2018-03-26 - SIGMA RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the infection traffic: 2018-03-26-Sigma-ransomware-infection-traffic.pcap.zip 11.8 MB (11,754,337 bytes)
- 2018-03-26-Sigma-ransomware-infection-traffic.pcap (12,507,887 bytes)
- Zip archive of associated Word docs with macros for Sigma ransomware: 2018-03-26-Word-docs-pushing-Sigma-ransomware.zip 420 kB (420,147 bytes)
- 63-password-removed.doc (27,802 bytes)
- 63.doc (37,376 bytes)
- 82.doc (37,376 bytes)
- 89.doc (37,376 bytes)
- 144.doc (37,376 bytes)
- 175.doc (37,376 bytes)
- 180.doc (37,376 bytes)
- 184.doc (37,376 bytes)
- 227.doc (37,376 bytes)
- 254.doc (37,376 bytes)
- 301.doc (37,376 bytes)
- 316.doc (37,376 bytes)
- 340.doc (37,376 bytes)
- 395.doc (37,376 bytes)
- 458.doc (37,376 bytes)
- 463.doc (37,376 bytes)
- 487.doc (37,376 bytes)
- Zip archive of the associated malware: 2018-03-26-artifacts-and-malware-from-Sigma-ransomware-infection.zip 3.5 MB (3,473,538 bytes)
- 2018-03-26-Sigma-ransomware-ReadMe.html (4,565 bytes)
- 2018-03-26-Sigma-ransomware-ReadMe.txt (1,969 bytes)
- 2018-03-26-Sigma-ransomware-initial-download-1-of-2-45.png-self-extracting-archive.exe (53,022 bytes)
- 2018-03-26-Sigma-ransomware-initial-download-2-of-2-icon.png.exe (3,456,974 bytes)
- 2018-03-26-malware-extracted-from-45.png-file-svchost.exe (122,880 bytes)
NOTES:
- This is based on information sent to me from someone who reads this blog.
- Unfortunately, I was unable to get a copy of the emails for today's malspam.
- Today's campaign is similar to what I reported earlier this month at: https://isc.sans.edu/forums/diary/Malspam+pushing+Sigma+ransomware/23443/
- This time, the password for all of the Word documents is: 5558
- Plenty of samples were submitted to VirusTotal, so I grabbed some for this blog post.
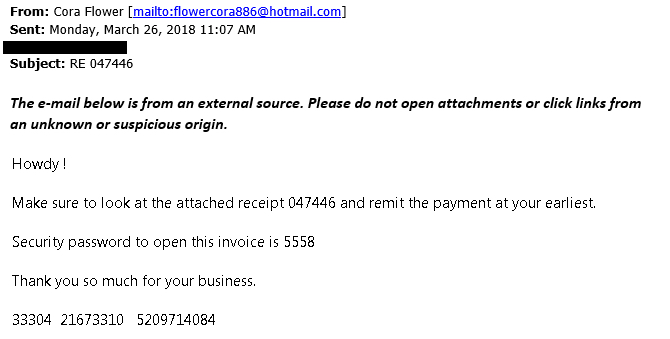
Shown above: Screenshot sent by the person who notified me of this malspam.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- hxxp[:]//185.121.139[.]229/~document/45.png
- hxxp[:]//185.121.139[.]229/~document/icon.png
- yowl2ugopitfzzwb[.]onion[.]link
- yowl2ugopitfzzwb[.]onion
EMAILS
EMAIL INFO:
- Date/Time: Monday, 2018-03-26 unknown time frame
- Received: from [various IP addresses]
- From: [random first and last name followed by 3 random digits]@hotmail[.]com - Spoofed address
- Subject: [various topics followed by 6 random digits]
EXAMPLES OF PASSWORD-PROTECTED WORD DOCUMENTS ASSOCIATED WITH THIS MALSPAM (ALL ARE 37,376 BYTES):
- 1e0d99b677189829a54a1d7d9bc6e380a275bb92a16d35330eb88f1d1dca49f8 - 63.doc
- cda7844049550b46a2b8e7352f8645910b4bb8bbe24df9d565746ff1b3619c71 - 82.doc
- 082c5a96d49dcead978d067c4cebfd2b2232181ae9d65162917e09b0f633a766 - 89.doc
- fd83df715755b5c454dd8ce11f0906d9c025d0f802fe4edd3d987f9e22754af5 - 144.doc
- e4eb08385e98050fa3d6c38d1c91a1cf5ea8cb0a032e2cd24a001743a8180a49 - 175.doc
- adeae5afd133efe3905c977889d799ac145423fe463bf40cb5211a36c65c75fc - 180.doc
- ab75d9f83499c86997dda1aeb2d6c5a1a68b57a4b8ae4b8efaa2cc16e32c006c - 184.doc
- d8efc2289508d9a6e81c09146652130aa6e215a9251a361587dd66b6b3197c74 - 227.doc
- 5ea1d1667ca5963cad5c20a9989adaf520b0ec21c2b27e89b806d92914746b98 - 254.doc
- e47434db908809d37cbb0c22baf6b0ac8c65f16a38e85e0140db439ce78a2c19 - 301.doc
- 0aa1ff490e398ca9bc16130e843da231f9289d2abb2303e3ddf9430d4b72b059 - 316.doc
- 58f652a7bd5f84ed95e4e5c0382acd05eb7a59d0b3cd35c4631a924d8035df8a - 340.doc
- e7e9375250e30f7a57f13b2553003f6b021d79488ba408170faadd3306b71bca - 395.doc
- 450c184787963e568916893774cf6226674aceac7048e72cd9a3dce30174043a - 458.doc
- 768e2e96a252be53bb550afa9e507a6c67d928a0cec58d3633e6fd894a1b0b57 - 463.doc
- bfb0970951e28653a58f863071c144f17e0fda32b1681f7e4af4d141ecf7d94e - 487.doc
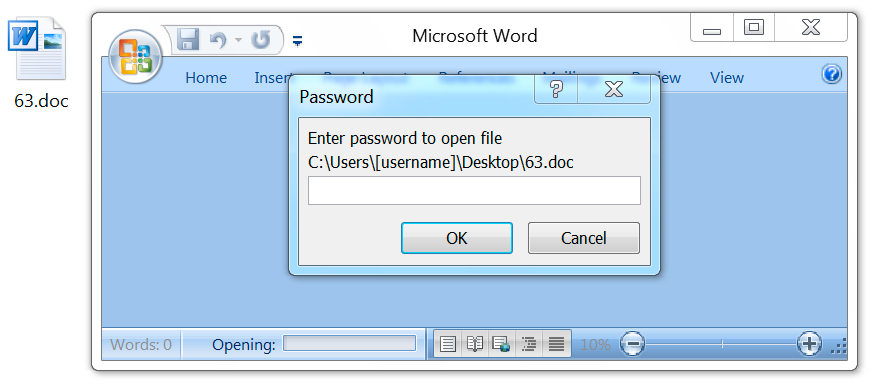
Shown above: Opening one of the associated Word documents from this malspam requests a password.
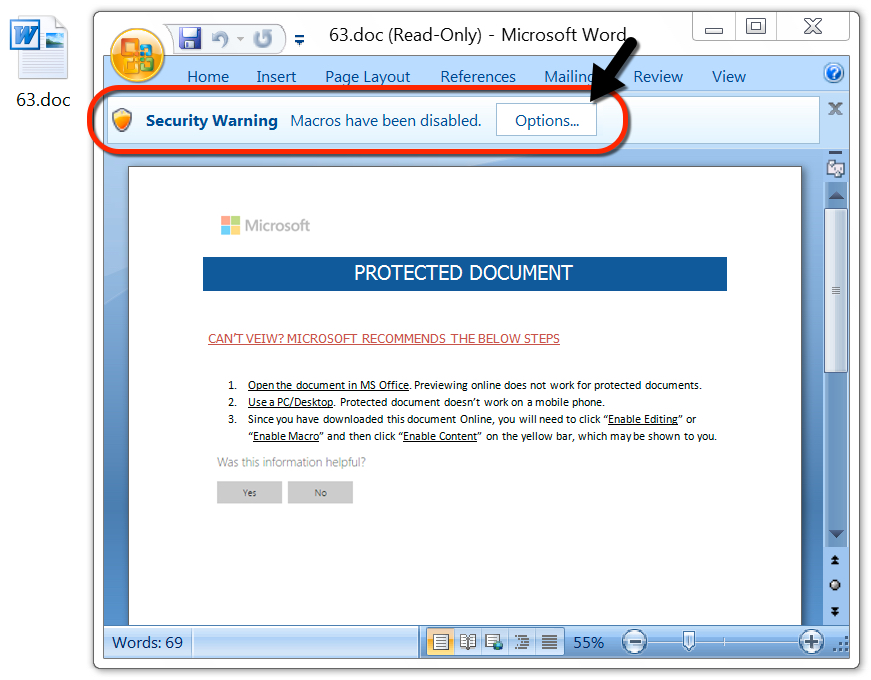
Shown above: After that, you're presented with a macro to enable.
TRAFFIC
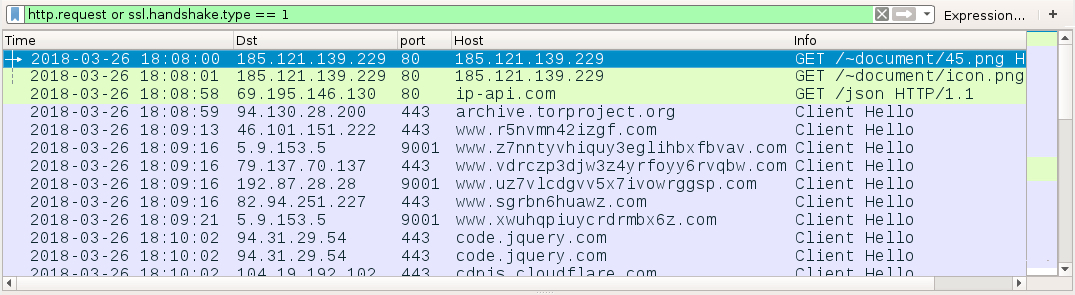
Shown above: Traffic from an infection filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 185.121.139[.]229 port 80 - 185.121.139[.]229 - GET/~document/45.png
- 185.121.139[.]229 port 80 - 185.121.139[.]229 - GET/~document/icon.png
- port 80 - in-api[.]com - GET /json (IP address check by the infected host
- port 443 - archive.torprogject[.]org - HTTPS/SSL/TLS traffic
- various IP addresses on various TCP ports - Tor traffic
TOR ADDRESSES FROM THE DECRYPTION INSTRUCTIONS (UNCHANGED FROM LAST TIME):
- yowl2ugopitfzzwb[.]onion[.]link
- yowl2ugopitfzzwb[.]onion
FILE HASHES
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 44dbc0977811db926a1880a71d259772d887570e171ff80c45439031f2b76f9f
File size: 53,022 bytes
File location: hxxp[:]//185.121.139[.]229/~document/45.png
File location: C:\Users\[username]\AppData\Local\Temp\svchost.exe
File description: Executable downloaded by the Word macro. It's a self-extracting archive.
- SHA256 hash: 20c90894d32c81f344b3dfaf6b55d48eb5b585c0f5ffe4ecf145d41db65e0507
File size: 122,880 bytes
File location: C:\Users\[username]\AppData\Local\Temp\RarSFX0\svchost.exe
File description: Binary from the above self-extracting archive.
- SHA256 hash: 32bcce37fce903996832ef92b79c2da0747c7d61a1a7d09b215960ad021d393c
File size: 345,6974 bytes
File location: hxxp[:]//185.121.139[.]229/~document/icon.png
File location: C:\Users\[username]\AppData\Roaming\Microsoft\[ransom ID string]\taskwgr.exe
File description: Another self-extracting archive, password-protected, contains tor components for the infected Windows host.
IMAGES
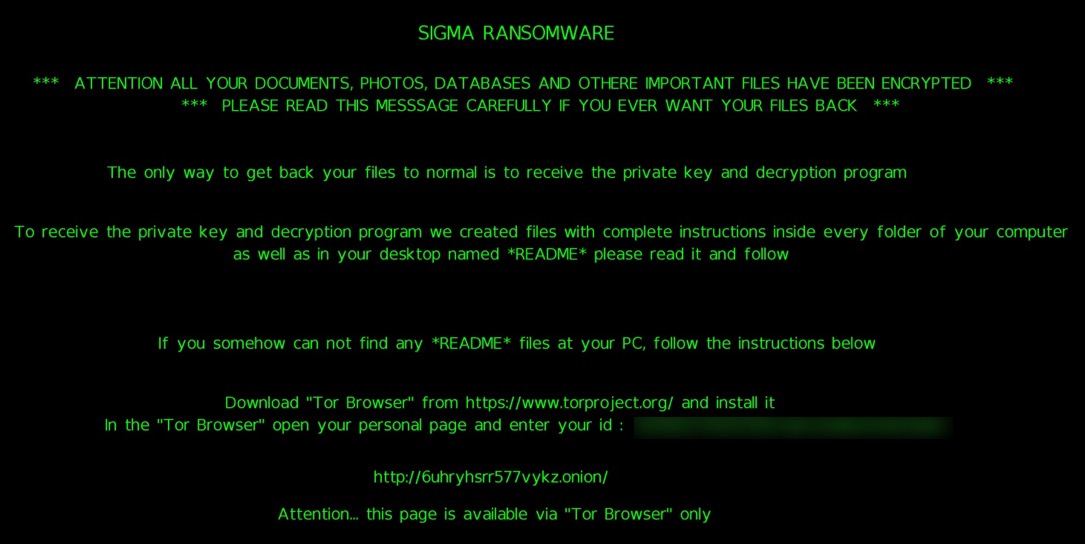
Shown above: Desktop background from an infected Windows host.
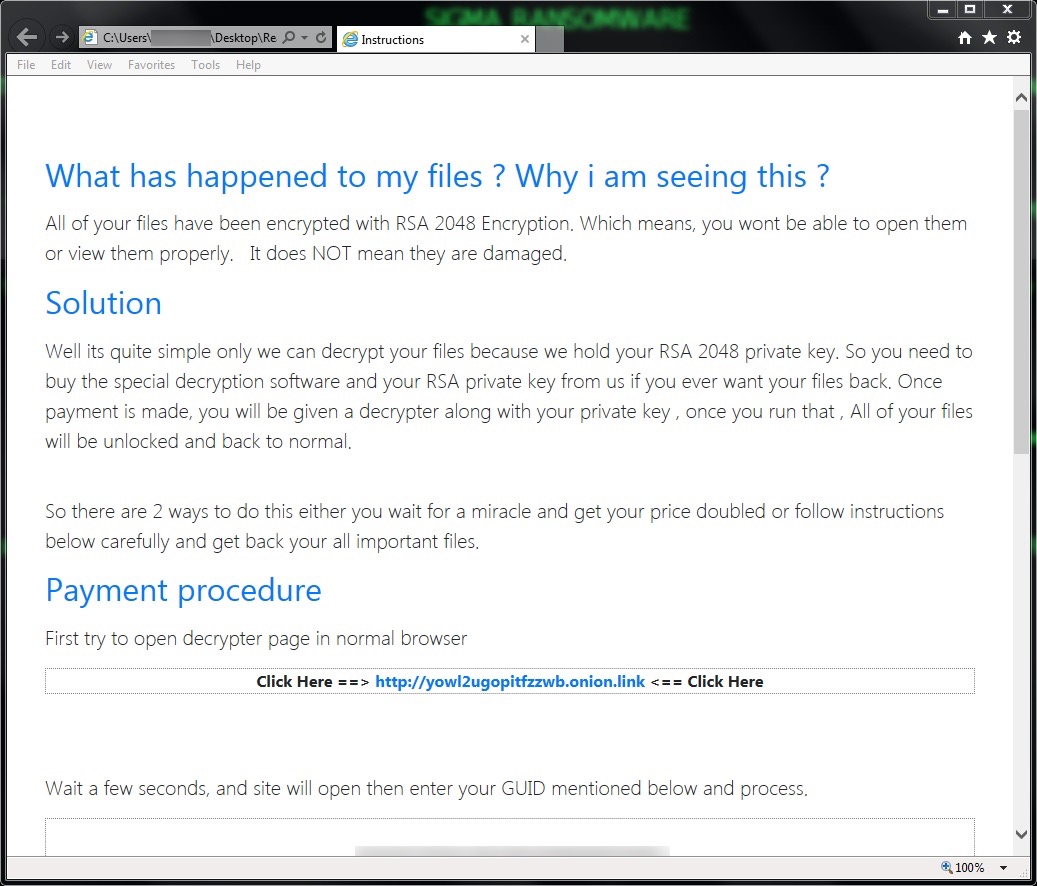
Shown above: Decryption instructions from an HTML file dropped to the infected user's desktop.
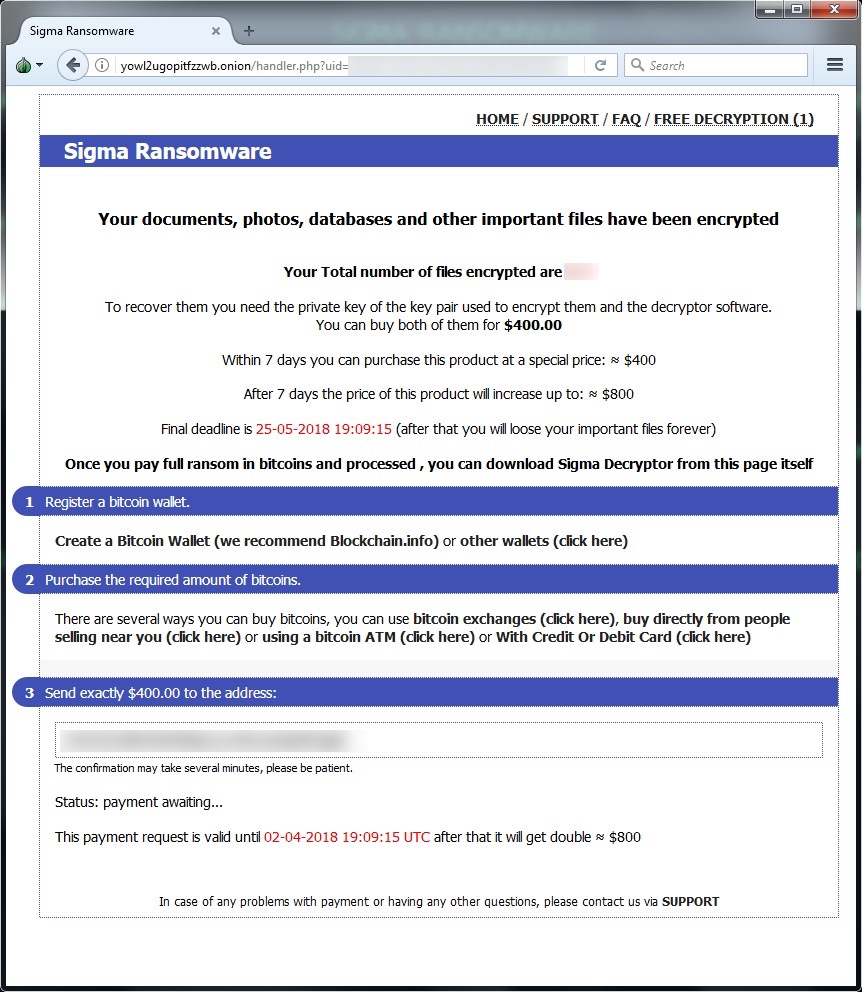
Shown above: Sigma ransomware decryptor.
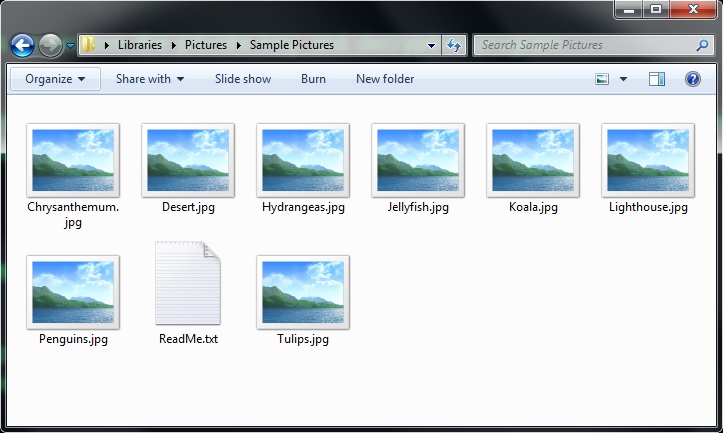
Shown above: Example of encrypted files from the Sigma ransomware infection.
Click here to return to the main page.