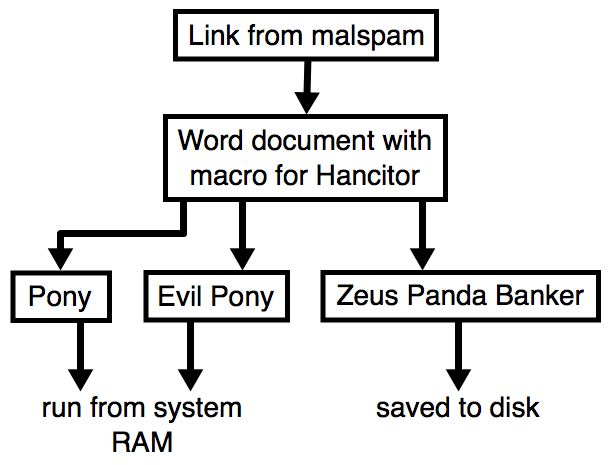
2018-03-13 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-03-13-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 2.2 MB (2,154,639 bytes)
- 2018-03-13-Hancitor-infection-with-Zeus-Panda-Bankerc.pcap (2,527,531 bytes)
- Zip archive of the emails: 2018-03-13-Hancitor-malspam-4-examples.txt.zip 4.6 kB (4,576 bytes)
- 2018-03-13-Hancitor-malspam-4-examples.txt (57,934 bytes)
- Zip archive of the malware: 2018-03-13-malware-from-Hancitor-infection.zip 233 kB (233,142 bytes)
- 2018-03-13-Hancitor-maldoc-invoice_169842.doc (230,912 bytes)
- 2018-03-13-Zeus-Panda-Banker.exe (180,224 bytes)
NOTES:
- As usual, for the 3 follow-up downloads, we're still seeing Pony, Evil Pony (both resident in memory), and Zeus Panda Banker (saved to disk).
- The block list contains additional post-infection URLs originally reported by @Techhelplistcom on the VirusTotal entry for today's Word document.
- My thanks to @James_inthe_box and everyone else who keeps an eye on this malspam and reports about it near-real-time on Twitter.
Shown above: Flow chart for a typical Hancitor malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- barmitzvahswag[.]com
- bnaimitzvahswag[.]com
- celticsradionetwork[.]com
- bostoncelticsradionetwork[.]com
- dssincorp[.]com
- globalspeaktraducciones[.]com
- oliviasacklerphotography[.]com
- soundpromos[.]com
- stevesackler[.]com
- sumohimbe[.]com
- himwotoldheg[.]ru
- guhanropug[.]ru
- hxxp://xn--gnstiger-baukredit-m6b[.]net//wp-content/plugins/simple-301-redirects/1
- hxxp://xn--gnstiger-baukredit-m6b[.]net//wp-content/plugins/simple-301-redirects/2
- hxxp://xn--gnstiger-baukredit-m6b[.]net//wp-content/plugins/simple-301-redirects/4
- hxxp://naturewasher[.]com/wp-content/plugins/new-google-plus-badge-widget/1
- hxxp://naturewasher[.]com/wp-content/plugins/new-google-plus-badge-widget/2
- hxxp://naturewasher[.]com/wp-content/plugins/new-google-plus-badge-widget/4
- hxxp://yourpersonalenergyspecialist[.]com/wp-content/plugins/jetpack/modules/1
- hxxp://yourpersonalenergyspecialist[.]com/wp-content/plugins/jetpack/modules/2
- hxxp://yourpersonalenergyspecialist[.]com/wp-content/plugins/jetpack/modules/4
- hxxp://gzoxhi[.]tokyo/wp-content/plugins/wp-multibyte-patch/1
- hxxp://gzoxhi[.]tokyo/wp-content/plugins/wp-multibyte-patch/2
- hxxp://gzoxhi[.]tokyo/wp-content/plugins/wp-multibyte-patch/4
- hxxp://coconutislandvilla[.]com/wp-content/plugins/soliloquy-lite/1
- hxxp://coconutislandvilla[.]com/wp-content/plugins/soliloquy-lite/2
- hxxp://coconutislandvilla[.]com/wp-content/plugins/soliloquy-lite/4
- lohidaleft[.]com
EMAILS
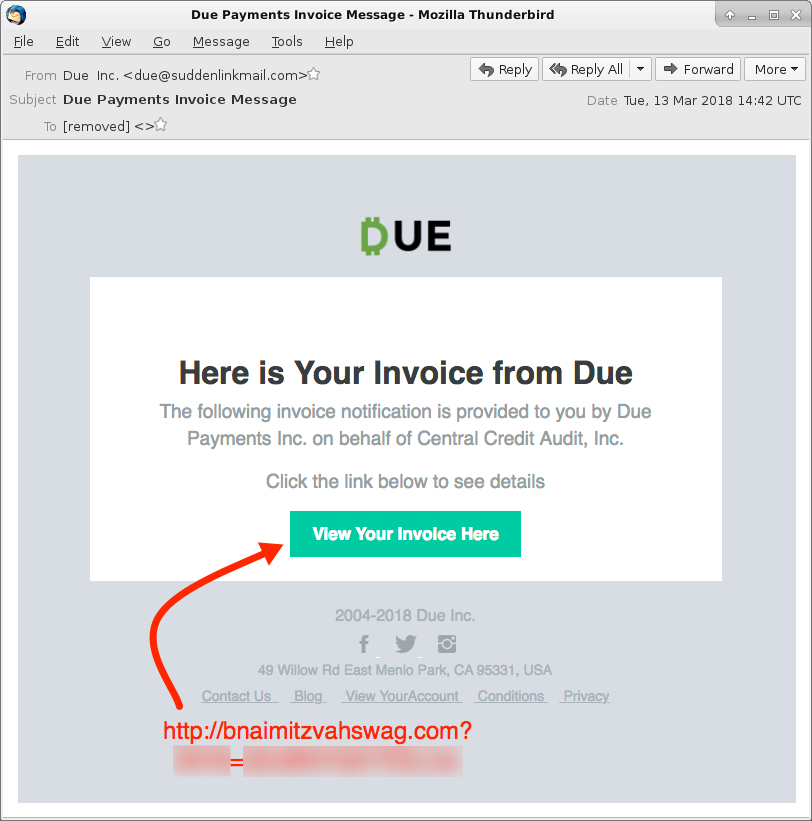
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Tuesday 2018-03-13 as early as 14:42 UTC through at least 15:13 UTC
- Received: from suddenlinkmail[.]com([23.30.139[.]233])
- Received: from suddenlinkmail[.]com ([50.242.219[.]161])
- Received: from tclimo[.]com ([76.18.161[.]40])
- Received: from tclimo[.]com ([96.89.73[.]5])
- From: "Due " <due@suddenlinkmail[.]com>
- From: "Due " <due@tclimo[.]com>
- From: "Due Inc." <due@suddenlinkmail[.]com>
- From: "Due Inc." <due@tclimo[.]com>
- Subject: Due Payments Invoice Message
- Subject: Due Message
- Subject: Due Invoice Notification
- Subject: Due Notification
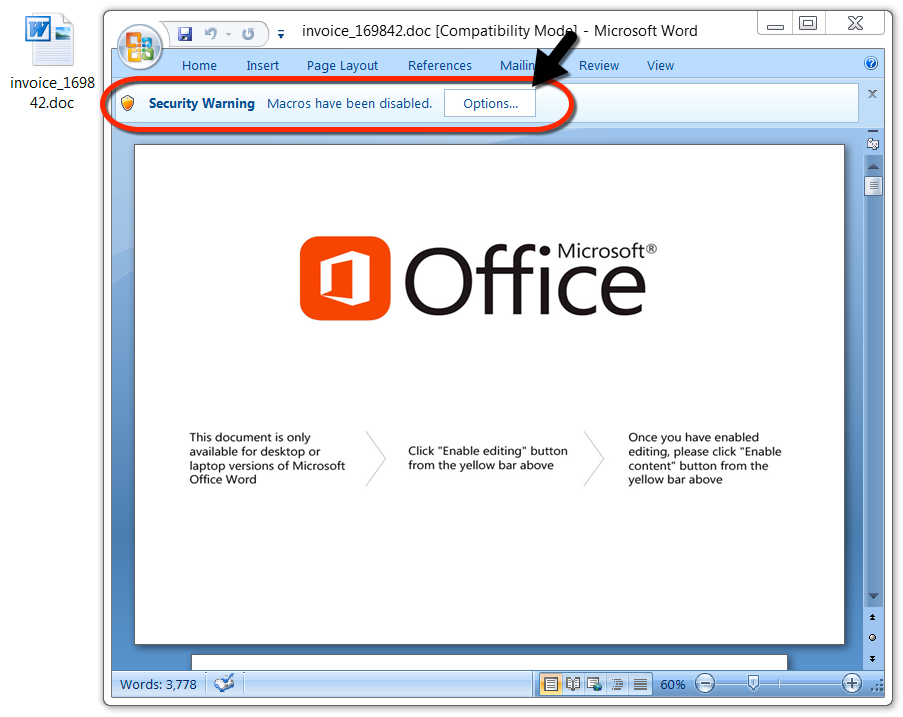
Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
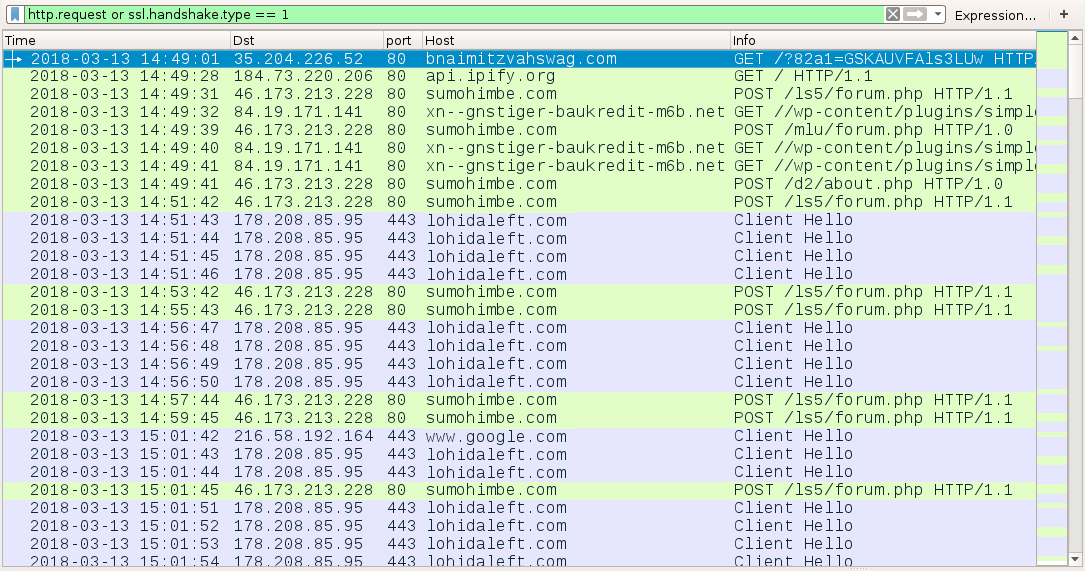
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS FOR THE WORD DOCUMENT:
- hxxp://barmitzvahswag[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp://bnaimitzvahswag[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp://bostoncelticsradionetwork[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp://celticsradionetwork[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp://dssincorp[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp://soundpromos[.]com?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 35.204.226[.]52 port 80 - bnaimitzvahswag[.]com - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify.org - GET /
- 46.173.213[.]228 port 80 - sumohimbe[.]com - POST /ls5/forum.php
- 46.173.213[.]228 port 80 - sumohimbe[.]com - POST /mlu/forum.php
- 46.173.213[.]228 port 80 - sumohimbe[.]com - POST /d2/about.php
- 84.19.171[.]141 port 80 - xn--gnstiger-baukredit-m6b[.]net - GET //wp-content/plugins/simple-301-redirects/1
- 84.19.171[.]141 port 80 - xn--gnstiger-baukredit-m6b[.]net - GET //wp-content/plugins/simple-301-redirects/2
- 84.19.171[.]141 port 80 - xn--gnstiger-baukredit-m6b[.]net - GET //wp-content/plugins/simple-301-redirects/4
- 178.208.85[.]95 port 443 - lohidaleft[.]com - HTTPS/SSL/TLS traffic from Zeus Panda Banker
- port 443 - google[.]com - connectivity check caused by Zeus Panda Banker
FILE HASHES
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 4074ae1af5d6c514e895cdc9ba844dffc5e58cb13ce2665ed1a79a63bb1f937e
File size: 230,912 bytes
File name: invoice_169842.doc [any six random digits for the numbers]
File description: Word document with macro for Hancitor
- SHA256 hash: 5aa76c94248a80b7e6a17d027d5c5b51d709b6b9eac652c6a548a929507ce00f
File size: 180,224 bytes
File location: C:\Users\[username]\AppData\Local\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
Click here to return to the main page.