2018-03-21 - EMOTET ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the spreadsheet tracker: 2018-03-21-Emotet-malspam-tracker-10-examples.csv.zip 1.4 kB (1,408 bytes)
- 2018-03-21-Emotet-malspam-tracker-10-examples.csv (2,138 bytes)
- Zip archive of 10 email examples: 2018-03-21-Emotet-malspam-10-examples.zip 14.6 kB (14,551 bytes)
- 2018-03-21-Emotet-malspam-0736-UTC.eml (2,487 bytes)
- 2018-03-21-Emotet-malspam-0819-UTC.eml (2,053 bytes)
- 2018-03-21-Emotet-malspam-1015-UTC.eml (1,818 bytes)
- 2018-03-21-Emotet-malspam-1018-UTC.eml (2,190 bytes)
- 2018-03-21-Emotet-malspam-1040-UTC.eml (1,085 bytes)
- 2018-03-21-Emotet-malspam-1233-UTC.eml (1,813 bytes)
- 2018-03-21-Emotet-malspam-1313-UTC.eml (2,238 bytes)
- 2018-03-21-Emotet-malspam-1359-UTC.eml (1,986 bytes)
- 2018-03-21-Emotet-malspam-1435-UTC.eml (2,053 bytes)
- 2018-03-21-Emotet-malspam-1522-UTC.eml (1,972 bytes)
- Zip archive of the infection traffic: 2018-03-21-Emotet-infection-traffic.pcap.zip 795 kB (794,736 bytes)
- 2018-03-21-Emotet-infection-traffic.pcap (969,538 bytes)
- Zip archive of the associated malware: 2018-03-21-malware-from-Emotet-infection.zip 208 kB (207,529 bytes)
- PivotMonet.exe (139,264 bytes)
- Tracking 5230576-PG-ASNX.doc (214,016 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- hxxp[:]//icetest.gectcr[.]ac[.]in/Mar-21-10-35-45/View/
- hxxp[:]//nisargseafood[.]com/Mar-21-10-00-51/Express-Domestic/
- hxxp[:]//piripiriveiculos[.]com/galerias/Past-Due-Invoice/
- hxxp[:]//www.angelhunter[.]club/Past-Due-Invoices/
- hxxp[:]//www.grandemacelleriaegidio[.]com/Information/
- hxxp[:]//www.i99point[.]com/wp-content/Past-Due-Invoices/
- hxxp[:]//www.parquenaturaldelmontgo[.]com/Rechnung/
- hxxp[:]//www.studiodilauro[.]com/RECHNUNG-24925/
- hxxp[:]//www.tgpitalia[.]com/Mar-21-08-39-37/Quantum-View/
- hxxp[:]//www.visit-cape-verde[.]com/Mar-21-05-59-20/Ship-Notification/
- hxxp[:]//aeksingolot[.]com/Z86ja4Q/
- hxxp[:]//mplus-sr[.]jp/029I80m/
- hxxp[:]//www.bharanihomoeoclinic[.]com/k8Ig/
- hxxp[:]//www.breakfasttravel[.]com/F3enp7s/
- hxxp[:]//www.cchc[.]org[.]pe/YTma/
EMAILS
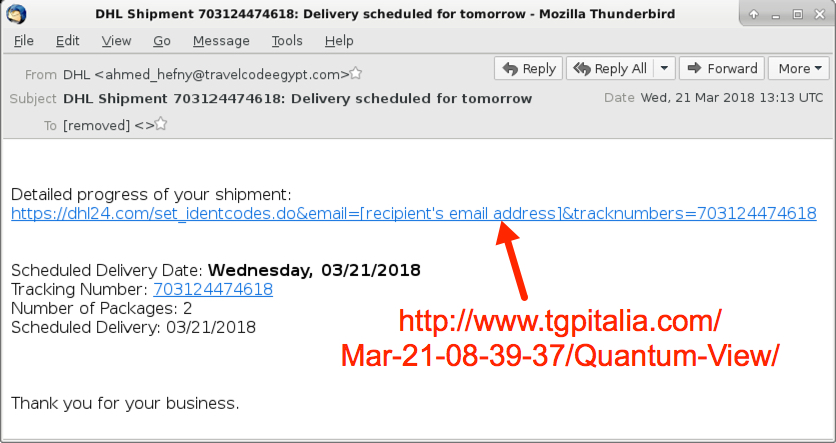
Shown above: Screenshot from one of the emails.
10 EMAIL SAMPLES:
- (Read: Date/Time - Sending address - Subject line)
- 2018-03-21 07:36 UTC - "Kundenservice Rechnungonline Telekom" <panya_amphone@student.friends[.]edu> - RechnungOnline Marz 2018 (Buchungs-Kto.: 4891167142)
- 2018-03-21 08:19 UTC - "Telekom Deutschland GmbH {NoReply}" <thomasj@elitetherapycenters[.]com> - RechnungOnline Marz 2018 - Buchungsaccount: 1003895617
- 2018-03-21 10:15 UTC - <terrence_mckinnon@student.friends[.]edu> - Scan MB - 443-TFP3456
- 2018-03-21 10:18 UTC - "UPS US" <blanton@insiteprops[.]com> - Tracking Number 4FT88977984781873
- 2018-03-21 10:40 UTC - <kssglobal@europe[.]com> - Past Due Invoices
- 2018-03-21 12:33 UTC - <vuqar.qurbanov@ascca[.]gov[.]az> - Outstanding Invoices
- 2018-03-21 13:13 UTC - "DHL" <ahmed_hefny@travelcodeegypt[.]com> - DHL Shipment 703124474618: Delivery scheduled for tomorrow
- 2018-03-21 13:59 UTC - "[fname lname]" <collins@nfcafrica[.]com> - Invoice for y/a 03/21/2018
- 2018-03-21 14:35 UTC - "UPS" <kellir@eccobella[.]com> - UPS Express Domestic
- 2018-03-21 15:22 UTC - "DHL Express" <rt@tinchband[.]com> - DHL Ship Notification, Tracking Number 619697968601
URLS FROM THE EMAILS TO DOWNLOAD THE INITIAL WORD DOCUMENT:
- hxxp[:]//icetest.gectcr[.]ac[.]in/Mar-21-10-35-45/View/
- hxxp[:]//nisargseafood[.]com/Mar-21-10-00-51/Express-Domestic/
- hxxp[:]//piripiriveiculos[.]com/galerias/Past-Due-Invoice/
- hxxp[:]//www.angelhunter[.]club/Past-Due-Invoices/
- hxxp[:]//www.grandemacelleriaegidio[.]com/Information/
- hxxp[:]//www.i99point[.]com/wp-content/Past-Due-Invoices/
- hxxp[:]//www.parquenaturaldelmontgo[.]com/Rechnung/
- hxxp[:]//www.studiodilauro[.]com/RECHNUNG-24925/
- hxxp[:]//www.tgpitalia[.]com/Mar-21-08-39-37/Quantum-View/
- hxxp[:]//www.visit-cape-verde[.]com/Mar-21-05-59-20/Ship-Notification/
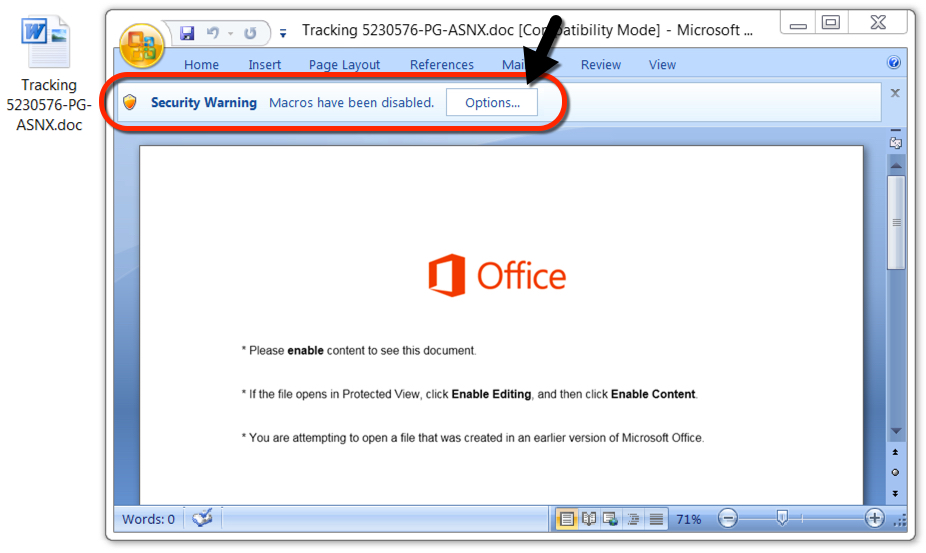
Shown above: Word document downloaded from one of the email links.
TRAFFIC
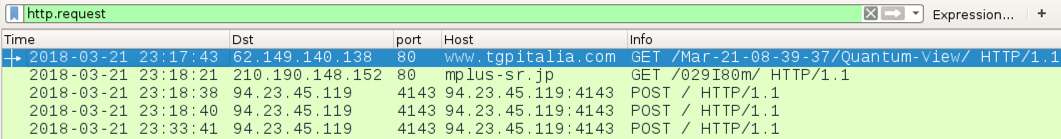
Shown above: Traffic from an infection filtered in Wireshark.
URLS FROM THE WORD MACRO TO DOWNLOAD EMOTET (FROM ANY.RUN ANALYSIS):
- hxxp[:]//aeksingolot[.]com/Z86ja4Q/
- hxxp[:]//mplus-sr[.]jp/029I80m/
- hxxp[:]//www.bharanihomoeoclinic[.]com/k8Ig/
- hxxp[:]//www.breakfasttravel[.]com/F3enp7s/
- hxxp[:]//www.cchc[.]org[.]pe/YTma/
EMOTET BINARY ATTEMPTED TCP CONNECTIONS (FROM REVERSE.IT ANALYSIS):
- 2.20.193[.]233 port 80
- 88.221.182[.]110 port 80
- 94.23.45[.]119 port 4143
- 92.122.122[.]136 port 80
- 92.122.122[.]155 port 80
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 62.149.140[.]138 port 80 - www.tgpitalia[.]com - GET /Mar-21-08-39-37/Quantum-View/
- 210.190.148[.]152 port 80 - mplus-sr[.]jp - GET /029I80m/
- 94.23.45[.]119 port 4143 - 94.23.45[.]119:4143 - POST /
FILE HASHES
DOWNLOADED WORD DOCUMENT:
- SHA256 hash: fa33ed5509519fabc4126386f289e58a8b863358e8173991ad857d3745bc8aa6
File size: 214,016 bytes
File name: Tracking 5230576-PG-ASNX.doc
File description: Word document with malicious macro to download/install Emotet
EMOTET BINARY:
- SHA256 hash: a0fb30c1542dee5eb3889233cb8fed4a9e30d6900012b27379c7495ce7529148
File size: 139,264 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\PivotMonet.exe
File description: Emotet malware binary
IMAGES
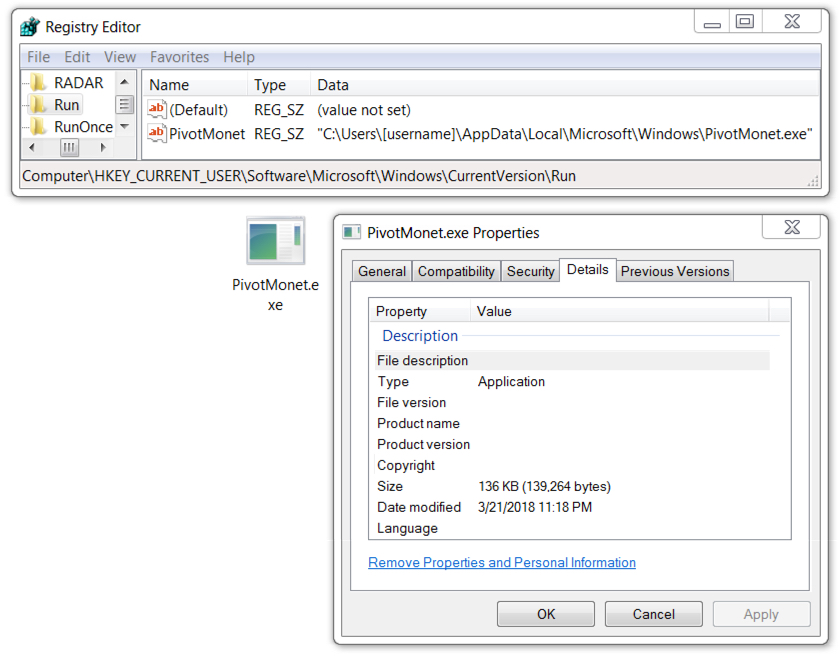
Shown above: Emotet made persistent on my infected Windows host.
Click here to return to the main page.
