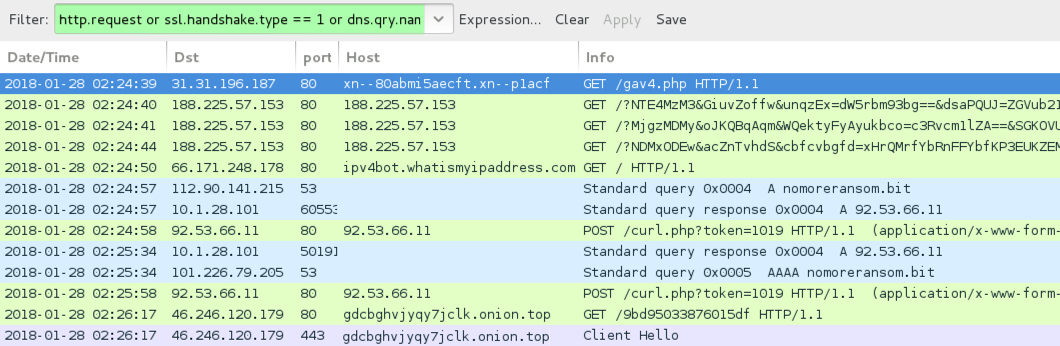
Shown above: Seamless campaign Rig EK from 2018-01-28.
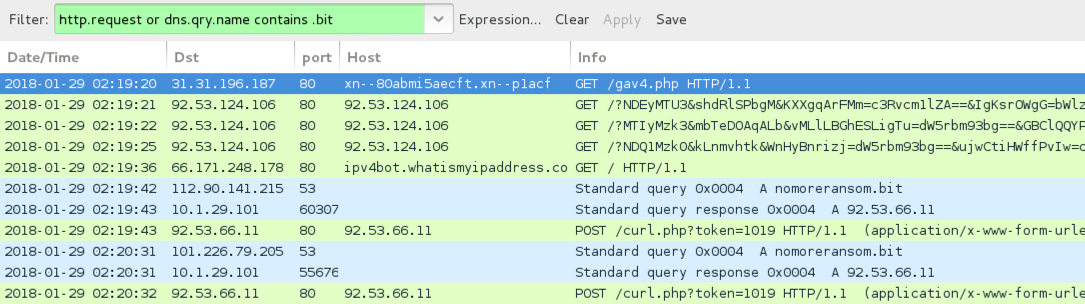
Shown above: Seamless campaign Rig EK from 2018-01-29.
MALWARE
RIG EK FLASH EXPLOITS:
- SHA256 hash: 496a5f41e206b552c93690926d6678b2f2550fe14db8dbdc42e6532353735c13
File description: Rig EK flash exploit seen on 2018-01-27
- SHA256 hash: 6a19146eb0ae8a352b166454f69bf95b4152f43b9692b4c014f9258f43be8d02
File description: Rig EK flash exploit seen on 2018-01-28 and 2018-01-29
GANDCRAB RANSOMWARE:
- SHA256 hash: 69f55139df165bea1fcada0b0174d01240bc40bc21aac4b42992f2e0a0c2ea1d
File description: Gandcrab ransomware from Seamless campaign Rig EK on 2018-01-27
- SHA256 hash: 0e47b58d99eaf5ca77f7c1b4e03e779992c7e9bf7860ec5e6cd817b4d9199b63
File description: Gandcrab ransomware from Seamless campaign Rig EK on 2018-01-28
- SHA256 hash: 3e2e881ec6fcfb6329cad95c15de4a90aef1032550176c7c7729c0a0e383c615
File description: Gandcrab ransomware from Seamless campaign Rig EK on 2018-01-29
GANDCRAB RANSOMWARE PERSISTENT ON AN INFECTED WINDOWS HOST ON 2018-01-29:
- Registry key: HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
Value name: yitjigcgcmp
Value type: REG_SZ
Value data: C:\Users\[username]\AppData\Roaming\Microsoft\yfibhp.exe
IMAGES
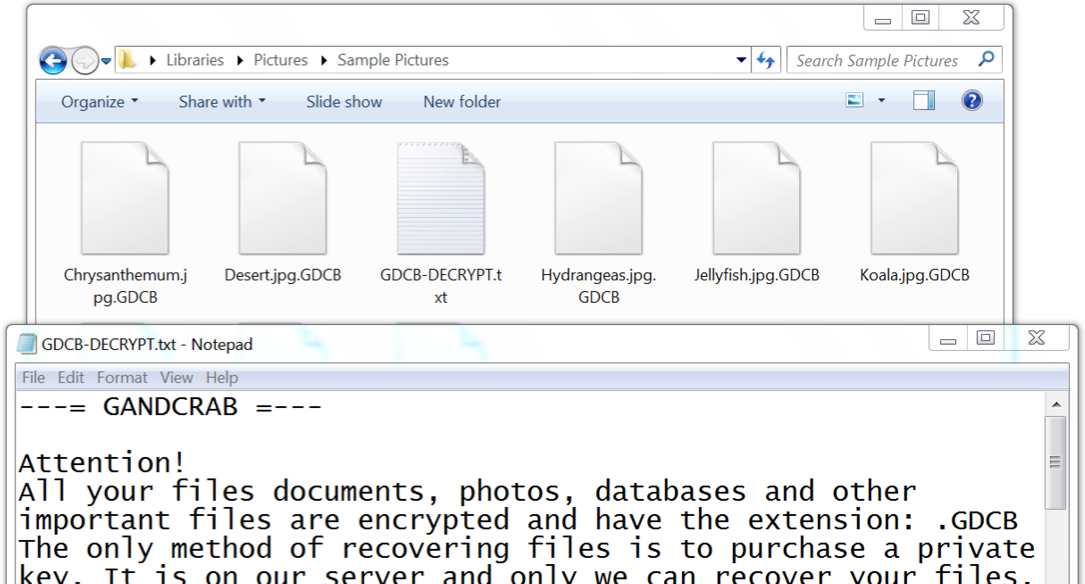
Shown above: Encrypted files on an infected Windows host.
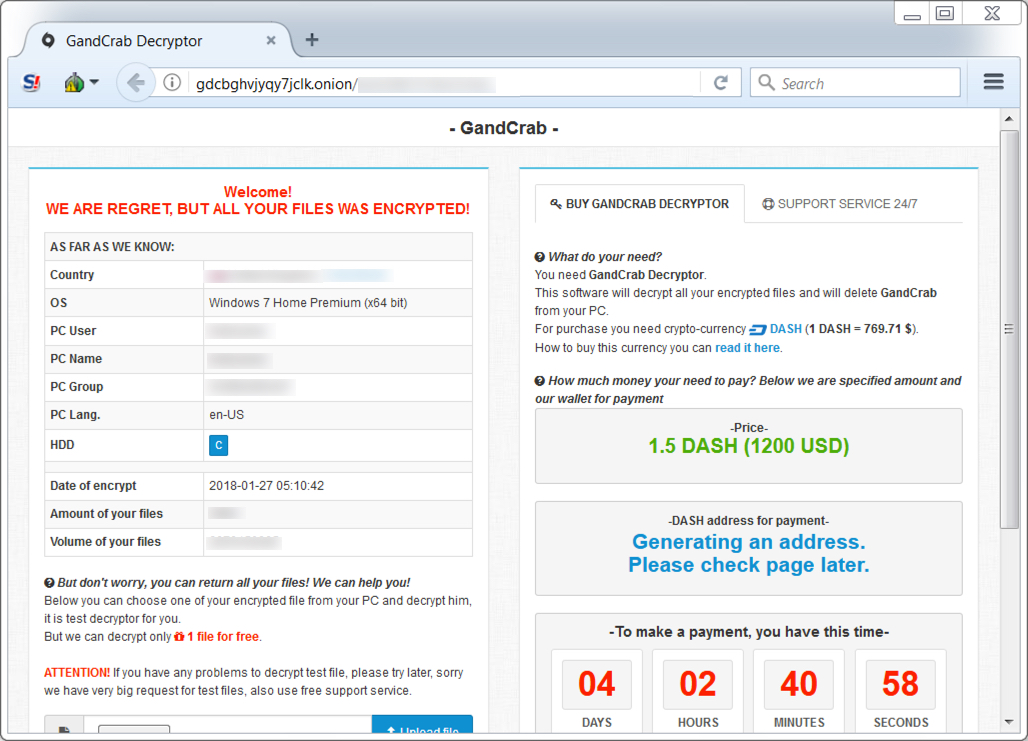
Shown above: Gandcrab decryptor.
Click here to return to the main page.
