2018-05-01 - HANCITOR FROM FAKE U.S. BANK NOTIFICATIONS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-05-01-Hancitor-infection-with-Zeus-Panda-Banker.pcap.zip 583 kB (582,768 bytes)
- 2018-05-01-Hancitor-infection-with-Zeus-Panda-Banker.pcap (784,611 bytes)
- Zip archive of the emails: 2018-05-01-Hancitor-malspam-60-examples.txt.zip 39 kB (39,197 bytes)
- 2018-05-01-Hancitor-malspam-60-examples.txt (1,296,449 bytes)
- Zip archive of the malware: 2018-05-01-malware-from-Hancitor-infection.zip 307 kB (306,904 bytes)
- 2018-05-01-Word-doc-with-macro-for-Hancitor.doc (276,480 bytes)
- 2018-05-01-Zeus-Panda-Banker-from-Hancitor.exe (168,448 bytes)
NOTES:
- The block list contains additional info reported by @Techhelplistcom in the VirusTotal entry for the associated Word Document.
- As always, my thanks to everyone who keeps an eye on this malspam and reports about it near-real-time on Twitter.
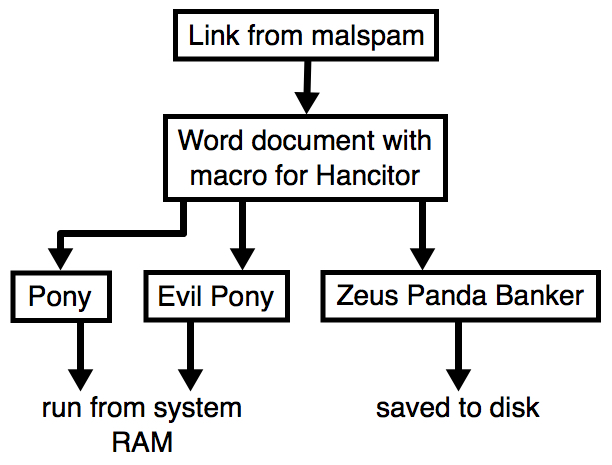
Shown above: Flow chart for a typical Hancitor malspam infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- actuneupca[.]com
- chiropracticlibrary[.]com
- clifmays[.]com
- gamification4you[.]com
- ifewholehousefan[.]com
- ifewholehousefan[.]net
- ifewholehousefans[.]com
- ifewholehousefans[.]info
- ifewholehousefans[.]net
- interfaithelectricandsolar[.]co
- interfaithelectricnsolar[.]co
- lmperfumes[.]com
- spinalrt[.]com
- superiorcomfortprohvac[.]com
- superiorhvacuniversity[.]com
- triadhangout[.]com
- triadpain[.]com
- triadpaingroup[.]com
- supratparfa[.]com
- losupsofof[.]ru
- depeparand[.]ru
- hxxp[:]//kdprvirtual[.]com/wp-content/plugins/duplicate-post/1
- hxxp[:]//kdprvirtual[.]com/wp-content/plugins/duplicate-post/2
- hxxp[:]//kdprvirtual[.]com/wp-content/plugins/duplicate-post/3
- hxxp[:]//animalhealthcenterinc[.]com/wp-content/plugins/post-expirator/1
- hxxp[:]//animalhealthcenterinc[.]com/wp-content/plugins/post-expirator/2
- hxxp[:]//animalhealthcenterinc[.]com/wp-content/plugins/post-expirator/3
- hxxp[:]//rogersonenterprises[.]com/blog/wp-content/plugins/jetpack/1
- hxxp[:]//rogersonenterprises[.]com/blog/wp-content/plugins/jetpack/2
- hxxp[:]//rogersonenterprises[.]com/blog/wp-content/plugins/jetpack/3
- hxxp[:]//militaryschools101[.]com/wp-content/plugins/nofollow-for-external-link/1
- hxxp[:]//militaryschools101[.]com/wp-content/plugins/nofollow-for-external-link/2
- hxxp[:]//militaryschools101[.]com/wp-content/plugins/nofollow-for-external-link/3
- hxxp[:]//bestwptricks[.]com/wp-content/plugins/polldaddy/1
- hxxp[:]//bestwptricks[.]com/wp-content/plugins/polldaddy/2
- hxxp[:]//bestwptricks[.]com/wp-content/plugins/polldaddy/3
- bithetbuter[.]ru
EMAILS
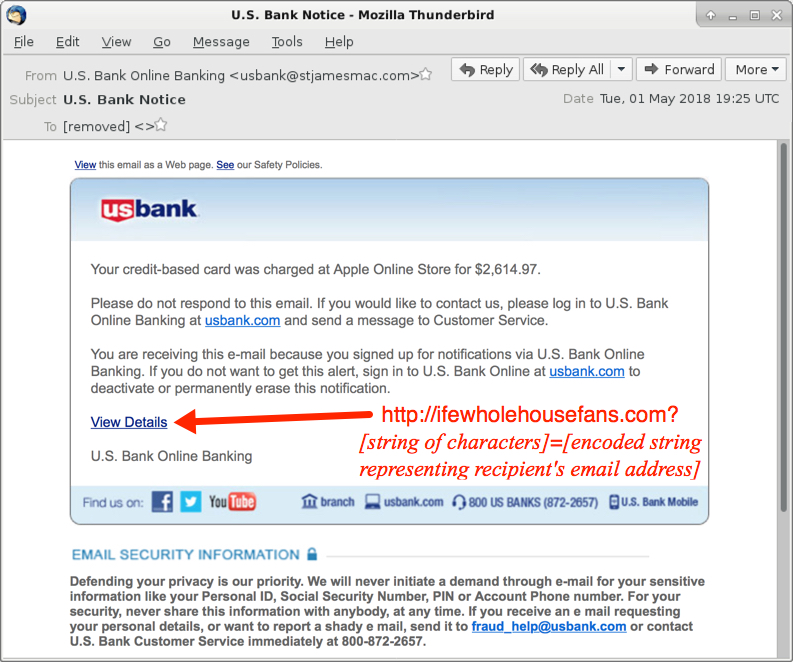
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
- Date/Time: Tuesday 2018-05-01 as early as 14:35 UTC through at least 19:20 UTC
- Received: from stjamesmac[.]com ([12.71.215[.]234])
- Received: from stjamesmac[.]com ([12.154.171[.]180])
- Received: from stjamesmac[.]com ([12.192.193[.]186])
- Received: from stjamesmac[.]com ([23.24.72[.]250])
- Received: from stjamesmac[.]com ([23.30.139[.]233])
- Received: from stjamesmac[.]com ([24.18.144[.]193])
- Received: from stjamesmac[.]com ([24.172.35[.]186])
- Received: from stjamesmac[.]com ([24.178.178[.]233])
- Received: from stjamesmac[.]com ([24.197.23[.]194])
- Received: from stjamesmac[.]com ([24.227.60[.]226])
- Received: from stjamesmac[.]com ([24.94.233[.]117])
- Received: from stjamesmac[.]com ([40.79.56[.]104])
- Received: from stjamesmac[.]com ([50.76.68[.]94])
- Received: from stjamesmac[.]com ([50.225.140[.]58])
- Received: from stjamesmac[.]com ([50.246.140[.]38])
- Received: from stjamesmac[.]com ([50.253.24[.]13])
- Received: from stjamesmac[.]com ([50.255.162[.]73])
- Received: from stjamesmac[.]com ([65.117.102[.]66])
- Received: from stjamesmac[.]com ([65.95.68[.]185])
- Received: from stjamesmac[.]com ([66.64.45[.]22])
- Received: from stjamesmac[.]com ([67.214.241[.]54])
- Received: from stjamesmac[.]com ([67.214.247[.]194])
- Received: from stjamesmac[.]com ([68.119.229[.]151])
- Received: from stjamesmac[.]com ([68.236.120[.]88])
- Received: from stjamesmac[.]com ([69.54.28[.]220])
- Received: from stjamesmac[.]com ([69.193.167[.]218])
- Received: from stjamesmac[.]com ([70.62.248[.]246])
- Received: from stjamesmac[.]com ([70.88.160[.]174])
- Received: from stjamesmac[.]com ([70.102.68[.]117])
- Received: from stjamesmac[.]com ([71.14.25[.]46])
- Received: from stjamesmac[.]com ([71.45.207[.]173])
- Received: from stjamesmac[.]com ([71.201.16[.]43])
- Received: from stjamesmac[.]com ([72.82.24[.]25])
- Received: from stjamesmac[.]com ([72.84.234[.]140])
- Received: from stjamesmac[.]com ([73.227.133[.]179])
- Received: from stjamesmac[.]com ([74.65.197[.]73])
- Received: from stjamesmac[.]com ([74.69.184[.]228])
- Received: from stjamesmac[.]com ([75.139.49[.]124])
- Received: from stjamesmac[.]com ([75.146.90[.]69])
- Received: from stjamesmac[.]com ([75.149.57[.]254])
- Received: from stjamesmac[.]com ([96.37.147[.]182])
- Received: from stjamesmac[.]com ([96.38.67[.]251])
- Received: from stjamesmac[.]com ([96.53.20[.]90])
- Received: from stjamesmac[.]com ([96.82.248[.]185])
- Received: from stjamesmac[.]com ([96.92.93[.]193])
- Received: from stjamesmac[.]com ([97.77.98[.]2])
- Received: from stjamesmac[.]com ([98.101.194[.]106])
- Received: from stjamesmac[.]com ([104.201.90[.]210])
- Received: from stjamesmac[.]com ([173.8.67[.]169])
- Received: from stjamesmac[.]com ([173.12.134[.]65])
- Received: from stjamesmac[.]com ([173.219.61[.]189])
- Received: from stjamesmac[.]com ([173.220.58[.]194])
- Received: from stjamesmac[.]com ([174.80.66[.]187])
- Received: from stjamesmac[.]com ([184.71.42[.]34])
- Received: from stjamesmac[.]com ([199.10.29[.]18])
- Received: from stjamesmac[.]com ([207.119.219[.]225])
- Received: from stjamesmac[.]com ([216.26.206[.]112])
- Received: from stjamesmac[.]com ([216.130.144[.]155])
- From: "U.S. Bank Online " <usbank@stjamesmac[.]com>
- From: "U.S. Bank Online Banking" <usbank@stjamesmac[.]com>
- Subject: U.S. Bank Alert
- Subject: U.S. Bank Message
- Subject: U.S. Bank Notice
- Subject: U.S. Bank Notification
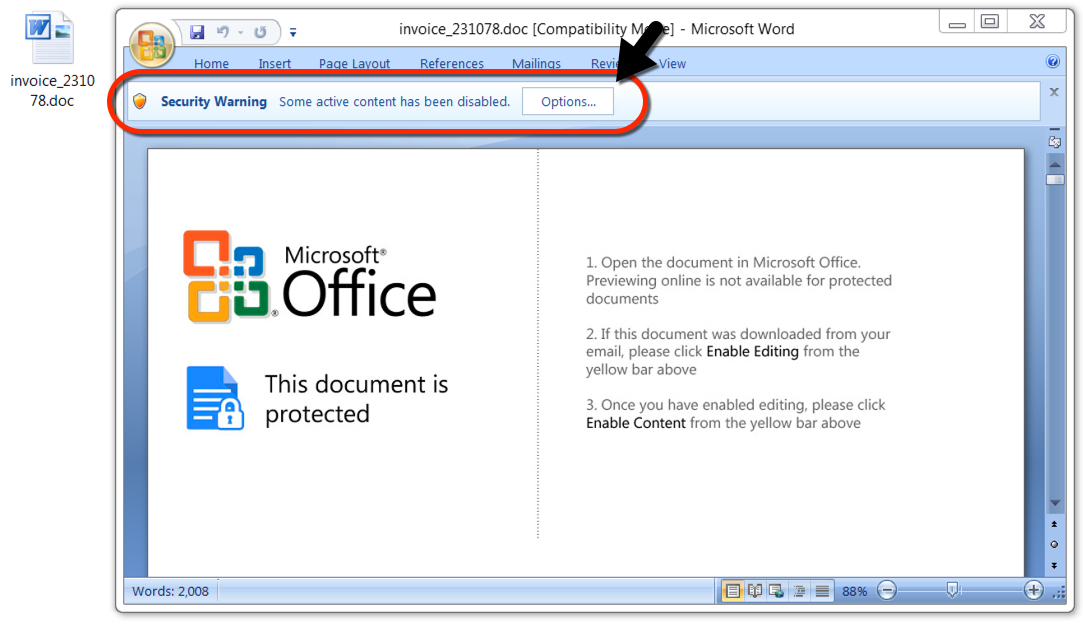
Shown above: Malicious Word document downloaded from link in the malspam.
TRAFFIC
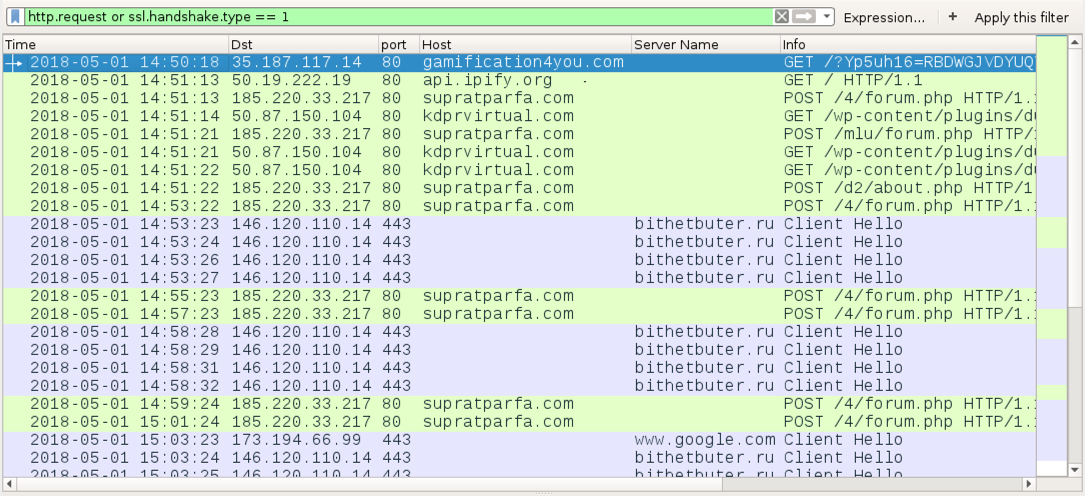
Shown above: Traffic from an infection filtered in Wireshark.
LINKS IN THE EMAILS TO DOWNLOAD THE WORD DOCUMENT:
- hxxp[:]//actuneupca[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//chiropracticlibrary[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//clifmays[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//gamification4you[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//ifewholehousefan[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//ifewholehousefan[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//ifewholehousefans[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//ifewholehousefans[.]info?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//ifewholehousefans[.]net?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//interfaithelectricandsolar[.]co?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//interfaithelectricnsolar[.]co?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//lmperfumes[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//spinalrt[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//superiorcomfortprohvac[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//superiorhvacuniversity[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//triadhangout[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//triadpain[.]com?[string of characters]=[encoded string representing recipient's email address]
- hxxp[:]//triadpaingroup[.]com?[string of characters]=[encoded string representing recipient's email address]
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 35.187.117[.]14 port 80 - gamification4you[.]com - GET /?[string of characters]=[encoded string representing recipient's email address]
- port 80 - api.ipify[.]org - GET /
- 185.220.33[.]217 port 80 - supratparfa[.]com - POST /4/forum.php
- 185.220.33[.]217 port 80 - supratparfa[.]com - POST /mlu/about.php
- 185.220.33[.]217 port 80 - supratparfa[.]com - POST /d2/about.php
- 50.87.150[.]104 port 80 - kdprvirtual[.]com - GET /wp-content/plugins/duplicate-post/1
- 50.87.150[.]104 port 80 - kdprvirtual[.]com - GET /wp-content/plugins/duplicate-post/2
- 50.87.150[.]104 port 80 - kdprvirtual[.]com - GET /wp-content/plugins/duplicate-post/3
- 146.120.110[.]14 port 443 - bithetbuter[.]ru - HTTPS/SSL/TLS traffic caused by Zeus Panda Banker
- port 80 - www.google[.]com - HTTPS/SSL/TLS traffic - probable connectivity check caused by Zeus Panda Banker
FILE HASHES
MALWARE RETRIEVED FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: d2a812fbc44b5612d39806a96631b36f5b98c93458e49eb4f0ace42b6b8d6c66
File size: 276,480 bytes
File name: invoice_231078.doc [any six random digits for the numbers]
File description: Word document with macro for Hancitor
- SHA256 hash: 93930920ab4fab2dac0978c390b59cd6a6cb037c1faf404c0bdbe1e2f575fd2c
File size: 168,448 bytes
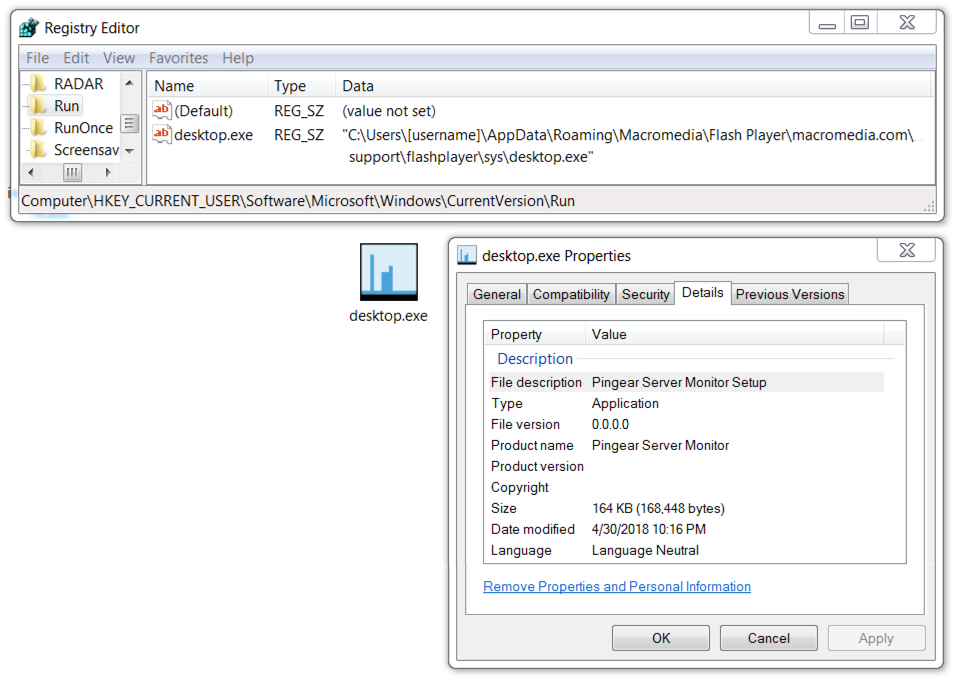
File location: C:\Users\[username]\AppData\Roaming\[existing directory path]\[random name].exe
File description: Zeus Panda Banker
Shown above: Zeus Panda Banker persistent on the infected Windows host.
Click here to return to the main page.