2018-01-30 - RIG EK SENDS RAMNIT, FOLLOW-UP MALWARE: AZORULT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcaps: 2018-01-30-Rig-EK-pcaps.zip 6.0 MB (6,005,758 bytes)
- 2018-01-28-Rig-EK-traffic.pcap (2,363,533 bytes)
- 2018-01-29-Rig-EK-traffic.pcap (2,257,781 bytes)
- 2018-01-30-Rig-EK-traffic.pcap (2,588,932 bytes)
- Zip archive of the malware: 2018-01-30-Rig-EK-malware-and-artifacts.zip 1.1 MB (1,055,211 bytes)
- 2018-01-28-Rig-EK-artifact-u32.tmp.txt (1,141 bytes)
- 2018-01-28-Rig-EK-flash-exploit.swf (11,909 bytes)
- 2018-01-28-Rig-EK-landing-page.txt (95,611 bytes)
- 2018-01-28-thru-30-Rig-EK-payload.exe (428,544 bytes)
- 2018-01-28-thru-30-follow-up-malware-prink.exe (909,312 bytes)
- 2018-01-29-Rig-EK-landing-page.txt (95,553 bytes)
- 2018-01-29-and-30-Rig-EK-artifact-u32.tmp.txt (1,141 bytes)
- 2018-01-29-and-30-Rig-EK-flash-exploit.swf (13,780 bytes)
- 2018-01-30-Rig-EK-landing-page.txt (95,534 bytes)
NOTES:
WEB TRAFFIC BLOCK LIST
The following block list is based on URLs and domains from the infection traffic. See the traffic images for more details.
- pumpme[.]ga
- jr753gey6528iyehd[.]com
- mdgoixkousej[.]com
- jinrdvvggkqsbafam[.]com
- hxxp[:]//31.31.203[.]14/prink.exe
- doueven[.]click
- gtlijnbttxtstnisew[.]com
- hndhysdogmddmlbms[.]com
- jblciykrcfxyymxwgdd[.]com
- okqigyiadj[.]com
- rgaonnkejei[.]com
- scihytydbukstbtwok[.]com
- xegrplmhtvfevx[.]com
- xvlaykoevuesourj[.]com
- yxvcjnrx[.]com
TRAFFIC
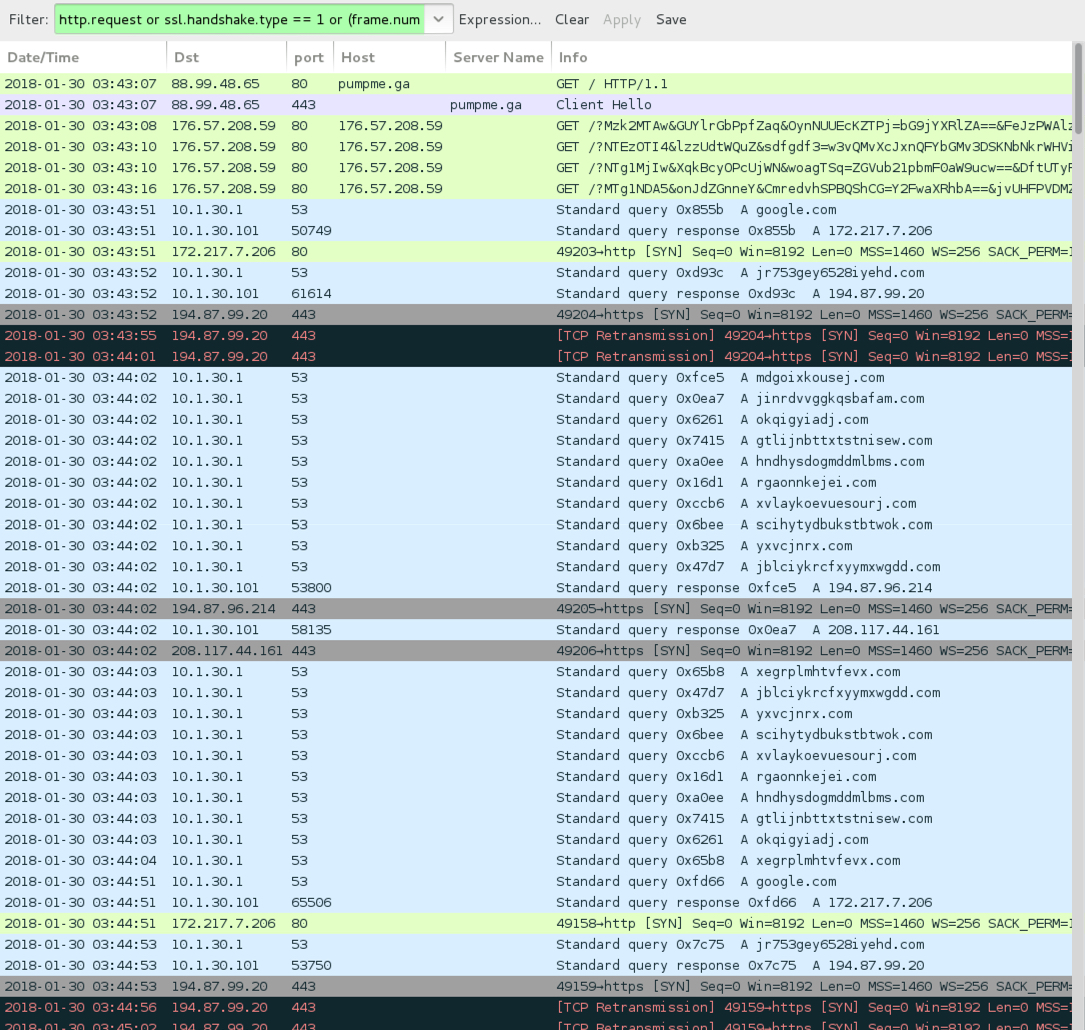
Shown above: Rig EK infection traffic from 2018-01-30 (part 1 of 2).
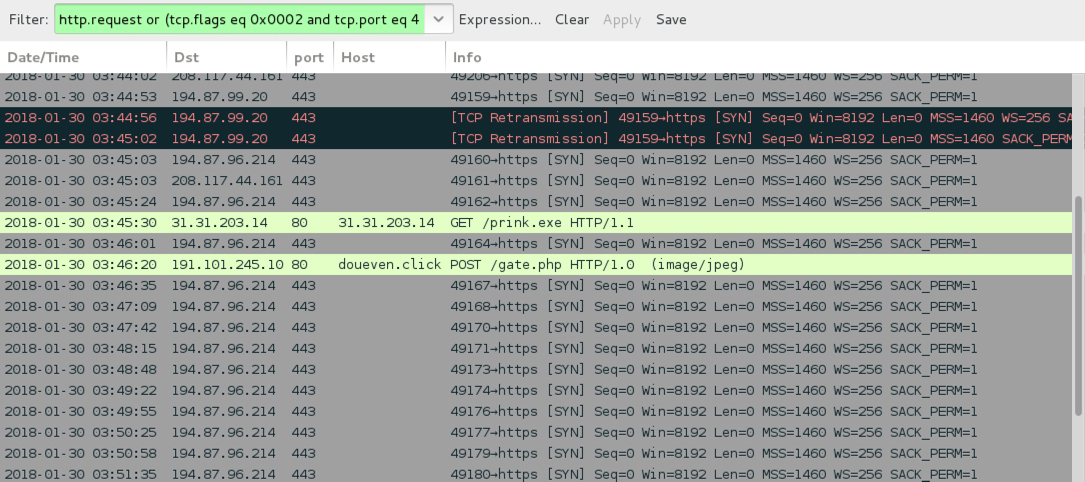
Shown above: Rig EK infection traffic from 2018-01-30 (part 2 of 2).
ASSOCIATED DOMAINS AND URLS:
- 88.99.48[.]65 port 80 - pumpme[.]ga - GET / (gate used by this campaign)
- 88.99.48[.]65 port 443 - pumpme[.]ga - HTTPS traffic
- 176.57.208[.]59 port 80 - 176.57.208[.]59 - Rig EK
- 194.87.99[.]20 port 443 - jr753gey6528iyehd[.]com - attempted TCP connections caused by Ramnit, but no response from the server
- 194.87.96[.]214 port 443 - mdgoixkousej[.]com - encrypted traffic caused by Ramnit
- 208.117.44[.]161 port 443 - jinrdvvggkqsbafam[.]com - encrypted traffic caused by Ramnit
- 31.31.203[.]14 port 80 - 31.31.203[.]14 - GET /prink.exe (AZORult follow-up malware)
- 191.101.245[.]101 port 80 - doueven[.]click - POST /gate.php (AZORult callback)
- DNS query for gtlijnbttxtstnisew[.]com - response: No such name (SOA a.gtld-servers.net)
- DNS query for hndhysdogmddmlbms[.]com - response: No such name (SOA a.gtld-servers.net)
- DNS query for jblciykrcfxyymxwgdd[.]com - response: No such name (SOA a.gtld-servers.net)
- DNS query for okqigyiadj[.]com - response: No such name (SOA a.gtld-servers.net)
- DNS query for rgaonnkejei[.]com - response: No such name (SOA a.gtld-servers.net)
- DNS query for scihytydbukstbtwok[.]com - response: No such name (SOA a.gtld-servers.net)
- DNS query for xegrplmhtvfevx[.]com - response: No such name (SOA a.gtld-servers.net)
- DNS query for xvlaykoevuesourj[.]com - response: No such name (SOA a.gtld-servers.net)
- DNS query for yxvcjnrx[.]com - response: No such name (SOA a.gtld-servers.net)
MALWARE
RIG EK FLASH EXPLOITS:
- 6a19146eb0ae8a352b166454f69bf95b4152f43b9692b4c014f9258f43be8d02 - 2018-01-28 Rig EK flash exploit
- 92c5c223db18b03e1630070d606fc3a2143fd8d637dddb6617615277b892204e - 2018-01-29 and 30 Rig EK flash exploit
MALWARE BINARIES:
- 726b21fde2206f9c8cf6e4ee75ccea70684ad2548f98aab8a42f53c7575a582f - 2018-01-28 thru 30 Rig EK payload (Ramnit)
- b0c91214a3ed6af1fb66938c96881af0b0633ce6f439ac9b9c6469c9dd770074 - 2018-01-28 thru 30 follow-up malware (AZORult)
IMAGES
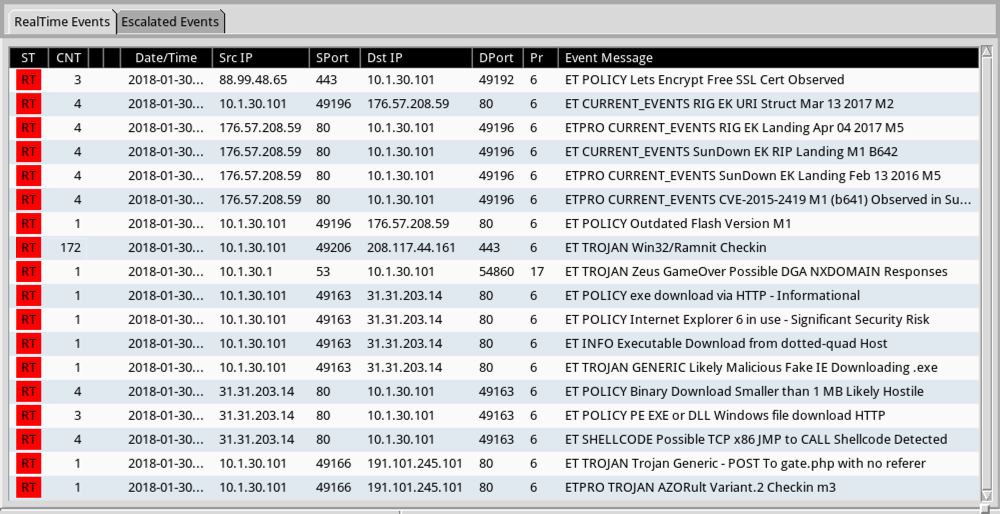
Shown above: Alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
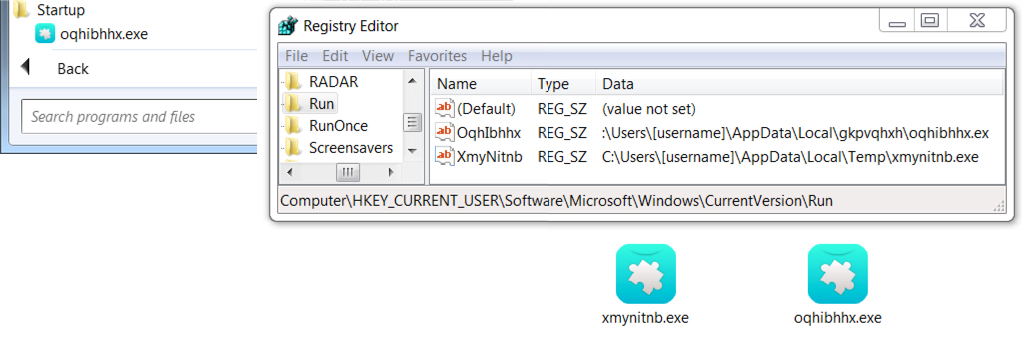
Shown above: Malware (Ramnit) persistent on the infected Windows host.
Click here to return to the main page.
