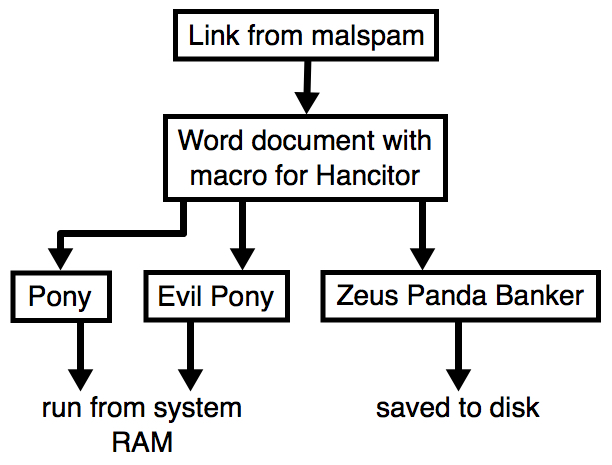
2018-04-11 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-04-11-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 2.2 MB (2,192,695 bytes)
- 2018-04-11-Hancitor-infection-with-Zeus-Panda-Banker.pcap (2,645,333 bytes)
- Zip archive of the emails: 2018-04-11-Hancitor-malspam-15-examples.txt.zip 4.9 kB (4,843 bytes)
- 2018-04-11-Hancitor-malspam-15-examples.txt (94,925 bytes)
- Zip archive of the malware: 2018-04-11-malware-from-Hancitor-infection.zip 226 kB (225,763 bytes)
- 2018-04-11-Word-doc-with-macro-for-Hancitor.doc (224,256 bytes)
- 2018-04-11-Zeus-Panda-Banker-sample.exe (184,320 bytes)
NOTES:
- The block list contains additional post-infection URLs originally reported by @James_inthe_box reported on a Pastebin link here.
- As always, my thanks to everyone who keeps an eye on this malspam and reports about it near-real-time on Twitter.
Shown above: Flow chart for a typical Hancitor malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- 166e61[.]com
- drywallexpo[.]com
- estimating[.]training
- finishtradeexpo[.]com
- fleamarketfragrances[.]com
- gurwitz[.]com
- ourversionfragrances[.]com
- ourversionscents[.]com
- knockoffcologne[.]com
- virtualdrywallexpo[.]com
- gotsurievent[.]com
- henfetanug[.]ru
- saortonsjohn[.]ru
- hxxp[:]//contentsuperstar[.]com/wp-content/languages/plugins/1
- hxxp[:]//contentsuperstar[.]com/wp-content/languages/plugins/4
- hxxp[:]//contentsuperstar[.]com/wp-content/languages/plugins/5
- hxxp[:]//image-a[.]com/wp/wp-content/plugins/easy-media-gallery/includes/1
- hxxp[:]//image-a[.]com/wp/wp-content/plugins/easy-media-gallery/includes/4
- hxxp[:]//image-a[.]com/wp/wp-content/plugins/easy-media-gallery/includes/5
- hxxp[:]//kuchingsupplies[.]com/wp-content/plugins/gallery-by-supsystic/vendor/Twig/1
- hxxp[:]//kuchingsupplies[.]com/wp-content/plugins/gallery-by-supsystic/vendor/Twig/4
- hxxp[:]//kuchingsupplies[.]com/wp-content/plugins/gallery-by-supsystic/vendor/Twig/5
- lyrintedba[.]com
EMAILS
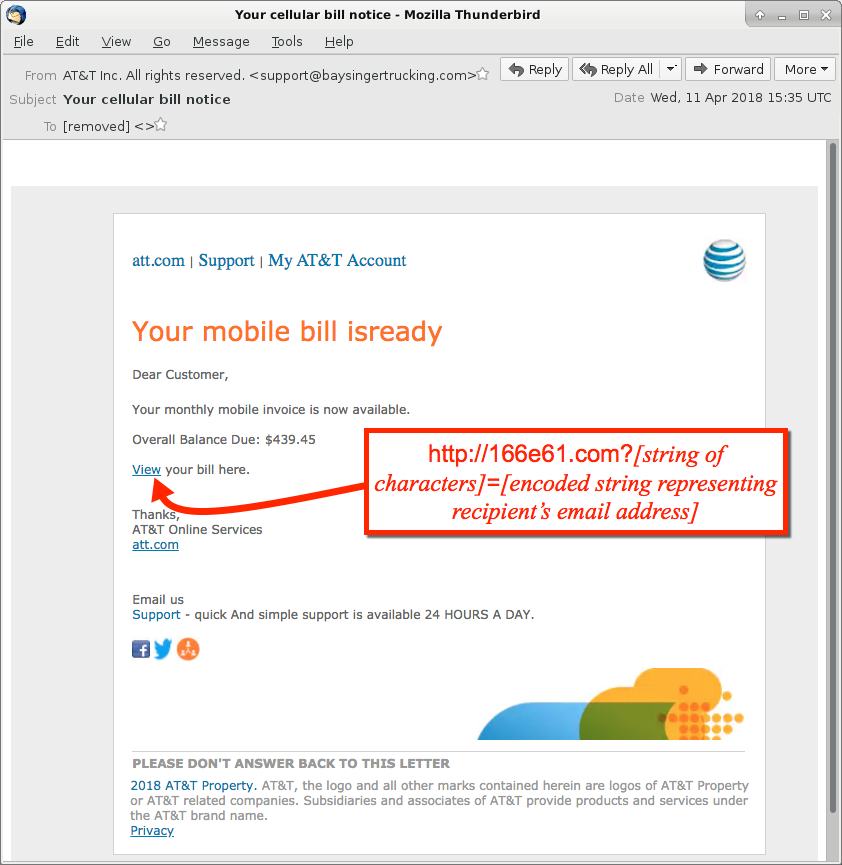
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2018-04-11 as early as 15:07 UTC through at least 17:42 UTC
- Received: from baysingertrucking[.]com ([8.46.162[.]38])
- Received: from baysingertrucking[.]com ([12.25.2[.]162])
- Received: from baysingertrucking[.]com ([50.248.104[.]45])
- Received: from baysingertrucking[.]com ([65.71.222[.]139])
- Received: from baysingertrucking[.]com ([65.175.137[.]10])
- Received: from baysingertrucking[.]com ([69.36.88[.]210])
- Received: from baysingertrucking[.]com ([69.70.18[.]148])
- Received: from baysingertrucking[.]com ([76.189.202[.]187])
- Received: from baysingertrucking[.]com ([81.43.73[.]211])
- Received: from baysingertrucking[.]com ([81.199.17[.]201])
- Received: from baysingertrucking[.]com ([98.191.128[.]95])
- Received: from baysingertrucking[.]com ([152.160.35[.]34])
- Received: from baysingertrucking[.]com ([159.180.236[.]145])
- Received: from baysingertrucking[.]com ([174.109.248[.]174])
- Received: from baysingertrucking[.]com ([198.0.79[.]250])
- From: "AT&T Inc. " <support@baysingertrucking[.]com>
- From: "AT&T Inc. All rights reserved." <support@baysingertrucking[.]com>
- From: "AT&T Services " <support@baysingertrucking[.]com>
- From: "AT&T Services All rights reserved." <support@baysingertrucking[.]com>
- Subject: Your cellular bill notice
- Subject: Your cellular bill notice from AT&T
- Subject: Your cellular invoice notification from AT&T
- Subject: Your mobile bill notice from AT&T
- Subject: Your mobile bill notification from AT&T
- Subject: Your mobile invoice notification
- Subject: Your mobile invoice notification from AT&T
- Subject: Your wireless bill notice from AT&T
- Subject: Your wireless bill notification
- Subject: Your wireless invoice notice from AT&T

Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
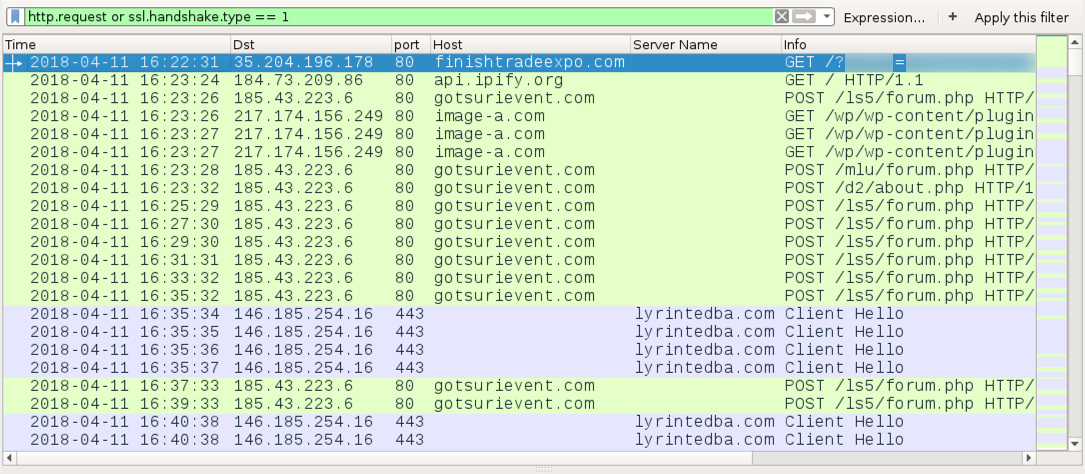
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS FOR THE WORD DOCUMENT:
- hxxp[:]//166e61[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//estimating[.]training?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//finishtradeexpo[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//fleamarketfragrances[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//gurwitz[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//knockoffcologne[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//ourversionfragrances[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//ourversionscents[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//virtualdrywallexpo[.]com?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 35.204.196[.]178 port 80 - finishtradeexpo.com - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify[.]org - GET /
- 185.43.223[.]6 port 80 - gotsurievent[.]com - POST /ls5/forum.php
- 185.43.223[.]6 port 80 - gotsurievent[.]com - POST /mlu/about.php
- 185.43.223[.]6 port 80 - gotsurievent[.]com - POST /d2/about.php
- 217.174.156[.]249 port 80 - image-a[.]com - GET /wp-content/plugins/easy-media-gallery/includes/1
- 217.174.156[.]249 port 80 - image-a[.]com - GET /wp-content/plugins/easy-media-gallery/includes/4
- 217.174.156[.]249 port 80 - image-a[.]com - GET /wp-content/plugins/easy-media-gallery/includes/5
- 146.185.254[.]16 port 443 - lyrintedba[.]com - HTTPS/SSL/TLS traffic from Zeus Panda Banker
FILE HASHES
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: d60dbc150c1ad9f052e4ed8c73d2dbcedf95ca02706697bb87b142afdc9351b6
File size: 224,256 bytes
File name: invoice_319872.doc [any six random digits for the numbers]
File description: Word document with macro for Hancitor
- SHA256 hash: 73df38455456a94565f47f06839ab029a7e8dddb42dcdb3e8a0e2db4ee148fba
File size: 184,320 bytes
File location: C:\Users\[username]\AppData\Local\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
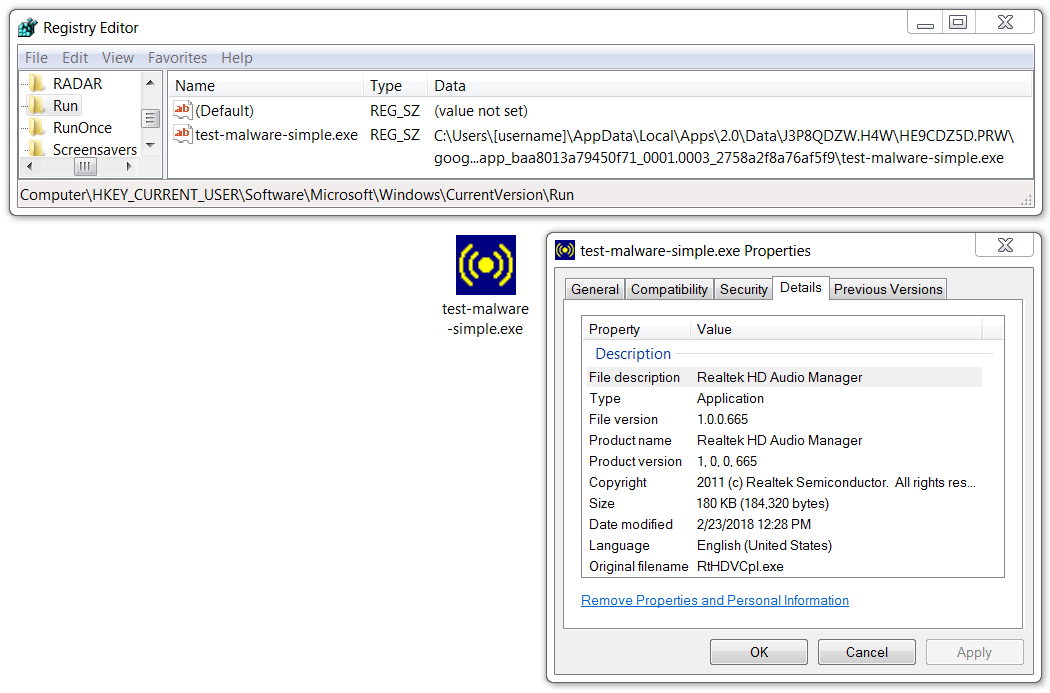
Shown above: Zeus Panda Banker persistent on the infected Windows host.
Click here to return to the main page.