2018-02-20 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-02-20-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 1.9 MB (1,895,268 bytes)
- 2018-02-20-Hancitor-infection-with-Zeus-Panda-Banker.pcap (2,173,787 bytes)
- Zip archive of the emails: 2018-02-20-Hancitor-malspam-30-examples.txt.zip 2.8 kB (2,763 bytes)
- 2018-02-20-Hancitor-malspam-30-examples.txt (30,105 bytes)
- Zip archive of the malware: 2018-02-20-malware-from-Hancitor-infection.zip 433.1 kB (433,127 bytes)
- 2018-02-20-Hancitor-binary.exe (61,440 bytes)
- 2018-02-20-Hancitor-downloader-invoice_311706.js (35,396 bytes)
- 2018-02-20-Hancitor-maldoc-invoice_143264.doc (346,624 bytes)
- 2018-02-20-Zeus-Panda-Banker.exe (169,984 bytes)
NOTES:
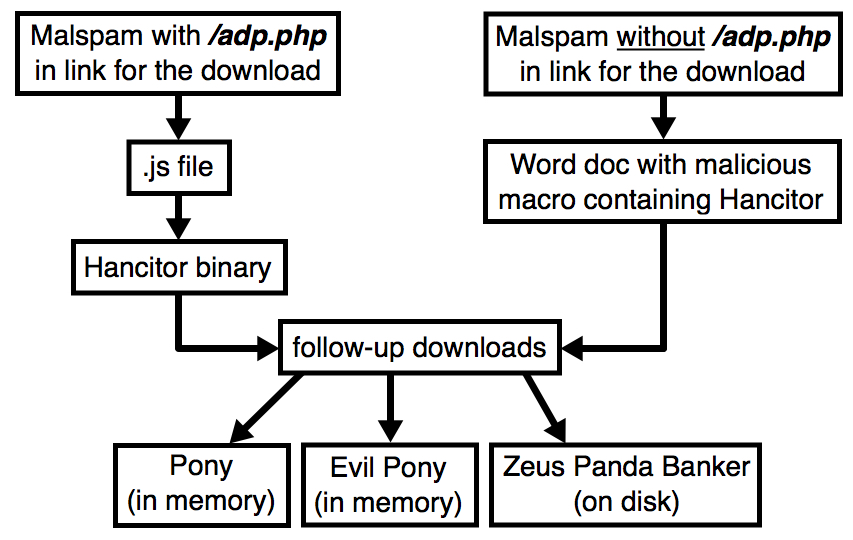
- Links from the malspam with /adp.php in the URL returned JavaScript (.js) files.
- Links from the malspam without /adp.php in the URL returned a Word document.
- The .js files downloaded Hancitor as a binary.
- The Word documents had a malicious macro that contained the Hancitor malware.
- As usual, we saw 3 follow-up downloads for Pony, Evil Pony, and Zeus Panda Banker.
- As usual, Pony and Evil Pony were resident in the infected host's memory, while Zeus Panda Banker was stored to disk.
Shown above: Flowchart for today's Hancitor infection traffic.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- beasecurityguard[.]com
- brelicensewithus[.]com
- foodhandlerlicense[.]com
- getabrelicense[.]com
- getyourbrelicense[.]com
- premierrealestateschools[.]info
- premierrealestateschools[.]org
- realestatelicense[.]la
- realestateschools[.]training
- realestatesschools[.]academy
- securityguardschooling[.]com
- rymoonthen[.]com
- hxxp[:]//uttamah[.]com/wp-content/plugins/pretty-link/includes/1
- hxxp[:]//uttamah[.]com/wp-content/plugins/pretty-link/includes/2
- hxxp[:]//uttamah[.]com/wp-content/plugins/pretty-link/includes/3
- lyhemsasit[.]ru
EMAILS
Shown above: Screenshot from one of the emails with link to a .js file.
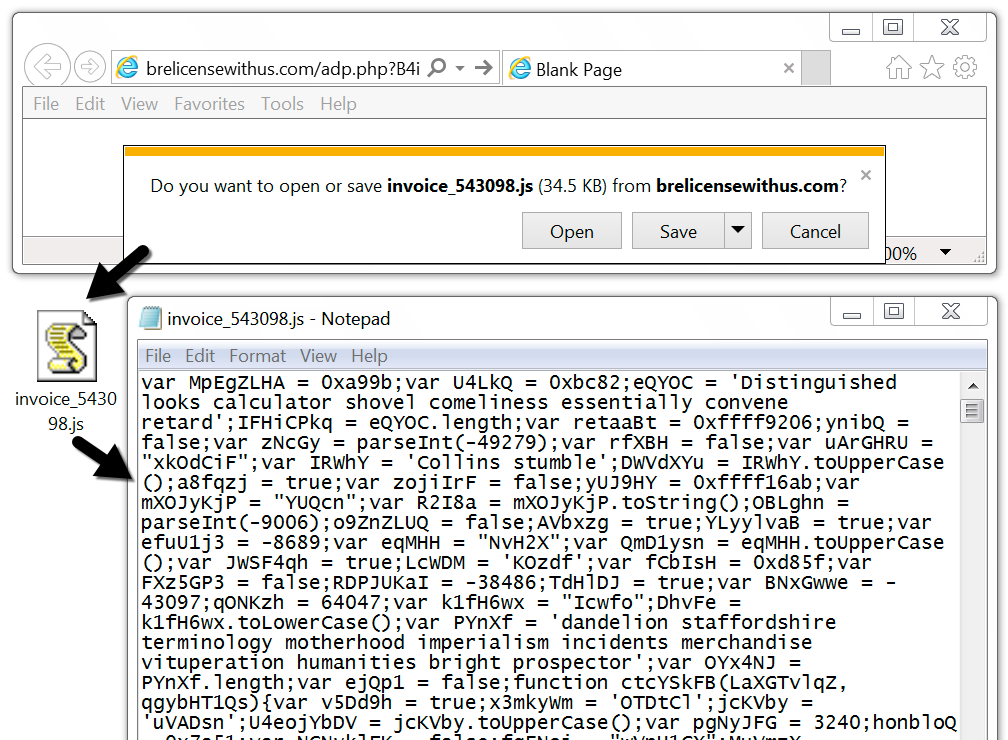
Shown above: Downloading a .js file from one of the emails.
Shown above: Screenshot from one of the emails with link to a Word document.
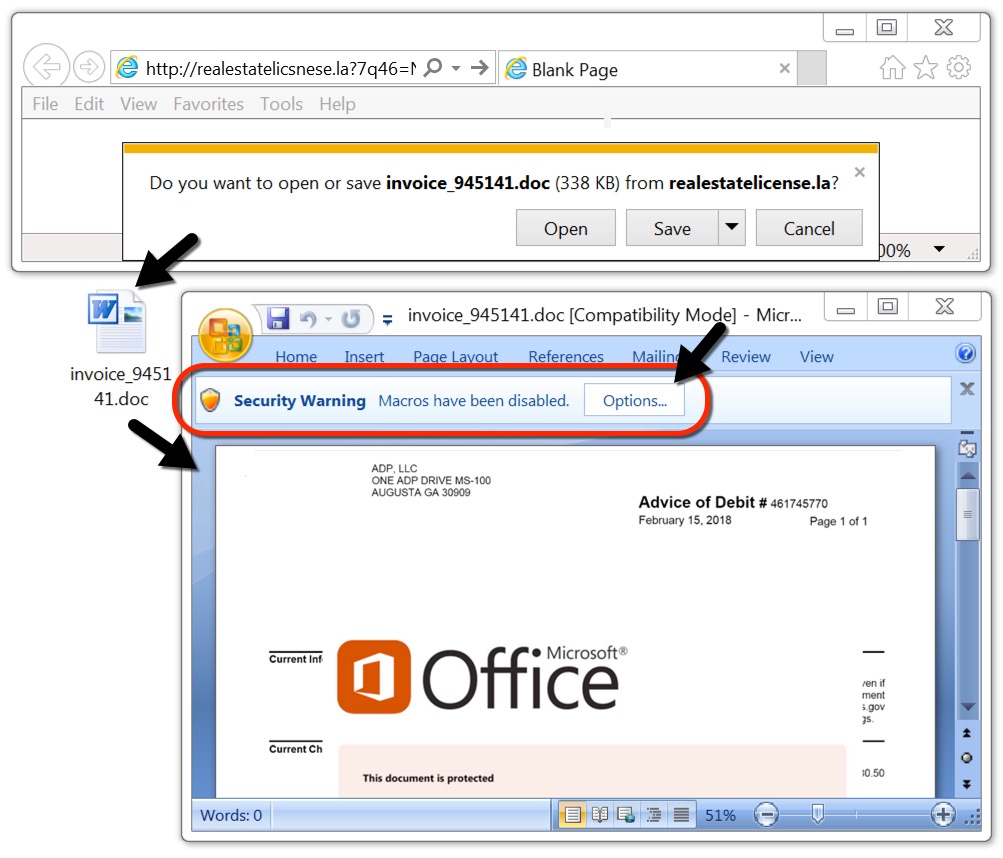
Shown above: Downloading a Word document from one of the emails.
EMAIL HEADERS:
- Date/Time: Tuesday 2018-02-20 as early as 15:47 through at least 20:12 UTC
- From (spoofed): "ADP, LLC" <un.payroll.invoice@apdm[.]com>
- Received: from ([75.144.249[.]209])
- Received: from ([76.237.148[.]143])
- Received: from apdm[.]com ([12.118.41[.]74])
- Received: from apdm[.]com ([24.18.144[.]193])
- Received: from apdm[.]com ([24.213.39[.]82])
- Received: from apdm[.]com ([47.190.13[.]102])
- Received: from apdm[.]com ([50.75.129[.]98])
- Received: from apdm[.]com ([50.77.19[.]245])
- Received: from apdm[.]com ([50.248.80[.]249])
- Received: from apdm[.]com ([64.31.248[.]50])
- Received: from apdm[.]com ([64.183.12[.]86])
- Received: from apdm[.]com ([65.153.153[.]118])
- Received: from apdm[.]com ([69.4.50[.]182])
- Received: from apdm[.]com ([70.91.150[.]67])
- Received: from apdm[.]com ([71.15.218[.]215])
- Received: from apdm[.]com ([72.76.45[.]178])
- Received: from apdm[.]com ([75.146.239[.]186])
- Received: from apdm[.]com ([117.240.183[.]117])
- Received: from apdm[.]com ([173.186.35[.]186])
- Received: from apdm[.]com ([173.209.154[.]162])
- Received: from apdm[.]com ([173.235.8[.]204])
- Received: from apdm[.]com ([185.99.139[.]214])
- Received: from apdm[.]com ([207.194.39[.]194])
- Received: from apdm[.]com ([208.67.102[.]180])
- Received: from apdm[.]com ([209.118.33[.]114])
- Received: from apdm[.]com ([216.7.131[.]82])
- Received: from apdm[.]com ([216.82.193[.]52])
- Received: from apdm[.]com ([216.218.189[.]211])
- Received: from apdm[.]com ([217.155.10[.]198])
- Received: from apdm[.]com ([218.197.8[.]26])
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 047165040
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 062383653
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 068118517
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 068385525
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 081870747
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 206611543
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 224331466
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 265360856
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 273258344
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 278020070
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 281036532
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 282152613
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 285474521
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 324623486
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 344321326
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 352164242
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 370563263
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 381310557
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 414713572
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 451315017
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 526237504
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 546271588
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 567075811
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 582484510
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 660404721
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 665524514
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 745258322
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 822521504
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 834775063
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 841467436
- Subject: ADP Payroll Invoice for week ending 02/16/2018 - 01728. Invoice: 861551581
TRAFFIC
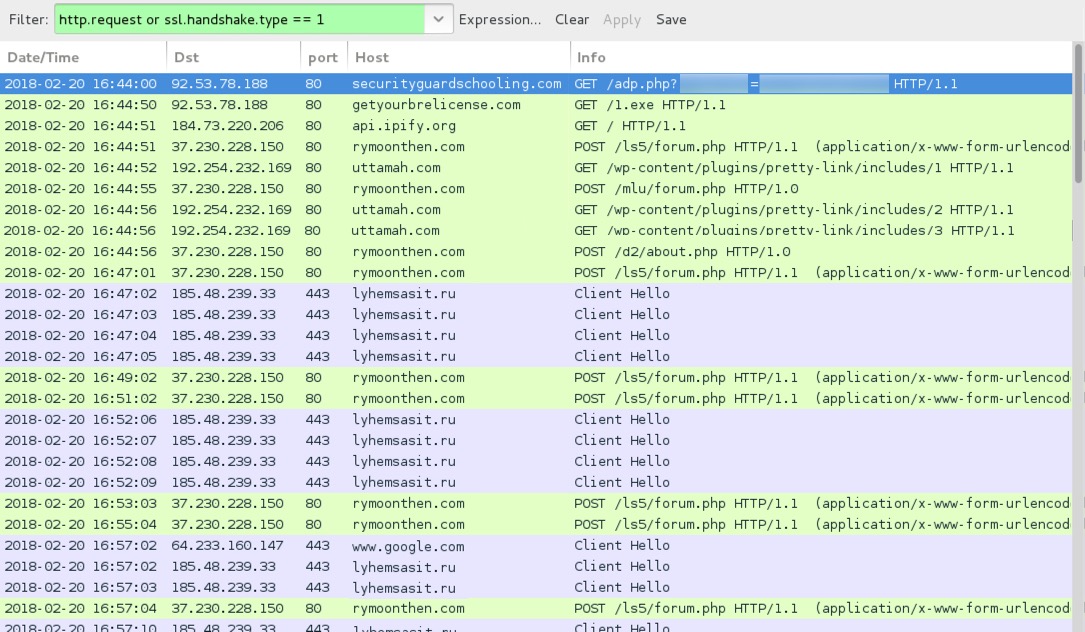
Shown above: Traffic from an .js-based Hancitor infection filtered in Wireshark.
LINKS IN THE EMAILS TO THE WORD DOCUMENT:
- hxxp[:]//beasecurityguard[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//brelicensewithus[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//brelicensewithus[.]com/adp.php?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//foodhandlerlicense[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//getabrelicense[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//getabrelicense[.]com/adp.php?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//getyourbrelicense[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//premierrealestateschools[.]info?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//premierrealestateschools[.]org?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//realestatelicense[.]la?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//realestateschools[.]training?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//realestatesschools[.]academy?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//realestatesschools[.]academy/adp.php?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//securityguardschooling[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//securityguardschooling[.]com/adp.php?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM MY INFECTED LAB HOST (.JS-BASED INFECTION):
- 92.53.78[.]188 port 80 - securityguardschooling[.]com - GET /adp.php?[string of characters]=[encoded string representing recipient's email address]
- 92.53.78[.]188 port 80 - getyourbrelicense[.]com - GET /1.exe
- api.ipify[.]org - GET /
- 37.230.228[.]150 port 80 - rymoonthen[.]com - POST /ls5/forum.php
- 37.230.228[.]150 port 80 - rymoonthen[.]com - POST /mlu/forum.php
- 37.230.228[.]150 port 80 - rymoonthen[.]com - POST /d2/about.php
- 192.254.232[.]169 port 80 - uttamah[.]com - GET /wp-content/plugins/pretty-link/includes/1
- 192.254.232[.]169 port 80 - uttamah[.]com - GET /wp-content/plugins/pretty-link/includes/2
- 192.254.232[.]169 port 80 - uttamah[.]com - GET /wp-content/plugins/pretty-link/includes/3
- 185.48.239[.]33 port 443 - lyhemsasit[.]ru - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- www.google[.]com - HTTPS traffic, probably a connectivity check by infected Windows host
FILE HASHES
MALWARE RETRIEVED FROM MY INFECTED HOSTS:
- SHA256 hash: 575f6764cc8041a1e7e22db8ed2db0eaa0a47989f6bfd26e63d867caa632225c
File size: 346,624 bytes
File name: invoice_143264.doc [any six random digits for the numbers]
File description: Word document with macro for Hancitor
- SHA256 hash: 56705514e3a93b7eb8a5555120eeb3f8b9b8e8a509dd0db2e7866dafcebb806a
File size: 35,396 bytes
File name: invoice_311706.js.doc [any six random digits for the numbers]
File description: JavaScript (.js) file to download and run Hancitor binary
- SHA256 hash: 27a7605e5246074d4eb119785d12d21d98833859f2623d95d56f3b3d9d6c1f37
File size: 61,440 bytes
File location: hxxp[:]//getyourbrelicense[.]com/1.exe
File location: C:\Users\[username]\WinHost32.exe
File description: Hancitor binary retreived by the .js file
- SHA256 hash: f8d02d9c20b45e4b558080e332beb710719151533b30c25cc53984d88ccc6769
File size: 169,984 bytes
File location: C:\Users\[username]\AppData\Local\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
IMAGES
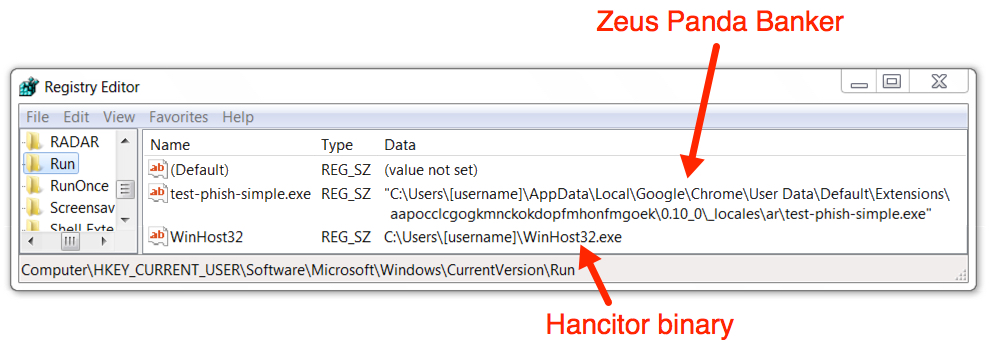
Shown above: Malware persistent on the infected Windows host through the Windows Registry.
Click here to return to the main page.