2018-03-14 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-03-14-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 418 kB (417,587 bytes)
- 2018-03-14-Hancitor-infection-with-Zeus-Panda-Banker.pcap (648,394 bytes)
- Zip archive of the emails: 2018-03-14-Hancitor-malspam-24-examples.txt.zip 5.7 kB (5,664 bytes)
- 2018-03-14-Hancitor-malspam-24-examples.txt (124,519 bytes)
- Zip archive of the malware: 2018-03-14-malware-from-Hancitor-infection.zip 265 kB (265,006 bytes)
- 2018-03-14-Hancitor-maldoc-invoice_353492zip.doc (279,040 bytes)
- 2018-03-14-Zeus-Panda-Banker.exe (193,536 bytes)
NOTES:
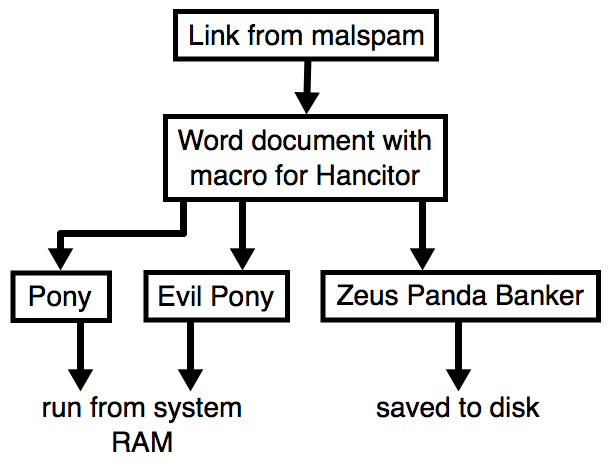
- As usual, for the 3 follow-up downloads, we're still seeing Pony, Evil Pony (both resident in memory), and Zeus Panda Banker (saved to disk).
- The block list contains additional post-infection URLs originally reported by @James_inthe_box reported on a Pastebin link here.
- My thanks to everyone who keeps an eye on this malspam and reports about it near-real-time on Twitter, and to those who've emailed me directly.
Shown above: Flow chart for a typical Hancitor malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- argentstrim[.]com
- budgetsignsplus[.]com
- mydaily5[.]com
- mysatya[.]com
- satyablog[.]com
- satyastore[.]com
- subeinc[.]com
- subeinc[.]net
- tailormadeduds[.]com
- duketofrob[.]com
- rithesforhep[.]ru
- witlyrenco[.]ru
- hxxp[:]//completestreetsathens[.]com/wp-content/plugins/contact-bank/lib/1
- hxxp[:]//completestreetsathens[.]com/wp-content/plugins/contact-bank/lib/2
- hxxp[:]//completestreetsathens[.]com/wp-content/plugins/contact-bank/lib/3
- hxxp[:]//ibesthoteldeals[.]eu/wp-content/plugins/Auto-Tube-Pro/1
- hxxp[:]//ibesthoteldeals[.]eu/wp-content/plugins/Auto-Tube-Pro/2
- hxxp[:]//ibesthoteldeals[.]eu/wp-content/plugins/Auto-Tube-Pro/3
- hxxp[:]//onlineprofitscoach[.]com/wp-content/plugins/social-count-plus/includes/1
- hxxp[:]//onlineprofitscoach[.]com/wp-content/plugins/social-count-plus/includes/2
- hxxp[:]//onlineprofitscoach[.]com/wp-content/plugins/social-count-plus/includes/3
- hxxp[:]//streetfoodandtraveltvindia[.]com/wp-content/themes/twentyfifteen/1
- hxxp[:]//streetfoodandtraveltvindia[.]com/wp-content/themes/twentyfifteen/2
- hxxp[:]//streetfoodandtraveltvindia[.]com/wp-content/themes/twentyfifteen/3
- hxxp[:]//winecountryuncorked[.]com/wp-content/themes/twentythirteen/inc/1
- hxxp[:]//winecountryuncorked[.]com/wp-content/themes/twentythirteen/inc/2
- hxxp[:]//winecountryuncorked[.]com/wp-content/themes/twentythirteen/inc/3
- hattalbutla[.]com
EMAILS
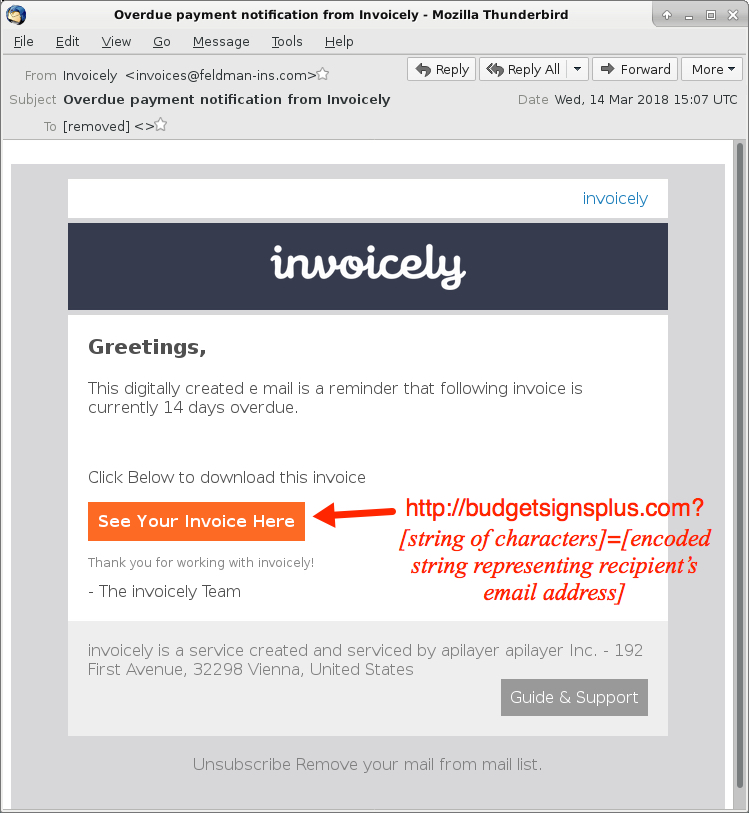
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2018-03-14 as early as 15:02 UTC through at least 18:18 UTC
- Received: from ([12.169.83[.]217])
- Received: from ([66.215.148[.]128])
- Received: from feldman-ins[.]com ([12.35.89[.]31])
- Received: from feldman-ins[.]com ([23.30.139[.]233])
- Received: from feldman-ins[.]com ([24.220.115[.]230])
- Received: from feldman-ins[.]com ([50.234.191[.]210])
- Received: from feldman-ins[.]com ([50.240.107[.]145])
- Received: from feldman-ins[.]com ([64.185.14[.]2])
- Received: from feldman-ins[.]com ([65.29.83[.]105])
- Received: from feldman-ins[.]com ([66.193.155[.]98])
- Received: from feldman-ins[.]com ([67.21.156[.]196])
- Received: from feldman-ins[.]com ([69.92.125[.]210])
- Received: from feldman-ins[.]com ([72.24.104[.]186])
- Received: from feldman-ins[.]com ([74.84.255[.]112])
- Received: from feldman-ins[.]com ([74.142.47[.]186])
- Received: from feldman-ins[.]com ([96.86.244[.]57])
- Received: from feldman-ins[.]com ([146.115.63[.]226])
- Received: from feldman-ins[.]com ([166.177.122[.]6])
- Received: from feldman-ins[.]com ([173.164.170[.]197])
- Received: from feldman-ins[.]com ([173.209.154[.]162])
- Received: from feldman-ins[.]com ([173.219.91[.]210])
- Received: from feldman-ins[.]com ([184.188.97[.]84])
- Received: from feldman-ins[.]com ([205.182.135[.]63])
- Received: from feldman-ins[.]com ([208.253.84[.]210])
- From: "Invoicely " <invoices@feldman-ins[.]com>
- From: "Invoicely Inc." <invoices@feldman-ins[.]com>
- From: "Invoicely Services" <invoices@feldman-ins[.]com>
- From: "Invoicely ServicesInc." <invoices@feldman-ins[.]com>
- Subject: Overdue payment notice from Invoicely
- Subject: Overdue payment notification from Invoicely
- Subject: Past due payment notice from Invoicely
- Subject: Past due payment notification from Invoicely
- Subject: Past-due payment notice from Invoicely
- Subject: Past-due payment notification from Invoicely

Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
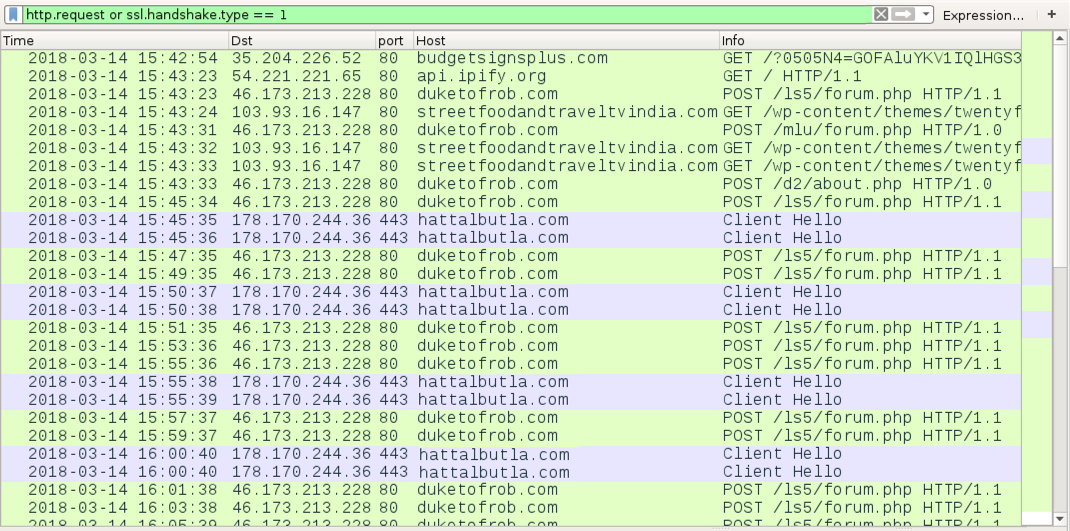
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS FOR THE WORD DOCUMENT:
- hxxp[:]//argentstrim[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//budgetsignsplus[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//mydaily5[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//mysatya[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//satyablog[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//satyastore[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//subeinc[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//subeinc[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//tailormadeduds[.]com?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 35.204.226[.]52 port 80 - budgetsignsplus[.]com - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify[.]org - GET /
- 46.173.213[.]228 port 80 - duketofrob[.]com - POST /ls5/forum.php
- 46.173.213[.]228 port 80 - duketofrob[.]com - POST /mlu/forum.php
- 46.173.213[.]228 port 80 - duketofrob[.]com - POST /d2/about.php
- 103.93.16[.]147 port 80 - streetfoodandtraveltvindia[.]com - GET /wp-content/themes/twentyfifteen/1
- 103.93.16[.]147 port 80 - streetfoodandtraveltvindia[.]com - GET /wp-content/themes/twentyfifteen/2
- 103.93.16[.]147 port 80 - streetfoodandtraveltvindia[.]com - GET /wp-content/themes/twentyfifteen/3
- 178.170.244[.]36 port 443 - hattalbutla[.]com - HTTPS/SSL/TLS traffic from Zeus Panda Banker
FILE HASHES
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: af290434ffa9a677133952b2d2622eabd7b274f545fc662f31dcfa0164d9f9de
File size: 279,040 bytes
File name: invoice_353492.doc [any six random digits for the numbers]
File description: Word document with macro for Hancitor
- SHA256 hash: 5782c7ade207fd4415c35bd1e98bad7c3fcaef206fa60f142b8d1062e7103670
File size: 193,536 bytes
File location: C:\Users\[username]\AppData\Local\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
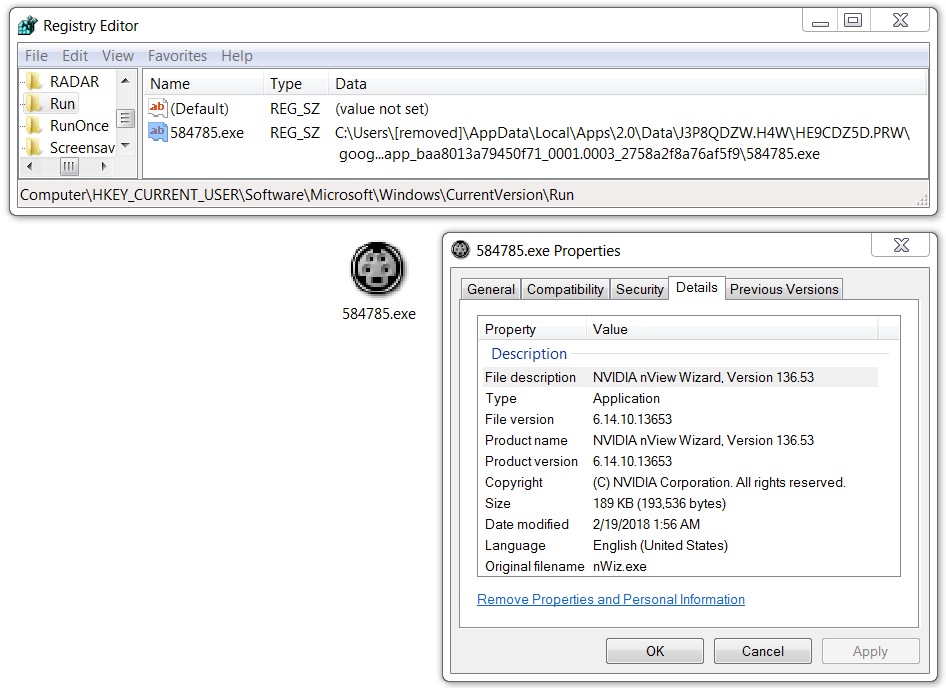
Shown above: Zeus Panda Banker persistent on the infected Windows host.
Click here to return to the main page.