2018-03-27 - FAKE CHROME, FIREFOX, OR FLASH UPDATE PAGES PUSH JS MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-03-27-injected-script-in-page-of-compromised-site.txt.zip 0.7 kB (723 bytes)
- 2018-03-22-fake-update-pcaps.zip 1.0 MB (1,023,489 bytes)
- 2018-03-22-fake-update-JS-files.zip 60.1 kB (60,060 bytes)
- 2018-03-22-fake-update-HTML-files.zip 654 kB (654,441 bytes)
- 2018-03-27-fake-update-pcaps.zip 1.1 MB (1,077,763 bytes)
- 2018-03-27-fake-update-JS-files.zip 56.3 kB (56,297 bytes)
- 2018-03-27-fake-update-HTML-files.zip 771 kB (771,043 bytes)
NOTES:
- Documented as early as 2017-10-16 with this sample: 7509d03a51430de9c69ab333ba70d11662e1ab4f118fc8934b4f11536cbf861a
- Traffic caused by downloaded JS files identified by EmergingThreats open ruleset as: Trojan.JS.Agent.dwz
- Thanks to @baberpervez2 who notified me about this traffic.
Shown above: Flow chart for this infection chain.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- track.positiverefreshment[.]org
- ceyr.biacap[.]com
- mvmj.fincruit[.]co
- eiow.fincruit[.]co[.]uk
- kaax.fincruit[.]co[.]uk
- hxxps[:]//www.dropbox[.]com/s/e8jszzoau8v6xfo/flashplayer_34.9.39_plugin.js?dl=1
- hxxps[:]//www.dropbox[.]com/s/2d4ix4jj5uedtxj/flashplayer_35.1.32_plugin.js?dl=1
- hxxps[:]//www.dropbox[.]com/s/flo9q730skowah2/Chrome_68.9.39.js?dl=1
- hxxps[:]//www.dropbox[.]com/s/bpjewqk4tqbkw3x/Chrome_71.1.33.js?dl=1
- hxxps[:]//www.dropbox[.]com/s/na6tnhz4khvsa0f/Firefox_63.9.39.js?dl=1
- hxxps[:]//www.dropbox[.]com/s/ixmahakuj13yng6/Firefox_65.1.34.js?dl=1
TRAFFIC
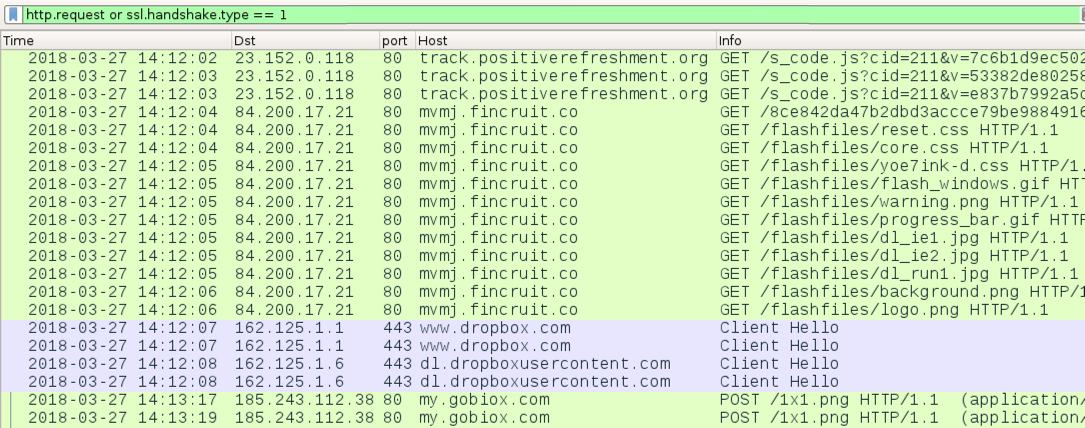
Shown above: Traffic from fake Flash updater page on 2018-03-27.
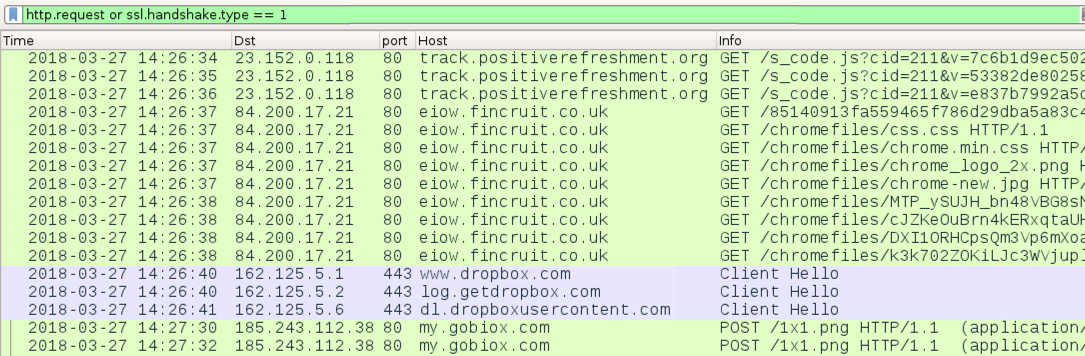
Shown above: Traffic from fake Chrome updater page on 2018-03-27.
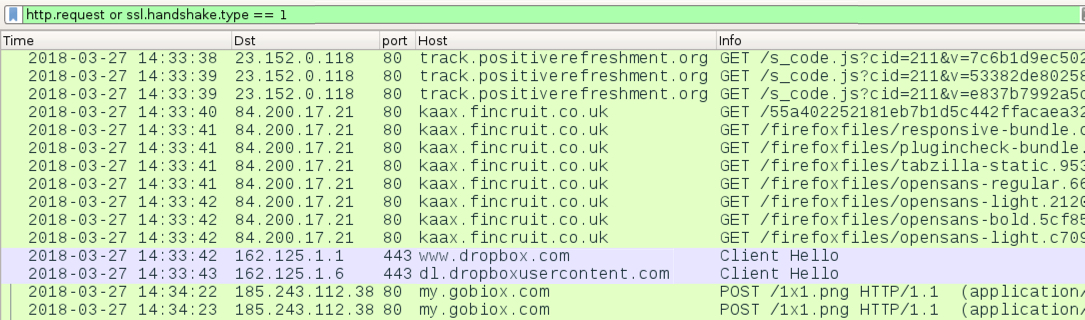
Shown above: Traffic from fake FireFox updater page on 2018-03-27.
2018-03-22 HTTP TRAFFIC FOR FAKE UPDATER PAGES:
- Compromised website with injected script
- 23.152.0[.]118 port 80 - track.positiverefreshment[.]org (sends script that leads to fake updater page)
- 84.200.17[.]21 port 80 - ceyr.biacap[.]com (fake updater page)
2018-03-22 DROPBOX URLS FOR THE FAKE UPDATERS:
- port 443 (HTTPS) - www.dropbox[.]com - GET /s/e8jszzoau8v6xfo/flashplayer_34.9.39_plugin.js?dl=1
- port 443 (HTTPS) - www.dropbox[.]com - GET /s/flo9q730skowah2/Chrome_68.9.39.js?dl=1
- port 443 (HTTPS) - www.dropbox[.]com - GET /s/na6tnhz4khvsa0f/Firefox_63.9.39.js?dl=1
2018-03-22 TRAFFIC GENERATED BY RUNNING DOWNLOADED .JS FILES:
- 185.243.112[.]38 port 80 - secur.rekomendasiforex[.]com - POST /index.aspx
2018-03-27 HTTP TRAFFIC FOR FAKE UPDATER PAGES:
- Compromised website with injected script
- 23.152.0[.]118 port 80 - track.positiverefreshment[.]org (sends script that leads to fake updater page)
- 84.200.17[.]21 port 80 - mvmj.fincruit[.]co (fake updater page)
- 84.200.17[.]21 port 80 - eiow.fincruit[.]co[.]uk (fake updater page)
- 84.200.17[.]21 port 80 - kaax.fincruit[.]co[.]uk (fake updater page)
2018-03-27 DROPBOX URLS WITH FAKE UPDATERS:
- port 443 (HTTPS) - www.dropbox[.]com - GET /s/2d4ix4jj5uedtxj/flashplayer_35.1.32_plugin.js?dl=1
- port 443 (HTTPS) - www.dropbox[.]com - GET /s/bpjewqk4tqbkw3x/Chrome_71.1.33.js?dl=1
- port 443 (HTTPS) - www.dropbox[.]com - GET /s/ixmahakuj13yng6/Firefox_65.1.34.js?dl=1
2018-03-27 TRAFFIC GENERATED BY RUNNING DOWNLOADED .JS FILES:
- 185.243.112[.]38 port 80 - my.gobiox[.]com - POST /1x1.png
FILE HASHES
FAKE UPDATERS FROM DROPBOX URLS ON 2018-03-22:
- SHA256 hash: b7d9330f59694d5a8a86f3e4ace40b725181f5f9f92e3c5a027fec9a52555f13
File size: 39,518 bytes
File name: Chrome_68.9.39.js
File name: Firefox_63.9.39.js
File name: flashplayer_34.9.39_plugin.js
FAKE UPDATERS FROM DROPBOX URLS ON 2018-03-27:
- SHA256 hash: d99eb06a125b6696d696070c04b95c01dff6484d9ba06819f584be956e3e90c8
File size: 39,224 bytes
File name: Chrome_71.1.33.js
- SHA256 hash: a1070843ee1d9d8aa08e9d6c3b7947dc3fc3b53155c6354d2cc373c76f996b72
File size: 35,789 bytes
File name: Firefox_65.1.34.js
- SHA256 hash: 46a659498f20c2cf1dd8e72da8a4b98075385849e1a8b1def6a9bb62d0a842b8
File size: 35,445 bytes
File name: flashplayer_35.1.32_plugin.js
IMAGES
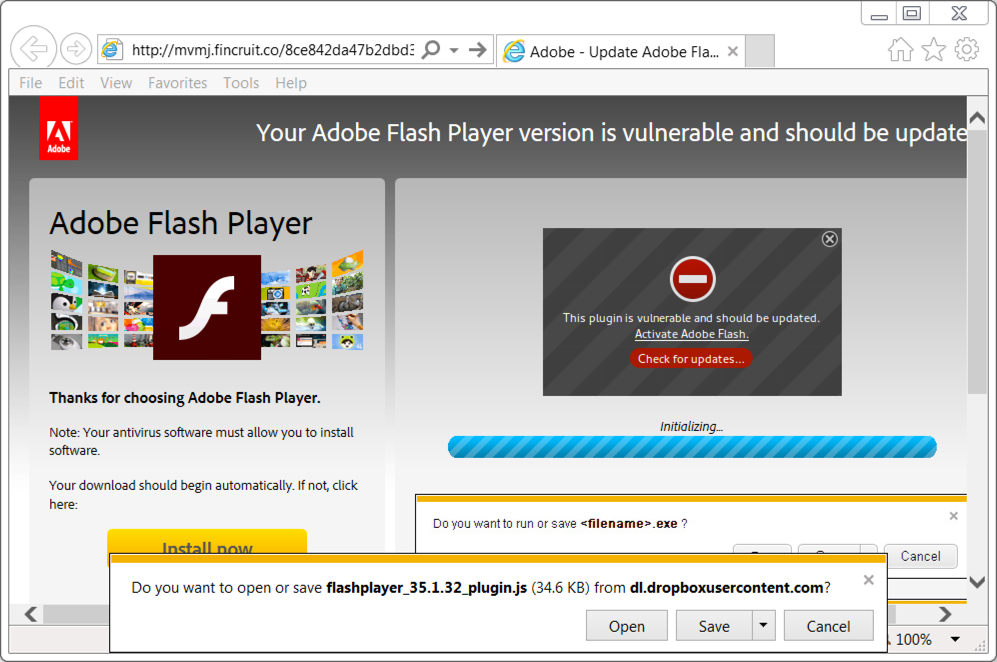
Shown above: Fake Flash player update page.
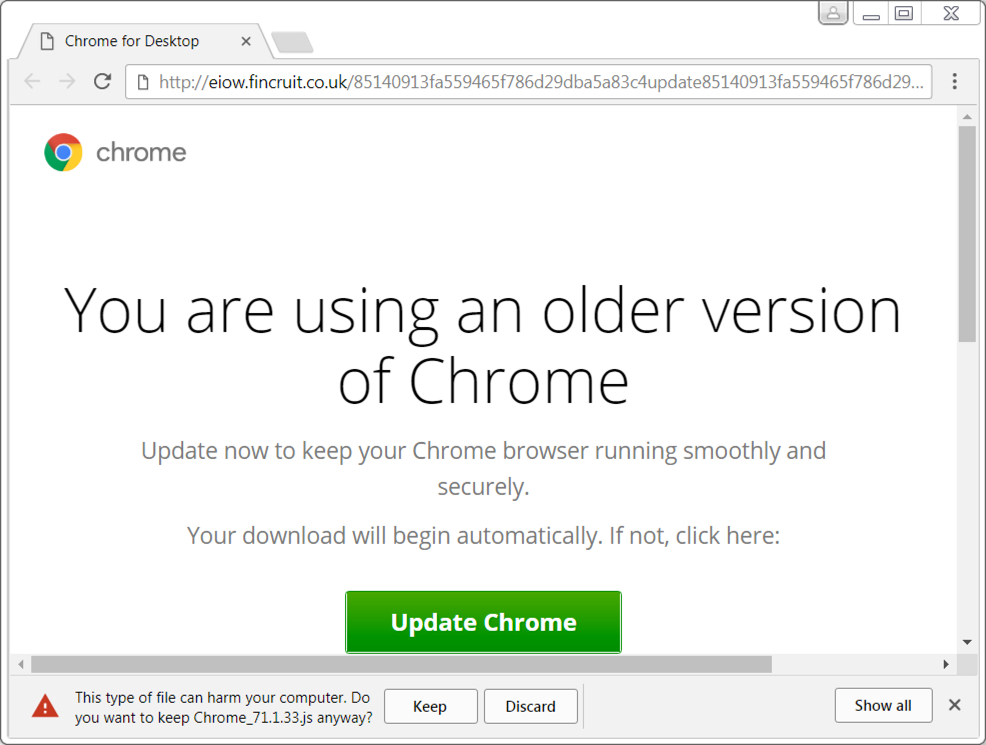
Shown above: Fake Chrome update page.
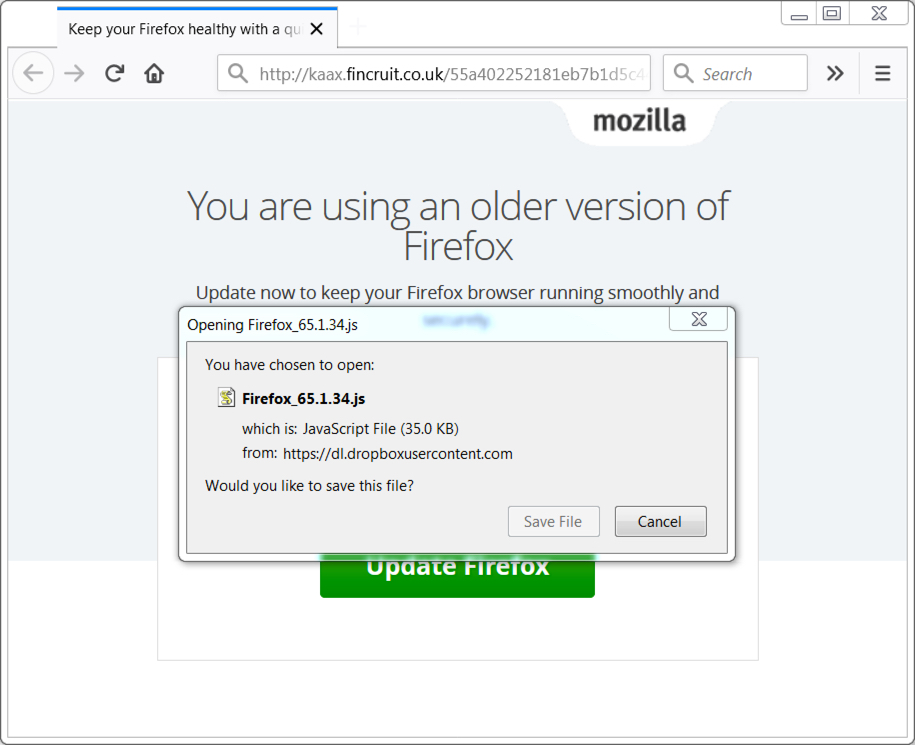
Shown above: Fake Firefox update page.
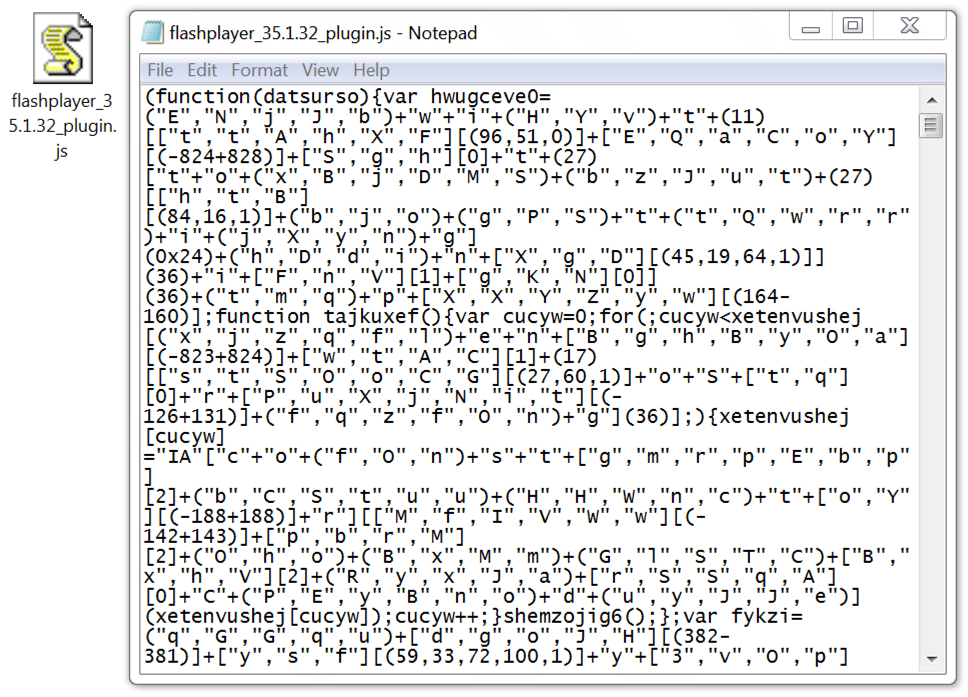
Shown above: One of the downloaded malicious JavaScript files.
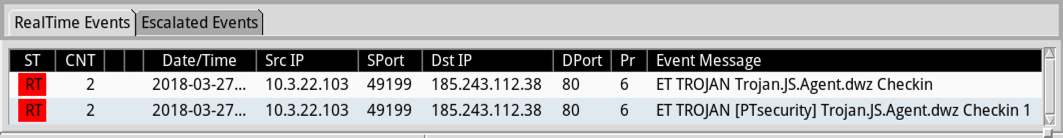
Shown above: Alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
Click here to return to the main page.

