2018-02-13 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
ASSOCIATED FILES:
- 2018-02-13-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 565.3 kB (565,324 bytes)
- 2018-02-13-Hancitor-infection-with-Zeus-Panda-Banker.pcap (803,943 bytes)
- 2018-02-13-Hancitor-malspam-8-examples.txt.zip 1.6 kB (1,624 bytes)
- 2018-02-13-Hancitor-malspam-8-examples.txt (11,119 bytes)
- 2018-02-13-malware-from-Hancitor-infection.zip 280.4 kB (280,396 bytes)
- 2018-02-13-Hancitor-maldoc-invoice_325399.doc (311,296 bytes)
- 2018-02-13-Zeus-Panda-Banker.exe (126,976 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- area-connection[.]net
- contactworks[.]biz
- mynexgreen[.]com
- nexgreen[.]net
- nexgreenlawn[.]com
- roc-inc[.]net
- sultenworks[.]com
- trentoncable[.]net
- hxxp://mail.bestnewantiwrinklecream[.]com/wp-content/plugins/jetpack/modules/1
- hxxp://mail.bestnewantiwrinklecream[.]com/wp-content/plugins/jetpack/modules/2
- hxxp://mail.bestnewantiwrinklecream[.]com/wp-content/plugins/jetpack/modules/3
- hxxp://mail.seadustfilms[.]com/wp-content/plugins/maxbuttons/includes/1
- hxxp://mail.seadustfilms[.]com/wp-content/plugins/maxbuttons/includes/2
- hxxp://mail.seadustfilms[.]com/wp-content/plugins/maxbuttons/includes/3
- hxxp://www.digitaldream[.]rs/wp-content/plugins/gallery-plugin/1
- hxxp://www.digitaldream[.]rs/wp-content/plugins/gallery-plugin/2
- hxxp://www.digitaldream[.]rs/wp-content/plugins/gallery-plugin/3
- thattahitin[.]com
- parwithutfi[.]ru
- houndlinggot[.]ru
- bulighhesin[.]ru
EMAILS
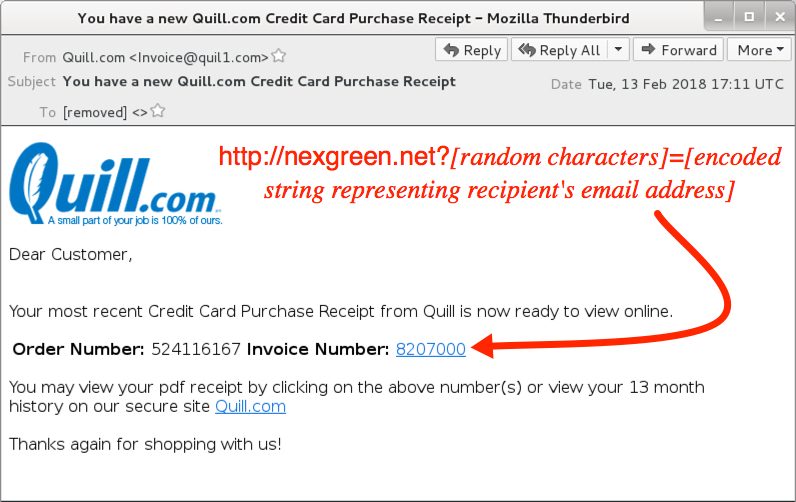
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Tuesday 2018-02-13 as early as 16:19 through at least 18:55 UTC
- Subject: You have a new Quill[.]com Credit Card Purchase Receipt
- From (spoofed): "Quill[.]com" <Invoice@quil1[.]com>
- Received: from quil1[.]com ([50.252.95[.]129])
- Received: from quil1[.]com ([70.55.226[.]153])
- Received: from quil1[.]com ([75.110.186[.]234])
- Received: from quil1[.]com ([96.61.127[.]2])
- Received: from quil1[.]com ([96.68.44[.]105])
- Received: from quil1[.]com ([206.40.111[.]53])
- Received: from quil1[.]com ([207.201.210[.]82])
- Received: from quil1[.]com ([216.218.189[.]211])
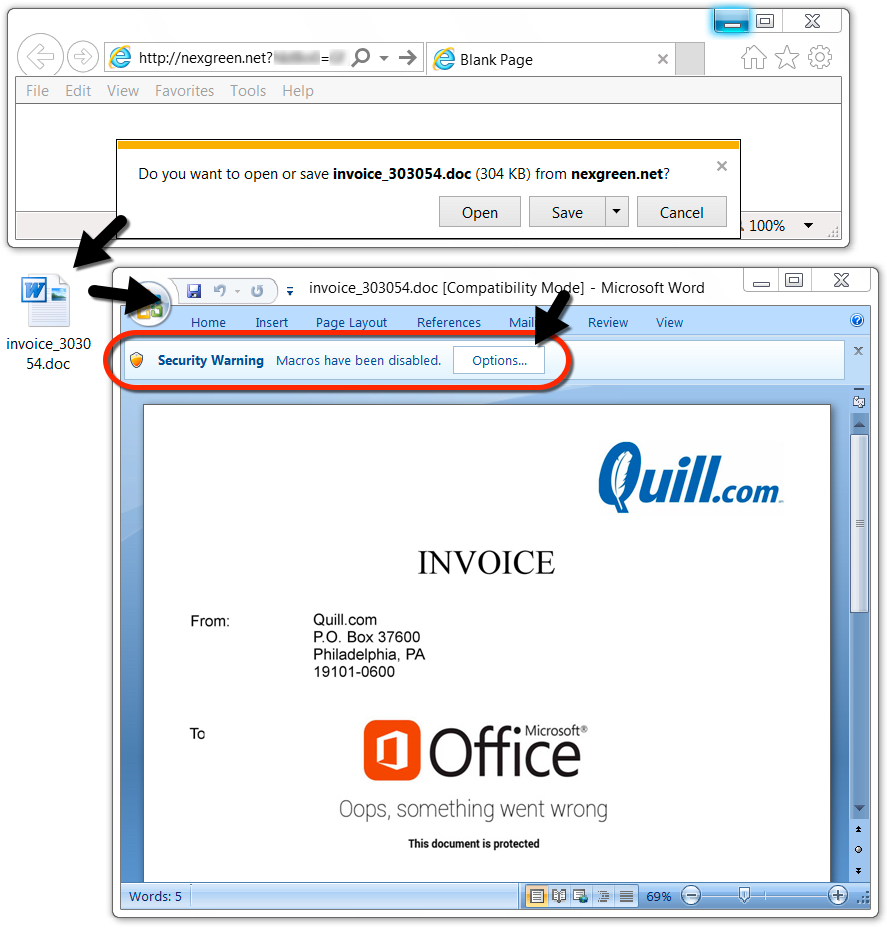
Shown above: Malicious Word document downloaded from a link in the malspam.
TRAFFIC
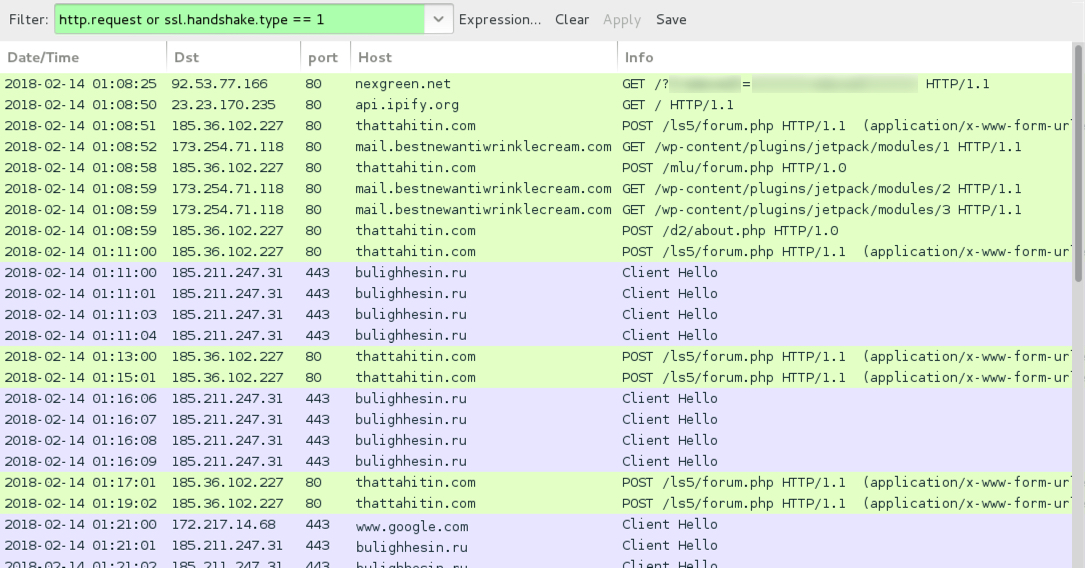
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- hxxp://contactworks[.]biz?[string of characters]=[encoded string representing recipient's email address]
- hxxp://MYNEXGREEN[.]COM?[string of characters]=[encoded string representing recipient's email address]
- hxxp://nexgreen[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp://sultenworks[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp://trentoncable[.]net?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM MY INFECTED LAB HOST:
- 92.53.77[.]166 port 80 - nexgreen[.]net - GET /?[string of characters]=[encoded string that includes info on recipient's email address]
- api.ipify[.]org - GET /
- 185.36.102[.]227 port 80 - thattahitin[.]com - POST /ls5/forum.php
- 185.36.102[.]227 port 80 - thattahitin[.]com - POST /mlu/forum.php
- 185.36.102[.]227 port 80 - thattahitin[.]com - POST /d2/about.php
- 173.254.71[.]118 port 80 - mail.bestnewantiwrinklecream[.]com - GET /wp-content/plugins/jetpack/modules/1
- 173.254.71[.]118 port 80 - mail.bestnewantiwrinklecream[.]com - GET /wp-content/plugins/jetpack/modules/2
- 173.254.71[.]118 port 80 - mail.bestnewantiwrinklecream[.]com - GET /wp-content/plugins/jetpack/modules/3
- 185.211.247[.]31 port 443 - bulighhesin[.]ru - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- www.google[.]com - HTTPS traffic, probably a connectivity check by infected Windows host
FILE HASHES
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 2101f58099128c1192da4373458e425e816fe3761bc2834423dfdb3944a939fe
File size: 311,296 bytes
File name: invoice_325399.doc [any six random digits for the numbers]
File description: Word document with macro for Hancitor
- SHA256 hash: 814e74e42d760b3f2ed66346156114122e7d2f9c209f9c51a97eb367e8d23d2b
File size: 126,976 bytes
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
IMAGES
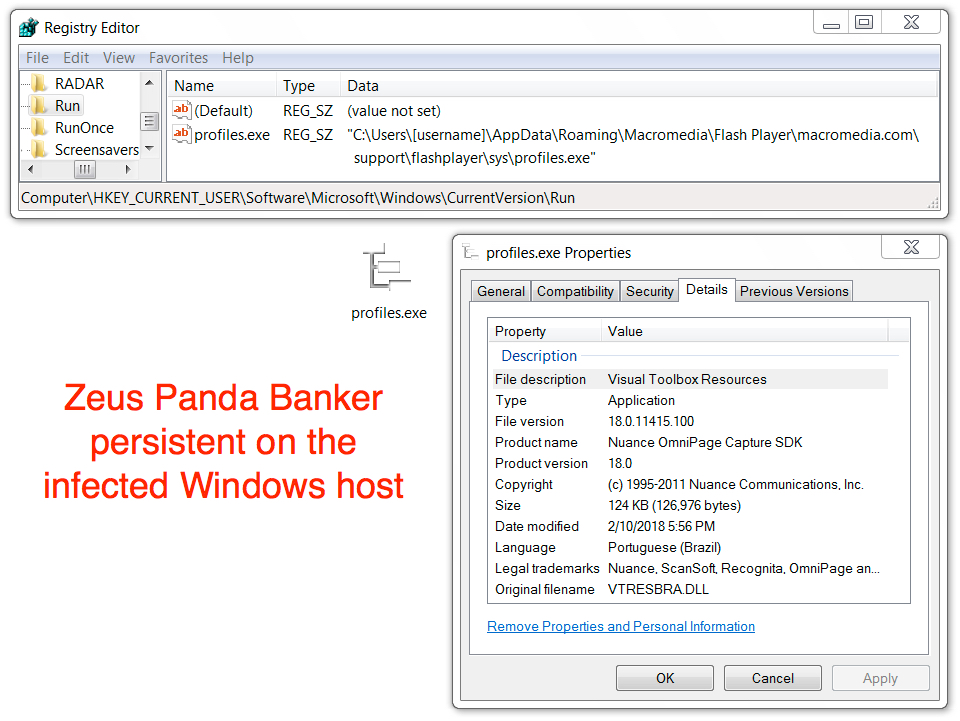
Shown above: Zeus Panda Banker persistent on the infected Windows host.
Click here to return to the main page.
