2018-03-22 - TRICKBOT ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of 5 email examples: 2018-03-22-Trickbot-malspam-5-examples.zip 256 kB (255,919 bytes)
- 2018-03-22-Trickbot-malspam-120834-UTC.eml (144,137 bytes)
- 2018-03-22-Trickbot-malspam-120844a-UTC.eml (146,448 bytes)
- 2018-03-22-Trickbot-malspam-120844b-UTC.eml (146,454 bytes)
- 2018-03-22-Trickbot-malspam-120845a-UTC.eml (146,450 bytes)
- 2018-03-22-Trickbot-malspam-120845b-UTC.eml (146,460 bytes)
- Zip archive of the infection traffic: 2018-03-22-Trickbot-infection-traffic-2-pcaps.zip 6.4 MB (6,369,820 bytes)
- 2018-03-22-Trickbot-infection-traffic.pcap (2,622,359 bytes)
- 2018-03-22-sanitized-traffic-from-Reverse.it-analysis-of-Word-document.pcap (4,597,230 bytes)
- Zip archive of the malware: 2018-03-22-malware-from-Trickbot-infection.zip 243 kB (242,649 bytes)
- 2018-03-22-Trickbot-artifact-group_tag.txt (16 bytes)
- 2018-03-22-Trickbot-artifact-rhknve.bat.txt (328 bytes)
- 2018-03-22-Trickbot-binary-Yknxohk.exe (348,160 bytes)
- 2018-03-22-Trickbot-scheduled-task-MsNetMonitor.xml.txt (3,736 bytes)
- 2018-03-22-maldoc-with-macro-to-install-Trickbot-9S659EHDCSI72649DS.doc (80,896 bytes)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- hxxp[:]//ebrotasa[.]com/morbery.png
- hxxp[:]//pcstore[.]com[.]ve/morbery.png
- hxxp[:]//185.17.121[.]49/table.png
- hxxp[:]//185.17.121[.]49/toler.png
DATA FROM 5 EMAIL SAMPLES:
- Date/Time: Thursday 2018-03-22 as early as 12:08:34 through at least 12:08:45 UTC
- Received: from docusignemail[.]com ([162.13.147[.]46])
- Received: from docusignemail[.]com ([162.13.147[.]61])
- Received: from docusignmail[.]com (docusignmail[.]com [5.79.31[.]5])
- Received: from docusignmail[.]com (docusignmail[.]com [5.79.31[.]6])
- Received: from docusignmail[.]com ([162.13.147[.]65])
- From: "DocuSign" <no-reply@docusignemail[.]com>
- From: "DocuSign" <no-reply@docusignmail[.]com>
- Subject: You have received a secure document
- Attachment name: 9S659EHDCSI72649DS.doc
TRAFFIC
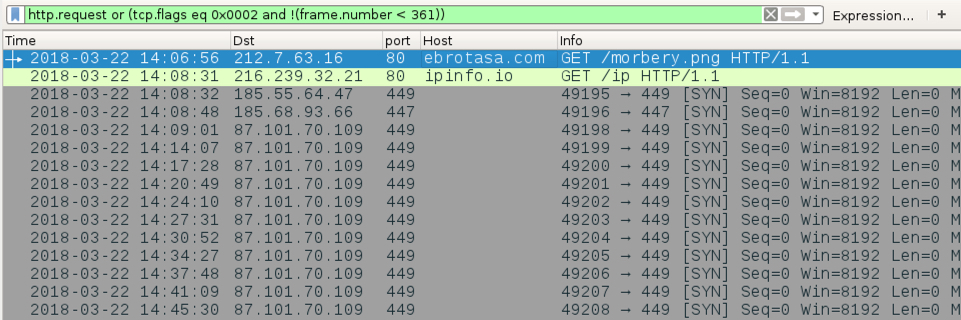
Shown above: Traffic from an infection filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 212.7.63[.]16 port 80 - ebrotasa[.]com - GET /morbery.png
- port 80 - ipinfo[.]io - GET /ip
- 185.55.64[.]47 port 449 - encrypted post-infection traffic caused by Trickbot
- 185.68.93[.]66 port 447 - encrypted post-infection traffic caused by Trickbot
- 87.101.70[.]109 port 449 - encrypted post-infection traffic caused by Trickbot
ADDITIONAL TRAFFIC FROM REVERSE.IT ANALYSIS OF THE WORD DOCUMENT (LINK):
- port 80 - wtfismyip[.]com - GET /text
- 212.14.51[.]56 port 443 - encrypted post-infection traffic caused by Trickbot
- 195.123.217[.]207 port 443 - encrypted post-infection traffic caused by Trickbot
- 185.17.121[.]49 port 80 - 185.17.121[.]49 - GET /table.png
- 185.17.121[.]49 port 80 - 185.17.121[.]49 - GET /toler.png
FILE HASHES
DOWNLOADED WORD DOCUMENT:
- SHA256 hash: 10281a188a26dbb10562bdc6f5467abad4b0e7fe73672b48a11fdd55819f81f3
File size: 80,896 bytes
File name: 9S659EHDCSI72649DS.doc
File description: Word document with malicious macro to download/install Trickbot
EMOTET BINARY:
- SHA256 hash: 1ea818b42112608931b01892a9b24d4120a8f96140b69531305ac0d7135eb3a2
File size: 348,160 bytes
File location: C:\Users\[username]\AppData\Local\Temp\Yknxohk.exe
File location: C:\Users\[username]\AppData\Roaming\TeamViewer\Yknxohk.exe
File description: Trickbot malware binary
Click here to return to the main page.
