2018-04-24 - DATA DUMP (HANCITOR, TRICKBOT, NECURS BOTNET/FLAWEDAMMYY)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
HANCITOR WITH ZEUS PANDA BANKER:
- 2018-04-24-Hancitor-malspam-30-examples.txt.zip 9.0 kB (8,956 bytes)
- 2018-04-24-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 2.5 MB (2,517,013 bytes)
- 2018-04-24-malware-from-Hancitor-infection.zip 294 kB (294,299 bytes)
TRICKBOT:
- 2018-04-24-Trickbot-malspam-example-UTC.eml.zip 47 kB (46,899 bytes)
- 2018-04-24-Trickbot-infection-traffic.pcap.zip 8.0 MB (7,956,957 bytes)
- 2018-04-24-malware-from-Trickbot-infection.zip 232 kB (231,569 bytes)
POSSIBLE NECURS BOTNET MALSPAM PUSHING ARS STEALER/ASPC BOT & FLAWEDAMMYY:
- 2018-04-24-Necurs-botnet-malspam-tracker-8-examples.csv.zip 1 kB (1,040 bytes)
- 2018-04-24-Necurs-botnet-pushes-FlawedAmmyy.pcap.zip 1.2 MB (1,154,208 bytes)
- 2018-04-24-Necurs-botnet-and-FlawedAmmyy-malspam-malware-and-artifacts.zip 675 kB (675,180 bytes)
- 200-VBS-files-from-blumblummpg_com.zip 7.0 MB (6,966,462 bytes)
NOTES AND IMAGES FOR NECURS BOTNET WAVE:
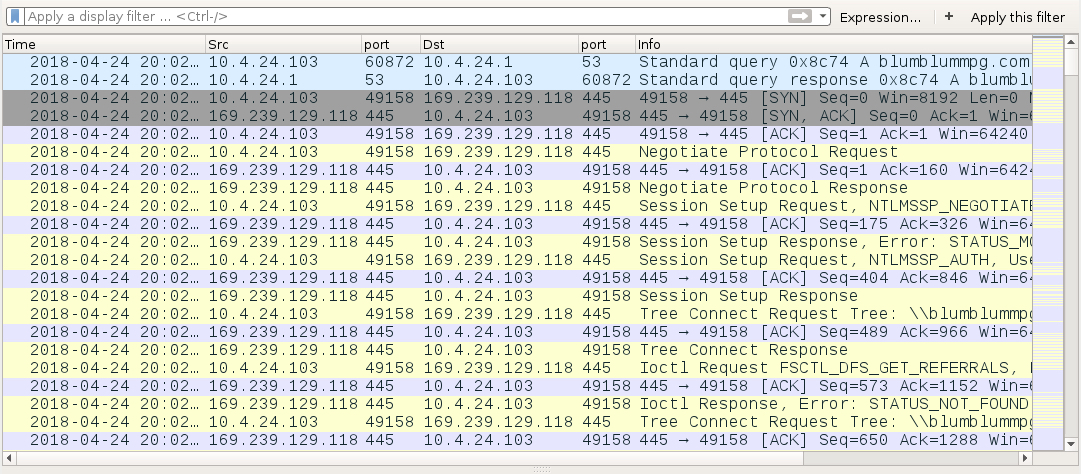
- Email --> .zip attachment --> Extracted .url file --> retrieves .vbs file over SMB --> .vbs file retrieves follow-up malware over HTTP.
Shown above: .url file causeing SMB traffic to blumblummpg.com to retrieve a .vbs file.
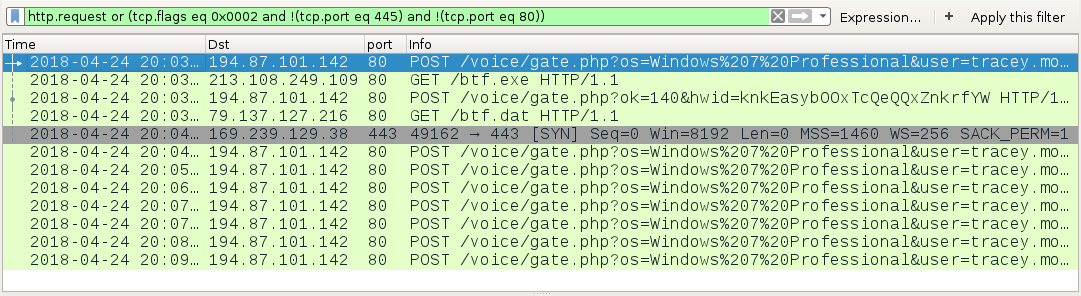
Shown above: Port 80 HTTP POSTs are ARS Stealer/ASPC Bot traffic. Port 443 traffic is FlawedAmmyy.
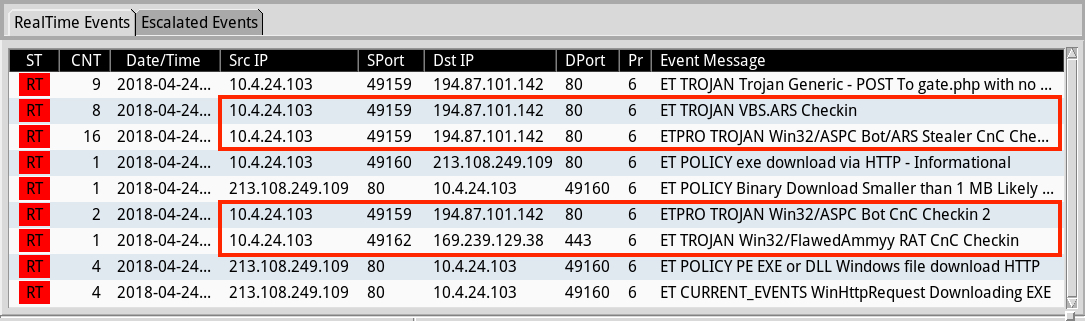
Shown above: Some alerts on the traffic from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
Click here to return to the main page.