2018-02-06 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2018-02-06-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 2.2 MB (2,153,232 bytes)
- Zip archive of 8 email samples: 2018-02-06-Hancitor-malspam-8-examples.txt.zip 2.0 kB (1,966 bytes)
- Zip archive of the malware: 2018-02-06-malware-from-Hancitor-infection.zip 230.4 kB (230,464 bytes)
TWEETS ON TODAY'S HANCITOR RUN:
- @killamjr - link to Tweet
- @Techhelplistcom - link to tweet - link to Paste.ee data
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- comharcapital[.]com
- homeimprovementpodcast[.]com
- mchughconst[.]com
- oasispropertyworks[.]com
- rangeviewestates[.]com
- hxxp[:]//africanpeace[.]org/wp-content/plugins/visual-form-builder/includes/1
- hxxp[:]//africanpeace[.]org/wp-content/plugins/visual-form-builder/includes/2
- hxxp[:]//africanpeace[.]org/wp-content/plugins/visual-form-builder/includes/3
- ofttacotoft[.]com
- bulighhesin[.]ru
EMAILS
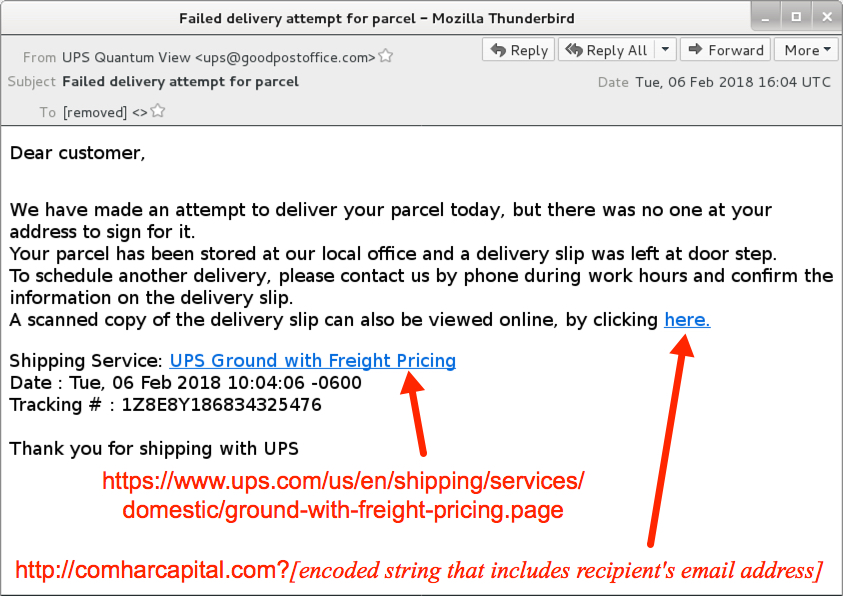
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Tuesday 2018-02-06 as early as 15:37 through at least 17:44 UTC
- From (spoofed): "UPS Quantum View" <ups@goodpostoffice[.]com>
- Subject: Failed delivery attempt for package
- Subject: Failed delivery attempt for parcel
- Subject: Failed delivery attempt for shipment
- Subject: Failed delivery attempt for shipping
- Subject: Failed delivery attempt for tracking
- Received: from goodpostoffice[.]com ([47.36.141[.]33])
- Received: from goodpostoffice[.]com ([97.64.164[.]194])
- Received: from goodpostoffice[.]com ([104.193.29[.]46])
- Received: from goodpostoffice[.]com ([108.58.46[.]222])
- Received: from goodpostoffice[.]com ([142.162.234[.]63])
- Received: from goodpostoffice[.]com ([206.217.6[.]169])
- Received: from goodpostoffice[.]com ([216.100.89[.]39])
- Received: from goodpostoffice[.]com ([216.227.31[.]99])
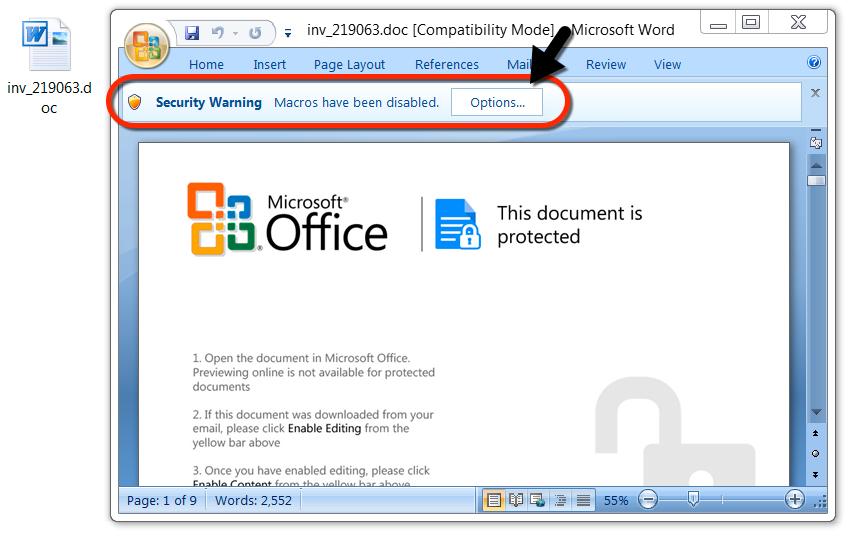
Shown above: Malicious Word document downloaded from a link in the malspam.
TRAFFIC
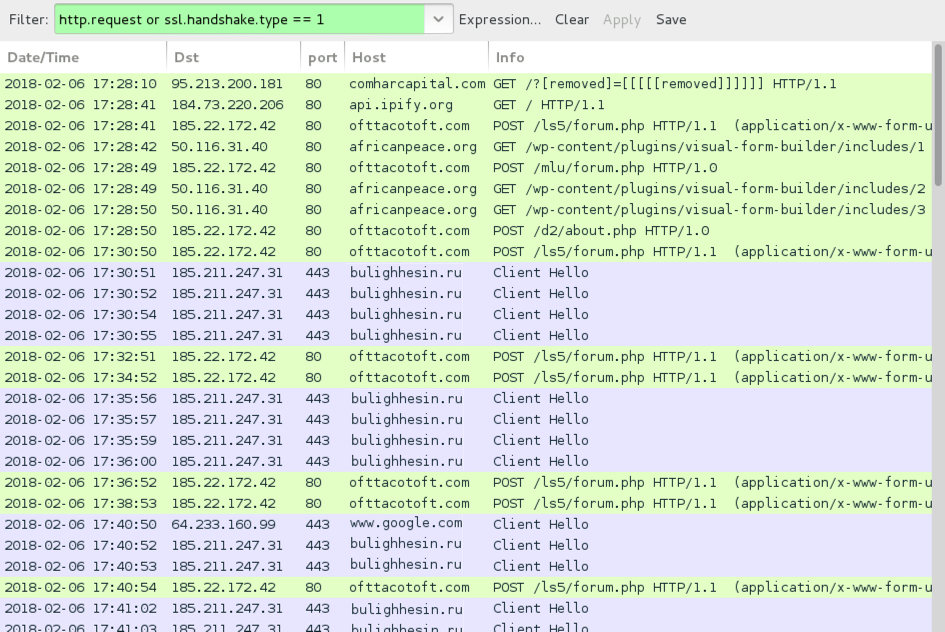
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- hxxp[:]//comharcapital[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//homeimprovementpodcast[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//mchughconst[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//oasispropertyworks[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//rangeviewestates[.]com?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM MY INFECTED LAB HOST:
- 95.213.200[.]181 port 80 - comharcapital[.]com - GET /?[string of characters]=[encoded string that includes info on recipient's email address]
- api.ipify[.]org - GET /
- 185.22.172[.]42 port 80 - ofttacotoft[.]com - POST /ls5/forum.php
- 185.22.172[.]42 port 80 - ofttacotoft[.]com - POST /mlu/forum.php
- 185.22.172[.]42 port 80 - ofttacotoft[.]com - POST /d2/about.php
- 50.116.31[.]40 port 80 - africanpeace[.]org - GET /wp-content/plugins/visual-form-builder/includes/1
- 50.116.31[.]40 port 80 - africanpeace[.]org - GET /wp-content/plugins/visual-form-builder/includes/2
- 50.116.31[.]40 port 80 - africanpeace[.]org - GET /wp-content/plugins/visual-form-builder/includes/3
- 185.211.247[.]31 port 443 - bulighhesin[.]ru - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- www.google[.]com - HTTPS traffic, probably a connectivity check by infected Windows host
FILE HASHES
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 155ef288ba55de9c35c33a8d2e2a662c5e9024dee68fcd64d42a766d729784ee
File size: 220,672 bytes
File name: inv_[6 random digits].doc
File description: Word document with macro for Hancitor
- SHA256 hash: 18738524538960e451bcd527c943511ac6c15e329fb954b02e3a2255e303e344
File size: 157,184 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
IMAGES
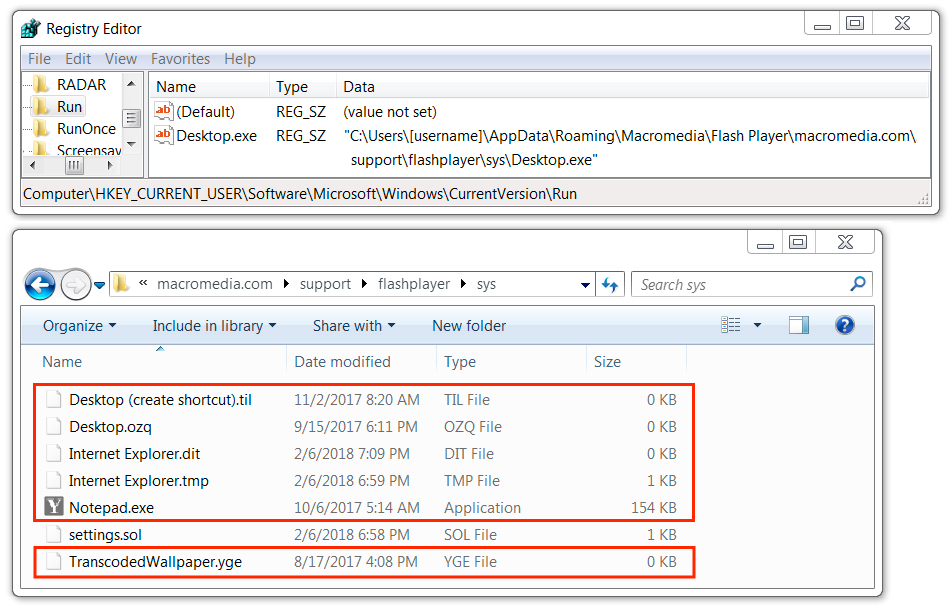
Shown above: Zeus Panda Banker persistent on the infected Windows host.
Click here to return to the main page.
