2018-03-16 - GANDCRAB RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-03-16-GandCrab-malspam-tracker.csv.zip 1.0 kB (913 bytes)
- 2018-03-16-GandCrab-emails-and-malware.zip 387 kB (386,816 bytes)
- 2018-03-16-GandCrab-infection-traffic.pcap.zip 188 kB (188,371 bytes)
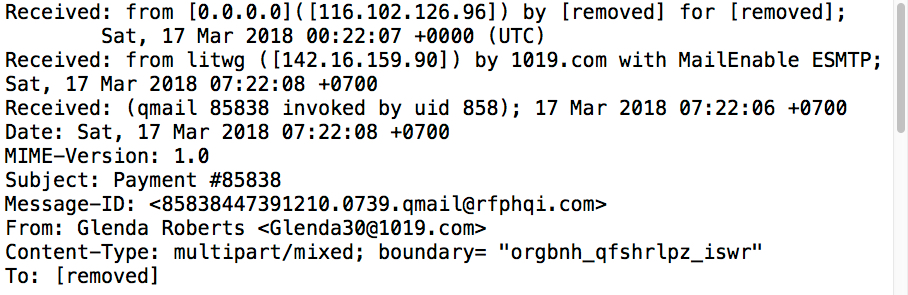
Shown above: Email headers from a message I found right before drafting this blog post.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URL and domain:
- hxxp[:]//92.63.197[.]59/r.exe?VpTgr
- malwarehunterteam[.]bit
EMAILS
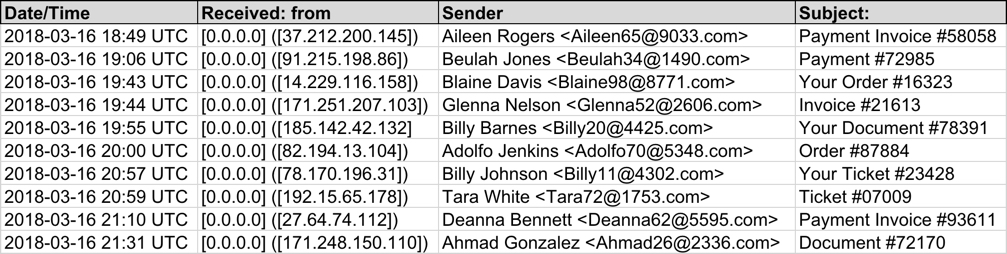
Shown above: Screenshot from the spreadsheet tracker (1 of 2).
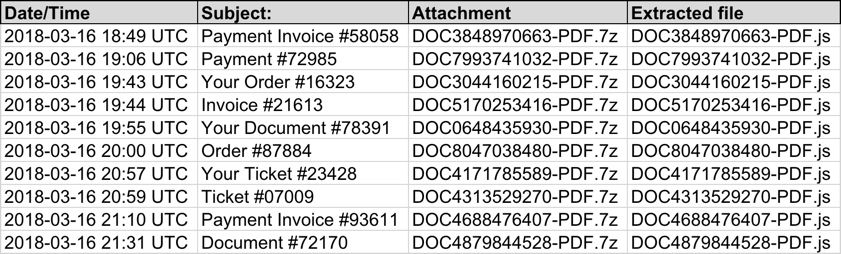
Shown above: Screenshot from the spreadsheet tracker (2 of 2).
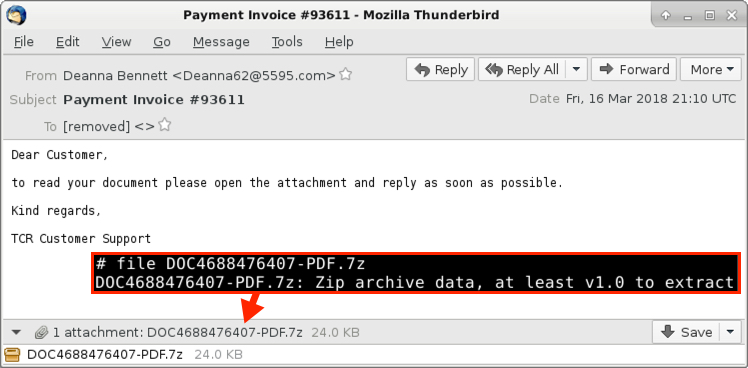
Shown above: Screenshot from one of the emails.
DATA FROM 10 EMAIL SAMPLES:
- Date/Time: Friday 2018-03-16 as early as 18:49 UTC through at least 21:31 UTC
- Received: from [0.0.0[.]0] ([14.229.116[.]158])
- Received: from [0.0.0[.]0] ([27.64.74[.]112])
- Received: from [0.0.0[.]0] ([37.212.200[.]145])
- Received: from [0.0.0[.]0] ([78.170.196[.]31])
- Received: from [0.0.0[.]0] ([82.194.13[.]104])
- Received: from [0.0.0[.]0] ([91.215.198[.]86])
- Received: from [0.0.0[.]0] ([171.248.150[.]110])
- Received: from [0.0.0[.]0] ([171.251.207[.]103])
- Received: from [0.0.0[.]0] ([185.142.42[.]132]
- Received: from [0.0.0[.]0] ([192.15.65[.]178])
- From: Adolfo Jenkins <Adolfo70@5348[.]com>
- From: Ahmad Gonzalez <Ahmad26@2336[.]com>
- From: Aileen Rogers <Aileen65@9033[.]com>
- From: Beulah Jones <Beulah34@1490[.]com>
- From: Billy Barnes <Billy20@4425[.]com>
- From: Billy Johnson <Billy11@4302[.]com>
- From: Blaine Davis <Blaine98@8771[.]com>
- From: Deanna Bennett <Deanna62@5595[.]com>
- From: Glenna Nelson <Glenna52@2606[.]com>
- From: Tara White <Tara72@1753[.]com>
- Subject: Document #72170
- Subject: Invoice #21613
- Subject: Order #87884
- Subject: Payment #72985
- Subject: Payment Invoice #58058
- Subject: Payment Invoice #93611
- Subject: Ticket #07009
- Subject: Your Document #78391
- Subject: Your Order #16323
- Subject: Your Ticket #23428
MALWARE
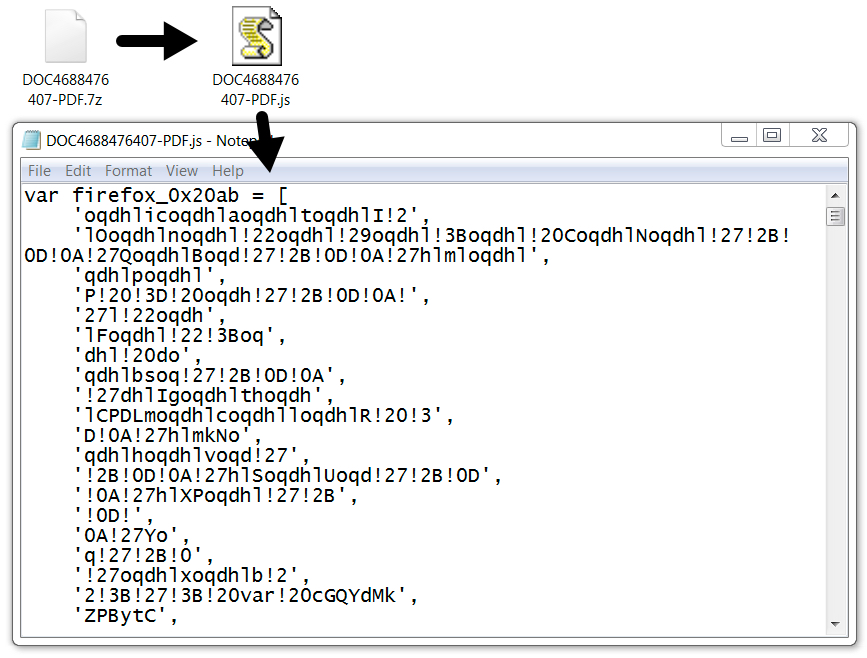
Shown above: JavaScript file extracted from one of the zip attachments.
EMAIL ATTACHMENTS (ALL ZIP ARCHIVES WITH .7Z FILE EXTENSIONS):
- 187416b1d8b89e5d87ecfa40dec4b1ff4565ca30a1c8dad64678b077eb13cd78 - DOC0648435930-PDF.7z
- ba0396b15696017be766331a6141b5f6e4993d4bfe51b348f29662684a8c2305 - DOC3044160215-PDF.7z
- d4c19a3c2796474f6b52fa1ee61b33c5f4eddd4d191787647b285d9c841a7018 - DOC3848970663-PDF.7z
- 28697d239b348373f6bcdc4c555d2d04edc463eb15a3422dbfbae7ae6be2fd05 - DOC4171785589-PDF.7z
- 45e5ddd3481c33fb89bb3a08fdc7ce9dce8c2f2d27bbb4741e10e96963331103 - DOC4313529270-PDF.7z
- 98c6f0e0e0bfae8ae09c36ebe7f0c1761242888bf695b2a06ed11f20747673d3 - DOC4688476407-PDF.7z
- b7df178da5a02b676666b62ceff7a457106ad8b4b77f2cd71fcc54bae8737598 - DOC4879844528-PDF.7z
- bf02fa2e63121ef9b87153bc34f4a4871797af9329fb3d27eaccca7d928c36d9 - DOC5170253416-PDF.7z
- 75aacbf2d757259e03ea87fd535f9565c351696c781ce159bf3ff036d53c8b3e - DOC7993741032-PDF.7z
- 44b32236584e9cee5361ca6e23467f793a548b664c631609504d58db2f08a901 - DOC8047038480-PDF.7z
JAVASCRIPT FILE EXTRACTED FROM THE ZIP ATTACHMENTS (SAME FILE, DIFFERENT NAMES):
- 84af0e532258e11129e860b8bc68b5a8d7933f044185bdceecf4c785b5fb1759 - DOC0648435930-PDF.js
- 84af0e532258e11129e860b8bc68b5a8d7933f044185bdceecf4c785b5fb1759 - DOC3044160215-PDF.js
- 84af0e532258e11129e860b8bc68b5a8d7933f044185bdceecf4c785b5fb1759 - DOC3848970663-PDF.js
- 84af0e532258e11129e860b8bc68b5a8d7933f044185bdceecf4c785b5fb1759 - DOC4171785589-PDF.js
- 84af0e532258e11129e860b8bc68b5a8d7933f044185bdceecf4c785b5fb1759 - DOC4313529270-PDF.js
- 84af0e532258e11129e860b8bc68b5a8d7933f044185bdceecf4c785b5fb1759 - DOC4688476407-PDF.js
- 84af0e532258e11129e860b8bc68b5a8d7933f044185bdceecf4c785b5fb1759 - DOC4879844528-PDF.js
- 84af0e532258e11129e860b8bc68b5a8d7933f044185bdceecf4c785b5fb1759 - DOC5170253416-PDF.js
- 84af0e532258e11129e860b8bc68b5a8d7933f044185bdceecf4c785b5fb1759 - DOC7993741032-PDF.js
- 84af0e532258e11129e860b8bc68b5a8d7933f044185bdceecf4c785b5fb1759 - DOC8047038480-PDF.js
GANDCRAB RANSOMWARE BINARY RETRIEVED BY THE .JS FILE:
- SHA256 hash: 9282ffd0f7aef39febc84f33a3090898e2fae6236cae7465a21ca58978d81b86
File size: 265,224 bytes
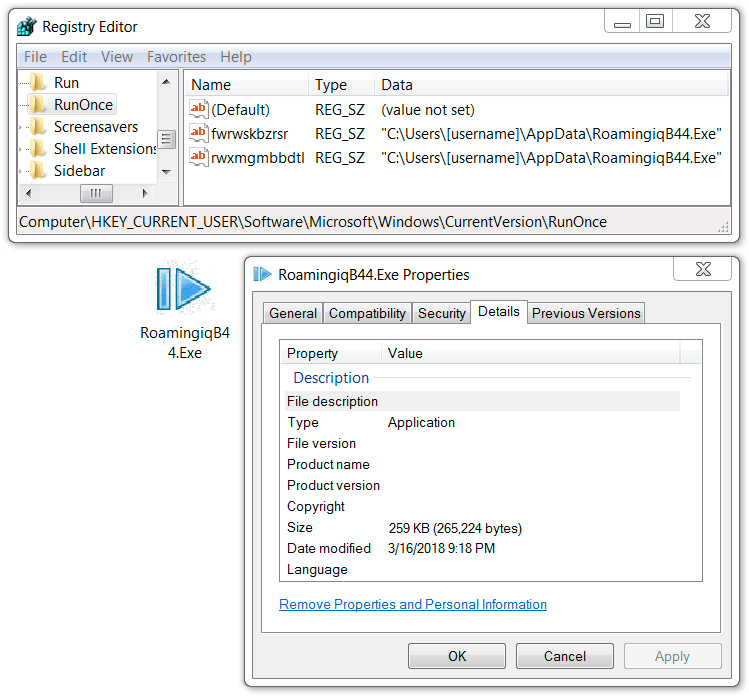
File location: C:\Users\[username]\AppData\RoamingiqB44.Exe
Shown above: GandCrab ransomware persistent on an infected Windows host.
TRAFFIC
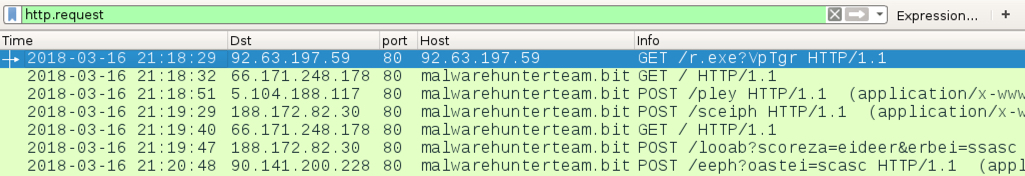
Shown above: Traffic from an infection filtered in Wireshark.
URL FROM THE EXTRACTED .JS FILES TO DOWNLOAD THE GANDCRAB RANSOMWARE EXECUTABLE:
- 92.63.197[.]59 port 80 - 92.63.197[.]59 - GET /r.exe?VpTgr
GANDCRAB RANSOMWARE INFECTION TRAFFIC:
- 66.171.248[.]178 port 80 - malwarehunterteam[.]bit - GET /
- 5.104.188[.]117 port 80 - malwarehunterteam[.]bit - POST /pley
- 188.172.82[.]30 port 80 - malwarehunterteam[.]bit - POST /sceiph
- 66.171.248[.]178 port 80 - malwarehunterteam[.]bit - GET /
- 188.172.82[.]30 port 80 - malwarehunterteam[.]bit - POST /looab?scoreza=eideer&erbei=ssasc
- 90.141.200[.]228 port 80 - malwarehunterteam[.]bit - POST /eeph?oastei=scasc
IMAGES
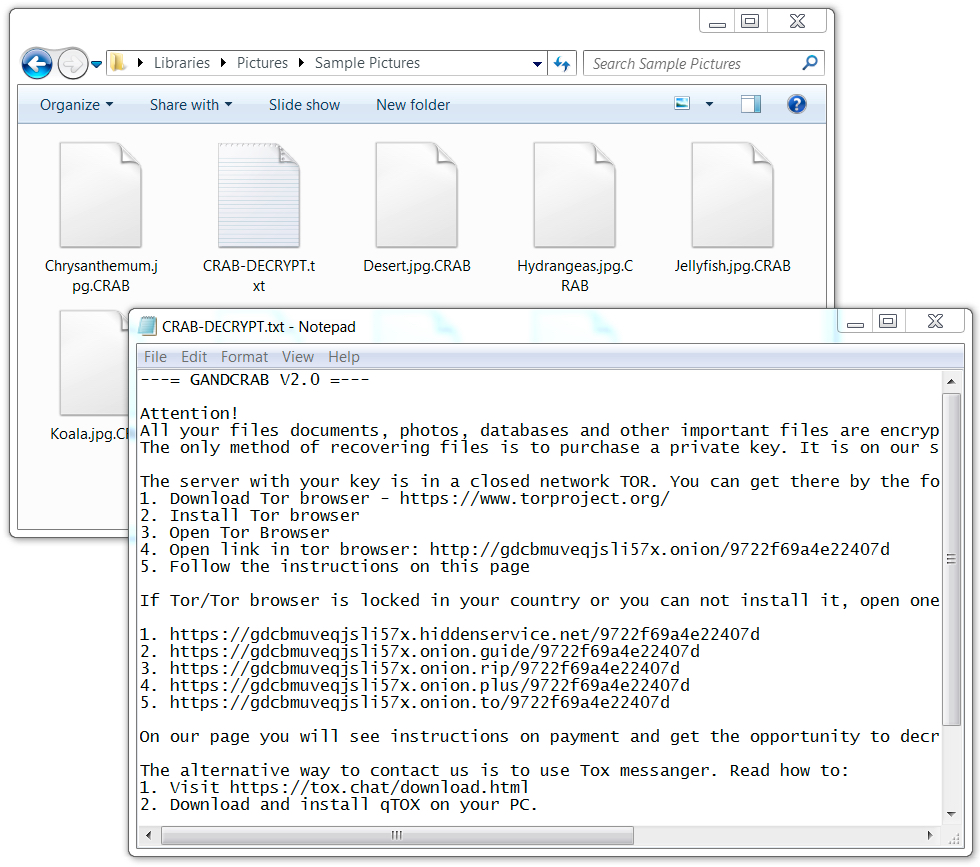
Shown above: Encrypted files on an infected Windows host.
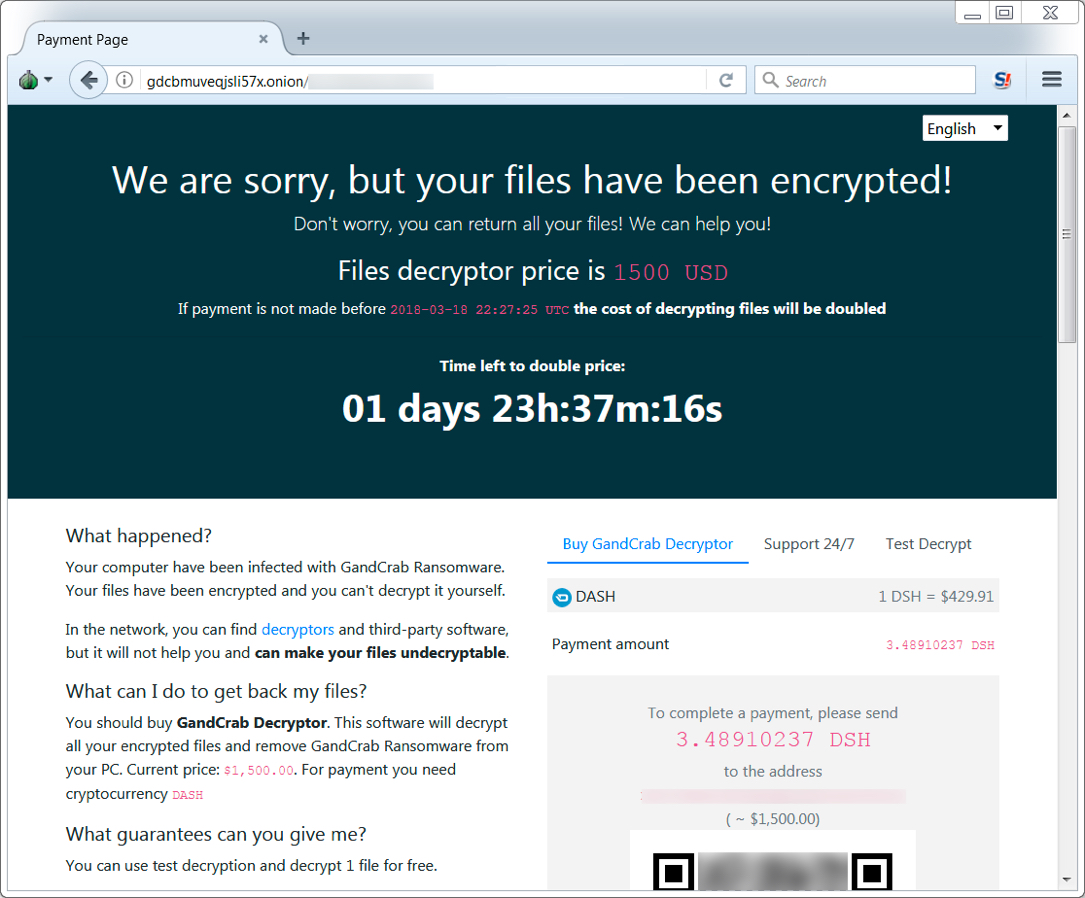
Shown above: GandCrab decryptor aksed me for 1,500 US dollars.
Click here to return to the main page.