2018-02-16 - FORMBOOK INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2018-02-16-Formbook-infection-traffic.pcap.zip 919.3 kB (919,310 bytes)
- 2018-02-16-Formbook-infection-traffic.pcap (1,285,123 bytes)
- Zip archive of the email and malware: 2018-02-16-Formbook-email-and-malware.zip 844.7 kB (844,653 bytes)
- 2018-02-16-extracted-Formbook-malware.exe (495,616 bytes)
- 2018-02-16-malspam-attachment.zip (277,181 bytes)
- 2018-02-16-malspam-pushing-Formbook-1228-UTC.eml (384,353 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list, especially since the associated domains appear to be legitimate websites. If you feel the need to block web traffic, I suggest the following partial URLs:
- hxxp[:]//www.885mt[.]com/m02/
- hxxp[:]//www.blitzathletics[.]fitness/m02/
- hxxp[:]//www.clevelandtaxaccountant[.]com/m02/
- hxxp[:]//www.deliciousvillefoods[.]com/m02/
- hxxp[:]//www.discovertellus[.]com/m02/
- hxxp[:]//www.erfenbu[.]com/m02/
- hxxp[:]//www.hemalipaterl[.]com/m02/
- hxxp[:]//www.jueduizan[.]com/m02/
- hxxp[:]//www.karselasansor[.]com/m02/
- hxxp[:]//www.kinketsukun[.]com/m02/
- hxxp[:]//www.navstyle[.]com/m02/
- hxxp[:]//www.siwi[.]solutions/m02/
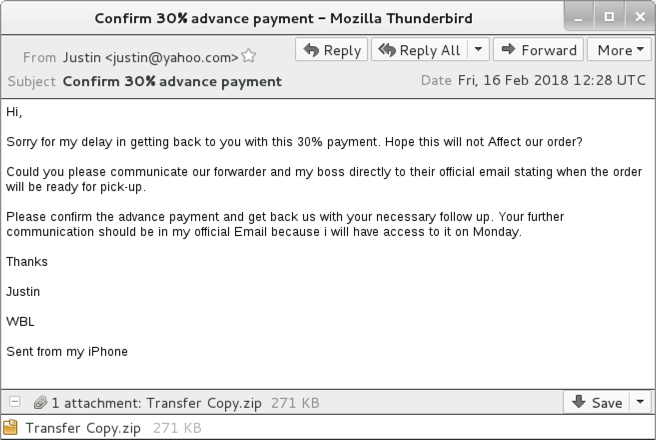
Shown above: Screenshot of the email.
EMAIL INFORMATION:
- Date: Friday, 2018-02-16 at 12:28 UTC
- Subject: Confirm 30% advance payment
- From: "Justin" <justin@yahoo[.]com>
- Received: from 139.162.5.147 ([139.162.5[.]147])
- Message-ID: <E1emf7M-0000Xa-Sm@kccgroups.dnsracks[.]com>
- Attachment name: Transfer Copy.zip
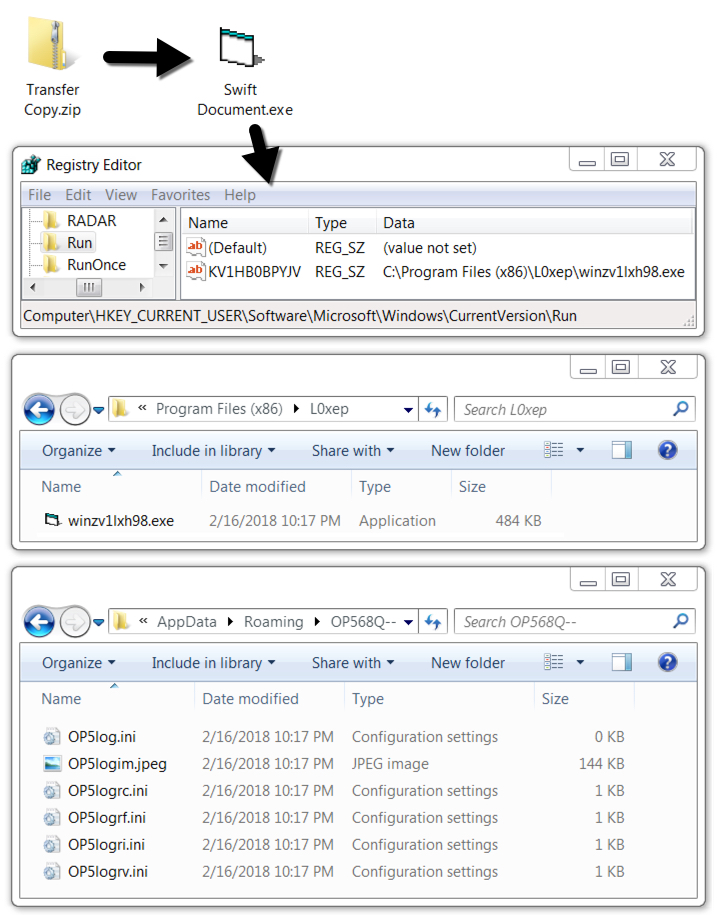
Shown above: Extracting the malware from the zip attachment and running it.
TRAFFIC
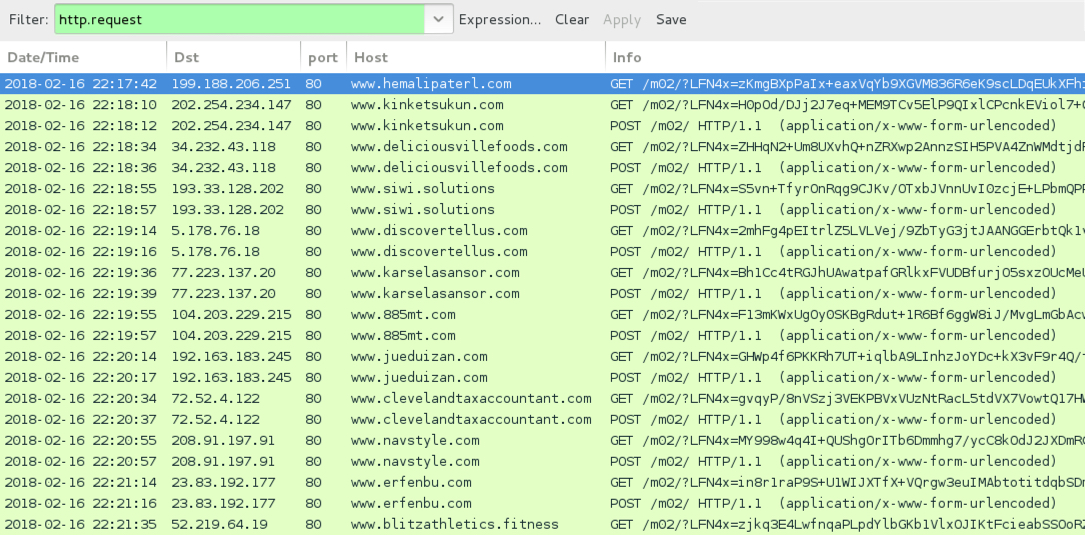
Shown above: Traffic from the infection filtered in Wireshark.
INFECTION TRAFFIC:
- 199.188.206[.]251 port 80 - www.hemalipaterl[.]com - GET /m02/?LFN4x=[long string]==&wN688b=HZl0
- 202.254.234[.]147 port 80 - www.kinketsukun[.]com - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
- 202.254.234[.]147 port 80 - www.kinketsukun[.]com - POST /m02/
- 34.232.43[.]118 port 80 - www.deliciousvillefoods[.]com - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
- 34.232.43[.]118 port 80 - www.deliciousvillefoods[.]com - POST /m02/
- 193.33.128[.]202 port 80 - www.siwi[.]solutions - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
- 193.33.128[.]202 port 80 - www.siwi[.]solutions - POST /m02/
- 5.178.76[.]18 port 80 - www.discovertellus[.]com - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
- 5.178.76[.]18 port 80 - www.discovertellus[.]com - POST /m02/
- 77.223.137[.]20 port 80 - www.karselasansor[.]com - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
- 77.223.137[.]20 port 80 - www.karselasansor[.]com - POST /m02/
- 104.203.229[.]215 port 80 - www.885mt[.]com - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
- 104.203.229[.]215 port 80 - www.885mt[.]com - POST /m02/
- 192.163.183[.]245 port 80 - www.jueduizan[.]com - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
- 192.163.183[.]245 port 80 - www.jueduizan[.]com - POST /m02/
- 72.52.4[.]122 port 80 - www.clevelandtaxaccountant[.]com - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
- 72.52.4[.]122 port 80 - www.clevelandtaxaccountant[.]com - POST /m02/
- 208.91.197[.]91 port 80 - www.navstyle[.]com - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
- 208.91.197[.]91 port 80 - www.navstyle[.]com - POST /m02/
- 23.83.192[.]177 port 80 - www.erfenbu[.]com - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
- 23.83.192[.]177 port 80 - www.erfenbu[.]com - POST /m02/
- 52.219.64[.]19 port 80 - www.blitzathletics[.]fitness - GET /m02/?LFN4x=[long string]==&wN688b=HZl0&sql=1
MALWARE
EMAIL ATTACHMENT (ZIP ARCHIVE):
- SHA256 hash: f5e2ec975eb815e3963ec266e8090ef8abbd89af3dde5b036f5fa2840484a436
File size: 277,181 bytes
File name: Transfer Copy.zip
EXTRACTED FORMBOOK MALWARE:
- SHA256 hash: 22d9e1cf5d47b9cccd1b1449037ec1017f1747805cd09300bbd0fdc7167b28a8
File size: 495,616 bytes
File name: Swift Document.exe
File location after infection: C:\Program Files (x86)\L0xep\winzv1lxh98.exe
Click here to return to the main page.
