2018-03-07 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-03-07-Hancitor-infection-traffic-2-pcaps.zip 2.2 MB (2,224,049 bytes)
- 2018-03-07-Hancitor-infection-traffic.pcap (2,484,788 bytes)
- 2018-03-07-Zeus-Panda-Banker-infection-traffic.pcap (15,218 bytes)
- Zip archive of the emails: 2018-03-07-Hancitor-malspam-26-examples.txt.zip 13.5 kB (13,512 bytes)
- 2018-03-07-Hancitor-malspam-26-examples.txt (442,183 bytes)
- Zip archive of the malware: 2018-03-07-malware-from-Hancitor-infection.zip 233 kB (233,430 bytes)
- 2018-03-07-Hancitor-maldoc-invoice_276194.doc (226,304 bytes)
- 2018-03-07-Zeus-Panda-Banker.exe (163,840 bytes)
NOTES:
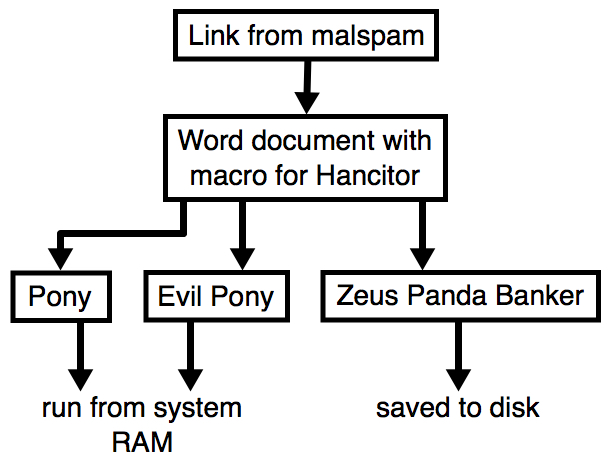
- As usual, for the 3 follow-up downloads, we're still seeing Pony, Evil Pony (both resident in memory), and Zeus Panda Banker (saved to disk).
- The block list contains additional post-infection URLs originally reported by @Techhelplistcom on the VirusTotal entry for today's Word document.
- My thanks to @Techhelplistcom, @James_inthe_box, and everyone else who keeps an eye on this malspam and reports about it near-real-time on Twitter.
Shown above: Screenshot from one of the emails.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- batcommunications[.]com
- creditdamageconsultant[.]com
- florida-pawn[.]com
- hnimgmt[.]com
- hollywood-pawn[.]com
- kanzlercompanies[.]com
- kastarqsr[.]com
- margate-pawn[.]com
- morris-law-firm[.]com
- myyogaberry[.]com
- starcorpinc[.]com
- toetallynailed[.]com
- cirewandbut[.]com
- babronwronot[.]ru
- romfinothad[.]ru
- hxxp[:]//mypartnerforever[.]me/wp-includes/customize/1
- hxxp[:]//mypartnerforever[.]me/wp-includes/customize/2
- hxxp[:]//mypartnerforever[.]me/wp-includes/customize/3
- hxxp[:]//euforia-piekna[.]pl/wp-content/plugins/thumbnail-for-excerpts/1
- hxxp[:]//euforia-piekna[.]pl/wp-content/plugins/thumbnail-for-excerpts/2
- hxxp[:]//euforia-piekna[.]pl/wp-content/plugins/thumbnail-for-excerpts/3
- hxxp[:]//helpfulcrooks[.]com/wp-content/plugins/bwp-recent-comments/includes/1
- hxxp[:]//helpfulcrooks[.]com/wp-content/plugins/bwp-recent-comments/includes/2
- hxxp[:]//helpfulcrooks[.]com/wp-content/plugins/bwp-recent-comments/includes/3
- hxxp[:]//prontohotel[.]fr/reiseblog/wp-content/plugins/wp-no-category-base/1
- hxxp[:]//prontohotel[.]fr/reiseblog/wp-content/plugins/wp-no-category-base/2
- hxxp[:]//prontohotel[.]fr/reiseblog/wp-content/plugins/wp-no-category-base/3
- hxxp[:]//eng.mhb[.]mx/wp-content/plugins/get-the-image/1
- hxxp[:]//eng.mhb[.]mx/wp-content/plugins/get-the-image/2
- hxxp[:]//eng.mhb[.]mx/wp-content/plugins/get-the-image/3
- diheclerow[.]ru
EMAILS
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2018-03-07 as early as 16:28 UTC through at least 18:52 UTC
- Received: from rachelallan[.]com ([24.43.154[.]229])
- Received: from rachelallan[.]com ([67.212.207[.]69])
- Received: from rachelallan[.]com ([68.185.227[.]33])
- Received: from rachelallan[.]com ([70.90.35[.]129])
- Received: from rachelallan[.]com ([75.145.156[.]49])
- Received: from trivalleyurology[.]com ([24.240.172[.]42])
- Received: from trivalleyurology[.]com ([50.247.22[.]145])
- Received: from trivalleyurology[.]com ([50.248.192[.]49])
- Received: from trivalleyurology[.]com ([66.97.110[.]230])
- Received: from trivalleyurology[.]com ([67.221.222[.]194])
- Received: from trivalleyurology[.]com ([70.182.4[.]13])
- Received: from trivalleyurology[.]com ([71.206.183[.]184])
- Received: from trivalleyurology[.]com ([73.103.77[.]175])
- Received: from trivalleyurology[.]com ([73.237.189[.]90])
- Received: from trivalleyurology[.]com ([75.106.127[.]147])
- Received: from trivalleyurology[.]com ([75.129.211[.]11])
- Received: from trivalleyurology[.]com ([76.70.31[.]65])
- Received: from trivalleyurology[.]com ([96.82.224[.]81])
- Received: from trivalleyurology[.]com ([99.254.166[.]184])
- Received: from trivalleyurology[.]com ([108.20.23[.]234])
- Received: from trivalleyurology[.]com ([108.189.55[.]3])
- Received: from trivalleyurology[.]com ([199.5.189[.]237])
- Received: from trivalleyurology[.]com ([206.127.114[.]54])
- Received: from trivalleyurology[.]com ([207.150.250[.]2])
- Received: from trivalleyurology[.]com ([208.80.167[.]34])
- From: "PayPal Inc" <invoice@rachelallan[.]com>
- From: "PayPal Inc" <invoice@trivalleyurology[.]com>
- From: "PayPal Invoice Service" <invoice@rachelallan[.]com>
- From: "PayPal Invoice Service" <invoice@trivalleyurology[.]com>
- From: "PayPal Services" <invoice@rachelallan[.]com>
- From: "PayPal Services" <invoice@trivalleyurology[.]com>
- Subject: PayPal Message
- Subject: PayPal Notification
- Subject: PayPal Invoice Message
- Subject: PayPal Invoice Notification
- Subject: PayPal Automated Message
- Subject: PayPal Automated Notice
- Subject: PayPal Automated Notification
- Subject: PayPal Automated Invoice Message
- Subject: PayPal Automated Invoice Notification
- Subject: PayPal Automatic Message
- Subject: PayPal Automatic Notice
- Subject: PayPal Automatic Notification
- Subject: PayPal Automatic Invoice Message
- Subject: PayPal Electronic Message
- Subject: PayPal Electronic Notice
- Subject: PayPal Electronic Invoice Message
- Subject: PayPal Electronic Invoice Notice
- Subject: PayPal Electronic Invoice Notification
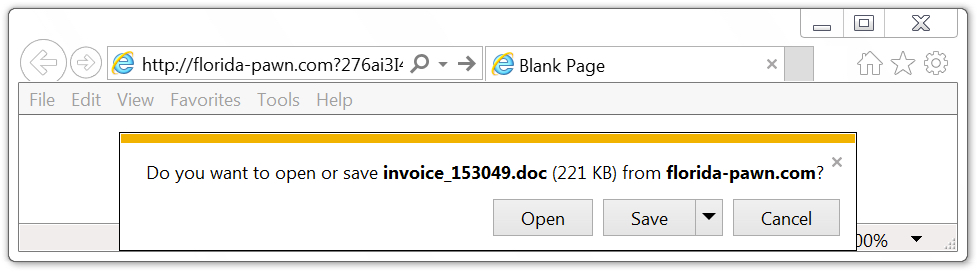
Shown above: Clicking on a link from one of the malspam examples.
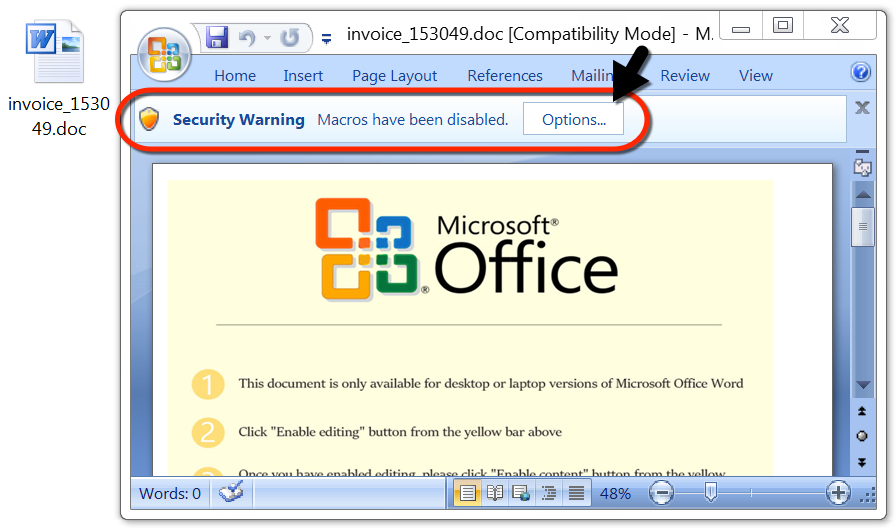
Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
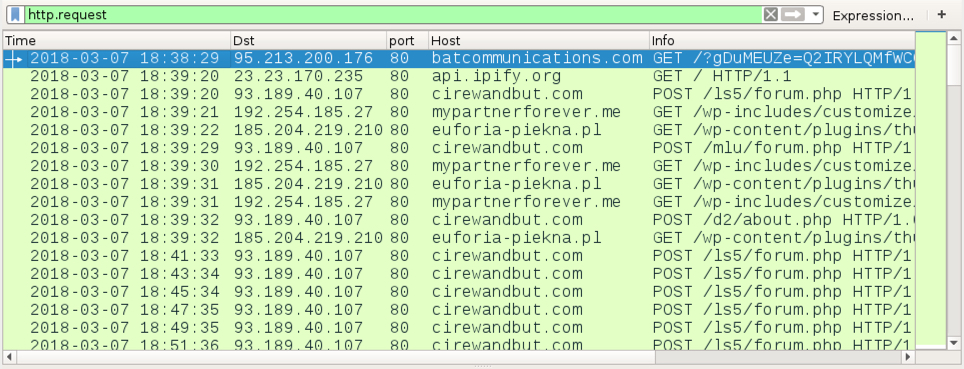
Shown above: Traffic from an infection filtered in Wireshark.
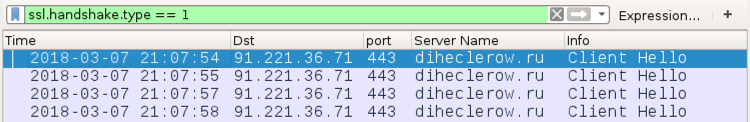
Shown above: Zeus Panda Banker traffic filtered in Wireshark.
LINKS IN THE EMAILS FOR THE WORD DOCUMENT:
- hxxp[:]//batcommunications[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//hnimgmt[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//hnimgmt[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//hnimgmt[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//hollywood-pawn[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//kastarqsr[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//kastarqsr[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//margate-pawn[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//morris-law-firm[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//myyogaberry[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//starcorpinc[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//toetallynailed[.]com?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 95.213.200[.]176 port 80 - batcommunications[.]com - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify[.]org - GET /
- 93.189.40[.]107 port 80 - cirewandbut[.]com - POST /ls5/forum.php
- 93.189.40[.]107 port 80 - cirewandbut[.]com - POST /mlu/forum.php
- 93.189.40[.]107 port 80 - cirewandbut[.]com - POST /d2/about.php
- 192.254.185[.]27 port 80 - mypartnerforever[.]me - GET /wp-includes/customize/1
- 192.254.185[.]27 port 80 - mypartnerforever[.]me - GET /wp-includes/customize/2
- 192.254.185[.]27 port 80 - mypartnerforever[.]me - GET /wp-includes/customize/3
- 185.204.219[.]210 port 80 - euforia-piekna[.]pl - GET /wp-content/plugins/thumbnail-for-excerpts/1
- 185.204.219[.]210 port 80 - euforia-piekna[.]pl - GET /wp-content/plugins/thumbnail-for-excerpts/2
- 185.204.219[.]210 port 80 - euforia-piekna[.]pl - GET /wp-content/plugins/thumbnail-for-excerpts/3
- 91.221.36[.]71 port 443 - diheclerow[.]ru - HTTPS/SSL/TLS traffic from Zeus Panda Banker
- port 443 - google[.]com - connectivity check caused by Zeus Panda Banker
FILE HASHES
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 1d63cfe0c0b6c80212aafef737fc63f63415634c74ac3159966f63c31c1a08d4
File size: 226,304 bytes
File name: invoice_276194.doc [any six random digits for the numbers]
File description: Word document with macro for Hancitor
- SHA256 hash: b148c9c73420619ac3efa018261da3f29b5bf86e2b1aded5895cc26dd74dd159
File size: 163,840 bytes
File location: C:\Users\[username]\AppData\Local\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
IMAGES
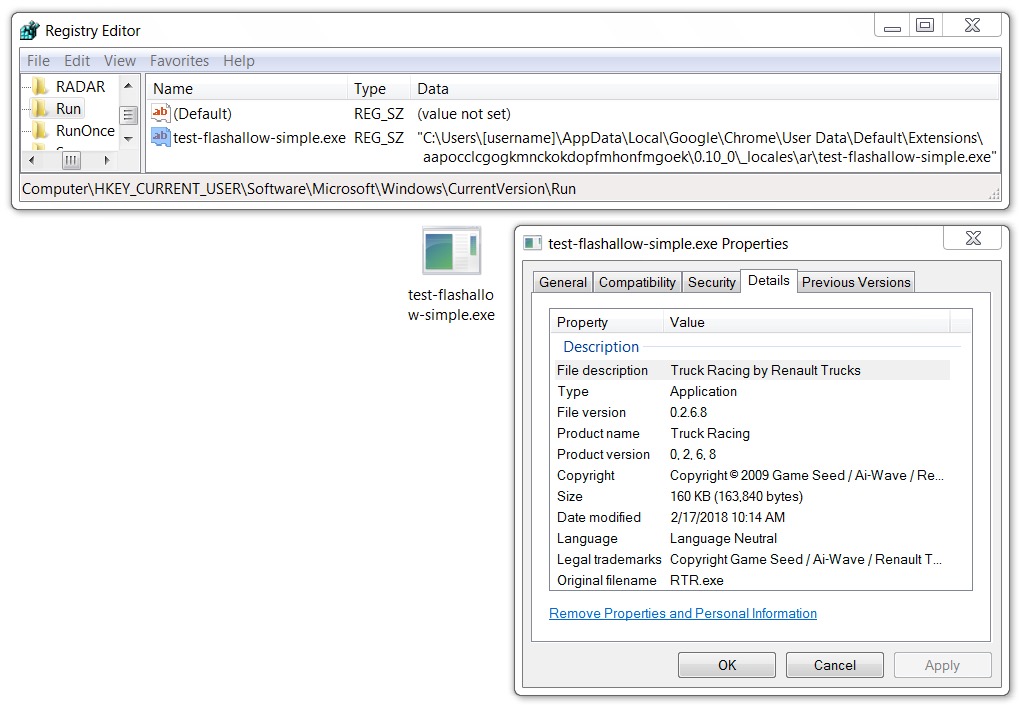
Shown above: Zeus Panda Banker persistent on an infected Windows host.
Click here to return to the main page.