2018-05-01 - TRICKBOT FROM MALSPAM, SUBJECT: FW: ACCOUNT DOCUMENTS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the traffic: 2018-05-01-Trickbot-infection-traffic.pcap.zip 6.5 MB (6,501,990 bytes)
- 2018-05-01-Trickbot-infection-traffic.pcap (7,121,402 bytes)
- Zip archive of the email: 2018-05-01-Trickbot-malspam-1133-UTC.eml.zip 38 kB (38,222 bytes)
- 2018-05-01-Trickbot-malspam-1133-UTC.eml (116,476 bytes)
- Zip archive of the malware and artifacts: 2018-05-01-malware-and-artifacts-from-Trickbot-infection.zip 422 kB (421,620 bytes)
- 2018-05-01-Trickbot-artifact.txt (329 bytes)
- 2018-05-01-Trickbot-binary-1-of-2.exe (270,336 bytes)
- 2018-05-01-Trickbot-binary-2-of-2.exe (372,224 bytes)
- 2018-05-01-Trickbot-malspam-attached-RTF-file.doc (62,492 bytes)
- 2018-05-01-scheduled-task-to-keep-Trickbot-persistent.txt (3,676 bytes)
NOTES:
- This post was delayed a day, because I was busy with other things.
- My thanks to @dvk01uk for Wednesday's blog post on My Online Security.
- For the past few weeks, Trickbot malspam has been using RTF attachments exploiting CVE-2017-11882.
- These RTF attachments are disguised as Microsoft Word documents, because they use the .doc file extension.
- Information on this Trickbot binary's configuration is available at this page on Github by @JR0driguezB.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- hxxp[:]//tasfitness[.]com/2593f737367806c10fb5aa7766eda1ea4a.bin
- hxxp[:]//opticsigns[.]com/2593f737367806c10fb5aa7766eda1ea4a.bin
- hxxp[:]//46.161.39[.]175/table.png
- hxxp[:]//46.161.39[.]175/toler.png
- hxxp[:]//193.233.62[.]81/526.png
EMAILS
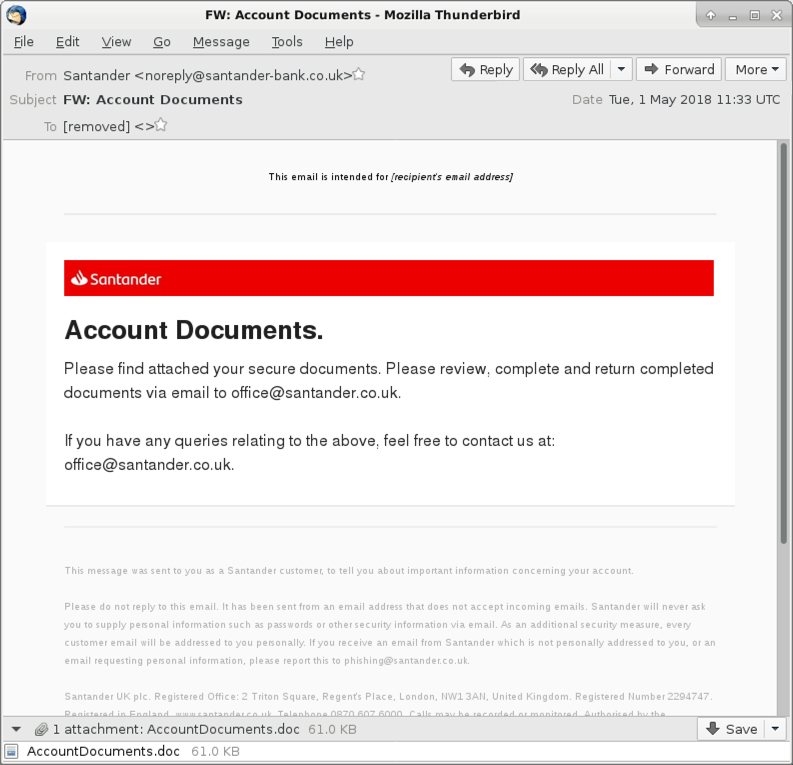
Shown above: Screenshot from one of the emails.
EMAIL HEADERS:
Received: from santander-bank[.]co[.]uk (unknown [128.127.108[.]227])by [removed] for [removed]; Tue, 1 May 2018 18:41:12 +0700 (WIB)
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=key; d=santander-bank[.]co[.]uk;
h=Mime-Version:Subject:From:Date:To:Content-Type:Message-ID;
bh=ejKKHFcJirhlS5iAlWanrKPxCG8=;
b=Apz+AO1YOiBWaxpz8Ec6NlMRyqEMSv/OEh4xSjpC3BSjKEGyX2Ne0iuDUF/P0ybaxeUKkF+x0Ez7
wzMHw2bLhSz+fTeLMRhEL6bId+lafRAAnD2iaOVnI8SLONPTsRtZ2+ZTl340x3cyBrFodl0/hOXU
K851ysBuZDS/9aiXpP4=
Received: by santander-bank[.]co[.]uk id ht196nocte0i for [removed]; Tue, 1 May 2018 07:33:09 -0400 (envelope-from <noreply-[recipient's email address]@santander-bank[.]co[.]uk>)
Mime-Version: 1.0
Subject: FW: Account Documents
From: "Santander" <noreply@santander-bank[.]co[.]uk>
Date: Tue, 1 May 2018 07:33:09 -0400
To: [removed]
Content-Type: multipart/mixed;
boundary=01b8f130f133240b42a2a8ce9c735cd9
Message-ID: <0.0.0.0.1D3E1402E438116.43E88E4@santander-bank[.]co[.]uk>

Shown above: RTF document attached to the malspam.
TRAFFIC
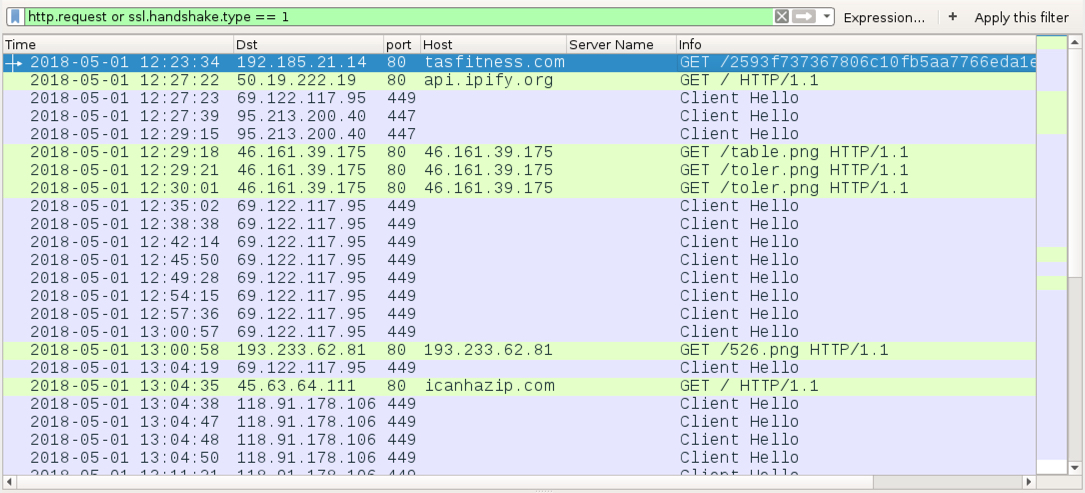
Shown above: Traffic from an infection filtered in Wireshark.
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 192.185.21[.]14 port 80 - tasfitness[.]com - GET /2593f737367806c10fb5aa7766eda1ea4a.bin
- port 80 - api.ipify[.]org - GET / (IP address check by the infected host)
- 69.122.117[.]95 port 449 - SSL/TLS traffic caused by Trickbot
- 95.213.200[.]40 port 447 - SSL/TLS traffic caused by Trickbot
- 69.122.117[.]95 port 449 - SSL/TLS traffic caused by Trickbot
- 46.161.39[.]175 port 80 - 46.161.39[.]175 - GET /table.png
- 46.161.39[.]175 port 80 - 46.161.39[.]175 - GET /toler.png
- 46.161.39[.]175 port 80 - 46.161.39[.]175 - GET /toler.png
- 193.233.62[.]81 port 80 - 193.233.62[.]81 - GET /526.png
- port 80 - icanhazip[.]com - GET / (IP address check by the infected host)
- 118.91.178[.]106 port 449 - SSL/TLS traffic caused by Trickbot
- 68.227.31[.]46 port 449 - SSL/TLS traffic caused by Trickbot
FILE HASHES
RTF ATTACHMENT FROM THE MALSPAM:
- SHA256 hash: 800150b0ecd5d7552f6d2714306c7ecc8df539bb358df48568265f7d405d2052
File size: 62,492 bytes
File name: AccountDocuments.doc
File description: RTF file with CVE-2017-11882 exploit for Microsoft Office
TRICKBOT BINARY (1 OF 2):
- SHA256 hash: 555c88051ccfa891550c7c149ee4d95843923bc8d98e9731ffb7e04004bb3d5d
File size: 270,336 bytes
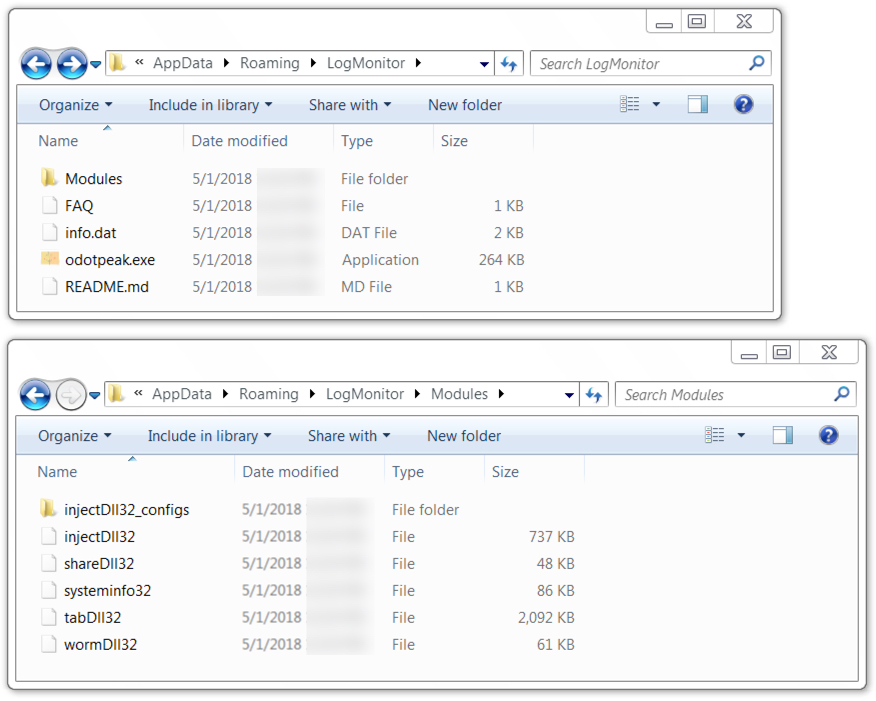
File location: C:\Users\[username]\AppData\Roaming\LogMonitor\odotpeak.exe
File description: Trickbot malware (Windows executable file)
TRICKBOT BINARY (2 OF 2):
- SHA256 hash: 6d57b3dfa296d9c296819ea4d89794aa8ada1f36edcf3134924c1a6460be7bc2
File size: 372,224 bytes
File location: C:\Users\[username]\AppData\Roaming\LogMonitor\odotpeak.exe
File description: Trickbot malware (Windows executable file)
Shown above: Trickbot malware persistent on the infected Windows host.
Click here to return to the main page.