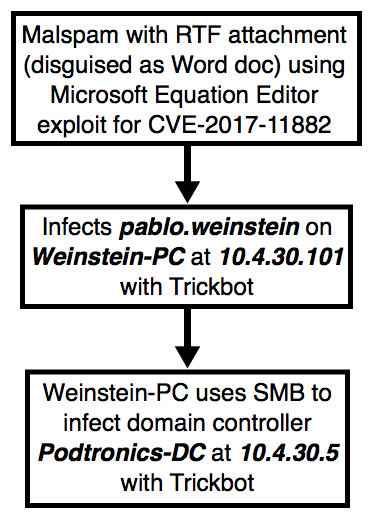
2018-04-30 - EXAMPLE OF TRICKBOT MOVING FROM CLIENT TO DOMAIN CONTROLLER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILE:
- 2018-04-30-Trickbot-goes-from-client-to-domain-controller.pcap.zip 21.1 MB (21,066,283 bytes)
NOTES:
- I normally don't test malware in an Active Directory environment, but I happened to run across this behavior from Trickbot last week.
- Don't know if there are any public examples of traffic for this, so I'm documenting it.
- The domain controller was a Windows 2008 R2 server with default security settings and no security updates.
- The client, as usual, was running Windows 7 SP1 without any security updates.
- I've stripped most, but not all, of traffic unrelated to the infection from today's pcap.
Shown above: Flowchart for this activity.
IMAGES:
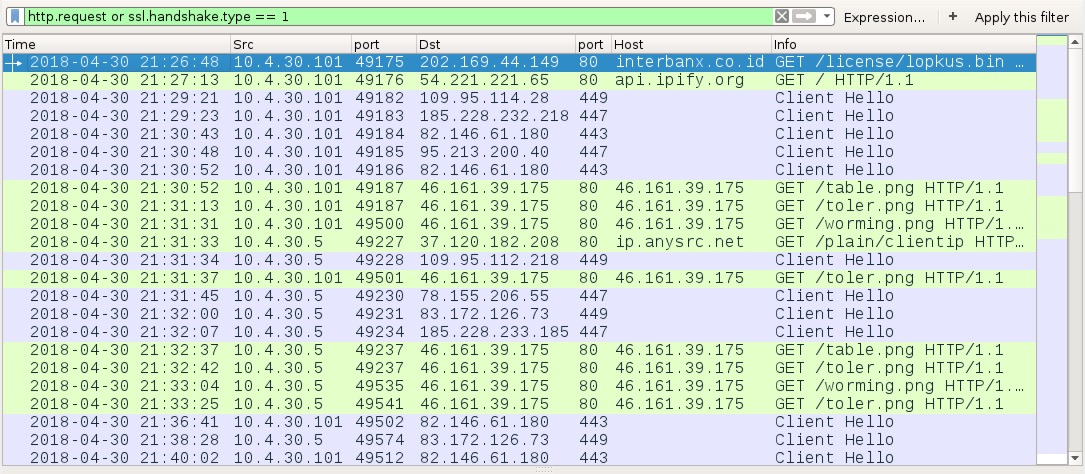
Shown above: HTTP and SSL traffic from the infection filtered in Wireshark. Note how 10.4.30[.]101 (the Windows client) and 10.4.30[.]5 (the domain controller) are both
generating post-infection traffic for Trickbot.
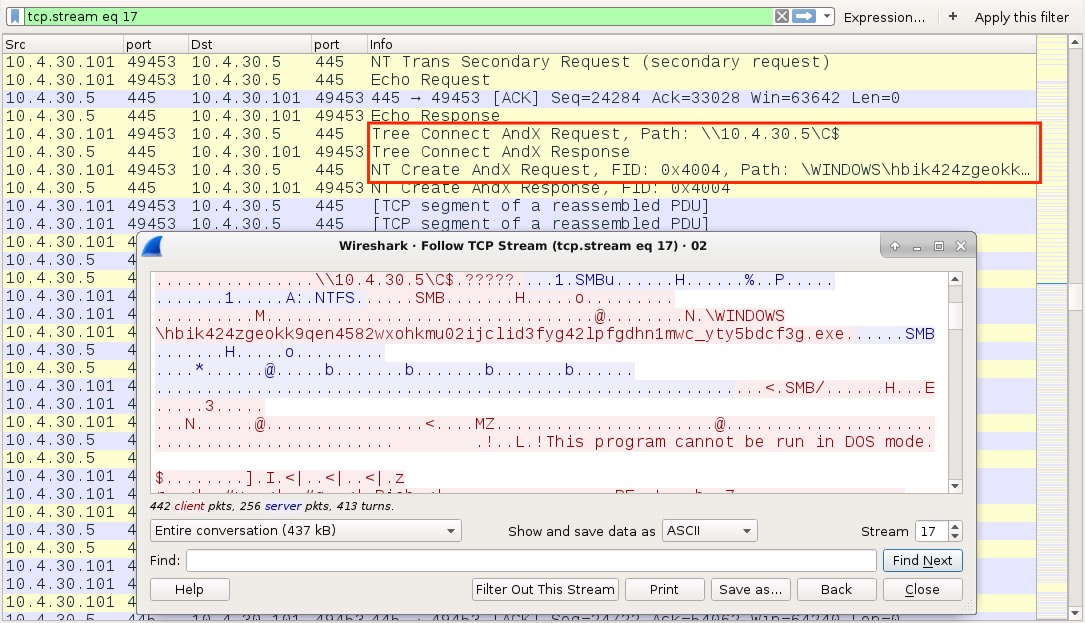
Shown above: One of the Trickbot malware files pushed from 10.4.30[.]101 to 10.4.30[.]5 over SMB
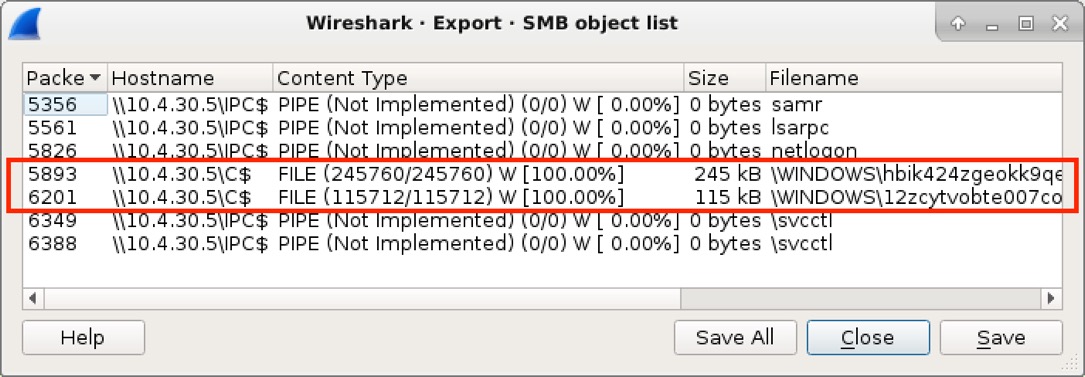
Shown above: You can extract these Trickbot malware samples from the pcap in Wireshark by using File --> Export Objects --> SMB...
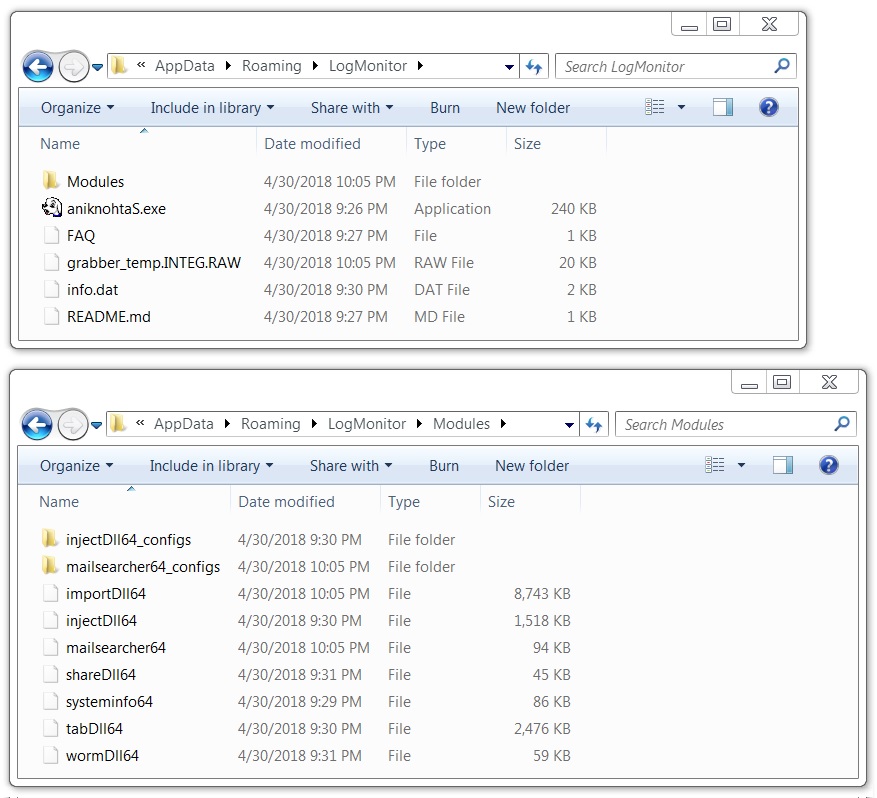
Shown above: Artifacts seen on the infected Windows client at 10.4.30[.]101.
Click here to return to the main page.