2018-04-18 - HANCITOR INFECTION WITH ZEUS PANDA BANKER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the emails: 2018-04-18-Hancitor-malspam-27-examples.txt.zip 8.3 kB (8,312 bytes)
- 2018-04-18-Hancitor-malspam-27-examples.txt (152,024 bytes)
- Zip archive of the traffic: 2018-04-18-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 366 kB (365,912 bytes)
- 2018-04-18-Hancitor-infection-with-Zeus-Panda-Banker.pcap (576,073 bytes)
- Zip archive of the malware: 2018-04-18-malware-from-Hancitor-infection.zip 229 kB (229,032 bytes)
- 2018-04-18-Word-doc-with-macro-for-Hancitor.doc (259,072 bytes)
- 2018-04-18-Zeus-Panda-Banker-sample.exe (185,344 bytes)
NOTES:
- The block list contains additional info originally reported by @James_inthe_box and @Techhelplistcom.
- As always, my thanks to everyone who keeps an eye on this malspam and reports about it near-real-time on Twitter.
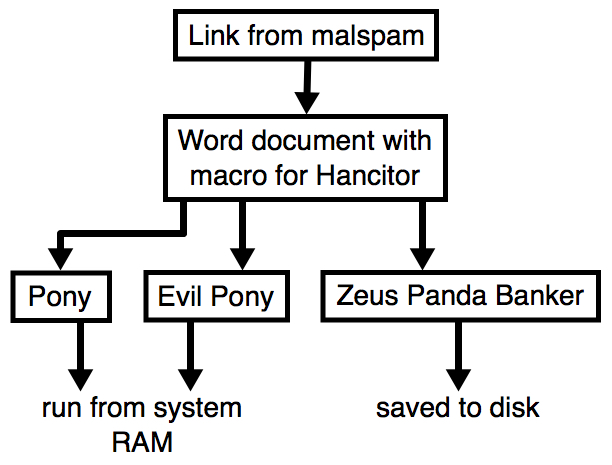
Shown above: Flow chart for a typical Hancitor malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- applyingtechnologyforsolutions[.]com
- bidsharp[.]net
- bidtraxx[.]net
- bieauviva[.]com
- citrobug[.]com
- contractorsauction[.]net
- div9[.]online
- finishtrades[.]org
- finishtradesmag[.]com
- fleamarketcologne[.]com
- fleamarketperfume[.]com
- graybirchcandle[.]com
- knockoffcolognes[.]com
- knockoffperfumes[.]com
- meh41[.]com
- paintestimatingclass[.]com
- paintestimatingcourse[.]com
- pro-lifeaction[.]org
- ettoldketru[.]com
- sacetothad[.]ru
- herstantosu[.]ru
- hxxp[:]//bestbodyrace[.]com/wp-content/plugins/evonapluginconfig/1
- hxxp[:]//bestbodyrace[.]com/wp-content/plugins/evonapluginconfig/2
- hxxp[:]//bestbodyrace[.]com/wp-content/plugins/evonapluginconfig/3
- hxxp[:]//itsonlyem[.]com/1
- hxxp[:]//itsonlyem[.]com/2
- hxxp[:]//itsonlyem[.]com/3
- hxxp[:]//agor-engineering[.]com/wp-content/plugins/really-simple-captcha/1
- hxxp[:]//agor-engineering[.]com/wp-content/plugins/really-simple-captcha/2
- hxxp[:]//agor-engineering[.]com/wp-content/plugins/really-simple-captcha/3
- hxxp[:]//australiancollectablesfair[.]com/wp-content/plugins/wordpress-importer/1
- hxxp[:]//australiancollectablesfair[.]com/wp-content/plugins/wordpress-importer/2
- hxxp[:]//australiancollectablesfair[.]com/wp-content/plugins/wordpress-importer/3
- hxxp[:]//grosirmebelmurah[.]com/wp-content/plugins/alexa-intsdernet/1
- hxxp[:]//grosirmebelmurah[.]com/wp-content/plugins/alexa-intsdernet/2
- hxxp[:]//grosirmebelmurah[.]com/wp-content/plugins/alexa-intsdernet/3
- lyrintedba[.]com
- reundlaboi[.]ru
EMAILS
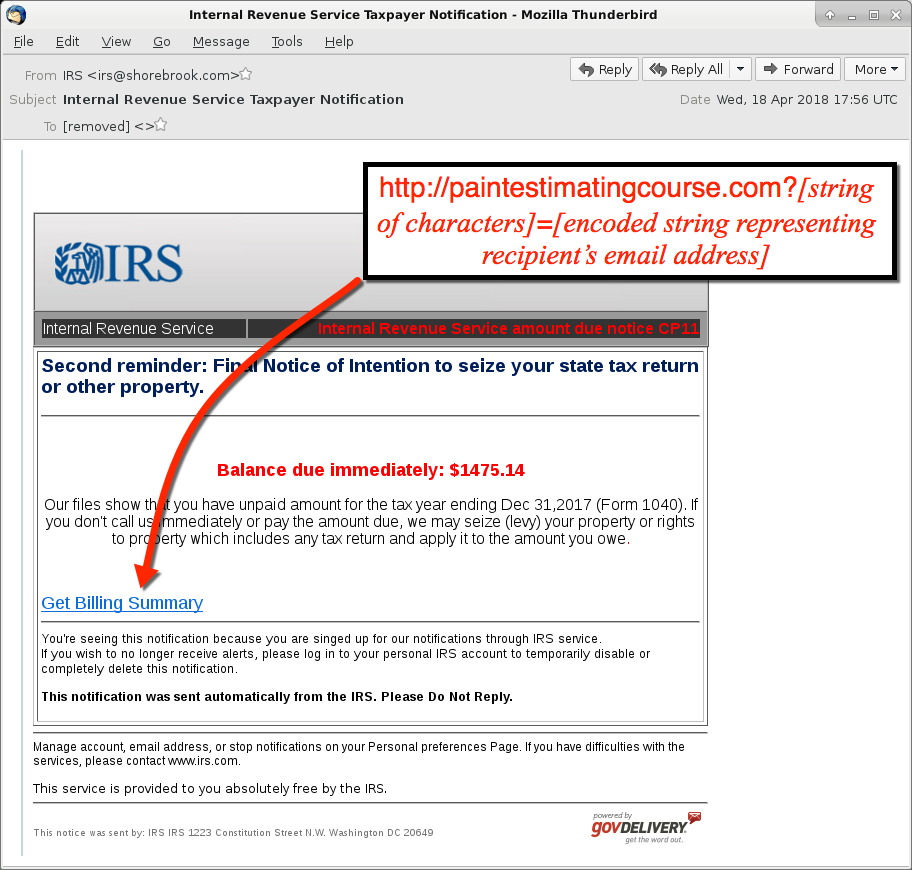
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Wednesday 2018-04-18 as early as 15:07 UTC through at least 17:56 UTC
- Received: from birchconnect[.]com ([12.162.128[.]222])
- Received: from birchconnect[.]com ([50.247.178[.]228])
- Received: from birchconnect[.]com ([50.249.244[.]57])
- Received: from birchconnect[.]com ([63.142.59[.]182])
- Received: from birchconnect[.]com ([69.128.215[.]202])
- Received: from birchconnect[.]com ([98.118.62[.]186])
- Received: from birchconnect[.]com ([142.160.83[.]229])
- Received: from birchconnect[.]com ([173.61.176[.]114])
- Received: from birchconnect[.]com ([174.229.129[.]82])
- Received: from birchconnect[.]com ([184.167.148[.]255])
- Received: from birchconnect[.]com ([208.118.138[.]224])
- Received: from birchconnect[.]com ([216.196.229[.]166])
- Received: from lawrencetractor[.]com ([50.78.130[.]206])
- Received: from lawrencetractor[.]com ([50.241.109[.]25])
- Received: from lawrencetractor[.]com ([73.34.196[.]197])
- Received: from lawrencetractor[.]com ([73.204.111[.]182])
- Received: from lawrencetractor[.]com ([108.46.196[.]93])
- Received: from lawrencetractor[.]com ([173.183.213[.]54])
- Received: from lawrencetractor[.]com ([173.25.234[.]93])
- Received: from shorebrook[.]com ([12.220.10[.]98])
- Received: from shorebrook[.]com ([24.245.109[.]158])
- Received: from shorebrook[.]com ([50.201.134[.]50])
- Received: from shorebrook[.]com ([74.208.185[.]164])
- Received: from shorebrook[.]com ([96.95.178[.]9])
- Received: from shorebrook[.]com ([98.21.120[.]166])
- Received: from shorebrook[.]com ([204.186.244[.]210])
- Received: from shorebrook[.]com ([216.196.229[.]166])
- From: "Internal Revenue Service" <irs@birchconnect[.]com>
- From: "Internal Revenue Service" <rs@shorebrook[.]com>
- From: "IRS" <irs@birchconnect[.]com>
- From: "IRS" <irs@lawrencetractor[.]com>
- From: "IRS" <rs@shorebrook[.]com>
- Subject: Internal Revenue Service
- Subject: Internal Revenue Service Final Notice
- Subject: Internal Revenue Service Important Notice
- Subject: Internal Revenue Service Important Notification
- Subject: Internal Revenue Service Notice to the Taxpayer
- Subject: Internal Revenue Service Notification
- Subject: Internal Revenue Service Taxpayer Notice
- Subject: Internal Revenue Service Taxpayer Notification
- Subject: IRS
- Subject: IRS Important Notice
- Subject: IRS Important Notification
- Subject: IRS Notice
- Subject: IRS Notice of intent to levy
- Subject: IRS Notice to the Taxpayer
- Subject: IRS Taxpayer Notice
- Subject: IRS Taxpayer Notification
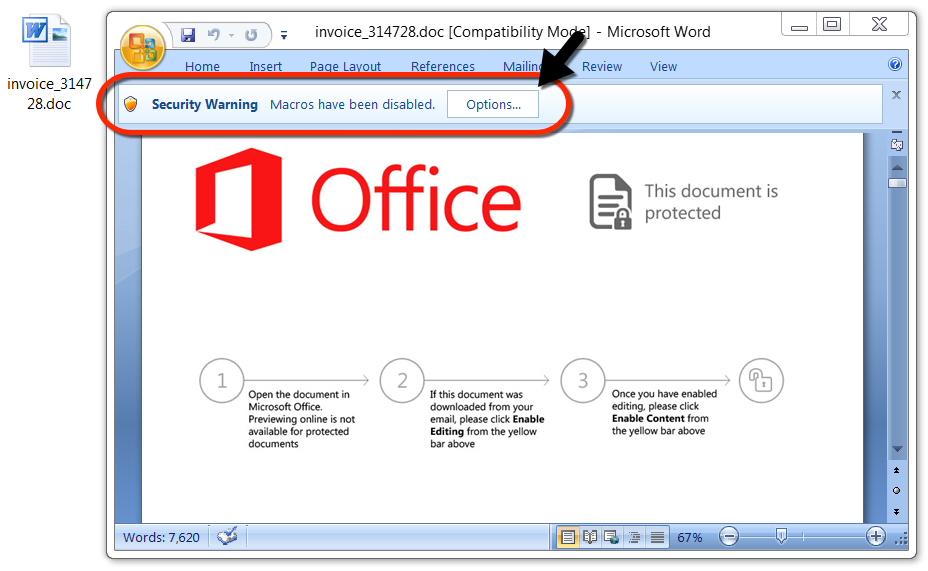
Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
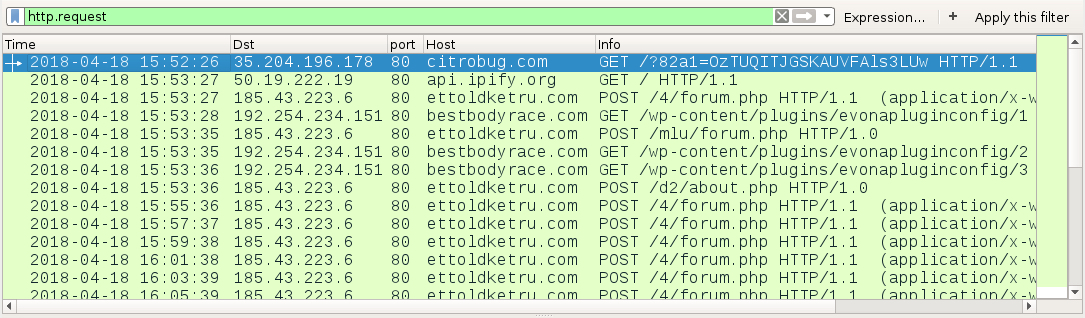
Shown above: Traffic from an infection filtered in Wireshark.
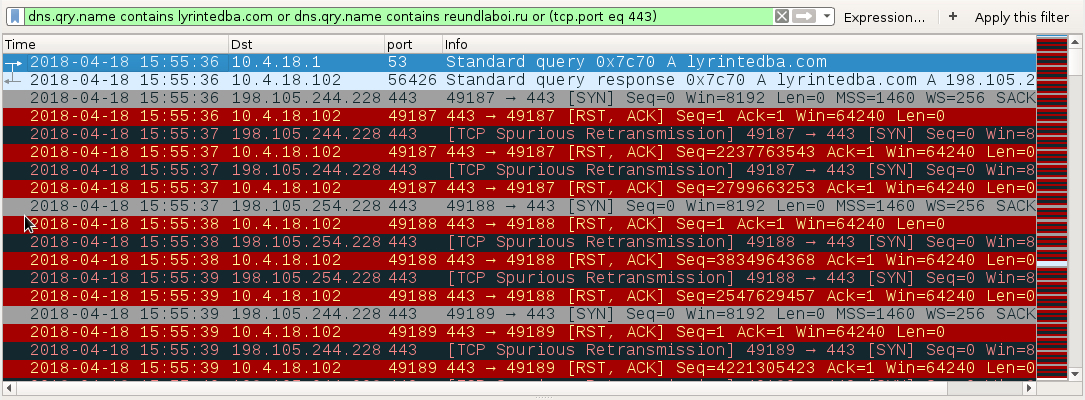
Shown above: DNS query and failed connection attempt for the Zeus Panda Banker traffic.
LINKS IN THE EMAILS TO DOWNLOAD THE WORD DOCUMENT:
- hxxp[:]//applyingtechnologyforsolutions[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//bidsharp[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//bidtraxx[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//citrobug[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//contractorsauction[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//div9[.]online?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//finishtrades[.]org?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//fleamarketcologne[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//fleamarketperfume[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//graybirchcandle[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//knockoffcolognes[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//knockoffperfumes[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//meh41[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//paintestimatingclass[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//paintestimatingcourse[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//pro-lifeaction[.]org?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 35.204.196[.]178 port 80 - citrobug[.]com - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify[.]org - GET /
- 185.43.223[.]6 port 80 - ettoldketru[.]com - POST /4/forum.php
- 185.43.223[.]6 port 80 - ettoldketru[.]com - POST /mlu/about.php
- 185.43.223[.]6 port 80 - ettoldketru[.]com - POST /d2/about.php
- 192.254.234[.]151 port 80 - image-a[.]com - GET /wp-content/plugins/easy-media-gallery/includes/1
- 192.254.234[.]151 port 80 - image-a[.]com - GET /wp-content/plugins/easy-media-gallery/includes/4
- 192.254.234[.]151 port 80 - image-a[.]com - GET /wp-content/plugins/easy-media-gallery/includes/5
- 198.105.244[.]228 port 443 - lyrintedba[.]com - attempted TCP connections but RST from server
- 198.105.254[.]228 port 443 - lyrintedba[.]com - attempted TCP connections but RST from server
- 198.105.244[.]228 port 443 - reundlaboi[.]ru - attempted TCP connections but RST from server
- 198.105.254[.]228 port 443 - reundlaboi[.]ru - attempted TCP connections but RST from server
FILE HASHES
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 006f7fd56fa89fa576fa95221bdf16422d66787ca366e57816ff6d8a957d7de5
File size: 259,072 bytes
File name: invoice_314728.doc [any six random digits for the numbers]
File description: Word document with macro for Hancitor
- SHA256 hash: 86d9910ae4314d3ac4f9544aa84db11786c2843ace598cf88dc51eaf806e6b54
File size: 185,344 bytes
File location: C:\Users\[username]\AppData\Local\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
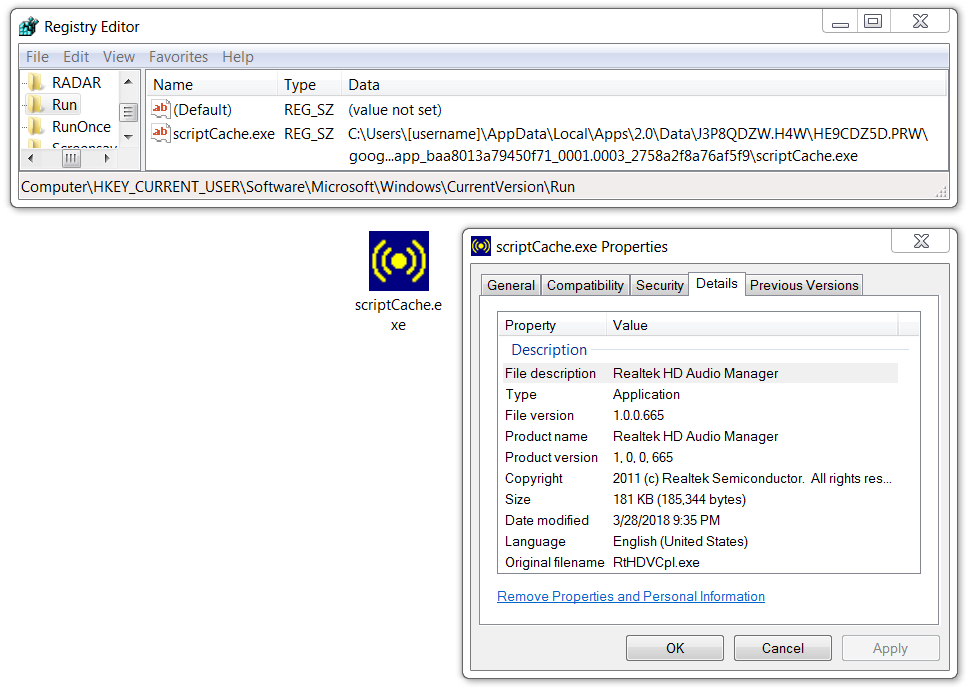
Shown above: Zeus Panda Banker persistent on the infected Windows host.
Click here to return to the main page.