2018-03-01 - EMOTET ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-02-28-Emotet-malspam-tracker.csv.zip 2.3 kB (2,574 bytes)
- 2018-02-28-Emotet-malspam-41-examples.zip 63.9 kB (63,904 bytes)
- 2018-03-01-Emotet-malspam-tracker.csv.zip 1.2 kB (1,242 bytes)
- 2018-03-01-Emotet-emails-and-attachments.zip 228.9 kB (228,853 bytes)
- 2018-03-01-Emotet-infection-traffic.pcap.zip 846.4 kB (846,401 bytes)
- 2018-03-01-malware-from-Emotet-infection.zip 378.5 kB (378,498 bytes)
NOTES:
- I received some email examples from Wednesday 2018-02-28, and I wanted to document them, but I didn't have time until today.
- As of today, Emotet malspam is adding PDF attachments to its emails as described by Joseph Roosen in this tweet with further details in this pastebin post.
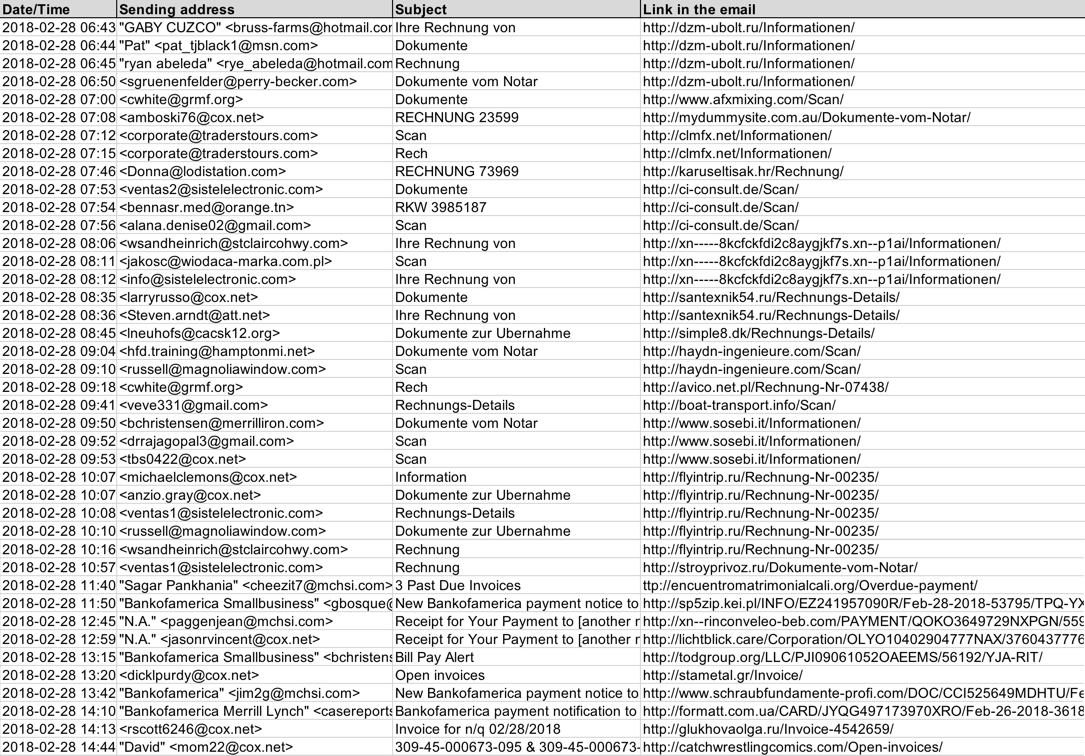
Shown above: Screenshot of the spreadsheet tracker.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- hxxp[:]//avico[.]net[.]pl/Rechnung-Nr-07438/
- hxxp[:]//boat-transport[.]info/Scan/
- hxxp[:]//catchwrestlingcomics[.]com/Open-invoices/
- hxxp[:]//ci-consult[.]de/Scan/
- hxxp[:]//clmfx[.]net/Informationen/
- hxxp[:]//dzm-ubolt[.]ru/Informationen/
- hxxp[:]//encuentromatrimonialcali[.]org/Overdue-payment/
- hxxp[:]//flyintrip[.]ru/Rechnung-Nr-00235/
- hxxp[:]//formatt[.]com[.]ua/CARD/JYQG497173970XRO/Feb-26-2018-36189271/PW-XDV/
- hxxp[:]//glukhovaolga[.]ru/Invoice-4542659/
- hxxp[:]//haydn-ingenieure[.]com/Scan/
- hxxp[:]//karuseltisak[.]hr/Rechnung/
- hxxp[:]//lichtblick.care/Corporation/OLYO10402904777NAX/37604377764/HRGS-BGPE-Feb-28-2018/
- hxxp[:]//mydummysite[.]com[.]au/Dokumente-vom-Notar/
- hxxp[:]//santexnik54[.]ru/Rechnungs-Details/
- hxxp[:]//simple8[.]dk/Rechnungs-Details/
- hxxp[:]//sp5zip.kei[.]pl/INFO/EZ241957090R/Feb-28-2018-53795/TPQ-YXNRR/
- hxxp[:]//stametal[.]gr/Invoice/
- hxxp[:]//stroyprivoz[.]ru/Dokumente-vom-Notar/
- hxxp[:]//todgroup[.]org/LLC/PJI09061052OAEEMS/56192/YJA-RIT/
- hxxp[:]//www.abexport[.]com/1ZQqbk/
- hxxp[:]//www.afxmixing[.]com/Scan/
- hxxp[:]//www.schraubfundamente-profi[.]com/DOC/CCI525649MDHTU/Feb-28-2018-13648823447/MQ-WBLNK-Feb-28-2018/
- hxxp[:]//www.sosebi[.]it/Informationen/
- hxxp[:]//xn-----8kcfckfdi2c8aygjkf7s[.]xn--p1ai/Informationen/
- hxxp[:]//xn--rinconveleo-beb[.]com/PAYMENT/QOKO3649729NXPGN/55905945473/SSZS-JEH/
EMAILS
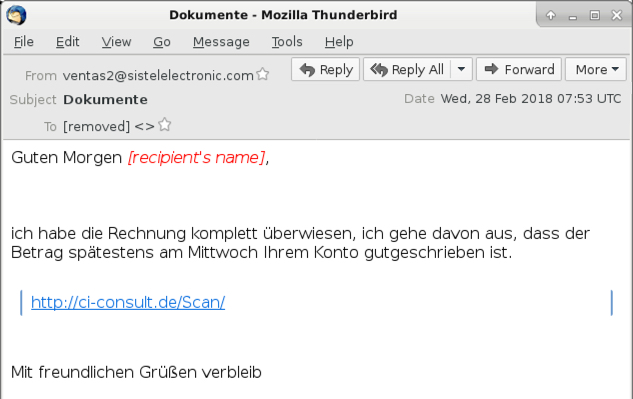
Shown above: Screenshot from one of the emails (1 of 3).
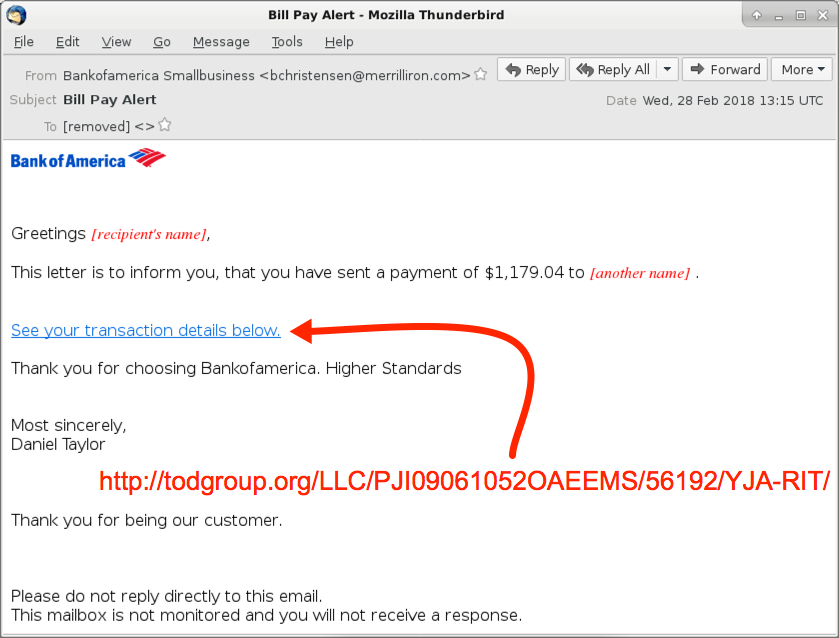
Shown above: Screenshot from one of the emails (2 of 3).
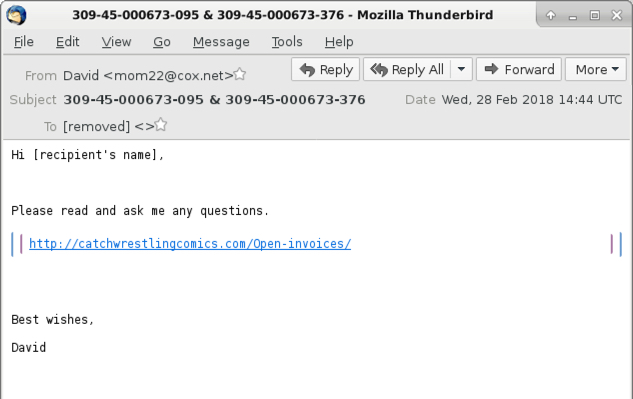
Shown above: Screenshot from one of the emails (3 of 3).
EMAIL HEADERS:
- 2018-02-28 06:43 UTC - From: "GABY CUZCO" <bruss-farms@hotmail[.]com> - Subject: Ihre Rechnung von
- 2018-02-28 06:44 UTC - From: "Pat" <pat_tjblack1@msn[.]com> - Subject: Dokumente
- 2018-02-28 06:45 UTC - From: "ryan abeleda" <rye_abeleda@hotmail[.]com> - Subject: Rechnung
- 2018-02-28 06:50 UTC - From: <sgruenenfelder@perry-becker[.]com> - Subject: Dokumente vom Notar
- 2018-02-28 07:00 UTC - From: <cwhite@grmf[.]org> - Subject: Dokumente
- 2018-02-28 07:08 UTC - From: <amboski76@cox[.]net> - Subject: RECHNUNG 23599
- 2018-02-28 07:12 UTC - From: <corporate@traderstours[.]com> - Subject: Scan
- 2018-02-28 07:15 UTC - From: <corporate@traderstours[.]com> - Subject: Rech
- 2018-02-28 07:46 UTC - From: <Donna@lodistation[.]com> - Subject: RECHNUNG 73969
- 2018-02-28 07:53 UTC - From: <ventas2@sistelelectronic[.]com> - Subject: Dokumente
- 2018-02-28 07:54 UTC - From: <bennasr.med@orange[.]tn> - Subject: RKW 3985187
- 2018-02-28 07:56 UTC - From: <alana.denise02@gmail[.]com> - Subject: Scan
- 2018-02-28 08:06 UTC - From: <wsandheinrich@stclaircohwy[.]com> - Subject: Ihre Rechnung von
- 2018-02-28 08:11 UTC - From: <jakosc@wiodaca-marka[.]com[.]pl> - Subject: Scan
- 2018-02-28 08:12 UTC - From: <info@sistelelectronic[.]com> - Subject: Ihre Rechnung von
- 2018-02-28 08:35 UTC - From: <larryrusso@cox[.]net> - Subject: Dokumente
- 2018-02-28 08:36 UTC - From: <Steven.arndt@att[.]net> - Subject: Ihre Rechnung von
- 2018-02-28 08:45 UTC - From: <lneuhofs@cacsk12[.]org> - Subject: Dokumente zur Ubernahme
- 2018-02-28 09:04 UTC - From: <hfd.training@hamptonmi[.]net> - Subject: Dokumente vom Notar
- 2018-02-28 09:10 UTC - From: <russell@magnoliawindow[.]com> - Subject: Scan
- 2018-02-28 09:18 UTC - From: <cwhite@grmf[.]org> - Subject: Rech
- 2018-02-28 09:41 UTC - From: <veve331@gmail[.]com> - Subject: Rechnungs-Details
- 2018-02-28 09:50 UTC - From: <bchristensen@merrilliron[.]com> - Subject: Dokumente vom Notar
- 2018-02-28 09:52 UTC - From: <drrajagopal3@gmail[.]com> - Subject: Scan
- 2018-02-28 09:53 UTC - From: <tbs0422@cox[.]net> - Subject: Scan
- 2018-02-28 10:07 UTC - From: <michaelclemons@cox[.]net> - Subject: Information
- 2018-02-28 10:07 UTC - From: <anzio.gray@cox[.]net> - Subject: Dokumente zur Ubernahme
- 2018-02-28 10:08 UTC - From: <ventas1@sistelelectronic[.]com> - Subject: Rechnungs-Details
- 2018-02-28 10:10 UTC - From: <russell@magnoliawindow[.]com> - Subject: Dokumente zur Ubernahme
- 2018-02-28 10:16 UTC - From: <wsandheinrich@stclaircohwy[.]com> - Subject: Rechnung
- 2018-02-28 10:57 UTC - From: <ventas1@sistelelectronic[.]com> - Subject: Rechnung
- 2018-02-28 11:40 UTC - From: "Sagar Pankhania" <cheezit7@mchsi[.]com> - Subject: 3 Past Due Invoices
- 2018-02-28 11:50 UTC - From: "Bankofamerica Smallbusiness" <gbosque@cox[.]net> - Subject: New Bankofamerica payment notice to [another name]
- 2018-02-28 12:45 UTC - From: "N.A." <paggenjean@mchsi[.]com> - Subject: Receipt for Your Payment to [another name]
- 2018-02-28 12:59 UTC - From: "N.A." <jasonrvincent@cox[.]net> - Subject: Receipt for Your Payment to [another name]
- 2018-02-28 13:15 UTC - From: "Bankofamerica Smallbusiness" <bchristensen@merrilliron[.]com> - Subject: Bill Pay Alert
- 2018-02-28 13:20 UTC - From: <dicklpurdy@cox[.]net> - Subject: Open invoices
- 2018-02-28 13:42 UTC - From: "Bankofamerica" <jim2g@mchsi[.]com> - Subject: New Bankofamerica payment notice to [recipient's name]
- 2018-02-28 14:10 UTC - From: "Bankofamerica Merrill Lynch" <casereports@scireslit[.]com> - Subject: Bankofamerica payment notification to [recipient's name]
- 2018-02-28 14:13 UTC - From: <rscott6246@cox[.]net> - Subject: Invoice for n/q 02/28/2018
- 2018-02-28 14:44 UTC - From: "David" <mom22@cox[.]net> - Subject: 309-45-000673-095 & 309-45-000673-376
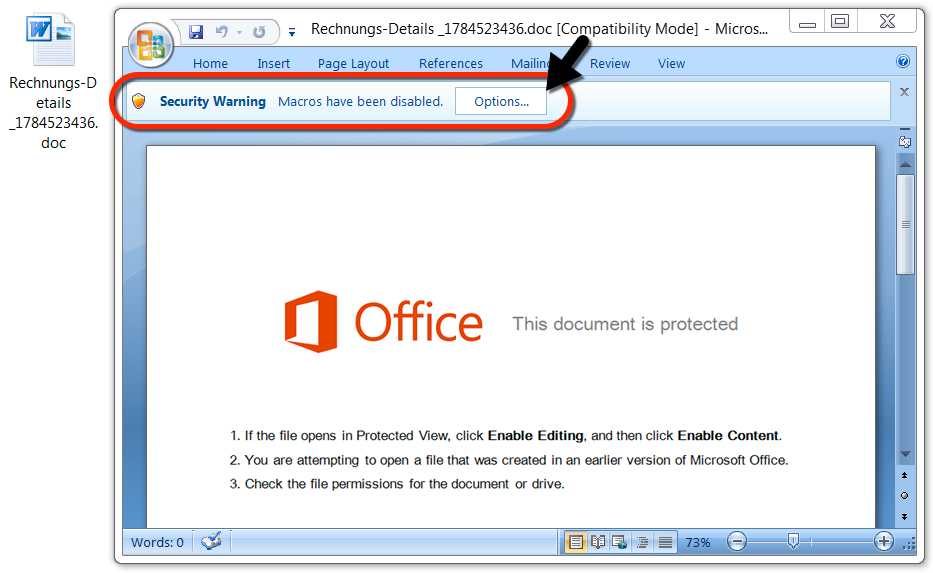
Shown above: Example of a Word document downloaded from one of the email links.
TRAFFIC
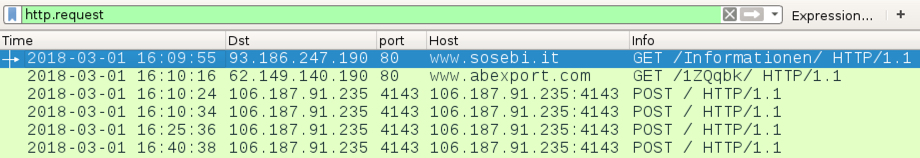
Shown above: Infection traffic filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 93.186.247[.]190 port 80 - www.sosebi[.]it - GET /Informationen/
- 62.149.140[.]190 port 80 - www.abexport[.]com - GET /1ZQqbk/
- 106.187.91[.]235 port 4143 - 106.187.91[.]235:4143 - POST /
FILE HASHES
MALWARE FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 1fa89fc30aeb12427c5486137ffb18dca89806755379da8e5bdf010e0e6b1264
File size: 259,072 bytes
File name: Rechnungs-Details _1784523436.doc
File description: Word document with macro for Emotet
- SHA256 hash: 1be3c5a54c962af1d266f0bb97ca2340e76885825159d1a78ed88a508978f29f
File size: 163,328 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random name].exe
File description: Emotet executable file
- SHA256 hash: 17a0d59255046ed2cff22cd5980fcc86c69e059839fec07d705051ac2e178693
File size: 233,472 bytes
File location: C:\ProgramFiles\bh3EQr.exe File description: More malware downloaded by Emotet (don't know what this one is)
IMAGES
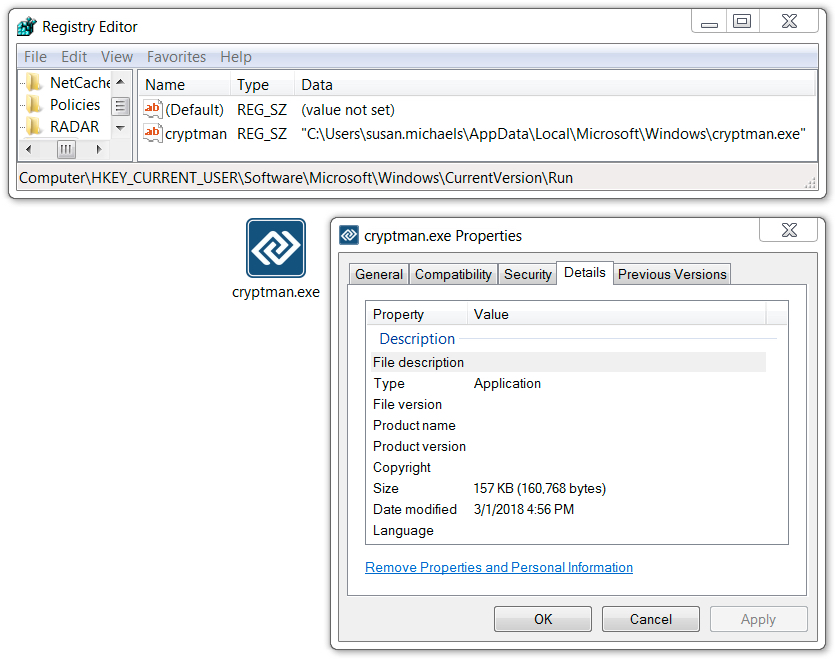
Shown above: Emotet binary persistent on the infected Windows host.
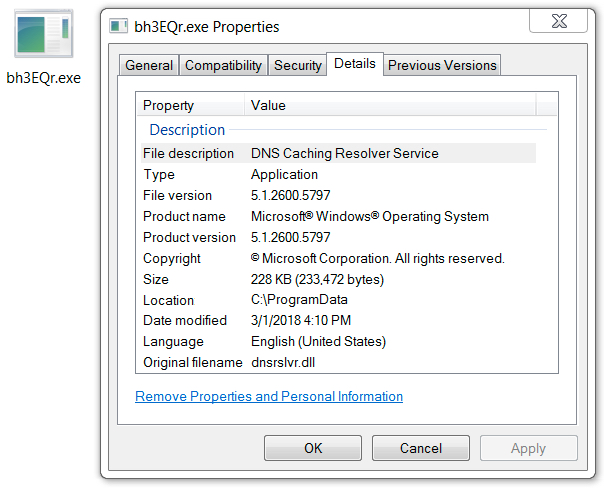
Shown above: Follow-up malware seen during an Emotet infection.
Click here to return to the main page.
