2018-04-17 - "ZERO-GAND" MALSPAM PUSHING GANDCRAB RANSOMAWARE AGAIN SINCE MONDAY 2018-04-16
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the malspam tracker: 2018-04-17-Zero-Gand-malspam-tracker-40-examples.csv.zip 2.3 kB (2,295 bytes)
- Zip archive of some infection traffic: 2018-04-17-GandCrab-infection-traffic.pcap.zip 191 kB (190,690 bytes)
- Zip archive of the emails, malware & artifacts: 2018-04-17-Zero-Gand-emails-and-malware-from-GandCrab-ransomware-infection.zip 1.6 MB (1,614,335 bytes)
NOTES:
- These waves of malspam use [0.0.0[.]0] as a spoofed address in a "Received: from" line from the email headers.
- Last week, I started calling this the "Zero-Gand" campaign as noted in this ISC diary.
- This campaign occasionally changes attachments. So far, I've seen it use Word documents or JS files.
- Since yesterday, it's been using JS files.
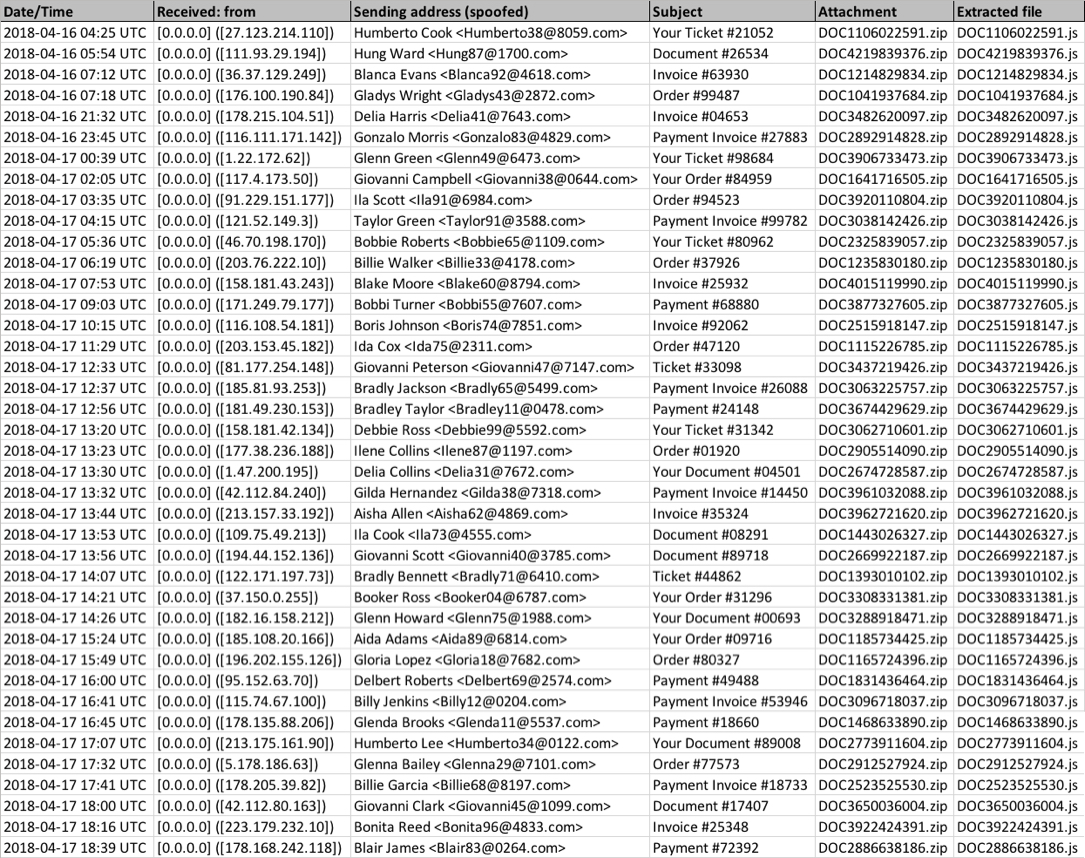
Shown above: Screenshot from the malspam tracker.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains. With the exception of "uh.exe", all of this has been previously reported.
- hxxp[:]//185.189.58[.]222/uh.exe
- ransomeware[.]bit
- zonealarm[.]bit
- gandcrab2pie73et[.]onion
- gandcrab2pie73et[.]onion[.]rip
- gandcrab2pie73et[.]onion[.]plus
- gandcrab2pie73et[.]onion[.]to
DATA FROM 40 EMAILS:
- Date/Time: Monday 2018-04-16 as early as 04:25 UTC through Tuesday 2018-04-17 as late as 18:39 UTC
- Received: from [0.0.0[.]0] ([1.22.172[.]62])
- Received: from [0.0.0[.]0] ([1.47.200[.]195])
- Received: from [0.0.0[.]0] ([5.178.186[.]63])
- Received: from [0.0.0[.]0] ([27.123.214[.]110])
- Received: from [0.0.0[.]0] ([36.37.129[.]249])
- Received: from [0.0.0[.]0] ([37.150.0[.]255])
- Received: from [0.0.0[.]0] ([42.112.80[.]163])
- Received: from [0.0.0[.]0] ([42.112.84[.]240])
- Received: from [0.0.0[.]0] ([46.70.198[.]170])
- Received: from [0.0.0[.]0] ([81.177.254[.]148])
- Received: from [0.0.0[.]0] ([91.229.151[.]177])
- Received: from [0.0.0[.]0] ([95.152.63[.]70])
- Received: from [0.0.0[.]0] ([109.75.49[.]213])
- Received: from [0.0.0[.]0] ([111.93.29[.]194])
- Received: from [0.0.0[.]0] ([115.74.67[.]100])
- Received: from [0.0.0[.]0] ([116.108.54[.]181])
- Received: from [0.0.0[.]0] ([116.111.171[.]142])
- Received: from [0.0.0[.]0] ([117.4.173[.]50])
- Received: from [0.0.0[.]0] ([121.52.149[.]3])
- Received: from [0.0.0[.]0] ([122.171.197[.]73])
- Received: from [0.0.0[.]0] ([158.181.42[.]134])
- Received: from [0.0.0[.]0] ([158.181.43[.]243])
- Received: from [0.0.0[.]0] ([171.249.79[.]177])
- Received: from [0.0.0[.]0] ([176.100.190[.]84])
- Received: from [0.0.0[.]0] ([177.38.236[.]188])
- Received: from [0.0.0[.]0] ([178.135.88[.]206])
- Received: from [0.0.0[.]0] ([178.168.242[.]118])
- Received: from [0.0.0[.]0] ([178.205.39[.]82])
- Received: from [0.0.0[.]0] ([178.215.104[.]51])
- Received: from [0.0.0[.]0] ([181.49.230[.]153])
- Received: from [0.0.0[.]0] ([182.16.158[.]212])
- Received: from [0.0.0[.]0] ([185.108.20[.]166])
- Received: from [0.0.0[.]0] ([185.81.93[.]253])
- Received: from [0.0.0[.]0] ([194.44.152[.]136])
- Received: from [0.0.0[.]0] ([196.202.155[.]126])
- Received: from [0.0.0[.]0] ([203.153.45[.]182])
- Received: from [0.0.0[.]0] ([203.76.222[.]10])
- Received: from [0.0.0[.]0] ([213.157.33[.]192])
- Received: from [0.0.0[.]0] ([213.175.161[.]90])
- Received: from [0.0.0[.]0] ([223.179.232[.]10])
- From: Aida Adams <Aida89@6814[.]com>
- From: Aisha Allen <Aisha62@4869[.]com>
- From: Billie Garcia <Billie68@8197[.]com>
- From: Billie Walker <Billie33@4178[.]com>
- From: Billy Jenkins <Billy12@0204[.]com>
- From: Blair James <Blair83@0264[.]com>
- From: Blake Moore <Blake60@8794[.]com>
- From: Blanca Evans <Blanca92@4618[.]com>
- From: Bobbi Turner <Bobbi55@7607[.]com>
- From: Bobbie Roberts <Bobbie65@1109[.]com>
- From: Bonita Reed <Bonita96@4833[.]com>
- From: Booker Ross <Booker04@6787[.]com>
- From: Boris Johnson <Boris74@7851[.]com>
- From: Bradley Taylor <Bradley11@0478[.]com>
- From: Bradly Bennett <Bradly71@6410[.]com>
- From: Bradly Jackson <Bradly65@5499[.]com>
- From: Debbie Ross <Debbie99@5592[.]com>
- From: Delbert Roberts <Delbert69@2574[.]com>
- From: Delia Collins <Delia31@7672[.]com>
- From: Delia Harris <Delia41@7643[.]com>
- From: Gilda Hernandez <Gilda38@7318[.]com>
- From: Giovanni Campbell <Giovanni38@0644[.]com>
- From: Giovanni Clark <Giovanni45@1099[.]com>
- From: Giovanni Peterson <Giovanni47@7147[.]com>
- From: Giovanni Scott <Giovanni40@3785[.]com>
- From: Gladys Wright <Gladys43@2872[.]com>
- From: Glenda Brooks <Glenda11@5537[.]com>
- From: Glenn Green <Glenn49@6473[.]com>
- From: Glenn Howard <Glenn75@1988[.]com>
- From: Glenna Bailey <Glenna29@7101[.]com>
- From: Gloria Lopez <Gloria18@7682[.]com>
- From: Gonzalo Morris <Gonzalo83@4829[.]com>
- From: Humberto Cook <Humberto38@8059[.]com>
- From: Humberto Lee <Humberto34@0122[.]com>
- From: Hung Ward <Hung87@1700[.]com>
- From: Ida Cox <Ida75@2311[.]com>
- From: Ila Cook <Ila73@4555[.]com>
- From: Ila Scott <Ila91@6984[.]com>
- From: Ilene Collins <Ilene87@1197[.]com>
- From: Taylor Green <Taylor91@3588[.]com>
- Subject: Document #08291
- Subject: Document #17407
- Subject: Document #26534
- Subject: Document #89718
- Subject: Invoice #04653
- Subject: Invoice #25348
- Subject: Invoice #25932
- Subject: Invoice #35324
- Subject: Invoice #63930
- Subject: Invoice #92062
- Subject: Order #01920
- Subject: Order #37926
- Subject: Order #47120
- Subject: Order #77573
- Subject: Order #80327
- Subject: Order #94523
- Subject: Order #99487
- Subject: Payment #18660
- Subject: Payment #24148
- Subject: Payment #49488
- Subject: Payment #68880
- Subject: Payment #72392
- Subject: Payment Invoice #14450
- Subject: Payment Invoice #18733
- Subject: Payment Invoice #26088
- Subject: Payment Invoice #27883
- Subject: Payment Invoice #53946
- Subject: Payment Invoice #99782
- Subject: Ticket #33098
- Subject: Ticket #44862
- Subject: Your Document #00693
- Subject: Your Document #04501
- Subject: Your Document #89008
- Subject: Your Order #09716
- Subject: Your Order #31296
- Subject: Your Order #84959
- Subject: Your Ticket #21052
- Subject: Your Ticket #31342
- Subject: Your Ticket #80962
- Subject: Your Ticket #98684
TRAFFIC
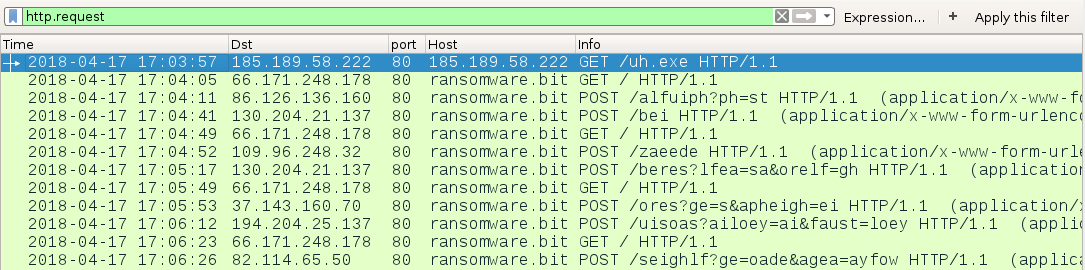
Shown above: Traffic from the infection fitlered in Wireshark.
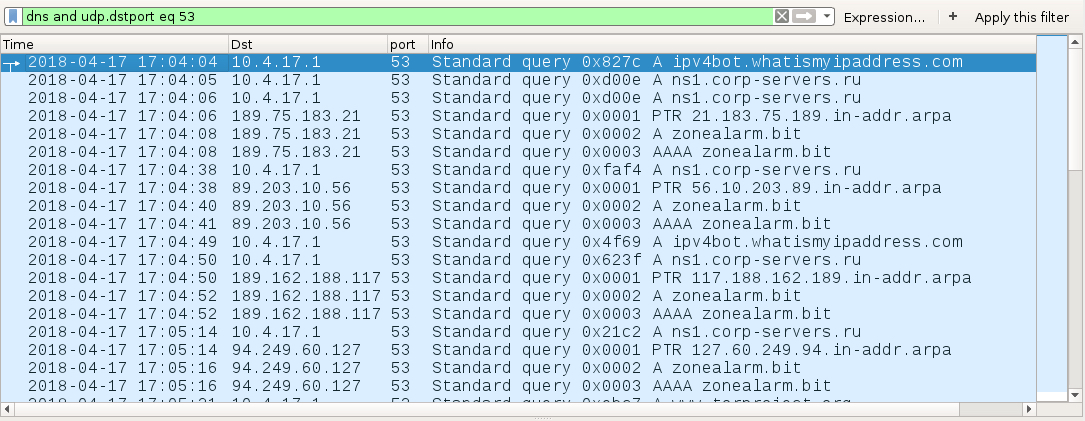
Shown above: Notice how some of the DNS traffic goes to public IP addresses, which is different than what's normally configured (in this case, normal is 10.4.17[.]1).
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 185.189.58[.]222 port 80 - 185.189.58[.]222 - GET /uh.exe
- 66.171.248[.]178 port 80 - ransomware[.]bit - GET /
- 86.126.136[.]160 port 80 - ransomware[.]bit - POST /alfuiph?ph=st
- 130.204.21[.]137 port 80 - ransomware[.]bit - POST /bei
- 66.171.248[.]178 port 80 - ransomware[.]bit - GET /
- 109.96.248[.]32 port 80 - ransomware[.]bit - POST /zaeede
- 130.204.21[.]137 port 80 - ransomware[.]bit - POST /beres?lfea=sa&orelf=gh
- 66.171.248[.]178 port 80 - ransomware[.]bit - GET /
- 37.143.160[.]70 port 80 - ransomware[.]bit - POST /ores?ge=s&apheigh=ei
- 194.204.25[.]137 port 80 - ransomware[.]bit - POST /uisoas?ailoey=ai&faust=loey
- 66.171.248[.]178 port 80 - ransomware[.]bit - GET /
- 82.114.65[.]50 port 80 - ransomware[.]bit - POST /seighlf?ge=oade&agea=ayfow
- DNS queries for ipv4bot.whatismyipaddress[.]com (results used in IP address checks to ransomware[.]bit)
- DNS queries for ns1.corp-servers[.]ru (results used in DNS queries for zonealarm[.]bit)
- 89.203.10[.]56 port 53 - DNS query for zonealarm[.]bit (results used in HTTP POST requests to ransomware[.]bit)
- 94.249.60[.]127 port 53 - DNS query for zonealarm[.]bit (results used in HTTP POST requests to ransomware[.]bit)
- 189.162.188[.]117 port 53 - DNS query for zonealarm[.]bit (results used in HTTP POST requests to ransomware[.]bit)
- 189.75.183[.]21 port 53 - DNS query for zonealarm[.]bit (results used in HTTP POST requests to ransomware[.]bit)
DOMAINS FROM THE DECRYPTION INSTRUCTIONS:
- gandcrab2pie73et[.]onion
- gandcrab2pie73et[.]onion[.]rip
- gandcrab2pie73et[.]onion[.]plus
- gandcrab2pie73et[.]onion[.]to
FILE HASHES
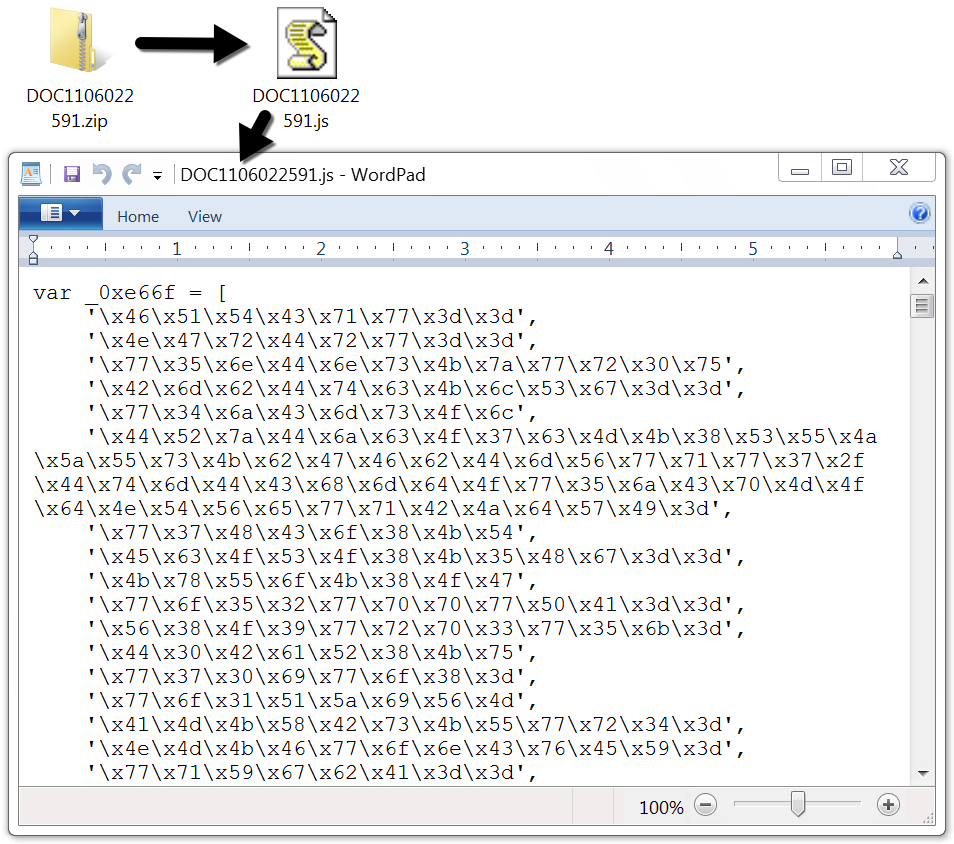
Shown above: One of the malspam attachments and its extracted JS file.
40 EMAIL ATTACHMENTS:
- faf0ebf33d21e2a9cf46b6d6bb67cd0b50256cfe4b33588e087f72c6f653d08b - DOC1041937684.zip
- 7fe716a12480983c7694d66ff9f379d780fdb1cca1131031dbd9af109c010986 - DOC1106022591.zip
- 7ef9665776daf32e2f643de696e0f84ccb396e03c565840cb3c5d6421eba5415 - DOC1115226785.zip
- bf1f21531e2356036006115bde8585061f97bddd5b940b2417e71c59ee78214b - DOC1165724396.zip
- bc2399c08e1b31d0247bbd579e73296ce6305703cecf0628fa0567031fd06cf6 - DOC1185734425.zip
- 28fcdeacda337c36b9fc26849cc8531654ec2f5cedecd8fb8e24e4b1eccf3799 - DOC1214829834.zip
- d77eb535d17cb82f48b8a8db1529de7c1501a1c8cce030056fd7737c520d300f - DOC1235830180.zip
- bfe6ad096e9ef46fb13da46e0253ffa772a947e8b1f2aff9f0aed14a52e04dc5 - DOC1393010102.zip
- b143002c473786d89ea86658ce84cddd9e72a610d35fc7e0c9face57b4a4c4b7 - DOC1443026327.zip
- c0b164d4731ff52a6e7a2f67b813e96e586d9250f21b91a59625425f228b2c73 - DOC1468633890.zip
- 8da730793a001de06b3d029e7811e78837461f0ebc389956735694c137c6ba07 - DOC1641716505.zip
- 6438a70837d41daad80b68e1ea7bcdce8d08b8f6054de9ee510998dc32943ea1 - DOC1831436464.zip
- 98b9cf06d55798b754f5758a6486121901d20631f923cba6815568ed090cc04d - DOC2325839057.zip
- 2b36af6efd2b0fbea039f385a54070392fa6c352a820df888c788b22e06d11c4 - DOC2515918147.zip
- 7de669191877e04d6450fed5aa0616ba761d642429ca9ff612362774dfd6c87c - DOC2523525530.zip
- a6645dad4201a884645c00259e092c0dbaa5a94139d35921425e3ce67e8fa25b - DOC2669922187.zip
- ee0100e58c52657166a2baed792dfd4cdbc2928d6e29c34ae0d53ce640e52055 - DOC2674728587.zip
- 196f8ef5430bfb2ca30c8aeb09e90af82a4a74b2bfd7376634d11e27180e5594 - DOC2773911604.zip
- 828d1c02d94efa6f1982136f96af116f4f82e93dd40589cf8c9b2661983e90eb - DOC2886638186.zip
- c4eee41c646e840cf86142c97cc5d07ce45a7c93d2e66aa00c9d61840acbdb97 - DOC2892914828.zip
- ce006e1d06143ed2305154c55cc5c108b864c517d0233d934550991d4a6fb313 - DOC2905514090.zip
- 163d4f46900adae36b1467fe0e54ddf6185bfa51470ac7c26bae3c58aba79d00 - DOC2912527924.zip
- 5e85c40eca99c0dd79f5689ca443b6d529d9ab41837c47552d67dfc3830a4ff1 - DOC3038142426.zip
- 7df64aa821a9e39851c2994a7f4d39b7b0b1ae221a58ec8aecb55ded864c42aa - DOC3062710601.zip
- 11d7dfc73c6a1603030f27dbccff4a64caec47b4f258a440c176be6065ad4148 - DOC3063225757.zip
- 98ecddb70755ceeff10625765710e98e8d53ee6fe81a7ef91f404302b68bff0b - DOC3096718037.zip
- 920129258b67b150df804c9055330e1413bb93b83661b732bebb9977f7986eca - DOC3288918471.zip
- 2788dd2548f14945ce895df84ce8459f1735a154c243bcce90a9b22e3f0afbdc - DOC3308331381.zip
- 999388d82f1d51c7b3931045dfd289b5afa455def7297d3493a3686f7d05d0c5 - DOC3437219426.zip
- 3adb20ca38173db2faff3b10fb54964616dad7328193b499109f9203eb4203b8 - DOC3482620097.zip
- 38366f219b691f8415888313cf42e1213e7cc290927a0ee95fcf5649f5862c86 - DOC3650036004.zip
- ea9c75c00986f3593e27a7fe024825646366673959496353800b3311ece1f35d - DOC3674429629.zip
- 247acff8a2b1c2fbf1ad6c5e61c0ce8b361087b9a8b2bd514a5e5891bfb8dc6f - DOC3877327605.zip
- feb5ceeeea8d5174a69fdb8c0a0d55efaf74d368309769fc45720c2621ca18a9 - DOC3906733473.zip
- 7db92b7e99698b0074802a93c32782a9b019a05d8f424fb4c5bc8b8a7cb59c06 - DOC3920110804.zip
- 2a3d45abc55bfdbb25ff20b38f6c2ca4c58de8f062ab96ea6ccc6d52d61b0278 - DOC3922424391.zip
- f5cbec1fb7dd120f603f1b8ca75ad52367090405cbeaa173c8415b8ce83c7b01 - DOC3961032088.zip
- e318d924cbef7a8e5fe2205b5e079a95302b2e0ae330cd5809d3d12cfaafe85e - DOC3962721620.zip
- 403b2cbd35d6c177544d9fde8a807df201ba70b3adacab73d8bca67921a2b08f - DOC4015119990.zip
- 2c8b1c591b852b4acacb5f8dda24f863f5faabfbe54a5386aeb0c90026952150 - DOC4219839376.zip
40 EXTRACTED .JS FILES:
- bcccda3051c89d4bd2c1f9e70450cd8150284498cf188d98278b344d3a4841d7 - DOC1041937684.js
- 1eb351f8882be28fb0d52ed387cb1fe87efcbb185400248c4202ca8c26eb2896 - DOC1106022591.js
- c3a3c01680304de2f06015d1b79dc76d3fde7659ff98a975c0d2ca97e7ae4dae - DOC1115226785.js
- fd7e1992bee5a4beb9beefff1f2982356348574e6a07d6bcea2da7faab3b1352 - DOC1165724396.js
- 2fe4a5d7c748a5cb568b78ad364bffb3b40530eb873aa2562aa4aafbc58c08f9 - DOC1185734425.js
- 7bf0b6f86bf916614bc7ae67e567794e39df6097e1de3721f0f496e516a74334 - DOC1214829834.js
- 64b0d90da749409ebe2ab1c68ada8ea9b8f2e82bafd2a83babab4a40a51c022d - DOC1235830180.js
- 34f54e6a102435d7e7c19ca5ff0a1959f9dd56261a48b20476ef0302064214ee - DOC1393010102.js
- 14f31304b270f1e4009d012dd6959ed0db8dec5516c2bb578ba8bf5dd19eb26d - DOC1443026327.js
- 65e47f8492fd868c9c9a91d7ac35b8be73c94d1f96ab47a0d99a45e9f93989dc - DOC1468633890.js
- 3cd4312dcaac23dd29995f2d60a86554175b0e10d657ed3c8d007d0c9217d0f5 - DOC1641716505.js
- 2d1a8ad9936837daa2aa9c06d752a7efa84d856b847c48d21481886c9421a058 - DOC1831436464.js
- 3a37d90e98c0964f57163c3ec7b0805f8b8d3d1da8206db3a23af4523bd71460 - DOC2325839057.js
- 9134352687fe37b7d7fccf0727de431e7e0ba67fd071fe7a9c407e8fc3e334aa - DOC2515918147.js
- 1a49671814fde04000f22e8f6faf2dbf99b1ac951444c3910f99eec20e28511c - DOC2523525530.js
- 42fde73c742467f8df796a162607e8f17337fb02207ca35a4c7e6383a0c31419 - DOC2669922187.js
- 713d4f1f206a6a773827e9d1960269c51c8681c7a530639ab309763c2dcb7625 - DOC2674728587.js
- 5a273b0de041c6a520cce29dec9c435ae8179cb9def7f87959d44769c9ec683f - DOC2773911604.js
- 90f3b488a144e74bd81d318d9173d96f39e5a6107b1dbb617c3ee9877c4dc5d4 - DOC2886638186.js
- 1394a8cc6d7a945ebb674e23f08939f4c9ba6577c89c0dd252f292542dcda974 - DOC2892914828.js
- ee7fbb555a15a3b74b848bb09c702f55476b134f2489a8fb660f63096b180420 - DOC2905514090.js
- 7503ae5601d7daf81dcb2113bf2aac9175f3dfb5b386c4b6d4bf7df77532f334 - DOC2912527924.js
- 808aff0889036605b26beaee394148f8e172b30c83a33c707f439917e2f0f169 - DOC3038142426.js
- a6b7689d7efe0132cddd06662b30b76cf48f903fef6b40d3c88fa89ef31ea756 - DOC3062710601.js
- 46a39c24126e1fe5a2a88e60b2aba329942409ca2964633ea86a0386d16ba8f6 - DOC3063225757.js
- 57c398a854784b811ab4a14e558c25c2f51d4ba935e30b3513d635dc168bf3c0 - DOC3096718037.js
- da6e88ca1a256597f2e5382fdfe949abdbb303b53433eab6757f145327875b29 - DOC3288918471.js
- 05aacf529c09fbd8c85252af3306e8ce8318123ccc581f8d00cce4b9127f157a - DOC3308331381.js
- e3581807504cd338722b7031cf631c46404d66322b5ae090047936b16ebb52ec - DOC3437219426.js
- d41128ebd262fed5785cbc07335077d811612d70ad23476f36a204baf7410a6e - DOC3482620097.js
- 8392a6a5d04de4e09d048fb4e058c3aa12ed5b5f91ff1cd5603612210322550e - DOC3650036004.js
- 8bd9569019a3e739ea24bdc6dae691e45c028d59ce8330c98981710668aae424 - DOC3674429629.js
- 6148952ea78af12e9e54d42f2a3a9a8e4707d60990f8884be81e9be98997e528 - DOC3877327605.js
- 6eca72dece5f59f60903901bd3e4ac9c64c67a86c857cae4ad80d18d4fb4d435 - DOC3906733473.js
- 771d376429e18ca84bd24f64b15605e97f6392e362e7e63dce131a460e2cf2a3 - DOC3920110804.js
- d441d25540b7f0afdfdfd1bd8b2ca97b866380a0b79c16b18a85a2a35215415a - DOC3922424391.js
- 4eb7eeabd603bccdd1048c2f4b4393a14aa124c59430b492192f5e14d97c92ee - DOC3961032088.js
- c4b85dd31156948414d3c7da5b7226098e9bdb20661a75daa65762a0d66d0674 - DOC3962721620.js
- 134051bca4b9718c810e2bca64ad0c4aa8578384db1d73f52c67e8946d8f9748 - DOC4015119990.js
- ba5044f299986f223f41c7148cb71f996c2f2e4a1cdc86e6875a198319bce044 - DOC4219839376.js
GANDCRAB RANSOMWARE:
- SHA256 hash: 339d22b5e02c79cdaa355bb11b063645332d0a2fd43ae78af6577818c4078284
File size: 208,392 bytes
File location: C:\Users\[username]\AppData\Local\Temp\z.exe
File location: C:\Users\[username]\AppData\Roaming\Microsoft\cooxjh.exe
File description: Gandcrab ransomware
Click here to return to the main page.