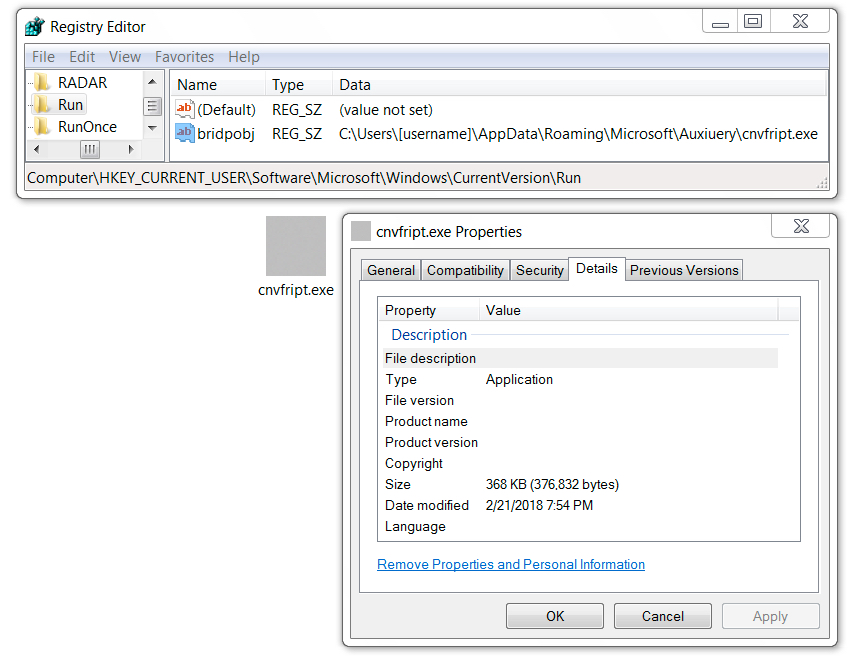
2018-02-21 - INFECTION TRAFFIC FROM ITALIAN DHL-THEMED MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2018-02-21-infection-traffic.pcap.zip 877.8 kB (877,787 bytes)
- 2018-02-21-infection-traffic.pcap (1,206,208 bytes)
- Zip archive of the email and malware: 2018-02-21-email-and-malware.zip 337.7 kB (337,734 bytes)
- 012725.js (24,970 bytes)
- 2018-02-21-malspam-1737-UTC.eml (2,919 bytes)
- conferma_ordine_57427.js (9,350 bytes)
- conferma_ordine_57427.zip (4,916 bytes)
- pzamd.exe (376,832 bytes)
ASSOCIATED FILES:
- Couldn't figure out what the follow-up malware binary is, but it used a Let's Encrypt certificate for HTTPS/SSL/TLS post-infection traffic.
- Confirmed by @James_inthe_box: the follow-up malware binary is Ursnif.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- deliveryclub-6589[.]download
- ockoy.deliveryclub-6589[.]download
- e32sg.deliveryclub-6589[.]download
- hxxp[:]//www.adrive[.]com/public/CczDyD.html
- hxxp[:]//downloadwww31.adrive[.]com/public/view/CczDyD.html
- delivery1class[.]download
- globalthlinkalgounsi[.]win
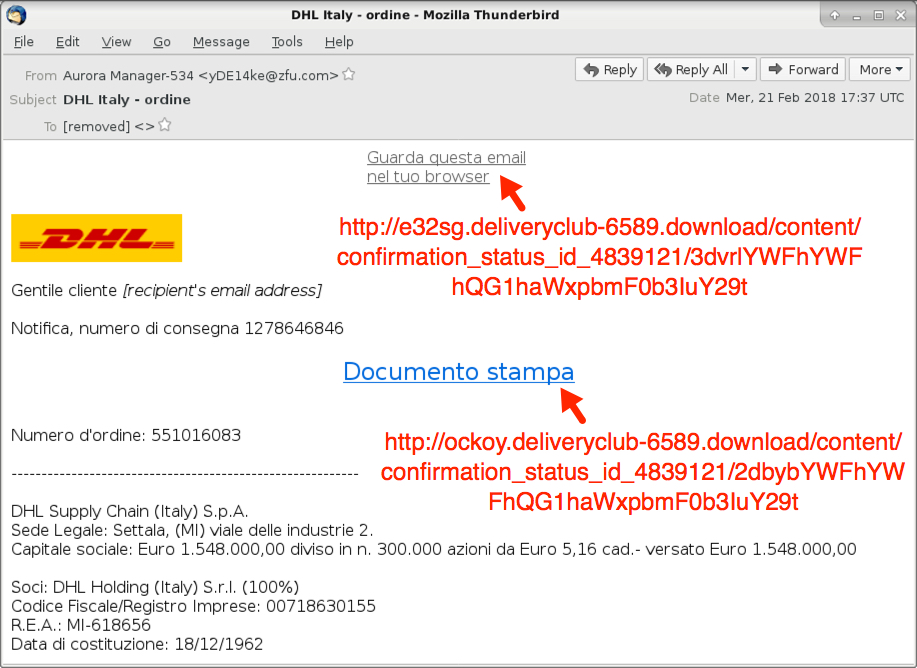
Shown above: Screenshot of the email.
EMAIL INFORMATION:
- Date: Wednesday, 2018-02-21 at 17:37 UTC
- Subject: DHL Italy - ordinet
- From: "Aurora Manager-534" <yDE14ke@zfu[.]com>
- Message-ID: <42C9860C3E8@gng[.]com>
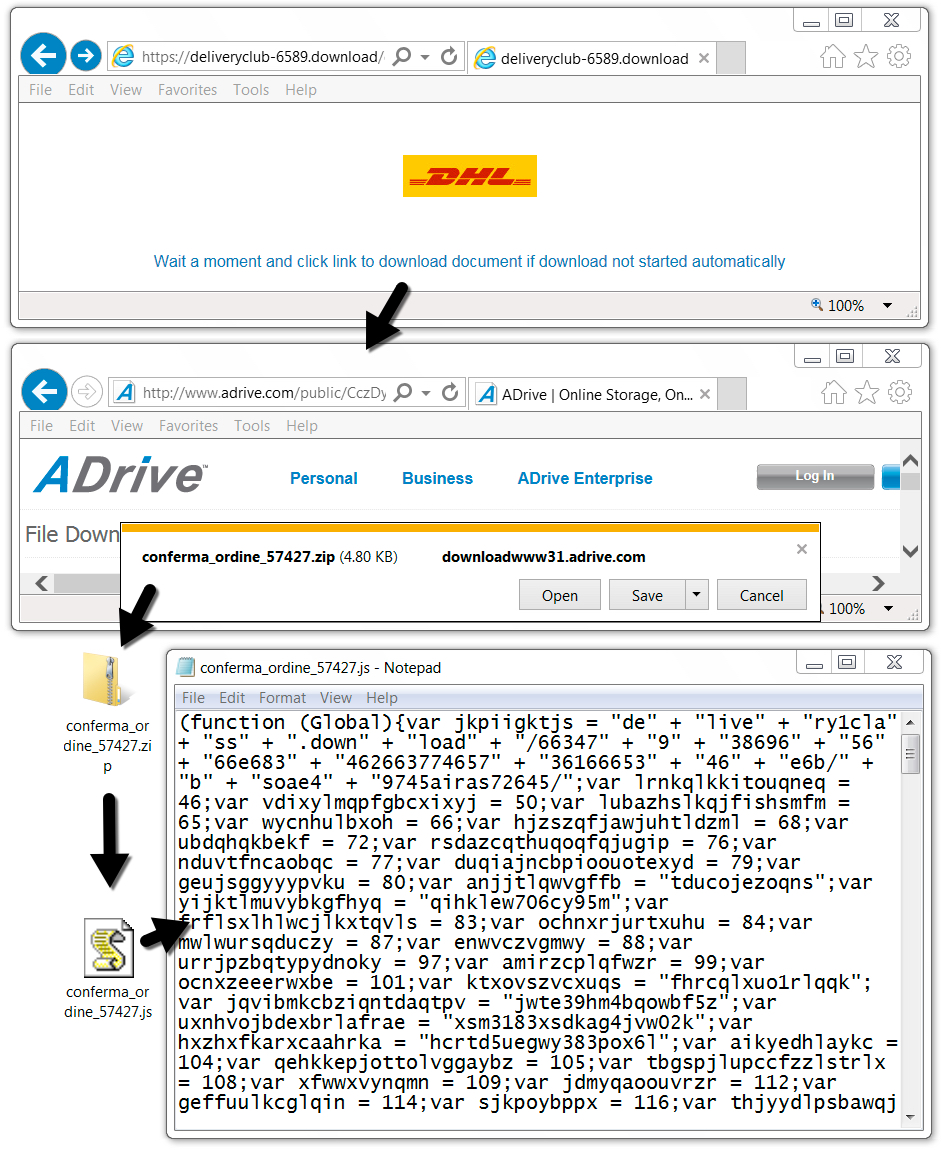
Shown above: Downloading the zip attachment and extracting the malicious .js file.
TRAFFIC
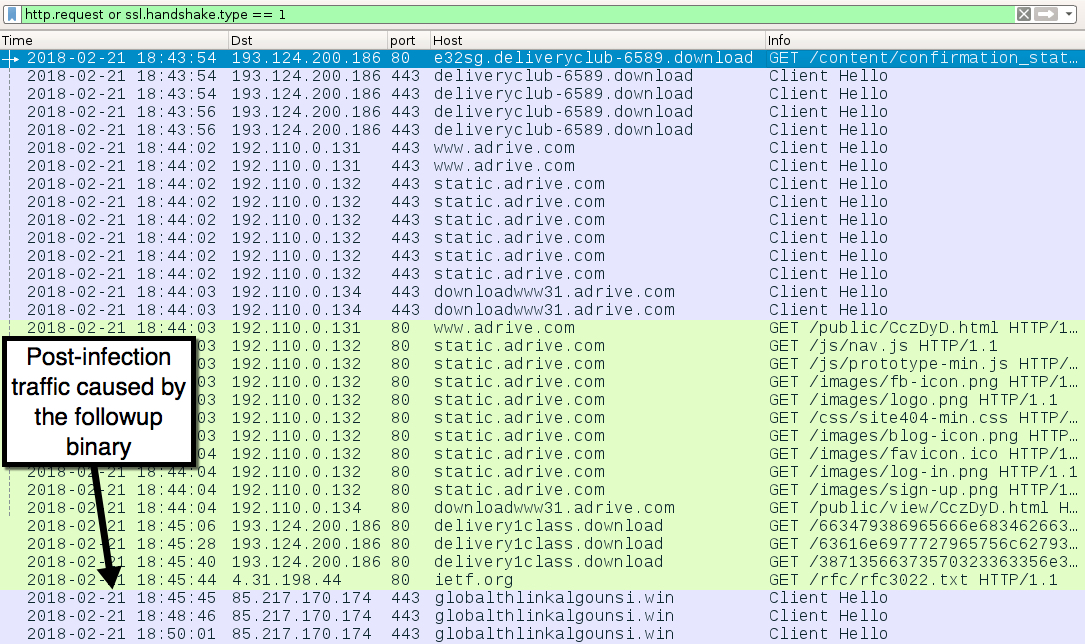
Shown above: Traffic from the infection filtered in Wireshark.
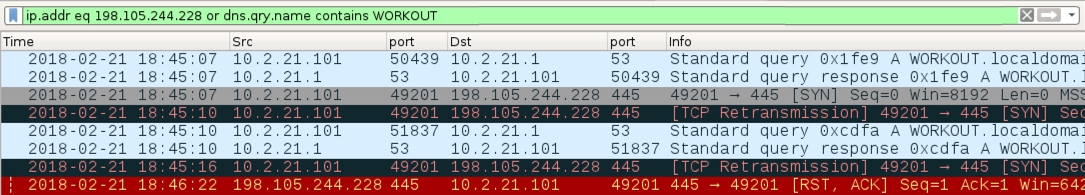
Shown above: This was somewhat odd. It happened right after the first HTTP request to delivery1class[.]download that returned JavaScript.
INFECTION TRAFFIC:
- 193.124.200[.]186 port 80 - e32sg.deliveryclub-6589[.]download - GET /content/confirmation_status_id_4839121/3dvrlYWFhYWFhQG1haWxpbmF0b3IuY29t
- 193.124.200[.]186 port 443 - deliveryclub-6589[.]download - HTTPS traffic
- port 443 - www.adrive[.]com - HTTPS traffic
- port 443 - static.adrive[.]com - HTTPS traffic
- port 443 - downloadwww31.adrive[.]com - HTTPS traffic
- port 80 - static.adrive[.]com - various HTTP GET requests
- port 80 - downloadwww31.adrive[.]com - GET /public/view/CczDyD.html
- 193.124.200[.]186 port 80 - delivery1class[.]download - GET /663479386965666e6834626637746573616665346e6b/bsoae49745airas72645/
- 193.124.200[.]186 port 80 - delivery1class[.]download - GET /63616e6977727965756c62793832383734637761383838/bvmaz49745jodlp72645/
- 193.124.200[.]186 port 80 - delivery1class[.]download - GET /38713566373570323363356e3835326e7076666f61337735386e/psnaw99735miups/
- port 80 - ietf[.]org - GET /rfc/rfc3022.txt
- 198.105.244[.]228 port 445 - WORKOUT.localdomain - Attempted TCP connections, but no response by the server
- 85.217.170[.]174 port 443 - globalthlinkalgounsi[.]win - post-infection HTTPS/SSL/TLS traffic
MALWARE
DOWNLOADED ZIP ARCHIVE:
- SHA256 hash: 631602fa73ea9bff18977726720a2e9fd6b55766be881a90cfe86a2f12de5fe5
File size: 4,916 bytes
File name: conferma_ordine_57427.zip
EXTRACTED .JS FILE:
- SHA256 hash: b7fd2515621c719ce8871a70fdb65dc96d0b2e3b73ac012f9008c6985ad28533
Any.Run analysis: https://app.any.run/tasks/7281de05-c7b3-45e5-b246-e777901a6ad3
File size: 9,350 bytes
File name: conferma_ordine_57427.js
.JS FILE FOUND ON THE INFECTED HOST:
- SHA256 hash: 0d1188384c71ab85abc0c209ba8a43a880c34ca34fad65cd8aaebc3ba88b0b50
File size: 24,970 bytes
File location: C:\Users\[username]\AppData\Local\Temp\012725.js
FOLLOW-UP BINARY (URSNIF):
- SHA256 hash: a99049ff0bf525b856c65d12acdcd9ef6c236e6228b96f8db68170aa35bb71c5
File size: 376,832 bytes
File location: C:\Users\[username]\AppData\Local\Temp\pzamd.exe
File location: C:\Users\[username]\AppData\Roaming\Microsoft\[random name]\[random letters].exe
Shown above: Follow-up malware persistent on the infected host.
Click here to return to the main page.